UAF
USE AFTER FREE
简单理解就是free指针之后没有置为0,在某些情况下会造成uaf的漏洞,正如下面的例子。
#include <stdio.h>
#include <stdlib.h>
typedef struct name {
char *myname;
void (*func)(char *str);
} NAME;
void myprint(char *str) { printf("%s\n", str); }
void printmyname() { printf("call print my name\n"); }
int main() {
NAME *a;
a = (NAME *)malloc(sizeof(struct name));
a->func = myprint;
a->myname = "I can also use it";
a->func("this is my function");
// free without modify
free(a);
a->func("I can also use it");// 指针未置空
// free with modify
a->func = printmyname;
a->func("this is my function");
// set NULL
a = NULL;
printf("this pogram will crash...\n");
a->func("can not be printed...");// 报错,指针已置空
}
调试hacknote
echo 0 > /proc/sys/kernel/randomize_va_space
hacker@ubuntu:~/Desktop$ checksec hacknote
[*] '/home/hacker/Desktop/hacknote'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x8048000) # 加载基址,调试用
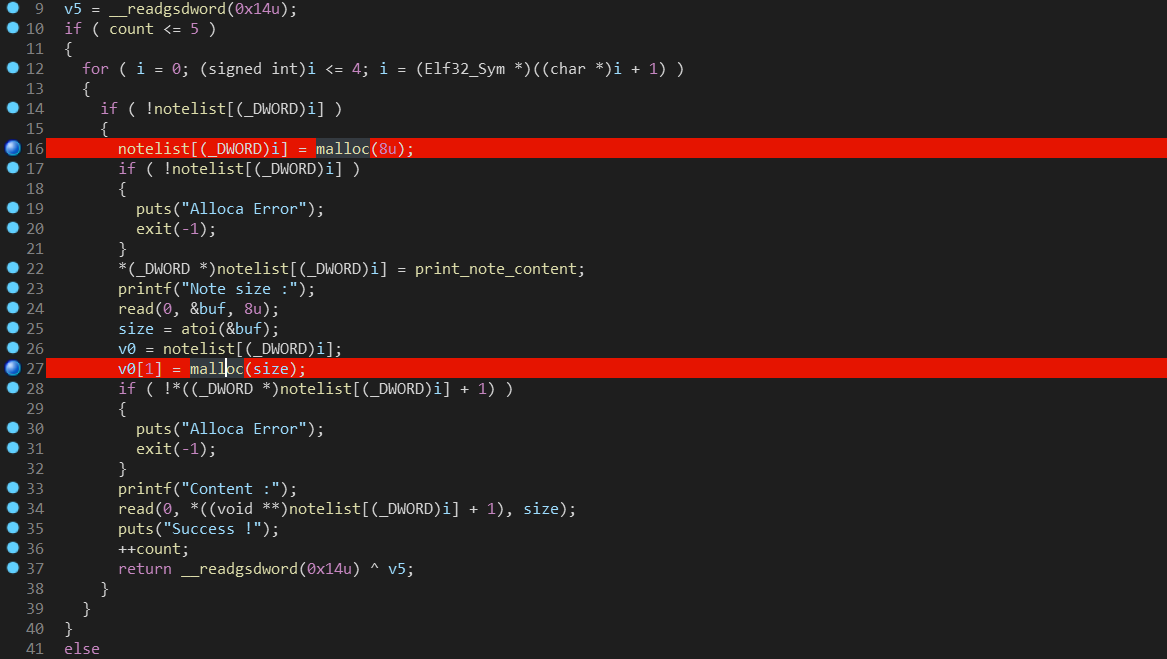

pwndbg> b *0x080486CA
Breakpoint 1 at 0x80486ca
pwndbg> b *0x0804875C
Breakpoint 2 at 0x804875c
pwndbg> b *0x08048893
Breakpoint 3 at 0x8048893
pwndbg> b *0x080488A9
Breakpoint 4 at 0x80488a9
由于调试的libc版本与ctf wiki不同,所以没有预期释放到fastbin中

cp /glibc/2.23/32/lib/ld-2.23.so /tmp/ld-2.23.so
patchelf --set-interpreter /tmp/ld-2.23.so /ctf/work/hacknote


root@--name:/glibc/2.23/32/lib# cp /glibc/2.23/32/lib/libc-2.23.so /tmp/libc-2.23.so
root@--name:/ctf/work# patchelf --replace-needed libc.so.6 /tmp/libc-2.23.so /ctf/work/axb_2019_fmt32
https://blog.csdn.net/qq_39563369/article/details/103950922
https://www.cnblogs.com/bhxdn/p/14541441.html
https://www.icode9.com/content-4-1060845.html
https://ohmygodlin.github.io/ctf/bin/2018/06/28/堆漏洞利用/
zer0_1s


