Cloud Design Patterns: Prescriptive Architecture Guidance for Cloud Applications 云设计模式:云应用的规范架构指导
Load data on demand into a cache from a data store. This pattern can improve performance and also helps to maintain consistency between data held in the cache and the data in the underlying data store.
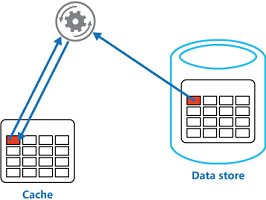
从数据存储区加载到缓存中的数据。这种模式可以提高性能,也有助于保持在缓存中的数据之间的一致性和底层数据存储的数据。
2、断路器(CircuitBreaker)设计模式
Handle faults that may take a variable amount of time to rectify when connecting to a remote service or resource. This pattern can improve the stability and resiliency of an application.
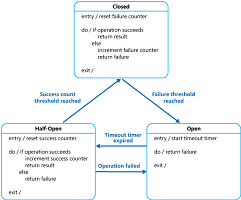
在连接到一个远程服务或资源时,处理故障可能需要一个变量的时间来纠正。这种模式可以提高应用程序的稳定性和弹性。
3、Compensating Transaction Pattern(事务修正模式)
Undo the work performed by a series of steps, which together define an eventually consistent operation, if one or more of the operations fails. Operations that follow the eventual consistency model are commonly found in cloud-hosted applications that implement complex business processes and workflows.
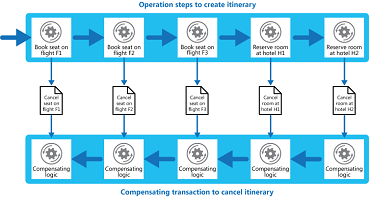
撤消由一系列步骤执行的工作,在一起定义一个最终一致的操作,如果一个或多个操作失败。在云托管的应用程序,实现复杂的业务流程和工作流程,遵循的最终一致性模型的操作是通常的做法。
4、Competing Consumers Pattern(消费者竞争模式)
Enable multiple concurrent consumers to process messages received on the same messaging channel. This pattern enables a system to process multiple messages concurrently to optimize throughput, to improve scalability and availability, and to balance the workload.
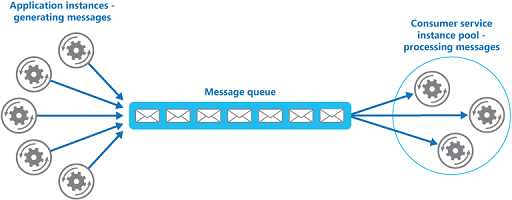
允许多个并发用户处理在同一消息通道上接收的处理消息。这种模式使系统能够处理多个消息,同时优化吞吐量,提高可扩展性和可用性,并以平衡的工作量。
5、Compute Resource Consolidation Pattern 计算资源整合模式
Consolidate multiple tasks or operations into a single computational unit. This pattern can increase compute resource utilization, and reduce the costs and management overhead associated with performing compute processing in cloud-hosted applications.
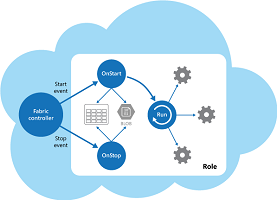
将多个任务或操作合并成一个单一的计算单元。这种模式可以提高计算资源的利用率,并降低成本和管理的开销与执行计算处理在云托管的应用程序。
6、Command and Query Responsibility Segregation (CQRS) Pattern 命令和查询职责分离(CQRS)模式
Segregate operations that read data from operations that update data by using separate interfaces. This pattern can maximize performance, scalability, and security; support evolution of the system over time through higher flexibility; and prevent update commands from causing merge conflicts at the domain level.
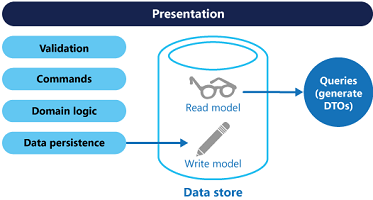
隔离操作,读取数据更新数据的操作通过使用单独的接口。这种模式可以最大限度地提高性能,可扩展性和安全性;支持系统的进化,随着时间的推移,通过更高的灵活性,并防止更新命令导致合并冲突在域级。
7、Event Sourcing Pattern 事件源模式
Use an append-only store to record the full series of events that describe actions taken on data in a domain, rather than storing just the current state, so that the store can be used to materialize the domain objects. This pattern can simplify tasks in complex domains by avoiding the requirement to synchronize the data model and the business domain; improve performance, scalability, and responsiveness; provide consistency for transactional data; and maintain full audit trails and history that may enable compensating actions.
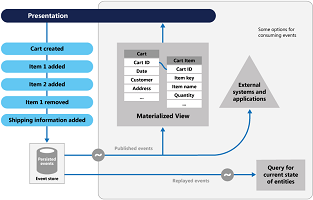
使用追加存储来记录在域中所采取的数据的完整系列事件,而不是存储当前状态,因此该存储区可以用来实现域对象。这种模式可以简化复杂的领域中的任务,以避免要求同步的数据模型和业务领域,提高性能,可扩展性和响应性;提供一致性的事务数据,并保持完整的审计跟踪和历史,可能使补偿行动。
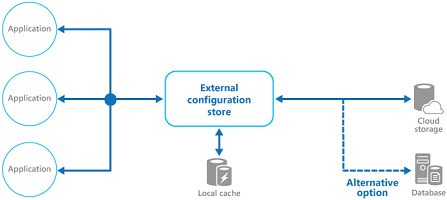
8、External Configuration Store Pattern 外部配置存储模式
Move configuration information out of the application deployment package to a centralized location. This pattern can provide opportunities for easier management and control of configuration data, and for sharing configuration data across applications and application instances.
