Istio从入门到精通——介绍 Istio (version: 1.16.2, Jan 30, 2023发版)
介绍 Istio (version: 1.16.2, Jan 30, 2023发版)
https://istio.io/latest/
一、Istio 是什么?
https://istio.io/latest/about/service-mesh/
Istio is an open source service mesh that layers transparently onto existing distributed applications.
Istio 是一个透明地分层到现有分布式应用程序的开源服务网格。
Istio;s powerful features provide a uniform and more efficient way to secure, connect, and monitor services.
Istio 的强大功能为安全、连接和监视服务提供了一种统一且更有效的方法。
Istio is the path to load balancing, service-to-service authentication, and monitoring – with few or no service code changes.
Istio 是负载平衡、服务到服务身份验证和监视的路径——只需要很少或根本不需要更改服务代码。
Isito 这里的关键字 "治理" 不局限于 "微服务治理"的范畴,任何服务,只要服务间有访问,如果需要对服务间的访问进行管理,就可以使用 Istio。
Istio 的重要特点:
-
- Secure service-to-service communication in a cluster with TLS encryption, strong identity-based authentication and authorization.
(使用 TLS 加密、强大的基于身份的认证和授权的集群中的安全服务到服务通信。)
-
- Automatic load balancing for HTTP, gRPC, WebSocket, and TCP traffic.
(HTTP、 gRPC、 WebSocket 和 TCP 流量的自动负载平衡。)
-
- Fine-grained control of traffic behavior with rich routing rules, retries, failovers, and fault injection.
(具有丰富的路由规则、重试、故障转移和故障注入的流量行为的细粒度控制。)
-
- A pluggable policy layer and configuration API supporting access controls, rate limits and quotas.
(支持访问控制、速率限制和配额的可插入策略层和配置 API。)
-
- Automatic metrics, logs, and traces for all traffic within a cluster, including cluster ingress and egress.
(集群内所有流量的自动度量、日志和跟踪,包括集群入口和出口。)
Istio 是为可扩展性而设计的,可以处理各种各样的部署需求。
Istio 的控制平面运行在 Kubernetes 上,你可以将部署在该集群中的应用程序添加到网格中,将网格扩展到其他集群,甚至连接运行在 Kubernetes 以外的虚拟机或其他端点。
二、Istio是如何工作的?
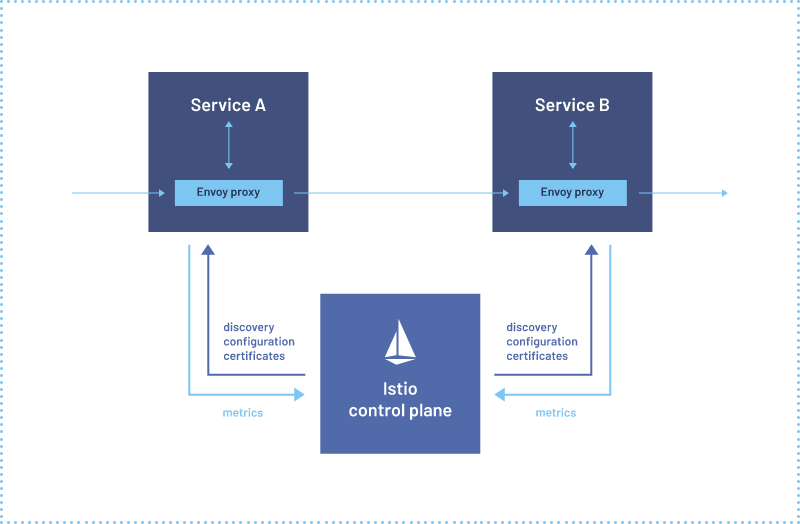
Istio 有 两个组件:
- 数据平面
- 控制平面
1)、The data plane is the communication between services. Without a service mesh, the network doesn’t understand the traffic being sent over, and can’t make any decisions based on what type of traffic it is, or who it is from or to.
