2023FSCTF-部分wp
Web
源码!启动!
开启环境
发现右键被禁用view-source:访问环境查看源码
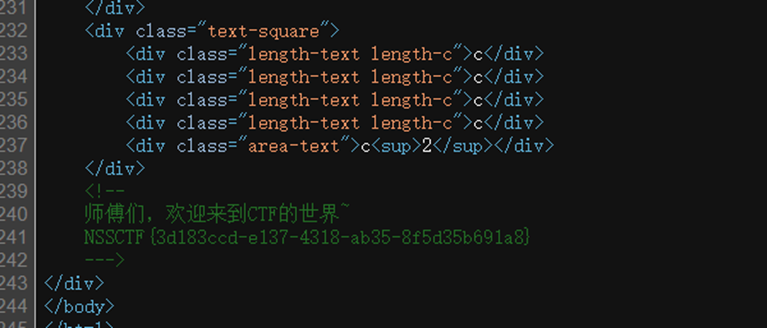
NSSCTF{3d183ccd-e137-4318-ab35-8f5d35b691a8}
webshell是啥捏
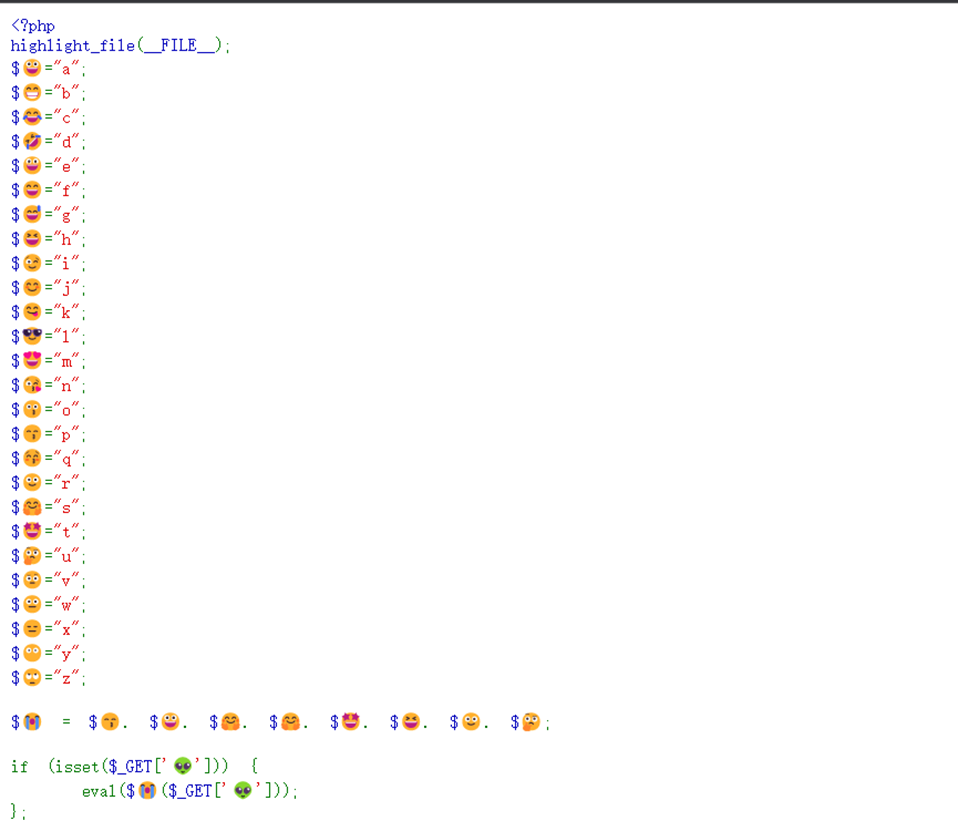
GET传参👽这个外星人直接执行命令
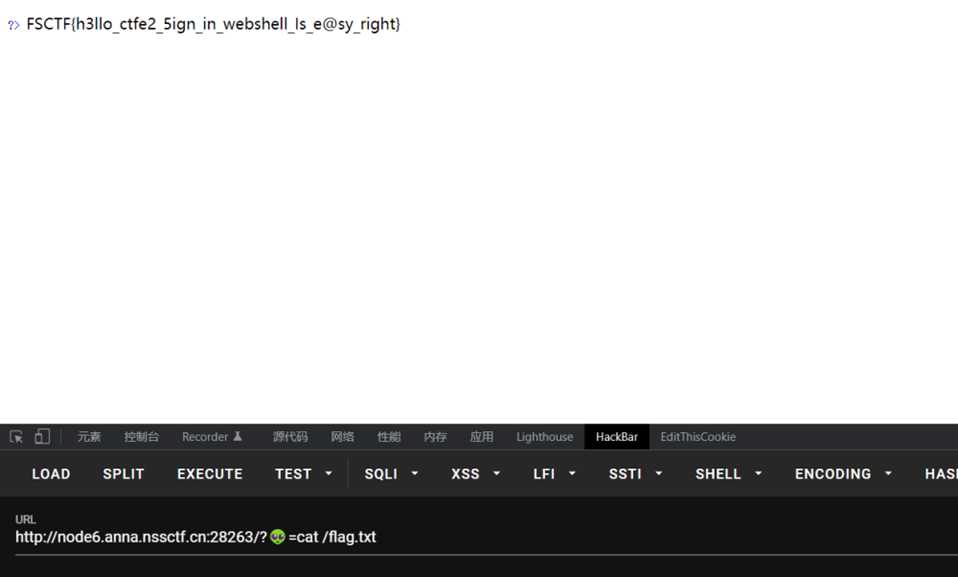
FSCTF{h3llo_ctfe2_5ign_in_webshell_Is_e@sy_right}
Crypto
做不出来就别阴阳怪气啦
题目描述很明确直接阴阳怪气解码梭哈
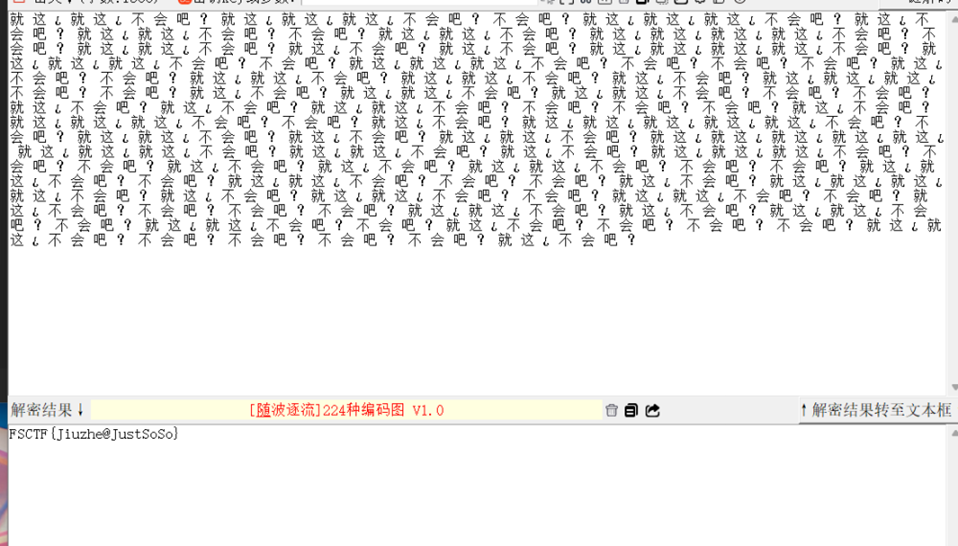
FSCTF{Jiuzhe@JustSoSo}
RSA 1

题目上说flag是d,不会rsa,搜了一下网上的文章https://www.bilibili.com/read/cv13392301/
条件都满足直接输出d提交即可
点击查看代码
import gmpy2
import libnum
p=1458769258361
q=4556983871563
e=17
n=p*q
phi_n=(p-1)*(q-1)
#求逆元
#d=libnum.invmod(e,phi_n)
d=gmpy2.invert(e,phi_n)
print(d)
FSCTF{5865518808244394324786753}
RSA 2
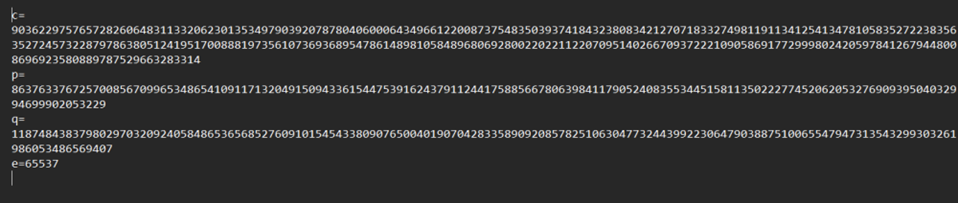
条件都够直接梭哈,这里使用spmonky的工具直接跑即可
工具地址:https://github.com/spmonkey/Crypto
n的话用python算一下p*q就能得到了
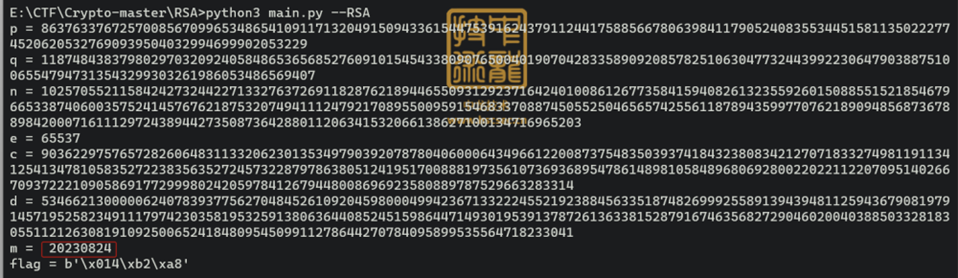
FSCTF{20230824}
RSA 3
很明显的dp泄露,套用风二西师傅的脚本就可以直接梭哈出结果
点击查看代码
import gmpy2
import libnum
n= 12308543373374311860115195114269947739026255098864232126071500623399852788903738569949462616714391748269539072128882946132686996592089735285396762634029371785959865779256901123369306119124563405765293657606975290441243965513640680841871955014230301486214824204887945375140818283280272607903500556306646445508386218951500563603482945071727344737690804338144982687000734071274618240408238519