Configparser :
If you want get the data with this formation:
[DEFAULT]
ServerAliveInterval = 45
Compression = yes
CompressionLevel = 9
ForwardX11 = yes
[bitbucket.org]
User = hg
[topsecret.server.com]
Port = 50022
ForwardX11 = no
You can use Python to profile:

import configparser config = configparser.ConfigParser() config["DEFAULT"] = {'ServerAliveInterval': '45', 'Compression': 'yes', 'CompressionLevel': '9'} config['bitbucket.org'] = {} config['bitbucket.org']['User'] = 'hg' config['topsecret.server.com'] = {} topsecret = config['topsecret.server.com'] topsecret['Host Port'] = '50022' # mutates the parser topsecret['ForwardX11'] = 'no' # same here config['DEFAULT']['ForwardX11'] = 'yes'<br> with open('example.ini', 'w') as configfile: config.write(configfile)
The operation of the file:

import configparser config = configparser.ConfigParser() #---------------------------------------------查 print(config.sections()) #[] config.read('example.ini') print(config.sections()) #['bitbucket.org', 'topsecret.server.com'] print('bytebong.com' in config)# False print(config['bitbucket.org']['User']) # hg print(config['DEFAULT']['Compression']) #yes print(config['topsecret.server.com']['ForwardX11']) #no for key in config['bitbucket.org']: print(key) # user # serveraliveinterval # compression # compressionlevel # forwardx11 print(config.options('bitbucket.org'))#['user', 'serveraliveinterval', 'compression', 'compressionlevel', 'forwardx11'] print(config.items('bitbucket.org')) #[('serveraliveinterval', '45'), ('compression', 'yes'), ('compressionlevel', '9'), ('forwardx11', 'yes'), ('user', 'hg')] print(config.get('bitbucket.org','compression'))#yes #---------------------------------------------删,改,增(config.write(open('i.cfg', "w"))) config.add_section('yuan') config.remove_section('topsecret.server.com') config.remove_option('bitbucket.org','user') config.set('bitbucket.org','k1','11111') config.write(open('i.cfg', "w"))
Hashlib:
For encryption related operations, 3. X replaces MD5 module and Sha module, mainly providing SHA1, sha224, sha256, sha384, SHA512, MD5 algorithm:

import hashlib m=hashlib.md5()# m=hashlib.sha256() m.update('hello'.encode('utf8')) print(m.hexdigest()) #5d41402abc4b2a76b9719d911017c592 m.update('alvin'.encode('utf8')) print(m.hexdigest()) #92a7e713c30abbb0319fa07da2a5c4af m2=hashlib.md5() m2.update('helloalvin'.encode('utf8')) print(m2.hexdigest()) #92a7e713c30abbb0319fa07da2a5c4af
Add one self indentified key to enforce the safe of the key:

import hmac h = hmac.new('alvin'.encode('utf8')) h.update('hello'.encode('utf8')) print (h.hexdigest())#320df9832eab4c038b6c1d7ed73a5940
The supplement of re:
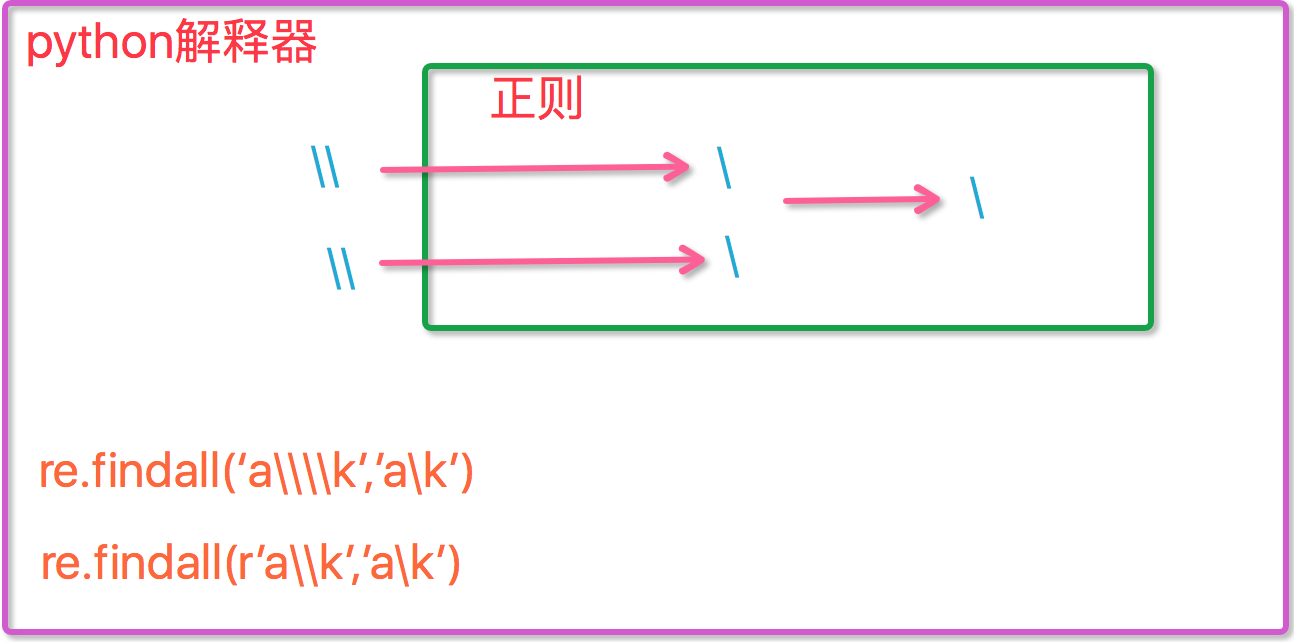
1:the use of "\"