(数据平面是服务之间的通信。如果没有服务网格,网络就不能理解发送过来的流量,也不能根据流量的类型、来自谁或发送到谁来做出任何决定。)
2)、Service mesh uses a proxy to intercept all your network traffic, allowing a broad set of application-aware features based on configuration you set.
(服务网格使用一个代理来拦截所有网络流量,允许基于所设置的配置实现一组广泛的应用程序感知特性。)
三、What is a Service Mesh?
https://istio.io/latest/about/service-mesh/
Modern applications are typically architected as distributed collections of microservices, with each collection of microservices performing some discrete business function. A service mesh is a dedicated infrastructure layer that you can add to your applications. It allows you to transparently add capabilities like observability, traffic management, and security, without adding them to your own code. The term “service mesh” describes both the type of software you use to implement this pattern, and the security or network domain that is created when you use that software.
(现代应用程序通常被设计为微服务的分布式集合,每个微服务集合执行一些离散的业务功能。服务网格是可以添加到应用程序中的专用基础结构层。它允许您透明地添加诸如可观察性、流量管理和安全性等功能,而无需将它们添加到您自己的代码中。术语“服务网格”既描述了用于实现此模式的软件类型,也描述了使用该软件时创建的安全或网络域。)
As the deployment of distributed services, such as in a Kubernetes-based system, grows in size and complexity, it can become harder to understand and manage. Its requirements can include discovery, load balancing, failure recovery, metrics, and monitoring. A service mesh also often addresses more complex operational requirements, like A/B testing, canary deployments, rate limiting, access control, encryption, and end-to-end authentication.
(随着分布式服务的部署(比如在基于 Kubernetes 的系统中)在规模和复杂性上的增长,理解和管理就会变得更加困难。它的需求可以包括发现、负载平衡、故障恢复、度量和监视。服务网格还经常处理更复杂的操作需求,如 A/B 测试、金丝雀部署、速率限制、访问控制、加密和端到端身份验证。)
Service-to-service communication is what makes a distributed application possible. Routing this communication, both within and across application clusters, becomes increasingly complex as the number of services grow. Istio helps reduce this complexity while easing the strain on development teams.
(服务到服务的通信使分布式应用程序成为可能。随着服务数量的增长,在应用程序集群内部和跨应用程序集群进行这种通信的路由变得越来越复杂。Istio 有助于降低这种复杂性,同时缓解开发团队的压力。)
四、概念介绍
4.1、Traffic management
https://istio.io/latest/docs/concepts/traffic-management/
Istio’s traffic routing rules let you easily control the flow of traffic and API calls between services.
(Istio 的流量路由规则使您可以轻松地控制服务之间的流量和 API 调用。)
Istio simplifies configuration of service-level properties like circuit breakers, timeouts, and retries, and makes it easy to set up important tasks like A/B testing, canary rollouts, and staged rollouts with percentage-based traffic splits.
(Istio 简化了服务级属性(如断路器、超时和重试)的配置,并使得设置重要任务(如 A/B 测试、金丝雀推出和基于百分比的流量分割分阶段推出)变得容易。)
It also provides out-of-box reliability features that help make your application more resilient against failures of dependent services or the network.
(它还提供了开箱即用的可靠性特性,帮助您的应用程序更有弹性地应对依赖服务或网络的故障。)
Istio’s traffic management model relies on the Envoy proxies that are deployed along with your services.
(Istio 的交通管理模型依赖于使者的代理,这些代理和你的服务一起部署。)
All traffic that your mesh services send and receive (data plane traffic) is proxied through Envoy, making it easy to direct and control traffic around your mesh without making any changes to your services.
(您的网格服务发送和接收的所有流量(数据平面流量)都是通过使者代理的,这使得它很容易指导和控制您的网格周围的流量,而不需要对您的服务做任何更改。)
4.1.1、介绍 Istio 流量管理
In order to direct traffic within your mesh, Istio needs to know where all your endpoints are, and which services they belong to. To populate its own service registry, Istio connects to a service discovery system. For example, if you’ve installed Istio on a Kubernetes cluster, then Istio automatically detects the services and endpoints in that cluster.
