RequestAuthentication实战
部署keycloak
[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# kubectl apply -f 01-deploy-keycloak.yaml [root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# cat 01-deploy-keycloak.yaml
---
apiVersion: v1
kind: Namespace
metadata:
name: keycloak
---
apiVersion: v1
kind: Service
metadata:
name: keycloak
namespace: keycloak
labels:
app: keycloak
spec:
ports:
- name: http
port: 8080
targetPort: 8080
selector:
app: keycloak
type: LoadBalancer
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: keycloak
namespace: keycloak
labels:
app: keycloak
spec:
replicas: 1
selector:
matchLabels:
app: keycloak
template:
metadata:
labels:
app: keycloak
spec:
containers:
- name: keycloak
image: quay.io/keycloak/keycloak:16.1.1
#image: quay.io/keycloak/keycloak:18.0.0-legacy
env:
- name: KEYCLOAK_USER
value: "admin"
- name: KEYCLOAK_PASSWORD
value: "admin"
- name: PROXY_ADDRESS_FORWARDING
value: "true"
ports:
- name: http
containerPort: 8080
- name: https
containerPort: 8443
readinessProbe:
httpGet:
path: /auth/realms/master
port: 8080[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# kubectl apply -f ./keycloak/[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# cat keycloak/keycloak-destinationrule.yaml
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: keycloak
namespace: keycloak