378280819162796749148066754028700125846348589164721591354555019608871411236973606149388257533629388508942271702742078883636357856776193846813894734271905070538713351614750057245897158615891962167410053552739441195871000310777649
e= 65537
c= 1855798257044238280327042455832785889763141234883180404158555071443088630113034033050409259513632343742665544043437830959750873431928980910236398026670945184328950692568113819821699696418438157336263799808404698795433243968536256780396910914692949484556950491722527661706255009863481905590371725089587377065000354109396062360440021447607401687082247775453369117424848927386857425051097931983703966253652921113920387008048024308793686643944404541941182997963873579988680965558581885273185721576668001462817150245955628293258512024323515581063235248627223179117549540541642185815489978089367061102920114395871329023208
dp= 28196759050232165736649945458463681080421101473761579424309687746007021074159564720195299959516638110870101025657932732247788828322476803386736345945717104030991724584628153257976163663460034720811420324255626233108130037584679035250792445830510130682783638394418531763109219293027733347554816808577799709553
p=gmpy2.gcd(pow(2,e*dp,n)-2,n)
print(p)
for i in range(1, e):
p = (dp * e - 1) // i + 1
if n % p == 0:
q = n // p
print(p)
break
phi_n = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi_n)
m = pow(c, d, n)
print(m)
flag = libnum.n2s(int(m))
print(flag)
FSCTF{Cheese_snow_1eop@rd}
埃塞克的秘密
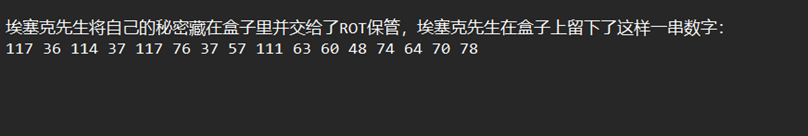
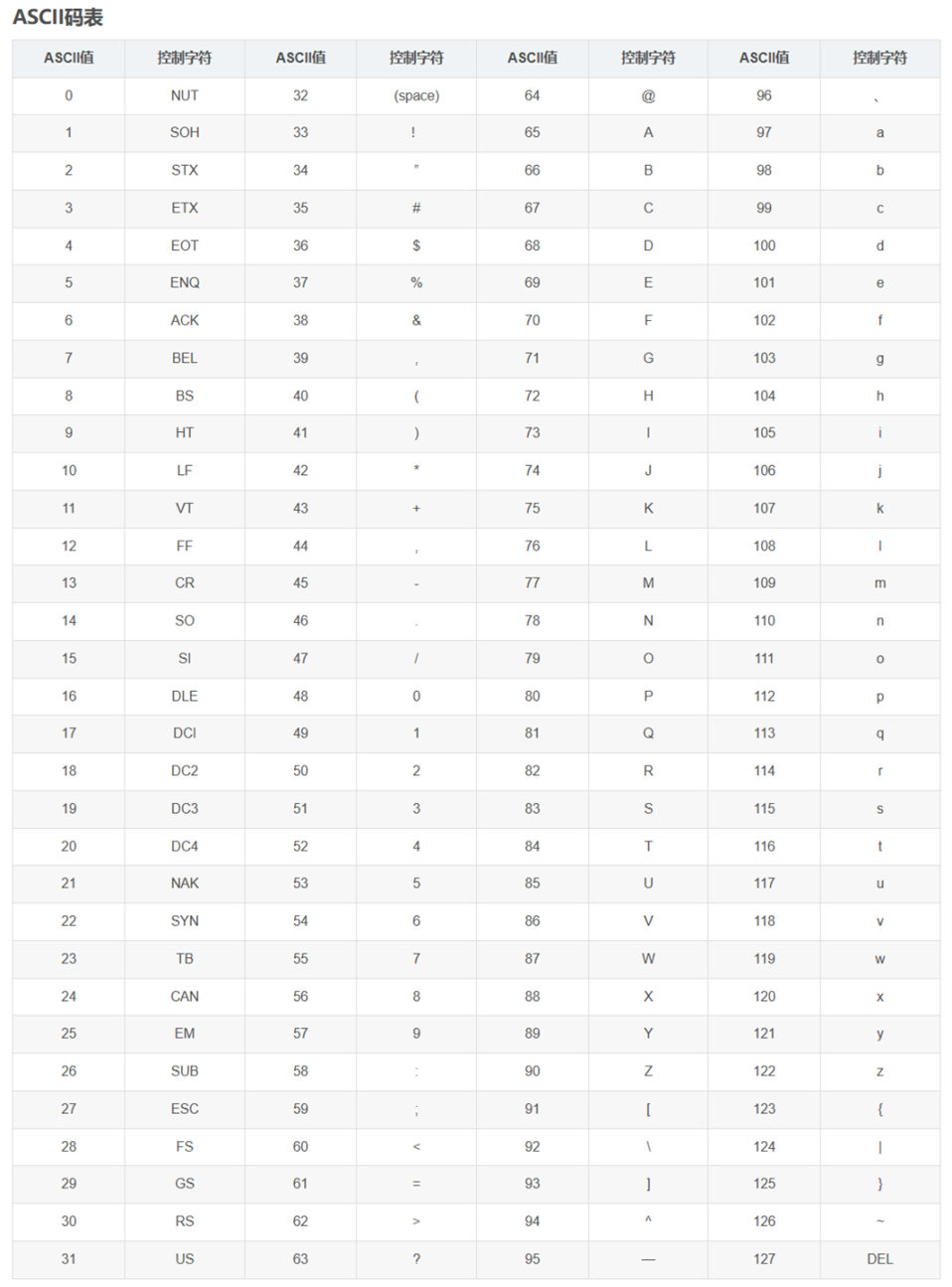
对着表一个一个找
u$r%uL%9o?<0J@FN
rot解码一个一个试,rot47
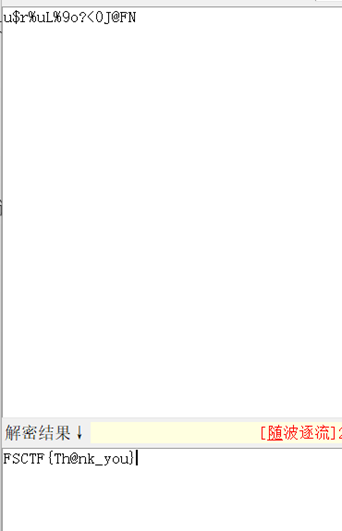
FSCTF{Th@nk_you}
Big_e
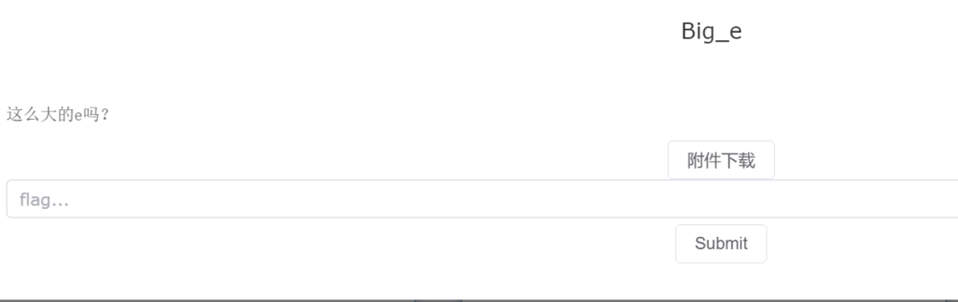
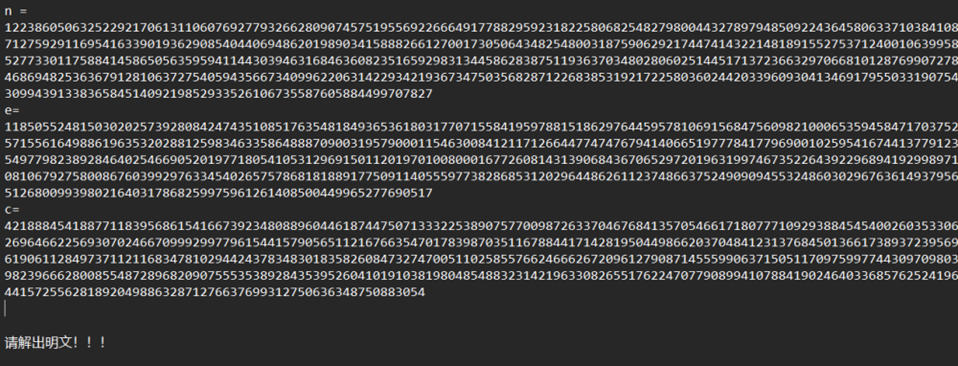
低解密指数攻击
工具地址:
https://github.com/pablocelayes/rsa-wiener-attack
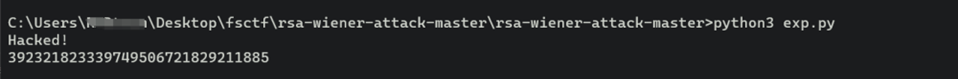
要把exp.py放到同一目录下
点击查看代码
import RSAwienerHacker
n = 12238605063252292170613110607692779326628090745751955692266649177882959231822580682548279800443278979485092243645806337103841086023159482786712759291169541633901936290854044069486201989034158882661270017305064348254800318759062921744741432214818915527537124001063995865927527037625277330117588414586505635959411443039463168463608235165929831344586283875119363703480280602514451713723663297066810128769907278246434745483846869482536367912810637275405943566734099622063142293421936734750356828712268385319217225803602442033960930413469179550331907541244416573641309943913383658451409219852933526106735587605884499707827