(为了指导网格中的流量,Istio 需要知道所有端点的位置,以及它们属于哪些服务。为了填充自己的服务注册中心,Istio 连接到一个服务发现系统。例如,如果您已经在 Kubernetes 集群上安装了 Istio,那么 Istio 将自动检测该集群中的服务和端点。)
Using this service registry, the Envoy proxies can then direct traffic to the relevant services. Most microservice-based applications have multiple instances of each service workload to handle service traffic, sometimes referred to as a load balancing pool. By default, the Envoy proxies distribute traffic across each service’s load balancing pool using a round-robin model, where requests are sent to each pool member in turn, returning to the top of the pool once each service instance has received a request.
(通过使用这个服务注册中心,使者代理可以将流量导向相关服务。大多数基于微服务的应用程序具有每个服务工作负载的多个实例来处理服务流量,有时称为负载平衡池。默认情况下,特使代理使用循环模型在每个服务的负载平衡池中分配流量,请求依次发送给每个池成员,一旦每个服务实例收到请求,请求就返回到池的顶部。)
While Istio’s basic service discovery and load balancing gives you a working service mesh, it’s far from all that Istio can do. In many cases you might want more fine-grained control over what happens to your mesh traffic. You might want to direct a particular percentage of traffic to a new version of a service as part of A/B testing, or apply a different load balancing policy to traffic for a particular subset of service instances. You might also want to apply special rules to traffic coming into or out of your mesh, or add an external dependency of your mesh to the service registry. You can do all this and more by adding your own traffic configuration to Istio using Istio’s traffic management API.
(虽然 Istio 的基本服务发现和负载平衡为您提供了一个可用的服务网格,但这远远不是 Istio 所能做到的。在许多情况下,您可能需要对网格流量发生的情况进行更细粒度的控制。作为 A/B 测试的一部分,您可能希望将特定百分比的流量指向服务的新版本,或者对特定服务实例子集的流量应用不同的负载平衡策略。您可能还希望应用特殊规则来处理进出网格的流量,或者向服务注册中心添加网格的外部依赖项。你可以通过使用 Istio 的流量管理 API 将自己的流量配置添加到 Istio 来完成所有这些甚至更多的工作。)
Like other Istio configuration, the API is specified using Kubernetes custom resource definitions (CRDs), which you can configure using YAML, as you’ll see in the examples.
(与其他 Istio 配置一样,API 是使用 Kubernetes 自定义资源定义(CRD)指定的,您可以使用 YAML 进行配置。)
The rest of this guide examines each of the traffic management API resources and what you can do with them. These resources are:
(本指南的其余部分将分析每个流量管理 API 资源以及如何使用它们。这些资源包括:)
- Virtual services
- Destination rules
- Gateways
- Service entries
- Sidecars
- Virtual services
4.2、Observability
https://istio.io/latest/docs/concepts/observability/
Istio generates detailed telemetry for all service communications within a mesh. This telemetry provides observability of service behavior, empowering operators to troubleshoot, maintain, and optimize their applications – without imposing any additional burdens on service developers. Through Istio, operators gain a thorough understanding of how monitored services are interacting, both with other services and with the Istio components themselves.
(Istio 为一个网格中的所有业务通信生成详细的遥测信息。这种遥测技术提供服务行为的可观测性,授权运营商进行故障排除、维护和优化其应用程序——而不会给服务开发人员带来任何额外负担。通过 Istio,运营商可以全面了解受监控的服务是如何与其他服务以及 Istio 组件本身进行交互的。)
Istio generates the following types of telemetry in order to provide overall service mesh observability:
(Istio 生成以下类型的遥测数据,以提供全面的服务网格可观测性:)
-
-
-
- Metrics. Istio generates a set of service metrics based on the four “golden signals” of monitoring (latency, traffic, errors, and saturation). Istio also provides detailed metrics for the mesh control plane. A default set of mesh monitoring dashboards built on top of these metrics is also provided.