spec:
host: keycloak
trafficPolicy:
tls:
mode: DISABLE
---
[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# cat keycloak/keycloak-gateway.yaml
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:
name: keycloak-gateway
namespace: istio-system
spec:
selector:
app: istio-ingressgateway
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- "keycloak.yzy.com"
---
[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# cat keycloak/keycloak-virtualservice.yaml
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: keycloak-virtualservice
namespace: keycloak
spec:
hosts:
- "keycloak.yzy.com"
gateways:
- "istio-system/keycloak-gateway"
http:
- match:
- uri:
prefix: /
route:
- destination:
host: keycloak
port:
number: 8080
---
开启另外一种访问方法
[root@k8s-node1 network-scripts]# cat ifcfg-eth0:1
# Generated by parse-kickstart
DEVICE="eth0:1"
IPV6INIT="yes"
BOOTPROTO="none"
#UUID="0940732d-ee6c-493d-97a4-b1b46f49740d"
ONBOOT="yes"
IPADDR=10.211.55.30
NETMASK=255.255.255.0
GATEWAY=10.211.55.254
[root@k8s-node1 network-scripts]# ifup eth0:1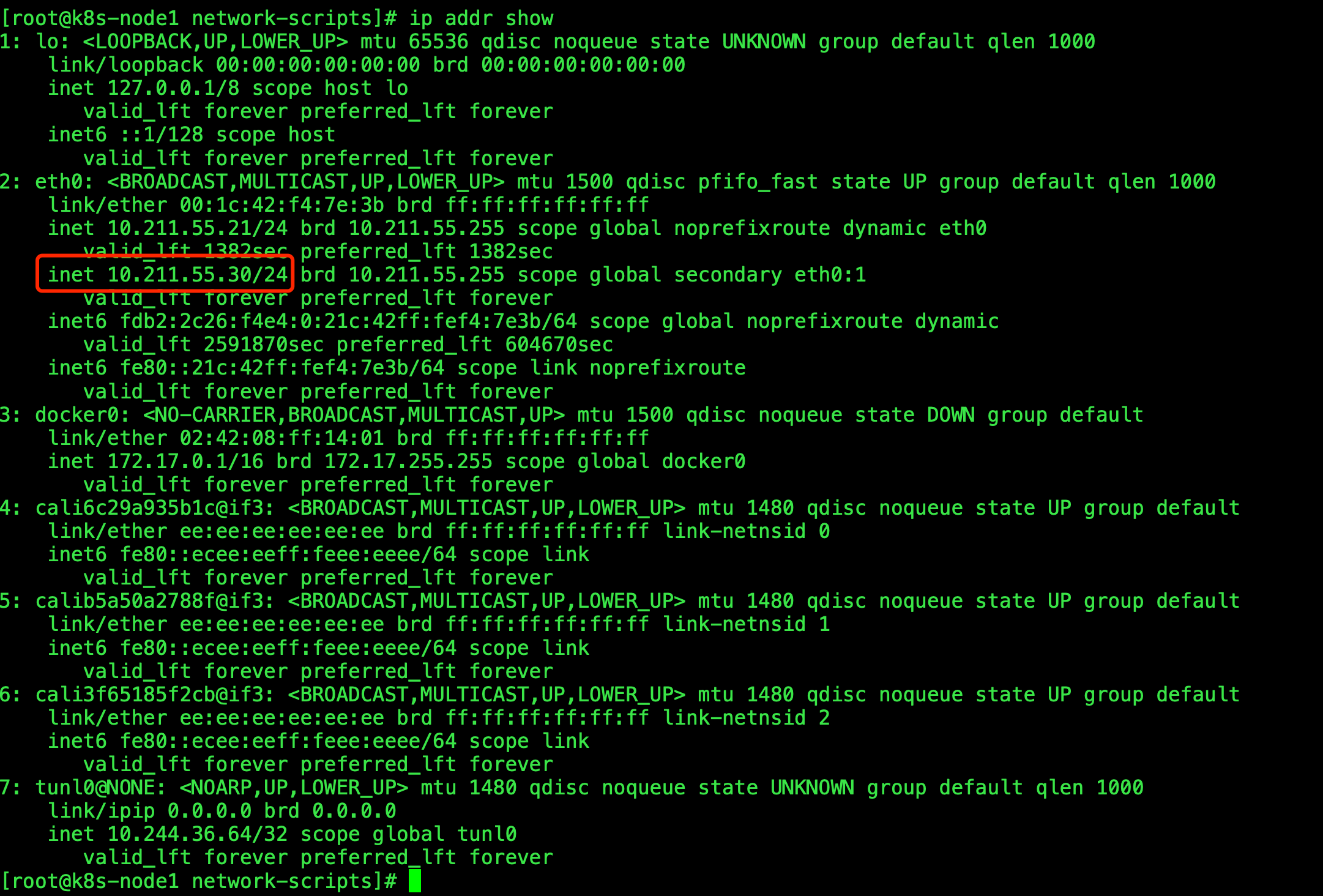
[root@k8s-master ~]# kubectl edit svc keycloak -n keycloak 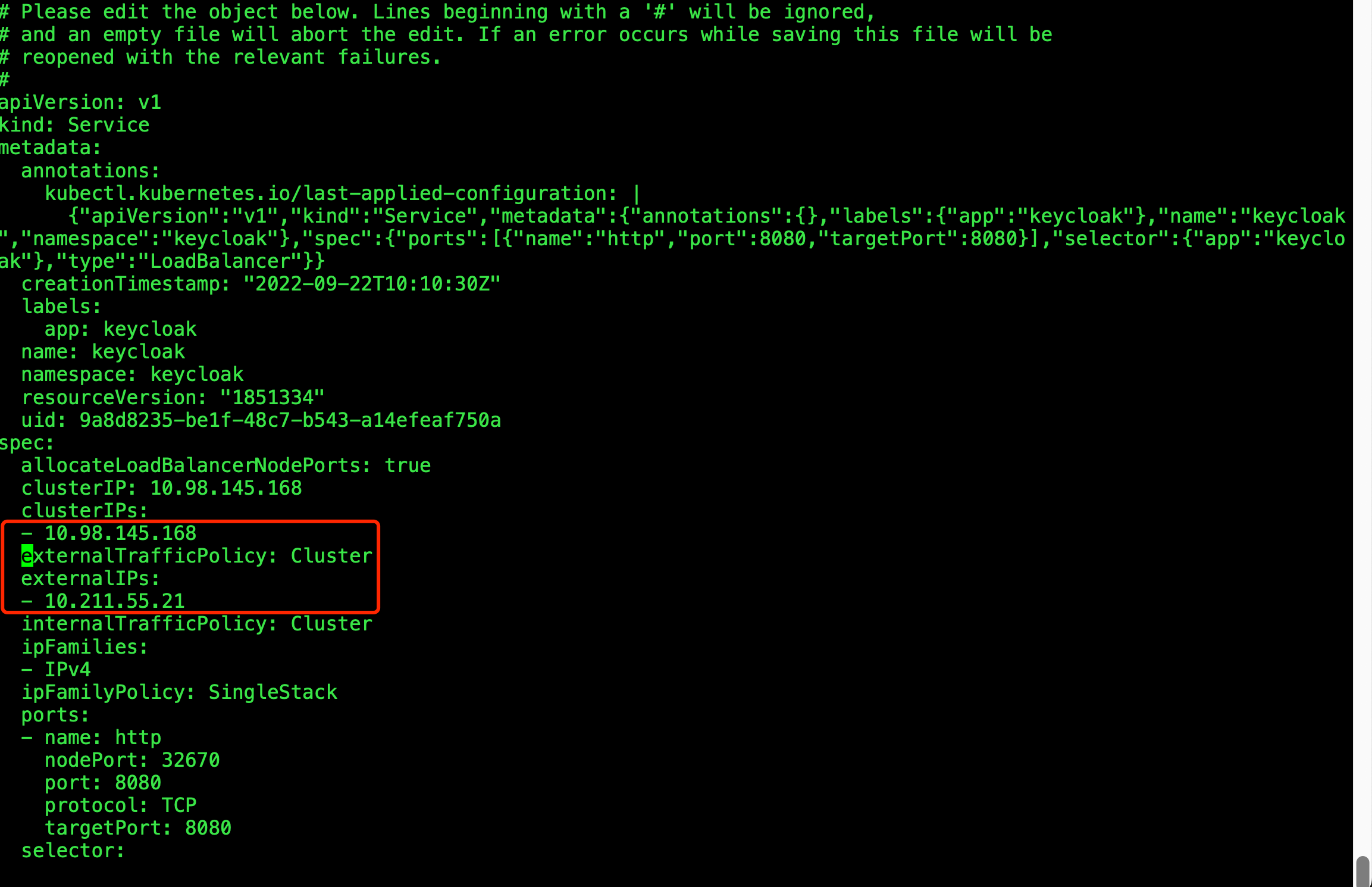
[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# kubectl get svc -n keycloak
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