e = 11850552481503020257392808424743510851763548184936536180317707155841959788151862976445957810691568475609821000653594584717037528429828330763571556164988619635320288125983463358648887090031957900011546300841211712664477474767941406651977784177969001025954167441377912326806132232375497798238928464025466905201977180541053129691501120197010080001677260814313906843670652972019631997467352264392296894192998971542816081534808106792758008676039929763345402657578681818891775091140555977382868531202964486261123748663752490909455324860302967636149379567988941803701512680099398021640317868259975961261408500449965277690517
d = RSAwienerHacker.hack_RSA(e,n)
if d:
print(d)
就可以解出d了,后面就简单了
也可以直接费马分解n之后,直接用spmonkey师傅的工具梭哈
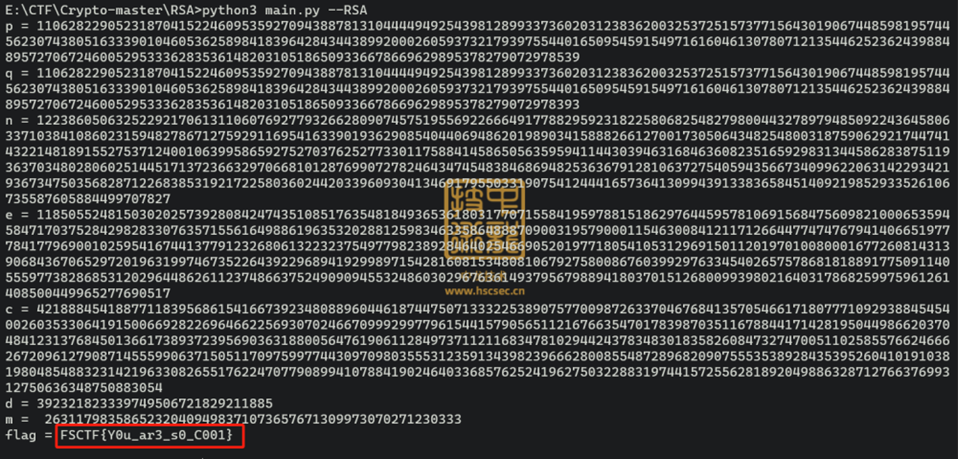
RSA签到
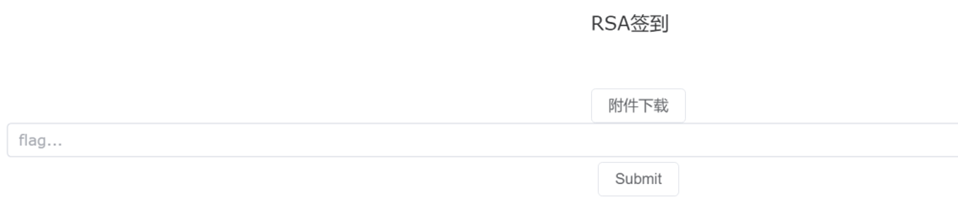
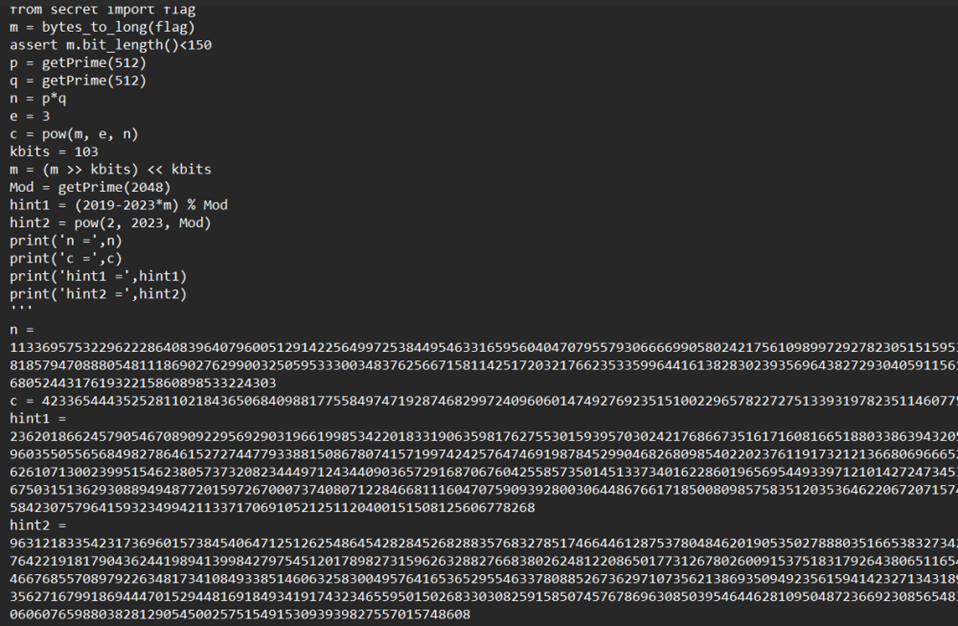
很明显e很短,低加密指数攻击
点击查看代码
import libnum
import gmpy2
n = 113369575322962228640839640796005129142256499725384495463316595604047079557930666699058024217561098997292782305151595366764483672240871690818579470888054811186902762990032505953330034837625667158114251720321766235335996441613828302393569643827293040591156144187232255906107532680524431761932215860898533224303
e = 3
c = 42336544435252811021843650684098817755849747192874682997240960601474927692351510022965782272751339319782351146077580929125
def exp(n, e, c):
k = 0
while 1:
m1 = k * n + c
m, t = gmpy2.iroot(m1, e)
if t:
print(m)
print(k)
print(libnum.n2s(int(m)))
break
k += 1
exp(n, e, c)

flag{sign_1n_RSA}
Do you know gcd?
