配置静态ip和网关
-
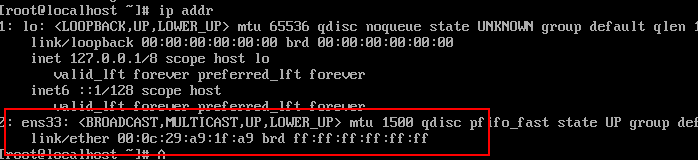
使用 ip addr 查看主机ip
![在这里插入图片描述]()
可以看到目前是没有ip地址的 -
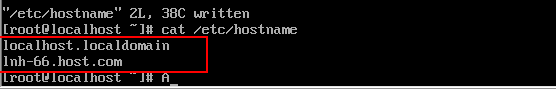
修改 /etc/hostname 文件
vi /etc/hostname
![在这里插入图片描述]()
-
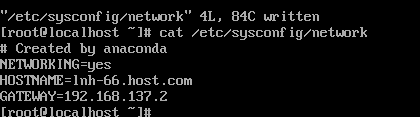
修改 /etc/sysconfig/network文件
NETWORKING=yes
HOSTNAME=lnh-11.host.com
GATEWAY=192.168.137.2
![在这里插入图片描述]()
具体网关地址GATEWAY,查看
![在这里插入图片描述]()
点击 "虚拟网络编辑器" 找到Vmnet8![在这里插入图片描述]()
点击上图中 “NAT设置”按钮,就可以找到具体的网关是多少了
![在这里插入图片描述]()
-
修改该配置文件 /etc/sysconfig/network-scripts/ifcfg-ens33
原有配置
![在这里插入图片描述]()
改为以下配置TYPE=Ethernet PROXY_METHOD=none BROWSER_ONLY=no BOOTPROTO=static # 修改上图中的dhcp为static DEFROUTE=yes IPADDR=192.168.137.66 # 新增配置 本机ip NETMASK=255.255.255.0 DNS1=114.114.114.114 # DNS解析 IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=ens33 UUID=fba41fb8-b0c2-4809-9431-0d92a0fd21d6 DEVICE=ens33 ONBOOT=yes # 将值改为yes -
重启
reboot
重启之后,查看 ip addr ,已经修改成功
![在这里插入图片描述]()
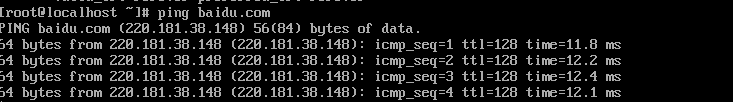
ping baidu.com ok!
![在这里插入图片描述]()
搭建bind9 DNS服务
-
初始化操作系统配置
# 关闭防火墙 systemctl disable firewalld.service # 永久关闭 systemctl stop firewalld.service # 临时关闭 # 关闭selinux sed -i 's/enforcing/disabled/' /etc/selinux/config #永久关闭 setenforce 0 #临时关闭 # 关闭swap sed -ri 's/.*swap.*/#&/' /etc/fstab # 永久关闭 swapoff -a # 临时关闭 # 时间同步 yum install ntpdate -y ntpdate time.windows.com -
安装必要的软件
yum install -y wget net-tools telnet tree nmap sysstat lrzsz dos2unix bind-utils vim less epel-release -
安装bind
yum install -y bind -
编辑主配置文件 /etc/named.conf
options { listen-on port 53 { 192.168.137.66; }; ## 修改为本机ip listen-on-v6 port 53 { ::1; }; forwarders { 192.168.137.2; }; ## 网关 directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; recursing-file "/var/named/data/named.recursing"; secroots-file "/var/named/data/named.secroots"; allow-query { any; }; ## 修改为any,允许任何访问 /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable no; # 修改为no dnssec-validation no; # 修改为 no /* Path to ISC DLV key */ bindkeys-file "/etc/named.root.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; -
编辑区域配置文件 /etc/named.rfc1912.zones
增加配置
## 为后缀 lnh-66.host.com zone "host.com" IN { type master; file "host.com.zone"; allow-update { 192.168.137.66; }; # 主机ip }; -
配置主机域文件 /var/named/host.com.zone
$ORIGIN host.com. $TTL 600 ; 10 minutes @ IN SOA dns.host.com. dnsadmin.host.com. ( 2021062401 ; serial 10800 ; refresh (3 hours) 900 ; retry (15 minutes) 604800 ; expire (1 week) 86400 ; minimum (1 day) ) NS dns.host.com. $TTL 60 ; 1 minute dns A 192.168.137.66 lnh-66 A 192.168.137.66 -
检查配置是否有错误
~]# named-checkconf -
修改主机的dns服务器地址 /etc/sysconfig/network-scripts/ifcfg-ens33
![在这里插入图片描述]()
-
重启网络
systemctl restart network -
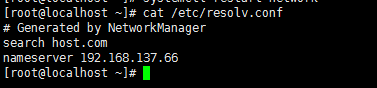
查看 /etc/resolv.conf
![在这里插入图片描述]()
-
启动 bind9
systemctl start named systemctl enable namedping 百度和内网 ok
![在这里插入图片描述]()
-
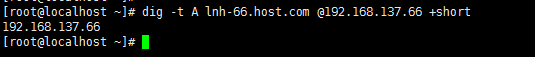
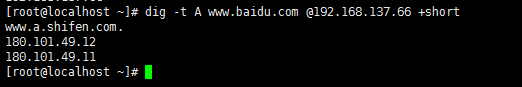
解析,查看dns指向
dig -t A lnh-66.host.com @192.168.137.66 +short![在这里插入图片描述]()
![在这里插入图片描述]()
-
找到宿主机如下配置
![在这里插入图片描述]()
修改DNS服务器,为192.168.137.66(安装bind的服务器地址)在宿主机通过虚拟机主机名ping ,ok
![在这里插入图片描述]()
充满鲜花的世界到底在哪里











 浙公网安备 33010602011771号
浙公网安备 33010602011771号