keycloak LoadBalancer 10.98.145.168 10.211.55.21 8080:32670/TCP 31m 
登陆到keycloak,用户名密码都是admin,开启中文
添加域
创建
创建客户端
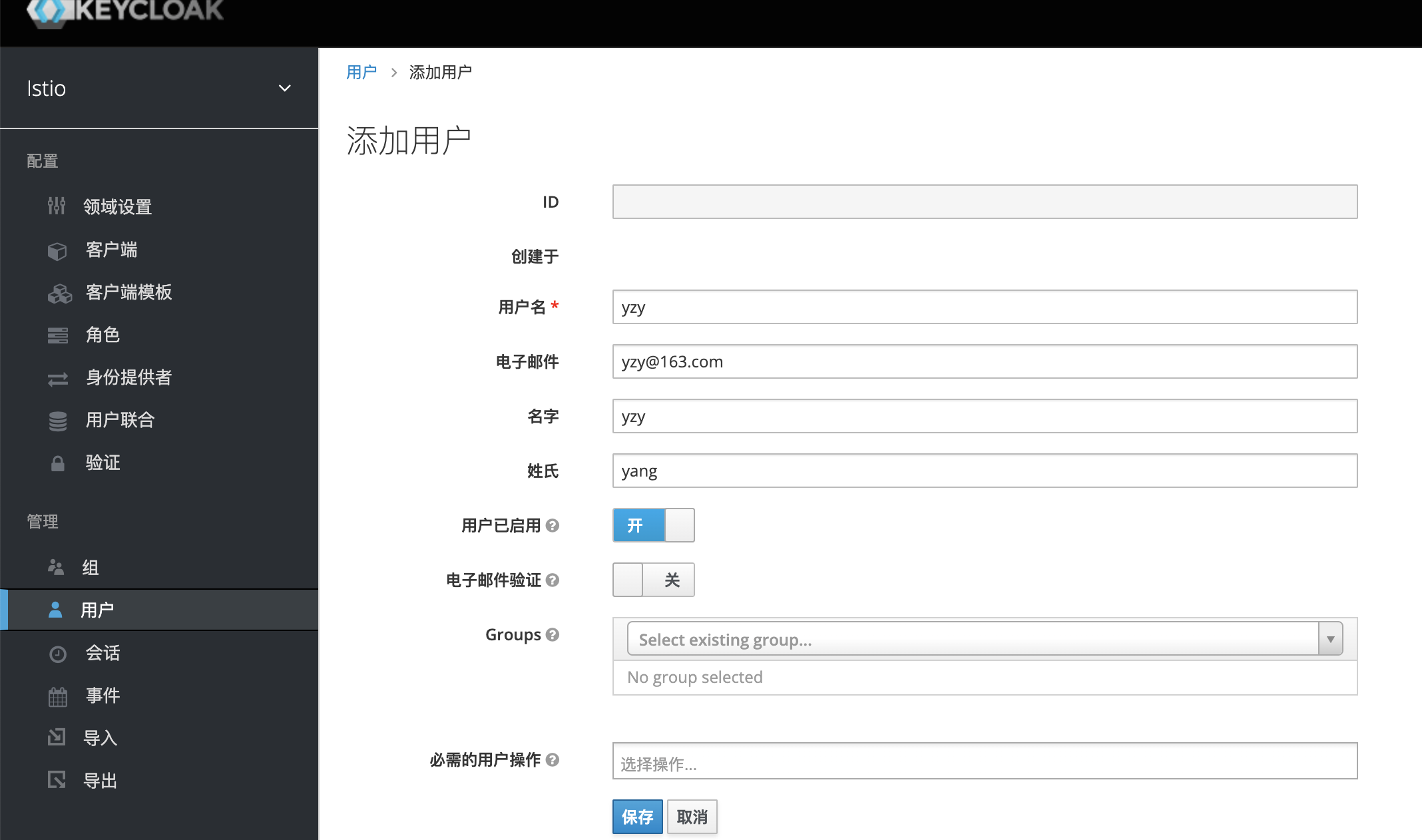
设置密码
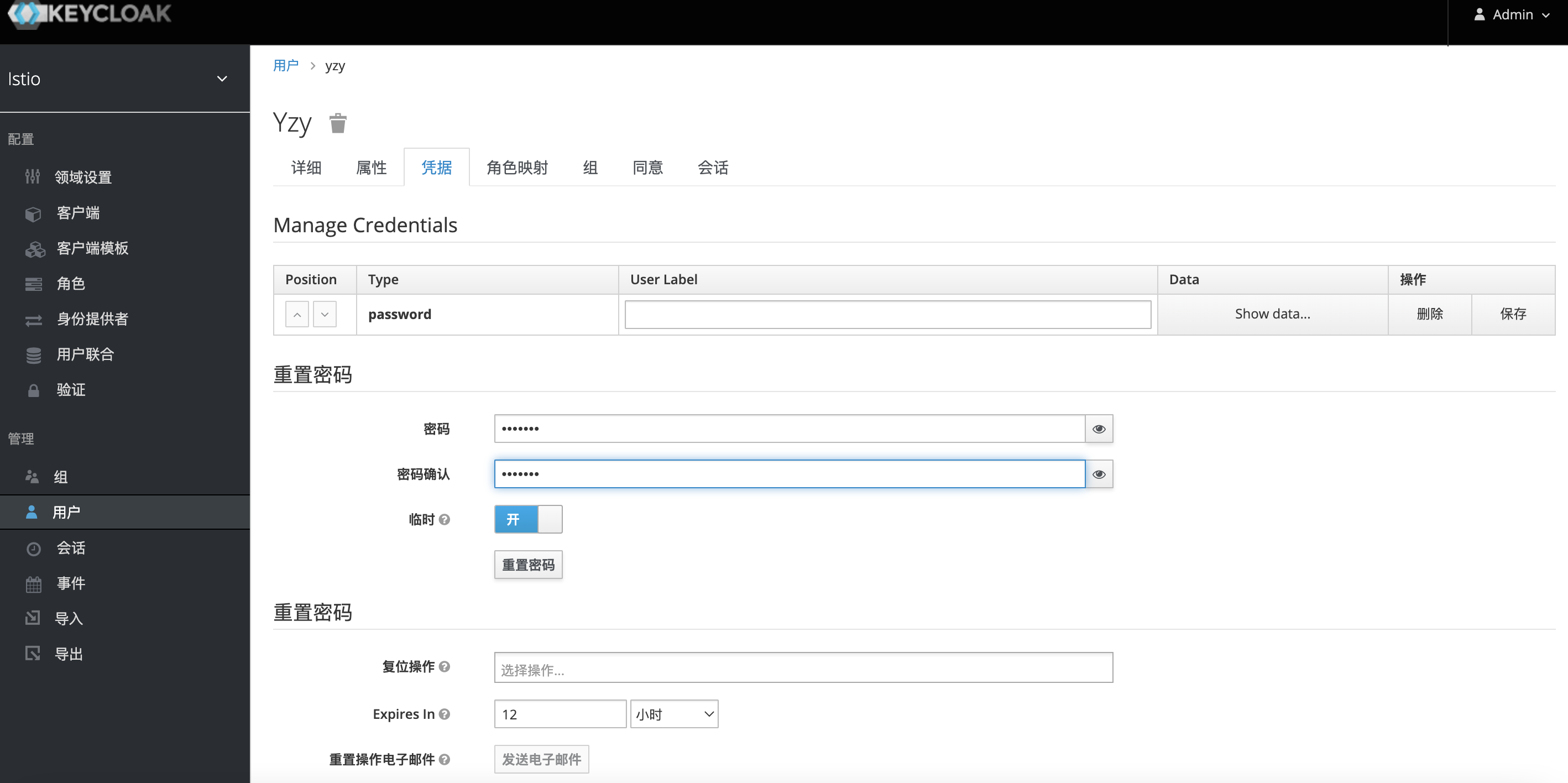
测试获取用户的token
[root@k8s-master ~]# kubectl exec -it sleep-698cfc4445-p84t6 -- /bin/sh
$ curl -sS -d "username=yzy&password=yzy.com&grant_type=password&client_id=istio" http://keycloak.keycloak.svc.cl
uster.local:8080/auth/realms/istio/protocol/openid-connect/token
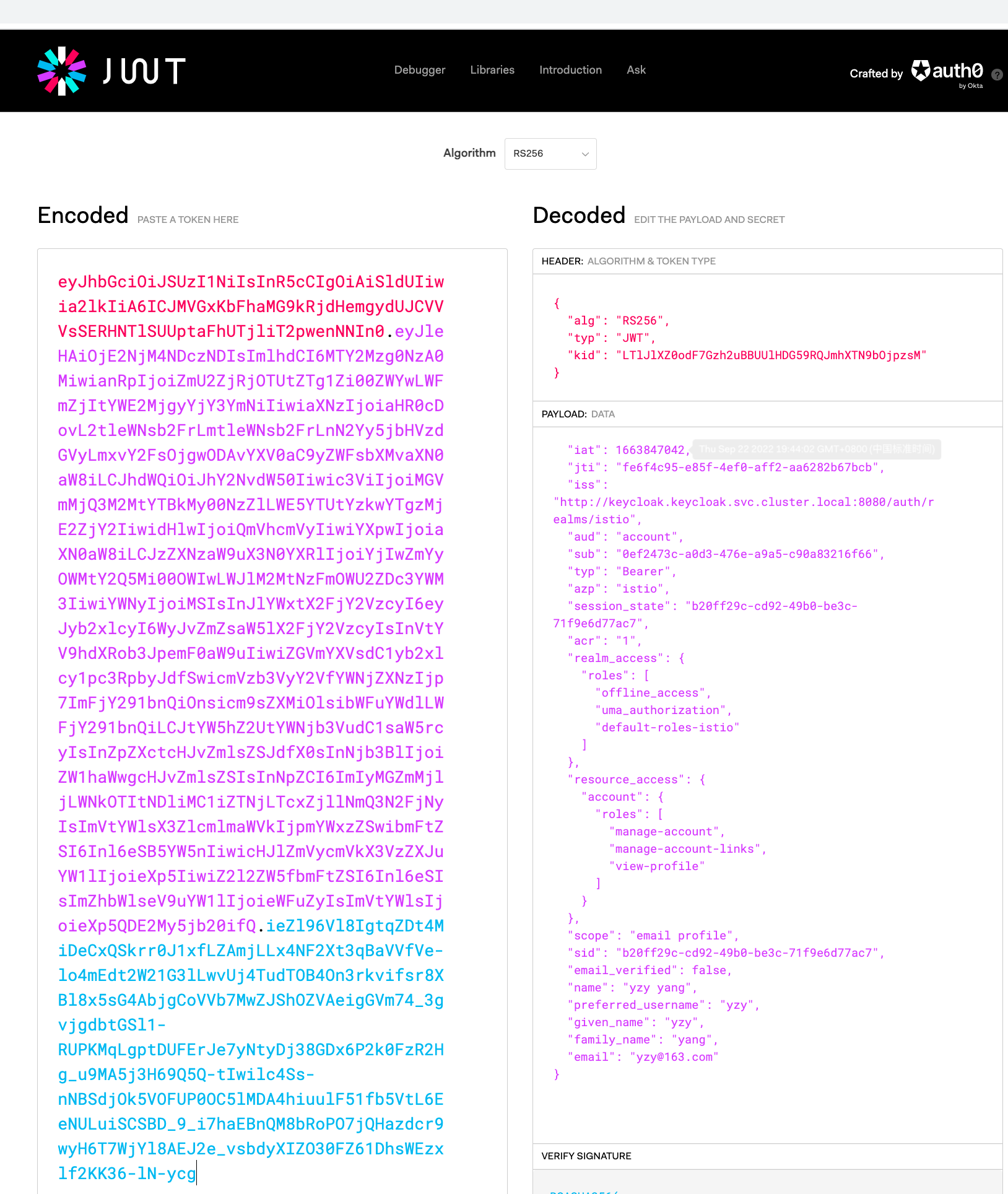
访问json2yaml.com,把获取的token复制到json框中转成yaml的格式
访问jwt.io
把access_token段复制到encoded中可以看到详细信息
[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# kubectl apply -f 02-requestauthn-policy.yaml
requestauthentication.security.istio.io/demoapp created
authorizationpolicy.security.istio.io/demoapp created使用sleep访问demoapp,再把规则删除,再次访问是可以访问到的
[root@k8s-master ~]# kubectl exec -it sleep-698cfc4445-p84t6 -- /bin/sh
/ $ curl demoapp:8080
RBAC: access denied/ $
/ $
[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# kubectl delete -f 02-requestauthn-policy.yaml
requestauthentication.security.istio.io "demoapp" deleted
authorizationpolicy.security.istio.io "demoapp" deleted
[root@k8s-master ~]# kubectl exec -it sleep-698cfc4445-p84t6 -- /bin/sh
/ $ curl demoapp:8080
iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-b5d9576cc-5hx8d, ServerIP: 10.244.169.150!
/ $再次创建规则,请求的时候添加access_token
[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# cat 02-requestauthn-policy.yaml
apiVersion: security.istio.io/v1beta1
kind: RequestAuthentication
metadata:
name: demoapp
namespace: default
spec:
selector:
matchLabels:
app: demoapp
jwtRules:
- issuer: "http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio"
jwksUri: "http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio/protocol/openid-connect/certs"
---
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: demoapp
namespace: default
spec:
selector:
matchLabels:
app: demoapp
rules:
- from:
- source:
requestPrincipals: ["*"]
to:
- operation:
methods: ["GET"]
paths: ["/*"][root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# kubectl apply -f 02-requestauthn-policy.yaml
requestauthentication.security.istio.io/demoapp created
authorizationpolicy.security.istio.io/demoapp created
[root@k8s-master ~]# kubectl exec -it sleep-698cfc4445-p84t6 -- /bin/sh
/$ curl -H "Authorization: Bearer eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJMVGxKbFhaMG9kRjdHemgydUJCVVVs
SERHNTlSUUptaFhUTjliT2pwenNNIn0.eyJleHAiOjE2NjM4NTAwMDgsImlhdCI6MTY2Mzg0OTcwOCwianRpIjoiZWVmYmVjMTEtNjEwZS00MzU4LTk
1NGEtMjY1MGFlNTdkOTFhIiwiaXNzIjoiaHR0cDovL2tleWNsb2FrLmtleWNsb2FrLnN2Yy5jbHVzdGVyLmxvY2FsOjgwODAvYXV0aC9yZWFsbXMvaX