直接套脚本

https://blog.csdn.net/bunner_/article/details/109198214
点击查看代码
import gmpy2
def get_p(n1, n2):
p = gmpy2.gcd(n1, n2)
assert gmpy2.is_prime(p) == True
return p
def int_str(data):
flag = ''
while data:
flag += chr(data & 0xff)
data >>= 8
return flag[::-1]
if __name__ == "__main__":
n1 = 18680935400842120133090782991548100098299141114788036098274292600814484762178879421175852824971602717084073867867453382415307589970440719890918576225495401632854107018246844209327118177917122236073227158593514362850629722223228335334773008682775987859295083444638923726449899310854161394586430943134469559429878238769266114132469166535509030877235272476877484918308883799496627699789051809542538091061550107526246728583019140703765888157806778516567048103700384849598143249322109207879381251223776896702362630437178664824125387477797876186939235800859102380783259361745143574493440078787931593394188675093506492640857
n2 = 16308523133405725830120564525574438512803584148781960516042054284309437381876822602134185065101371986717984978566359252072738078020261823966208153922611063201149105749778596739692554295573408850719208215646167050188830459343054219856901871953140988948482577813730729085764541988120049026971705499798003225755018687242522370406495429425494022876627543617474873929054728724093702291448754458748923218635900061398716191201846139296921753782690468189409101899415028480878296408735247604084627019116374444335509072590669239349212479592499426230525792270750612371117196200786891891430446212938482959351978202358044864822577
c1 = 534518909595318304521410713148076850830155521838755402438490325620155197496935820831936109252194297244161393310730073882257949954815312409974998733265641354273665213856408848764503848122264972023143474923678585167025591255034150826271791019266426616987355463111138963331008761826310757292765842789380409826387579098421126952331558360737102888876551724241978020305977032047901621477384392409864427091911872691182528938458750707982564581322551517287491916691010743390992018974168703956622998928457142606354825714033609199676987795174032254878017883605565760275857658822315970522114838062469258676628619381342357632179
c2 = 10248394002302905069278122013496854496130190499518622376819239887579692634750808499513497018453473232140518824608976734237637842228035017757831938865937098325684711995382081489403971465596662585196007547659143066184546400992333479193424580690897692586491475768279754939199148642035