1 #-----------------------------eg1: 2 import re 3 ret=re.findall('c\l','abc\le') 4 print(ret)#[] 5 ret=re.findall('c\\l','abc\le') 6 print(ret)#[] 7 ret=re.findall('c\\\\l','abc\le') 8 print(ret)#['c\\l'] 9 ret=re.findall(r'c\\l','abc\le') 10 print(ret)#['c\\l'] 11 12 #-----------------------------eg2: 13 #之所以选择\b是因为\b在ASCII表中是有意义的 14 m = re.findall('\bblow', 'blow') 15 print(m) 16 m = re.findall(r'\bblow', 'blow') 17 print(m)
metacharacters of grouping"()":

1 m = re.findall(r'(ad)+', 'add') 2 print(m) 3 4 ret=re.search('(?P<id>\d{2})/(?P<name>\w{3})','23/com') 5 print(ret.group())#23/com 6 print(ret.group('id'))#23
metacharacters of "|":

1 ret=re.search('(ab)|\d','rabhdg8sd') 2 print(ret.group())#ab
The usual use of re:

1 import re 2 #1 3 re.findall('a','alvin yuan') #返回所有满足匹配条件的结果,放在列表里 4 #2 5 re.search('a','alvin yuan').group() #函数会在字符串内查找模式匹配,只到找到第一个匹配然后返回一个包含匹配信息的对象,该对象可以 6 # 通过调用group()方法得到匹配的字符串,如果字符串没有匹配,则返回None。 7 8 #3 9 re.match('a','abc').group() #同search,不过尽在字符串开始处进行匹配 10 11 #4 12 ret=re.split('[ab]','abcd') #先按'a'分割得到''和'bcd',在对''和'bcd'分别按'b'分割 13 print(ret)#['', '', 'cd'] 14 15 #5 16 ret=re.sub('\d','abc','alvin5yuan6',1) 17 print(ret)#alvinabcyuan6 18 ret=re.subn('\d','abc','alvin5yuan6') 19 print(ret)#('alvinabcyuanabc', 2) 20 21 #6 22 obj=re.compile('\d{3}') 23 ret=obj.search('abc123eeee') 24 print(ret.group())#123
be iterable:

1 import re 2 ret=re.finditer('\d','ds3sy4784a') 3 print(ret) #<callable_iterator object at 0x10195f940> 4 5 print(next(ret).group()) 6 print(next(ret).group())
be careful:"?:"to dismiss the privilege:

1 import re 2 3 ret=re.findall('www.(baidu|oldboy).com','www.oldboy.com') 4 print(ret)#['oldboy'] 这是因为findall会优先把匹配结果组里内容返回,如果想要匹配结果,取消权限即可 5 6 ret=re.findall('www.(?:baidu|oldboy).com','www.oldboy.com') 7 print(ret)#['www.oldboy.com']
Supplement:

1 import re 2 3 print(re.findall("<(?P<tag_name>\w+)>\w+</(?P=tag_name)>","<h1>hello</h1>")) 4 print(re.search("<(?P<tag_name>\w+)>\w+</(?P=tag_name)>","<h1>hello</h1>")) 5 print(re.search(r"<(\w+)>\w+</\1>","<h1>hello</h1>")) 6 7 #匹配出所有的整数 8 import re 9 10 #ret=re.findall(r"\d+{0}]","1-2*(60+(-40.35/5)-(-4*3))") 11 ret=re.findall(r"-?\d+\.\d*|(-?\d+)","1-2*(60+(-40.35/5)-(-4*3))") 12 ret.remove("") 13 14 print(ret)