N0aW8iLCJhdWQiOiJhY2NvdW50Iiwic3ViIjoiMGVmMjQ3M2MtYTBkMy00NzZlLWE5YTUtYzkwYTgzMjE2ZjY2IiwidHlwIjoiQmVhcmVyIiwiYXpwI
joiaXN0aW8iLCJzZXNzaW9uX3N0YXRlIjoiMTgwMTQzZTgtZjNlYi00NDQwLTgyYTUtY2FlNjNmNmQwMzcyIiwiYWNyIjoiMSIsInJlYWxtX2FjY2Vz
cyI6eyJyb2xlcyI6WyJvZmZsaW5lX2FjY2VzcyIsInVtYV9hdXRob3JpemF0aW9uIiwiZGVmYXVsdC1yb2xlcy1pc3RpbyJdfSwicmVzb3VyY2VfYWN
jZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sIn
Njb3BlIjoiZW1haWwgcHJvZmlsZSIsInNpZCI6IjE4MDE0M2U4LWYzZWItNDQ0MC04MmE1LWNhZTYzZjZkMDM3MiIsImVtYWlsX3ZlcmlmaWVkIjpmY
WxzZSwibmFtZSI6Inl6eSB5YW5nIiwicHJlZmVycmVkX3VzZXJuYW1lIjoieXp5IiwiZ2l2ZW5fbmFtZSI6Inl6eSIsImZhbWlseV9uYW1lIjoieWFu
ZyIsImVtYWlsIjoieXp5QDE2My5jb20ifQ.cbGtbm5c6w3M_CkB91Yx4XVbVaHmyX4W0FiOTzIHO_lqBvZDpEKAoyCwyRRnWPnbPq5RzFEZGLXX07j3
Wg7lzzLv20QUxXaVqLV0Nygx78RDfGmSQq0NHsAeXLj11PKmKYx52MEgqtu2CP9-SsfQVFYdzjjG-arVHwFwm18bOqZ6xKFn42dGdiaDmtdAsxy5VdZ
GmsCc-QmBRLtV-qWut2D2GKpk6AxZVketRnt2KDHozkxN9zFuplqt8U52fpQQey30c7v-2ZEPf5T03g7rqR-IQdBEB6k7gc-JcZNeun2fsdp7PXeCmn
h0LjbSYV4pynsWxvQy9cijdyFRVhiIZw" demoapp:8080
iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-b5d9576cc-f6fpb, ServerIP: 10.244.169.152!
/ $创建第三个规则
[root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# cat 03-request-and-peer-authn-policy.yaml
apiVersion: security.istio.io/v1beta1