将配置信息从应用程序部署包中移动到集中位置。这种模式可以提供更容易的管理和控制配置数据的机会,并在应用程序和应用实例之间共享配置数据。
9、Federated Identity Pattern 联合身份模式
Delegate authentication to an external identity provider. This pattern can simplify development, minimize the requirement for user administration, and improve the user experience of the application.
将身份验证委托给外部标识提供程序。该模式可以简化开发,减少用户管理的需求,提高应用程序的用户体验。

Protect applications and services by using a dedicated host instance that acts as a broker between clients and the application or service, validates and sanitizes requests, and passes requests and data between them. This pattern can provide an additional layer of security, and limit the attack surface of the system.
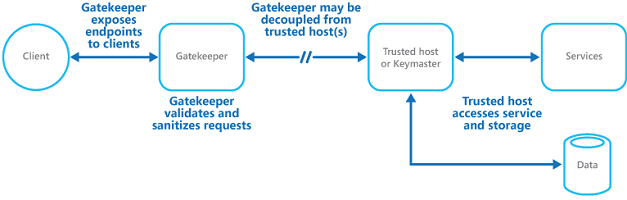
采用专用的主机实例,作为客户和应用程序或服务之间的代理保护的应用程序和服务,验证和清理的要求,并通过它们之间的请求数据。这种模式可以提供一个额外的安全层,并限制了对系统的攻击。
11、Health Endpoint Monitoring Pattern 健康端点监测模式
Implement functional checks within an application that external tools can access through exposed endpoints at regular intervals. This pattern can help to verify that applications and services are performing correctly.
在一个应用程序内实现功能检查,外部工具可以在定期的时间间隔中访问暴露的端点。这种模式可以帮助验证应用程序和服务是否正确执行。
12、Index Table Pattern 索引表模式
Create indexes over the fields in data stores that are frequently referenced by query criteria. This pattern can improve query performance by allowing applications to more quickly retrieve data from a data store.
创建索引查询数据在存储领域中经常引用的标准。这种模式可以提高查询性能,让应用程序更快速地从存储中检索数据。
13、Leader Election Pattern 领导选举模式
Coordinate the actions performed by a collection of collaborating task instances in a distributed application by electing one instance as the leader that assumes responsibility for managing the other instances. This pattern can help to ensure that tasks do not conflict with each other, cause contention for shared resources, or inadvertently interfere with the work that other task instances are performing.
14、Materialized View Pattern 物化视图模式
Generate pre-populated views over the data in one or more data stores when the data is formatted in a way that does not favor the required query operations. This pattern can help to support efficient querying and data extraction, and improve application performance.
15、Pipes and Filters Pattern 管道和过滤器模式
Decompose a task that performs complex processing into a series of discrete elements that can be reused. This pattern can improve performance, scalability, and reusability by allowing task elements that perform the processing to be deployed and scaled independently.
16、Priority Queue Pattern 优先级队列模式
Prioritize requests sent to services so that requests with a higher priority are received and processed more quickly than those of a lower priority. This pattern is useful in applications that offer different service level guarantees to individual types of client.
17、Queue-based Load Leveling Pattern 基于队列的负载均衡模式
Use a queue that acts as a buffer between a task and a service that it invokes in order to smooth intermittent heavy loads that may otherwise cause the service to fail or the task to timeout. This pattern can help to minimize the impact of peaks in demand on availability and responsiveness for both the task and the service.
18、Retry Pattern 重试模式
Enable an application to handle temporary failures when connecting to a service or network resource by transparently retrying the operation in the expectation that the failure is transient. This pattern can improve the stability of the application.
19、Runtime Reconfiguration Pattern 运行时重新配置模式
Design an application so that it can be reconfigured without requiring redeployment or restarting the application. This helps to maintain availability and minimize downtime.
20、Scheduler Agent Supervisor Pattern 调度代理主管模式
Coordinate a set of actions across a distributed set of services and other remote resources, attempt to transparently handle faults if any of these actions fail, or undo the effects of the work performed if the system cannot recover from a fault. This pattern can add resiliency to a distributed system by enabling it to recover and retry actions that fail due to transient exceptions, long-lasting faults, and process failures.
21、Sharding Pattern 分片模式
Divide a data store into a set of horizontal partitions shards. This pattern can improve scalability when storing and accessing large volumes of data.
22、Static Content Hosting Pattern 静态内容托管模式
Deploy static content to a cloud-based storage service that can deliver these directly to the client. This pattern can reduce the requirement for potentially expensive compute instances.
23、Throttling Pattern 节流模式
Control the consumption of resources used by an instance of an application, an individual tenant, or an entire service. This pattern can allow the system to continue to function and meet service level agreements, even when an increase in demand places an extreme load on resources.
24、Valet Key Pattern
Use a token or key that provides clients with restricted direct access to a specific resource or service in order to offload data transfer operations from the application code. This pattern is particularly useful in applications that use cloud-hosted storage systems or queues, and can minimize cost and maximize scalability and performance.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号