267049092880715299621206567123356521609120801306358100326600900326310677054810032471472266402660807205675696110133573150125117412696328434523507708110949743705536889950671778501402435457354251761692098671783596194430798692942013503015764266392551048702428063161786512924608239609802040937400619384828550050291094616346317726139970219621
e = 65537
p = get_p(n1, n2)
q1 = n1 // p
q2 = n2 // p
d1 = gmpy2.invert(e, (p - 1) * (q1 - 1))
d2 = gmpy2.invert(e, (p - 1) * (q2 - 1))
m1 = gmpy2.powmod(c1, d1, n1)
m2 = gmpy2.powmod(c2, d2, n2)
print(int_str(m1) + int_str(m2))
MISC
Simple Encryption
下载附件之后,解压发现有密码,选择7z解压可以无视伪加密等
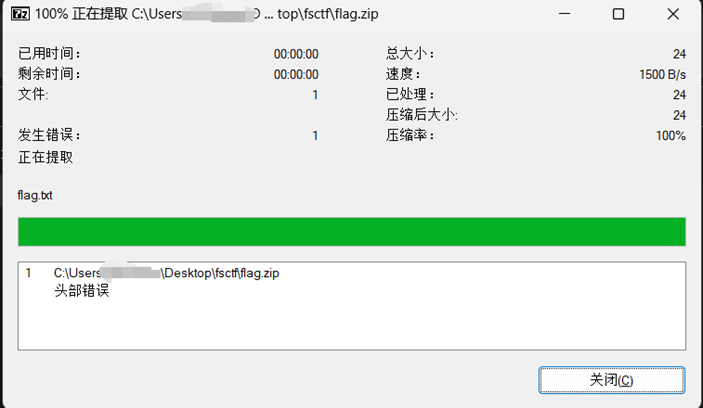
发现是头部错误已经提取出来了
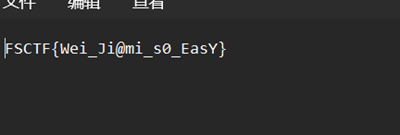
FSCTF{Wei_Ji@mi_s0_EasY}
萧河
根据题目提示补全图片头
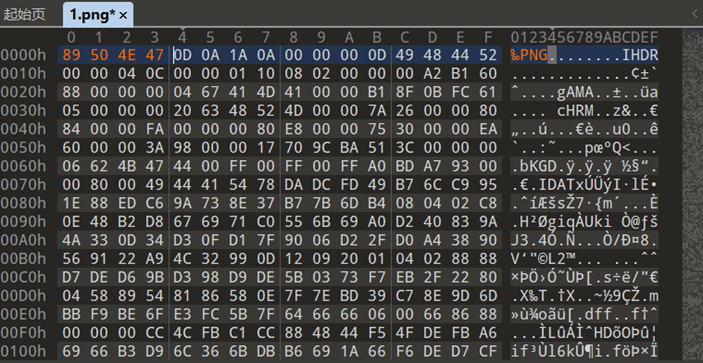
打开明显发现高度不够,p神工具梭哈
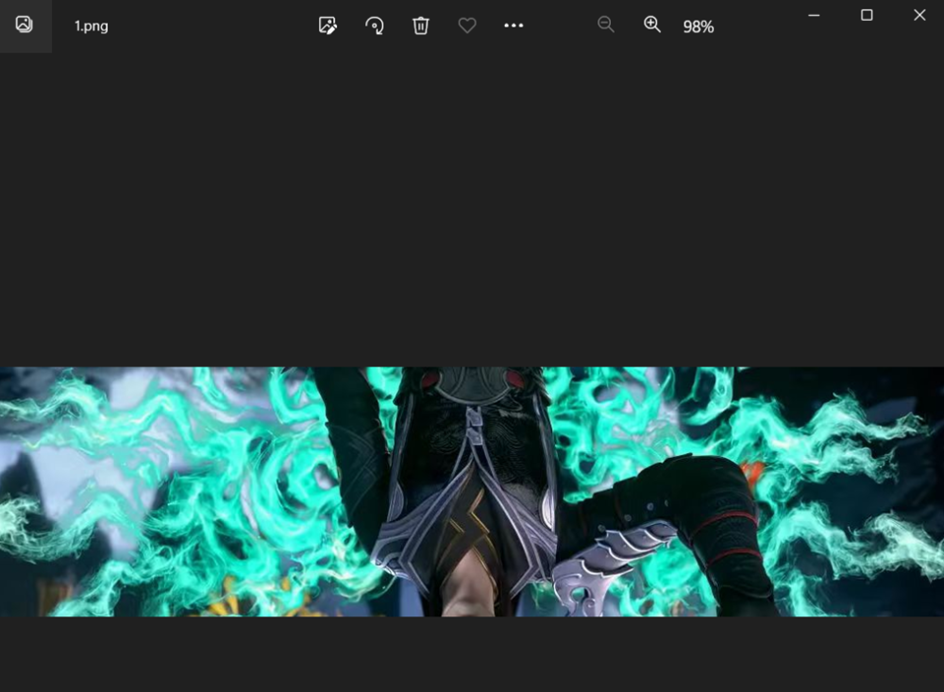

转个方向就好了

FSCTF{xiaojia_xiaohe}
为什么不换换思路捏

提示有反转,先看题目
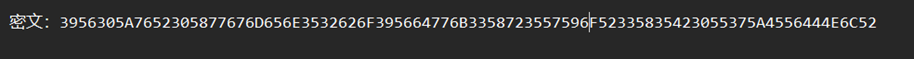
base16
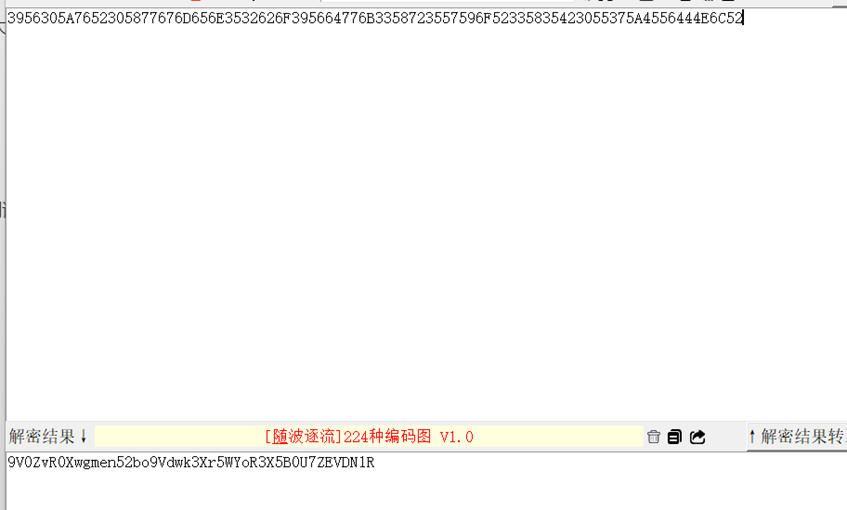
将结果反转
RlNDVEZ7U0B5X3RoYW5rX3kwdV9ob25nemgwX0RvZ0V9
反转之后base64解码

FSCTF{S@y_thank_y0u_hongzh0_DogE}
Reverse
MINE SWEEPER
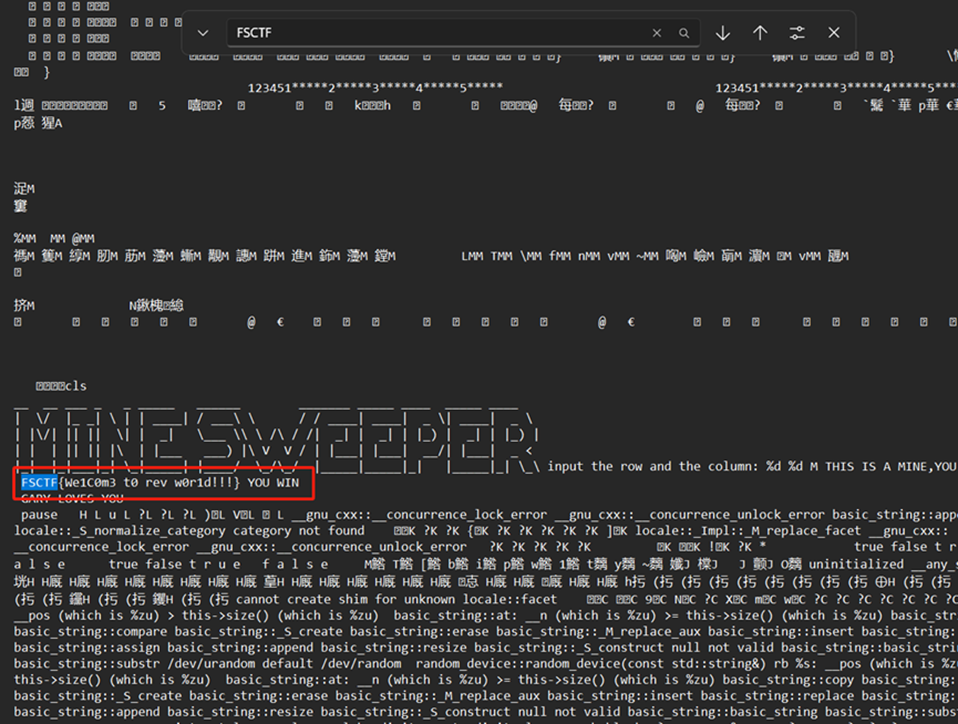
下好之后直接记事本打开搜索FSCTF
FSCTF{We1C0m3 t0 rev w0r1d!!!}
ez_pycxor