kind: RequestAuthentication
metadata:
name: demoapp
namespace: default
spec:
selector:
matchLabels:
app: demoapp
jwtRules:
- issuer: "http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio"
jwksUri: "http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio/protocol/openid-connect/certs"
---
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: demoapp
namespace: default
spec:
selector:
matchLabels:
app: demoapp
rules:
- from:
- source:
principals: ["cluster.local/ns/default/sa/default"]
- source:
namespaces: ["default", "dev", "istio-system"]
to:
- operation:
methods: ["GET"]
paths: ["/*"]
- from:
- source:
requestPrincipals: ["*"]
principals: ["cluster.local/ns/default/sa/default"]
to:
- operation:
methods: ["POST"]
paths: ["/livez", "/readyz"]
when:
- key: request.auth.claims[iss]
values: ["http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio"][root@k8s-master 04-RequestAuthn-and-AuthzPolicy]# kubectl apply -f 03-request-and-peer-authn-policy.yaml
requestauthentication.security.istio.io/demoapp created
authorizationpolicy.security.istio.io/demoapp created
[root@k8s-master ~]# kubectl exec -it sleep-698cfc4445-p84t6 -- /bin/sh
/ $ TOKEN=eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJMVGxKbFhaMG9kRjdHemgydUJCVVVsSERHNTlSUUptaFhUTjliT2pwe