-
-
(Metrics。Istio 根据监视的四个“黄金信号”(延迟、流量、错误和饱和度)生成一组服务度量。Istio 还提供了网格控制平面的详细度量。还提供了构建在这些指标之上的默认网格监视仪表板集。)
-
-
-
- Distributed Traces. Istio generates distributed trace spans for each service, providing operators with a detailed understanding of call flows and service dependencies within a mesh.
-
-
(分布式跟踪。Istio 为每个服务生成分布式的跟踪范围,为运营商提供对网格中的呼叫流和服务依赖关系的详细理解。)
-
-
-
- Access Logs. As traffic flows into a service within a mesh, Istio can generate a full record of each request, including source and destination metadata. This information enables operators to audit service behavior down to the individual workload instance level.
-
-
(访问记录。当流量流入网格中的服务时,Istio 可以生成每个请求的完整记录,包括源和目标元数据。此信息使操作员能够审计服务行为,直到单个工作负载实例级别。
4.3、Security capabilities
Breaking down a monolithic application into atomic services offers various benefits, including better agility, better scalability and better ability to reuse services. However, microservices also have particular security needs:
(将单一应用程序分解为原子服务可以带来各种好处,包括更好的敏捷性、更好的可伸缩性和更好的重用服务能力。然而,微服务也有特殊的安全需求):
- To defend against man-in-the-middle attacks, they need traffic encryption.
(为了防御中间人攻击,他们需要流量加密。)
- To provide flexible service access control, they need mutual TLS and fine-grained access policies.
(为了提供灵活的服务访问控制,它们需要相互的 TLS 和细粒度的访问策略。)
- To determine who did what at what time, they need auditing tools.
(为了确定谁在什么时间做了什么,他们需要审计工具。)
Istio Security provides a comprehensive security solution to solve these issues. This page gives an overview on how you can use Istio security features to secure your services, wherever you run them. In particular, Istio security mitigates both insider and external threats against your data, endpoints, communication, and platform.
(Istio Security 提供了一个全面的安全解决方案来解决这些问题。本页概述了如何使用 Istio 安全特性来保护您的服务,无论您在哪里运行它们。特别是,Istio 安全性可以减轻针对您的数据、端点、通信和平台的内部和外部威胁。)
4.4、Extensibility
https://istio.io/latest/docs/concepts/wasm/
WebAssembly is a sandboxing technology which can be used to extend the Istio proxy (Envoy). The Proxy-Wasm sandbox API replaces Mixer as the primary extension mechanism in Istio.
(WebAssembly 是一种沙箱技术,可用于扩展 Istio 代理(特使)。在 Istio,代理-Wasm 沙盒 API 取代 Mixer 成为主要的扩展机制。)
WebAssembly sandbox goals:
(WebAssembly 沙盒目标:)
-
-
- Efficiency - An extension adds low latency, CPU, and memory overhead.
-
(效率-扩展增加了低延迟、 CPU 和内存开销。)
-
-
- Function - An extension can enforce policy, collect telemetry, and perform payload mutations.
-
(功能-扩展可以强制执行策略,收集遥测数据,并执行有效载荷突变。)
-
-
- Isolation - A programming error or crash in one plugin doesn’t affect other plugins.
-
(隔离-一个插件中的编程错误或崩溃不会影响其他插件。)
-
-
- Configuration - The plugins are configured using an API that is consistent with other Istio APIs. An extension can be configured dynamically.
-
(配置-插件使用与其他 Istio API 一致的 API 进行配置。扩展可以动态配置。)
-
-
- Operator - An extension can be canaried and deployed as log-only, fail-open or fail-close.
-
(操作符-扩展可以是金丝雀式的,并且可以作为只有日志、故障打开或故障关闭的形式部署。)
-
-
- Extension developer - The plugin can be written in several programming languages.
-
(扩展开发者-插件可以用几种编程语言编写。)






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· AI技术革命,工作效率10个最佳AI工具