网站反编译
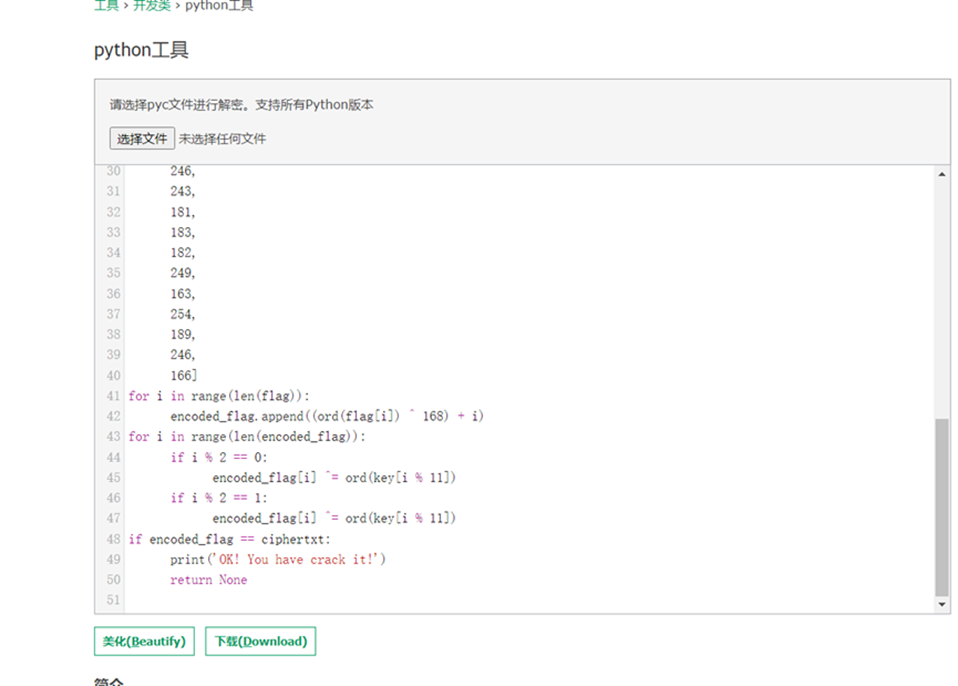
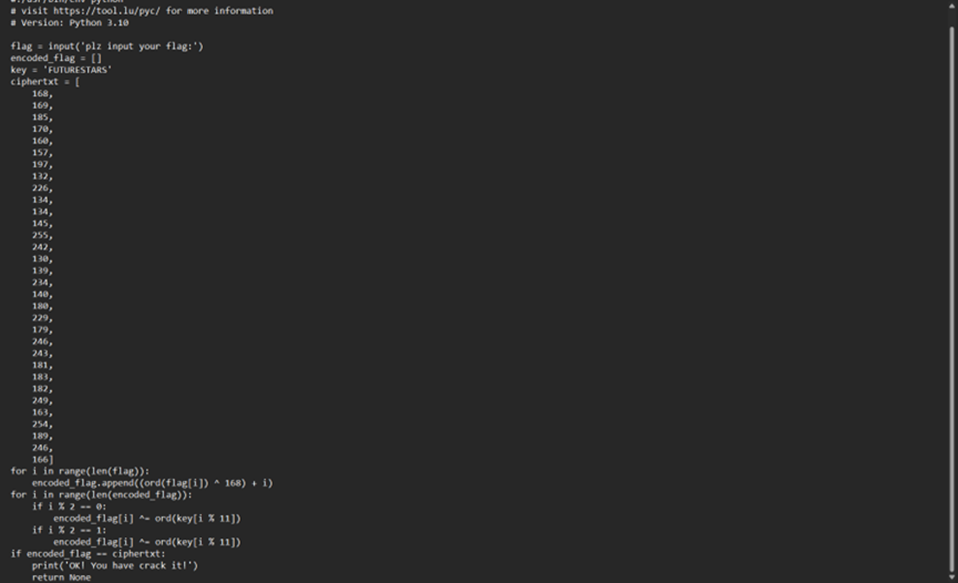
是一个异或
点击查看代码
key = 'FUTURESTARS'
ciphertxt = [168,169,185,170,160,157,197,132,226,134,134,145,255,242,130,139,234,140,180,229,179,246,243,181,183,182,249,163,254,189,246,166]
encoded_flag = []
flag = []
for i in range(len(ciphertxt)):
if i % 2 == 0:
ciphertxt[i] ^= ord(key[i % 11])
if i % 2 == 1:
ciphertxt[i] ^= ord(key[i % 11])
print(ciphertxt)
for i in range(len(ciphertxt)):
encoded_flag.append((ciphertxt[i] - i)^ 168)
print(encoded_flag)
for j in encoded_flag:
flag.append(chr(j))
print("".join(flag))
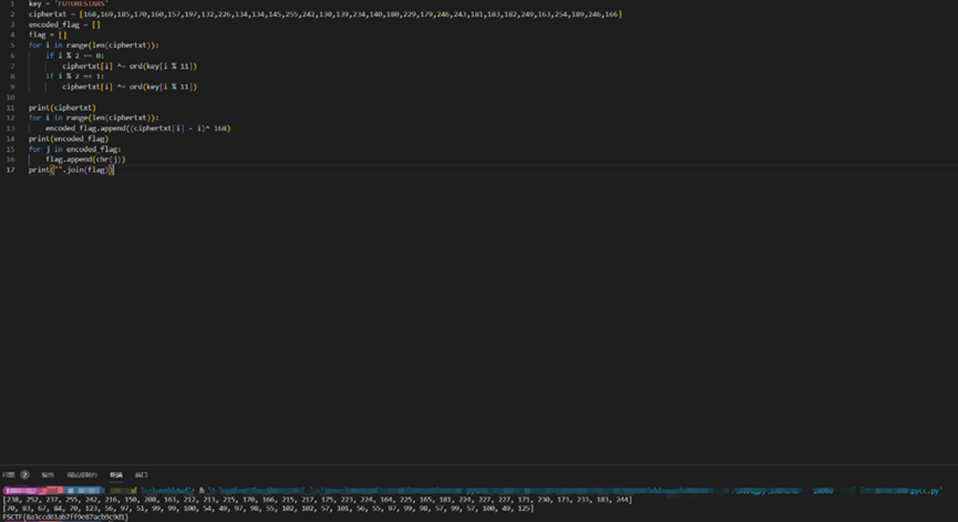
FSCTF{8a3ccd61ab7ff9e87acb9c9d1}
Xor
ida64打开然后查看main函数f5
发现异或
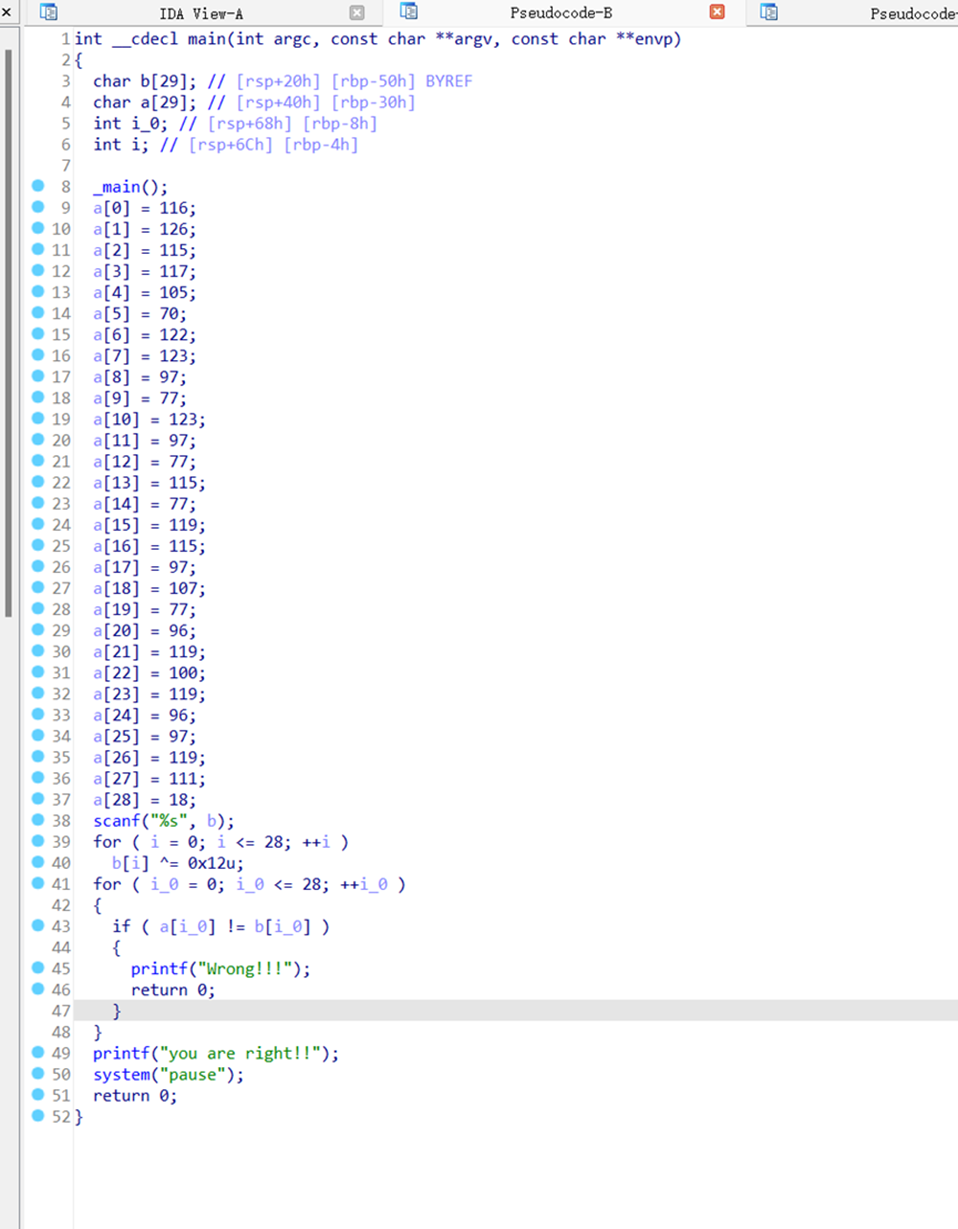
点击查看代码
ciphertxt = [116,126,115,117,105,70,122,123,97,77,123,97,77,115,77,119,115,97,107,77,96,119,100,119,96,97,119,111,18]
encoded_flag = []
flag = []
for i in range(len(ciphertxt)):
ciphertxt[i] ^= int("0x12", 16)
print(ciphertxt)
for j in ciphertxt:
flag.append(chr(j))
print("".join(flag))
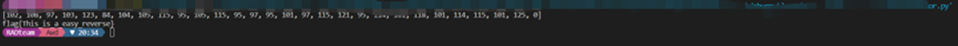
flag{This_is_a_easy_reverse}
本文作者:夜梓月
本文链接:https://www.cnblogs.com/zy4024/p/2023FSCTF_WP.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步