nNNIn0.eyJleHAiOjE2NjM4NTA4MzEsImlhdCI6MTY2Mzg1MDUzMSwianRpIjoiMGIwZGVmN2EtN2NhOS00YmZjLTk1NGUtODc1YWM5NjM1ZmM4Iiwi
aXNzIjoiaHR0cDovL2tleWNsb2FrLmtleWNsb2FrLnN2Yy5jbHVzdGVyLmxvY2FsOjgwODAvYXV0aC9yZWFsbXMvaXN0aW8iLCJhdWQiOiJhY2NvdW5
0Iiwic3ViIjoiMGVmMjQ3M2MtYTBkMy00NzZlLWE5YTUtYzkwYTgzMjE2ZjY2IiwidHlwIjoiQmVhcmVyIiwiYXpwIjoiaXN0aW8iLCJzZXNzaW9uX3
N0YXRlIjoiMmRkZWQ3OTAtNDQ2ZC00OGJhLWFhOTktZDRjM2NlYjE5NmViIiwiYWNyIjoiMSIsInJlYWxtX2FjY2VzcyI6eyJyb2xlcyI6WyJvZmZsa
W5lX2FjY2VzcyIsInVtYV9hdXRob3JpemF0aW9uIiwiZGVmYXVsdC1yb2xlcy1pc3RpbyJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsi
cm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sInNjb3BlIjoiZW1haWwgcHJvZml
sZSIsInNpZCI6IjJkZGVkNzkwLTQ0NmQtNDhiYS1hYTk5LWQ0YzNjZWIxOTZlYiIsImVtYWlsX3ZlcmlmaWVkIjpmYWxzZSwibmFtZSI6Inl6eSB5YW
5nIiwicHJlZmVycmVkX3VzZXJuYW1lIjoieXp5IiwiZ2l2ZW5fbmFtZSI6Inl6eSIsImZhbWlseV9uYW1lIjoieWFuZyIsImVtYWlsIjoieXp5QDE2M
y5jb20ifQ.RsnUKLr2Rcp7yYrp7Kr-HsvVwCDtbK0ZdHLAunguj2JmOaz3HRip_f72DiGd3IsC6bN_WurAbrJpsRepX_SXO_hSz_OT_8VFucHg2RVZs
e-UGi1LpIhQdjAaBstur85JZSEOxsKfHb4XfSDmB-mJoOl-nyPmvR16EnO6BQd7Kyygdhmrto9nFkM1NH5CcEpacPW-RYciKxf_E1vINyLeMPk5rJ0f
hJnh42WcFmBfGC04DNpbE5BsnsVbyoO_ifQn-2nQgIxTze7_OfcpQfxr1MDW_yRQQx2zDJ-OyWoMRPBx7DRRaq5Yc1FT09qL5OI1JMeBAiMsSJV-H4k
bDWMQrQ
/ $ curl -H "Authorization: Bearer $TOKEN" demoapp:8080
iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-b5d9576cc-npbj2, ServerIP: 10.244.36.124!
