1.现状:
如图,用户网段有192.168.50.0/24、192.168.51.0/24和192.168.52.0/24、192.168.53.0/24。在防火墙上有静态路由到运维专线的10.160.25.0/24网段,且有到10.70.31.0/24的IPSec VPN。
2.现象:
192.168.50.0/24、192.168.51.0/24和192.168.52.0/24、192.168.53.0/24均可正常通到各个外网。但10.160.25.0/24和10.70.31.0/24段到192.168.50.0/24、192.168.51.0/24能通,到192.168.52.0/24、192.168.53.0/24不通。
3.分析:
通过在10.160.25.0/24的一台机器上做trace发现断点在防火墙。
4.排查:
防火墙上开启debug flow
FGT5HD3915800383 # diagnose debug flow filter addr 10.160.25.39
FGT5HD3915800383 # diagnose debug flow show console enable
show trace messages on console
FGT5HD3915800383 # diagnose debug flow trace start 20
FGT5HD3915800383 # diagnose debug enable
FGT5HD3915800383 # id=13 trace_id=13 func=print_pkt_detail line=4313 msg="vd-root received a packet(proto=6, 10.160.25.39:54490->192.168.200.251:445) from port12. flag [S], seq 3745359550, ack 0, win 8192"
id=13 trace_id=13 func=init_ip_session_common line=4469 msg="allocate a new session-094e72cc"
id=13 trace_id=13 func=vf_ip4_route_input line=1600 msg="find a route: flags=00000000 gw-192.168.79.2 via to-cisco3750"
id=13 trace_id=13 func=fw_forward_handler line=685 msg="Allowed by Policy-63:"
id=13 trace_id=14 func=print_pkt_detail line=4313 msg="vd-root received a packet(proto=6, 192.168.200.251:445->10.160.25.39:54490) from to-cisco3750. flag [S.], seq 3483021419, ack 3745359551, win 8192"
id=13 trace_id=14 func=resolve_ip_tuple_fast line=4372 msg="Find an existing session, id-094e72cc, reply direction"
id=13 trace_id=14 func=vf_ip4_route_input line=1600 msg="find a route: flags=00000000 gw-192.168.72.2 via port12"
id=13 trace_id=15 func=print_pkt_detail line=4313 msg="vd-root received a packet(proto=6, 10.160.25.39:54490->192.168.200.251:445) from port12. flag [.], seq 3745359551, ack 3483021420, win 513"
id=13 trace_id=15 func=resolve_ip_tuple_fast line=4372 msg="Find an existing session, id-094e72cc, original direction"
//以上为10.160.25.39和192.168.200.251正常通信的信息
id=13 trace_id=16 func=print_pkt_detail line=4313 msg="vd-root received a packet(proto=1, 10.160.25.39:1->192.168.52.48:8) from port12. code=8, type=0, id=1, seq=1549."
id=13 trace_id=16 func=init_ip_session_common line=4469 msg="allocate a new session-094e7a2a"
id=13 trace_id=16 func=vf_ip4_route_input line=1600 msg="find a route: flags=00000000 gw-192.168.52.48 via port1"
id=13 trace_id=16 func=fw_forward_handler line=685 msg="Allowed by Policy-63:"
id=13 trace_id=17 func=print_pkt_detail line=4313 msg="vd-root received a packet(proto=1, 10.160.25.39:1->192.168.52.48:8) from port12. code=8, type=0, id=1, seq=1550."
id=13 trace_id=17 func=resolve_ip_tuple_fast line=4372 msg="Find an existing session, id-094e7a2a, original direction"
id=13 trace_id=18 func=print_pkt_detail line=4313 msg="vd-root received a packet(proto=1, 10.160.25.39:1->192.168.52.48:8) from port12. code=8, type=0, id=1, seq=1551."
id=13 trace_id=18 func=resolve_ip_tuple_fast line=4372 msg="Find an existing session, id-094e7a2a, original direction"
id=13 trace_id=19 func=print_pkt_detail line=4313 msg="vd-root received a packet(proto=1, 10.160.25.39:1->192.168.52.48:8) from port12. code=8, type=0, id=1, seq=1552."
id=13 trace_id=19 func=resolve_ip_tuple_fast line=4372 msg="Find an existing session, id-094e7a2a, original direction"
//发现10.160.25.39与192.168.52.48通信的包发到了“port1”
FGT5HD3915800383 # diagnose debug disable
排查结果即防火墙将数据包发给了port1
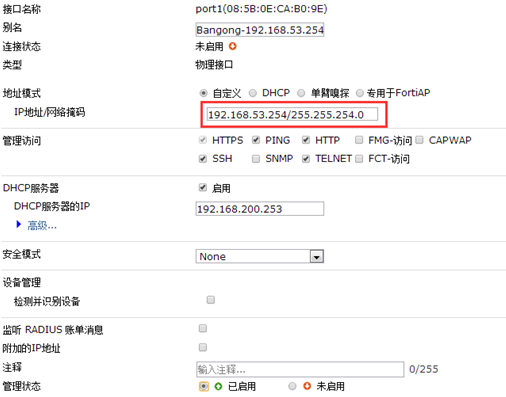
即,防火墙端口状态为启用时,防火墙会产生直连路由,但是在路由表里并不显示。
5.解决:
将端口状态改为未启用即可。





