PspTerminateProcess未文档化函数导出终止进程
前言:实现PspTerminateProcess未文档化函数导出使用的笔记
如何获得未导出的函数
如果要使用未导出的函数,只要自己定义一个函数指针,并且为函数指针提供正确的函数地址就可以使用了。
有两种办法都可以获取为导出的函数地址:
1、特征码搜索
2、解析内核PDB文件
后面老师还讲了一种方法:如果一个导出函数中用到了这个未导出函数(该未导出函数是未文档化函数),那么可以获取该导出函数中获取该未导出函数
获取未导出函数PspTerminateProcess
在10-10-12分页中PspTerminateProcess在ntoskrnl.exe模块中,所以这里就需要先从driver_object中获取相关的_LDR_DATA_TABLE_ENTRY对象,然后进行遍历,再进行特征码搜索该未导出函数的地址
测试代码:
#include <ntddk.h> typedef struct _PEB_LDR_DATA { ULONG Length; BOOLEAN Initialized; PVOID SsHandle; LIST_ENTRY InLoadOrderModuleList; //代表按加载顺序构成的模块列表 LIST_ENTRY InMemoryOrderModuleList; //代表按内存顺序构成的模块列表 LIST_ENTRY InInitializationOrderModuleList; //代表按初始化顺序构成的模块链表 }PEB_LDR_DATA, *PPEB_LDR_DATA; typedef struct _LDR_DATA_TABLE_ENTRY { LIST_ENTRY InLoadOrderModuleList; //代表按加载顺序构成的模块列表 LIST_ENTRY InMemoryOrderModuleList; //代表按内存顺序构成的模块列表 LIST_ENTRY InInitializeationOrderModuleList; //代表按初始化顺序构成的模块链表 PVOID DllBase; //该模块的基地址 PVOID EntryPoint; //该模块的入口 ULONG SizeOfImage; //该模块的影像大小 UNICODE_STRING FullDllName; //模块的完整路径 UNICODE_STRING BaseDllName; //模块名 ULONG Flags; SHORT LoadCount; SHORT TlsIndex; HANDLE SectionHandle; ULONG CheckSum; ULONG TimeDataStamp; }LDR_MODULE, *PLDR_MODULE; VOID UnDriver(PDRIVER_OBJECT driver) { DbgPrint(("Uninstall Driver Is OK \n")); } void getAllDriverModules(PDRIVER_OBJECT Driver) { __try{ // 遍历内核模块,输出模块名称,基址以及大小 LDR_MODULE* pLdrModule = NULL; pLdrModule = (LDR_MODULE*)(*(ULONG*)((CHAR*)Driver + 0x14)); while (pLdrModule->DllBase != NULL) { DbgPrint("DllName: %ws DllBase: 0x%x, SizeOfImage: 0x%x\n", pLdrModule->BaseDllName.Buffer, pLdrModule->DllBase, pLdrModule->SizeOfImage); pLdrModule = (LDR_MODULE*)pLdrModule->InLoadOrderModuleList.Blink; } } __except (EXCEPTION_EXECUTE_HANDLER) { DbgPrint("Exception Error..."); } } typedef NTSTATUS(*pfnPspTerminateProcess)(PEPROCESS pEprocess, NTSTATUS ExitCode); void getPspTerminateProcess(PDRIVER_OBJECT Driver) { ULONG signtureCode[] = { 0x0124a164, 0x758b0000, 0x44703b08, 0x0db80775, 0xebc00000, 0xbe8d575a, 0x00000248, 0x200147f6, 0x868d1274, 0x0174868d, 0x56500000, 0x636d7a68 }; LDR_MODULE* pLdrModule = NULL; UNICODE_STRING