/ $ curl -H "Authorization: Bearer $TOKEN" demoapp:8080
iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-b5d9576cc-npbj2, ServerIP: 10.244.36.124!
/ $ curl -H "Authorization: Bearer $TOKEN" demoapp:8080
iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-b5d9576cc-npbj2, ServerIP: 10.244.36.124!
/ $ curl demoapp:8080 #默认在default ns下符合第一个规则GET是可以访问的
iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-b5d9576cc-f6fpb, ServerIP: 10.244.169.152!
/ $ curl -XPOST -d 'livez=FAIL' demoapp:8080/livez
RBAC: access denied/ $我们使用demoappv11进行测试
使用POST方法进行测试
[root@k8s-master ~]# kubectl exec -it demoappv11-77755cdc65-6prmq -- /bin/sh
[root@demoappv11-77755cdc65-6prmq /]# apk add jq
[root@demoappv11-77755cdc65-6prmq /]# curl -sS -d "username=yzy&password=yzy.com&grant_type=password&client_id=isti
o" http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio/protocol/openid-connect/token | jq .access_tok
en
[root@demoappv11-77755cdc65-6prmq /]# TOKEN=$(curl -sS -d "username=yzy&password=yzy.com&grant_type=password&client
_id=istio" http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio/protocol/openid-connect/token | jq .ac
cess_token)
[root@demoappv11-77755cdc65-6prmq /]# curl -XPOST -d 'livez=FAIL' -H "Authorization: Bearer $TOKEN" demoapp:8080/li
vez