ntoskrnlString; pfnPspTerminateProcess pPspTerminateProcess; LONG codeLength = sizeof(signtureCode) / sizeof(LONG); ULONG i = 0; __try{ RtlInitUnicodeString(&ntoskrnlString, L"ntoskrnl.exe"); pLdrModule = (LDR_MODULE*)(*(ULONG*)((CHAR*)Driver + 0x14)); while (pLdrModule->DllBase != NULL) { if (RtlCompareUnicodeString(&ntoskrnlString, &pLdrModule->BaseDllName, TRUE) == 0) { DbgPrint("find -> DllName: %ws DllBase: 0x%x, SizeOfImage: 0x%x\n", pLdrModule->BaseDllName.Buffer, pLdrModule->DllBase, pLdrModule->SizeOfImage); for (; i<pLdrModule->SizeOfImage; i++) { if (RtlCompareMemory(signtureCode, (PVOID)((LONG)pLdrModule->DllBase + i), codeLength) == codeLength) { pPspTerminateProcess = (pfnPspTerminateProcess)((LONG)pLdrModule->DllBase + i - 0x6); DbgPrint("find pfnPspTerminateProcess -> 0x%x\n", pPspTerminateProcess); break; } } } pLdrModule = (LDR_MODULE*)pLdrModule->InLoadOrderModuleList.Blink; } } __except (EXCEPTION_EXECUTE_HANDLER) { DbgPrint("Exception Error..."); } } NTSTATUS DriverEntry(IN PDRIVER_OBJECT Driver, PUNICODE_STRING RegistryPath) { DbgPrint(("hello zpchcbd \n")); //getAllDriverModules(Driver); getPspTerminateProcess(Driver); Driver->DriverUnload = UnDriver; return STATUS_SUCCESS; }
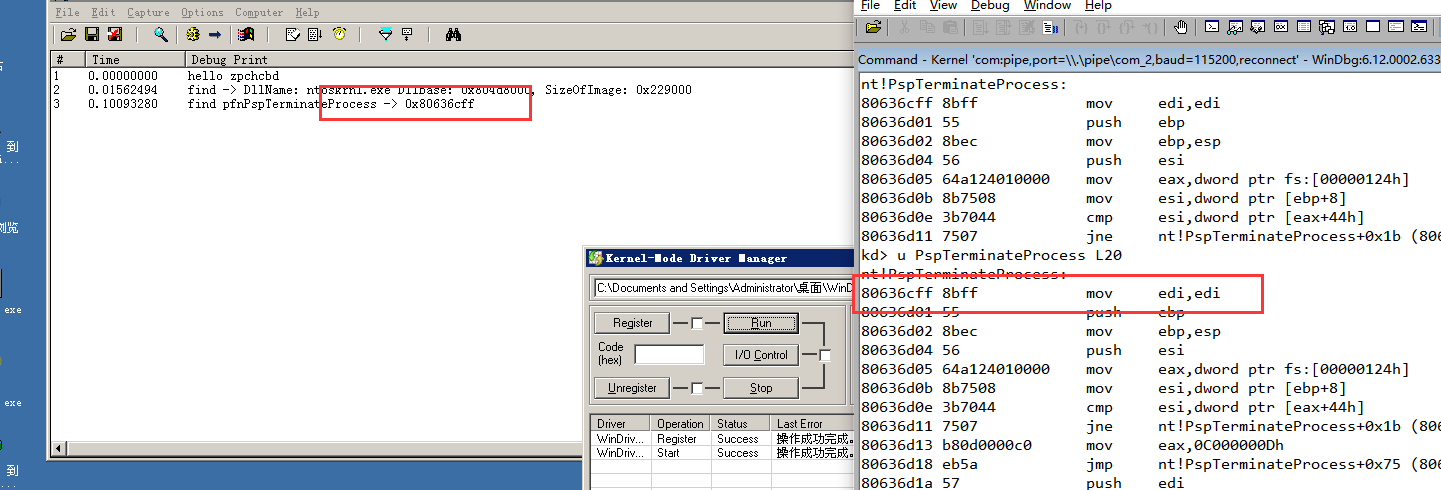
x86 XP下使用PspTerminateProcess结束记事本
void getPspTerminateProcess(PDRIVER_OBJECT Driver) { ULONG signtureCode[] = { 0x0124a164, 0x758b0000, 0x44703b08, 0x0db80775, 0xebc00000, 0xbe8d575a, 0x00000248, 0x200147f6, 0x868d1274, 0x0174868d, 0x56500000, 0x636d7a68 }; LDR_MODULE* pLdrModule = NULL; UNICODE_STRING ntoskrnlString; pfnPspTerminateProcess pPspTerminateProcess; LONG codeLength = sizeof(signtureCode) / sizeof(LONG); ULONG i = 0; NTSTATUS nStatus; __try{ RtlInitUnicodeString(&ntoskrnlString, L"ntoskrnl.exe"); pLdrModule = (LDR_MODULE*)(*(ULONG*)((CHAR*)Driver + 0x14)); while (pLdrModule->DllBase != NULL) { if (RtlCompareUnicodeString(&ntoskrnlString, &pLdrModule->BaseDllName, TRUE) == 0) { DbgPrint("find -> DllName: %ws DllBase: 0x%x, SizeOfImage: 0x%x\n", pLdrModule->BaseDllName.Buffer, pLdrModule->DllBase, pLdrModule->SizeOfImage); for (; i<pLdrModule->SizeOfImage; i++) { if (RtlCompareMemory(signtureCode, (PVOID)((LONG)pLdrModule->DllBase + i), codeLength) == codeLength) { PEPROCESS pEprocss; pPspTerminateProcess = (pfnPspTerminateProcess)((LONG)pLdrModule->DllBase + i - 0x6); DbgPrint("find pfnPspTerminateProcess -> 0x%x\n", pPspTerminateProcess); nStatus = PsLookupProcessByProcessId((HANDLE)592, &pEprocss); if (NT_SUCCESS(nStatus)) { pPspTerminateProcess(pEprocss, 0); // ObDereferenceObject(); break; } DbgPrint("PsLookupProcessByProcessId failed -> 0x%x\n", nStatus); break; } } } pLdrModule = (LDR_MODULE*)pLdrModule->InLoadOrderModuleList.Blink; } } __except (EXCEPTION_EXECUTE_HANDLER) { DbgPrint("Exception Error..."); } }
PspTerminateThreadByPointer
kd> u PsTerminateSystemThread L10 nt!PsTerminateSystemThread: 8058544d 8bff mov edi,edi 8058544f 55 push ebp 80585450 8bec mov ebp,esp 80585452 64a124010000 mov eax,dword ptr fs:[00000124h] 80585458 f6804802000010 test byte ptr [eax+248h],10h 8058545f 0f844e120800 je nt!PsTerminateSystemThread+0x14 (806066b3) 80585465 ff7508 push dword ptr [ebp+8] 80585468 50 push eax 80585469 e80117ffff call nt!PspTerminateThreadByPointer (80576b6f) 8058546e 5d pop ebp 8058546f c20400 ret 4 80585472 ff4118 inc dword ptr [ecx+18h] 80585475 8b883c050000 mov ecx,dword ptr [eax+53Ch] 8058547b 668b4104 mov ax,word ptr [ecx+4] 8058547f ff4114 inc dword ptr [ecx+14h] 80585482 663b4108 cmp ax,word ptr [ecx+8] kd> u PspTerminateThreadByPointer L10 nt!PspTerminateThreadByPointer: 80576b6f 8bff mov edi,edi 80576b71 55 push ebp 80576b72 8bec mov ebp,esp 80576b74 83ec0c sub esp,0Ch 80576b77 834df8ff or dword ptr [ebp-8],0FFFFFFFFh 80576b7b 56 push esi 80576b7c 57 push edi 80576b7d 8b7d08 mov edi,dword ptr [ebp+8] 80576b80 8db748020000 lea esi,[edi+248h] 80576b86 f60640 test byte ptr [esi],40h 80576b89 c745f4c0bdf0ff mov dword ptr [ebp-0Ch],0FFF0BDC0h 80576b90 0f8501fa0800 jne nt!PspTerminateThreadByPointer+0x23 (80606597) 80576b96 64a124010000 mov eax,dword ptr fs:[00000124h] 80576b9c 3bf8 cmp edi,eax 80576b9e 0f8543910100 jne nt!PspTerminateThreadByPointer+0x52 (8058fce7) 80576ba4 33c0 xor eax,eax



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY