Docker学习【6】私有仓库
Docker学习【6】私有仓库
一、搭建私有仓库
1、环境部署(centos)
| 服务器名称 | IP地址 | 功能 |
|---|---|---|
| Docker1 | 192.168.27.134 | Docker私有仓库 |
| Docker2 | 192.168.27.135 | 使用Docker私有仓库的客户机 |
2、自建仓库
(1)拉取仓库镜像
[root@Docker1 ~]# docker pull registry
Using default tag: latest
latest: Pulling from library/registry
619be1103602: Pull complete
5daf2fb85fb9: Pull complete
ca5f23059090: Pull complete
8f2a82336004: Pull complete
68c26f40ad80: Pull complete
Digest: sha256:fb9c9aef62af3955f6014613456551c92e88a67dcf1fc51f5f91bcbd1832813f
Status: Downloaded newer image for registry:latest
docker.io/library/registry:latest
[root@Docker1 ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
registry latest 9363667f8aec 5 weeks ago 25.4MB
(2)将仓库镜像运行成容器
[root@Docker1 ~]# docker run -it -d -p 5000:5000 \
> --restart=always \
> --name registry registry
848628d717f640eab0e18d5f9c9d73f4742005bb54830d59f273cda8441a0ee3
(3)将镜像上传至刚刚创建的镜像仓库
[root@Docker1 ~]# docker pull busybox
Using default tag: latest
latest: Pulling from library/busybox
7b2699543f22: Pull complete
Digest: sha256:c3839dd800b9eb7603340509769c43e146a74c63dca3045a8e7dc8ee07e53966
Status: Downloaded newer image for busybox:latest
docker.io/library/busybox:latest
#修改镜像的tag,使其指向私有仓库
[root@Docker1 ~]# docker tag busybox 192.168.27.134:5000/busybox:latest
[root@Docker1 ~]# docker push 192.168.27.134:5000/busybox:latest
The push refers to repository [192.168.27.134:5000/busybox]
Get "https://192.168.27.134:5000/v2/": net/http: request canceled while waiting for connection (Client.Timeout exceeded while awaiting headers)
(4)修改Docker的启动参数
[root@Docker1 ~]# cat /usr/lib/systemd/system/docker.service
[Unit]
Description=Docker Application Container Engine
Documentation=https://docs.docker.com
After=network-online.target docker.socket firewalld.service containerd.service time-set.target
Wants=network-online.target containerd.service
Requires=docker.socket
[Service]
Type=notify
# the default is not to use systemd for cgroups because the delegate issues still
# exists and systemd currently does not support the cgroup feature set required
# for containers run by docker
ExecStart=/usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock
ExecReload=/bin/kill -s HUP $MAINPID
TimeoutStartSec=0
RestartSec=2
Restart=always
# Note that StartLimit* options were moved from "Service" to "Unit" in systemd 229.
# Both the old, and new location are accepted by systemd 229 and up, so using the old location
# to make them work for either version of systemd.
StartLimitBurst=3
# Note that StartLimitInterval was renamed to StartLimitIntervalSec in systemd 230.
# Both the old, and new name are accepted by systemd 230 and up, so using the old name to make
# this option work for either version of systemd.
StartLimitInterval=60s
# Having non-zero Limit*s causes performance problems due to accounting overhead
# in the kernel. We recommend using cgroups to do container-local accounting.
LimitNPROC=infinity
LimitCORE=infinity
# Comment TasksMax if your systemd version does not support it.
# Only systemd 226 and above support this option.
TasksMax=infinity
# set delegate yes so that systemd does not reset the cgroups of docker containers
Delegate=yes
# kill only the docker process, not all processes in the cgroup
KillMode=process
OOMScoreAdjust=-500
[Install]
WantedBy=multi-user.target
[root@Docker1 ~]# vi /usr/lib/systemd/system/docker.service
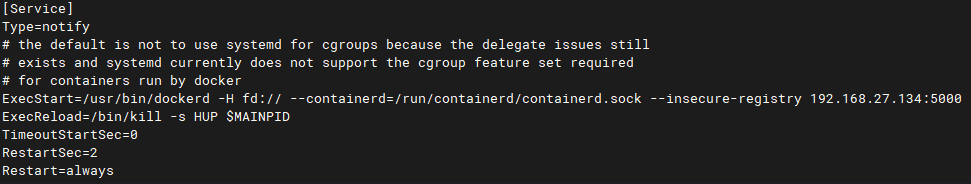
[root@Docker1 ~]# sudo systemctl daemon-reload
[root@Docker1 ~]# systemctl restart docker
(5)将镜像推送至私有仓库
[root@Docker1 ~]# docker push 192.168.27.134:5000/busybox:latest
The push refers to repository [192.168.27.134:5000/busybox]
95c4a60383f7: Pushed
latest: digest: sha256:db16cd196b8a37ba5f08414e6f6e71003d76665a5eac160cb75ad3759d8b3e29 size: 527
[root@Docker1 ~]#
(6)查看私有仓库中的镜像,并拉取其中镜像
[root@Docker1 ~]# curl -X GET http://192.168.27.134:5000/v2/_catalog
{"repositories":["busybox"]}
#使用curl工具查看,可以看到仓库中有一个Busybox镜像
(7)删除镜像
[root@Docker1 ~]# docker rmi busybox
Untagged: busybox:latest
Untagged: busybox@sha256:c3839dd800b9eb7603340509769c43e146a74c63dca3045a8e7dc8ee07e53966
[root@Docker1 ~]# docker rmi 192.168.27.134:5000/busybox
Untagged: 192.168.27.134:5000/busybox:latest
Untagged: 192.168.27.134:5000/busybox@sha256:db16cd196b8a37ba5f08414e6f6e71003d76665a5eac160cb75ad3759d8b3e29
Deleted: sha256:ba5dc23f65d4cc4a4535bce55cf9e63b068eb02946e3422d3587e8ce803b6aab
Deleted: sha256:95c4a60383f7b6eb6f7b8e153a07cd6e896de0476763bef39d0f6cf3400624bd
### docker images 本地镜像已经被删除
[root@Docker1 ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
registry latest 9363667f8aec 5 weeks ago 25.4MB
(8)从私有仓库拉取Busybox镜像
[root@Docker1 ~]# docker pull 192.168.27.134:5000/busybox
Using default tag: latest
latest: Pulling from busybox
Digest: sha256:db16cd196b8a37ba5f08414e6f6e71003d76665a5eac160cb75ad3759d8b3e29
Status: Image is up to date for 192.168.27.134:5000/busybox:latest
192.168.27.134:5000/busybox:latest
[root@Docker1 ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
registry latest 9363667f8aec 5 weeks ago 25.4MB
192.168.27.134:5000/busybox latest ba5dc23f65d4 11 months ago 4.26MB
[root@Docker1 ~]#
3、通过另一台服务器拉取私有仓库镜像
- 拉取镜像
[root@Docker2 ~]# docker pull 192.168.27.134:5000/busybox
Using default tag: latest
Error response from daemon: Get "https://192.168.27.134:5000/v2/": http: server gave HTTP response to HTTPS client
出现报错(解决如下)
-
1
[root@Docker1 ~]# vi /etc/resolv.conf [root@Docker1 ~]# cat /etc/resolv.conf # Generated by NetworkManager nameserver 192.168.27.128 nameserver 8.8.8.8 nameserver 114.114.114.114 nameserver 192.168.27.134 -
2
[root@Docker2 ~]# vi /etc/resolv.conf [root@Docker2 ~]# cat /etc/resolv.conf # Generated by NetworkManager nameserver 192.168.27.128 nameserver 8.8.8.8 nameserver 114.114.114.114 nameserver 192.168.27.134 nameserver 192.168.27.135 -
3
[root@Docker2 ~]# systemctl restart httpd [root@Docker2 ~]# docker pull 192.168.27.134:5000/busybox Using default tag: latest Error response from daemon: Get "https://192.168.27.134:5000/v2/": http: server gave HTTP response to HTTPS client [root@Docker2 ~]# reboot -
4 这里少了个0
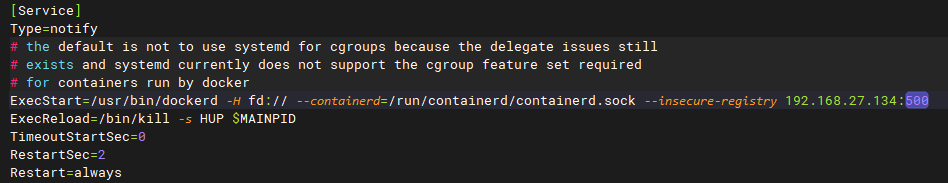
-
5 Finish
[root@Docker2 ~]# vi /usr/lib/systemd/system/docker.service [root@Docker2 ~]# cat /usr/lib/systemd/system/docker.service [Unit] Description=Docker Application Container Engine Documentation=https://docs.docker.com After=network-online.target docker.socket firewalld.service containerd.service time-set.target Wants=network-online.target containerd.service Requires=docker.socket [Service] Type=notify # the default is not to use systemd for cgroups because the delegate issues still # exists and systemd currently does not support the cgroup feature set required # for containers run by docker ExecStart=/usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock --insecure-registry 192.168.27.134:5000 ExecReload=/bin/kill -s HUP $MAINPID TimeoutStartSec=0 RestartSec=2 Restart=always # Note that StartLimit* options were moved from "Service" to "Unit" in systemd 229. # Both the old, and new location are accepted by systemd 229 and up, so using the old location # to make them work for either version of systemd. StartLimitBurst=3 # Note that StartLimitInterval was renamed to StartLimitIntervalSec in systemd 230. # Both the old, and new name are accepted by systemd 230 and up, so using the old name to make # this option work for either version of systemd. StartLimitInterval=60s # Having non-zero Limit*s causes performance problems due to accounting overhead # in the kernel. We recommend using cgroups to do container-local accounting. LimitNPROC=infinity LimitCORE=infinity # Comment TasksMax if your systemd version does not support it. # Only systemd 226 and above support this option. TasksMax=infinity # set delegate yes so that systemd does not reset the cgroups of docker containers Delegate=yes # kill only the docker process, not all processes in the cgroup KillMode=process OOMScoreAdjust=-500 [Install] WantedBy=multi-user.target [root@Docker2 ~]# sudo systemctl daemon-reload [root@Docker2 ~]# sudo systemctl restart docker [root@Docker2 ~]# docker pull 192.168.27.134:5000/busybox Using default tag: latest latest: Pulling from busybox 3a2e9cc4b126: Pull complete Digest: sha256:db16cd196b8a37ba5f08414e6f6e71003d76665a5eac160cb75ad3759d8b3e29 Status: Downloaded newer image for 192.168.27.134:5000/busybox:latest 192.168.27.134:5000/busybox:latest -
[root@Docker2 ~]# docker images REPOSITORY TAG IMAGE ID CREATED SIZE 192.168.27.134:5000/busybox latest ba5dc23f65d4 11 months ago 4.26MB
二、使用TLS证书
1、生成证书
#TLS:传输层安全
(1)使用OpenSSL工具生成私人证书文件:
[root@Docker1 ~]# mkdir -p /opt/docker/registry/certs
[root@Docker1 ~]# openssl req -newkey rsa:4096 -nodes -sha256 -keyout /opt/docker/registry/certs/domain.key -x509 -days 365 -out /opt/docker/registry/certs/domain.crt
Generating a RSA private key
....................................................................................................++++
.........++++
writing new private key to '/opt/docker/registry/certs/domain.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:xj
Locality Name (eg, city) [Default City]:cj
Organization Name (eg, company) [Default Company Ltd]:cjxy
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:registry.Docker.com
Email Address []:
(2)创建带有TSL证书的仓库容器:
[root@Docker1 ~]# docker run -it -d \
> --name registry-TLS \
> -p 5000:5000 \
> -v /opt/docker/registry/certs/:/certs \
> -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \
> -e REGISTRY_HTTP_TLS_KEY=/certs/domain.key registry
85d0839ca16f1e4cb95379f4a9aa3c0df5795aae5f067d026e7632c704e9d905
docker: Error response from daemon: driver failed programming external connectivity on endpoint registry-TLS (3de25122b74569e3131db4b90bd6b744f8718f4a0a41cbfd09f987ecc2328e3b): Bind for 0.0.0.0:5000 failed: port is already allocated.
[root@Docker1 ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
85d0839ca16f registry "/entrypoint.sh /etc…" 13 seconds ago Created registry-TLS
848628d717f6 registry "/entrypoint.sh /etc…" About an hour ago Up 19 minutes 0.0.0.0:5000->5000/tcp, :::5000->5000/tcp registry
[root@Docker1 ~]# docker stop registry
registry
[root@Docker1 ~]# docker rm 85
85
[root@Docker1 ~]# docker run -it -d --name registry-TLS -p 5000:5000 -v /opt/docker/registry/certs/:/certs -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt -e REGISTRY_HTTP_TLS_KEY=/certs/domain.key registry
8c5651691ccd0b444def682ba58c3165ea301c78f540f8fc4123c8c594878eaf
[root@Docker1 ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
8c5651691ccd registry "/entrypoint.sh /etc…" 5 seconds ago Up 4 seconds 0.0.0.0:5000->5000/tcp, :::5000->5000/tcp registry-TLS
848628d717f6 registry "/entrypoint.sh /etc…" About an hour ago Exited (2) 31 seconds ago registry
[root@Docker1 ~]#
(3)在两台docker客户端主机配置域名解析
-
两台主机以做好解析
[root@Docker1 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.27.134 registry.Docker.com
[root@Docker2 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.27.134 registry.Docker.com
[root@Docker2 ~]# mkdir -p /etc/docker/certs.d/registry.Docker.com:5000
(4)将证书damain.crt复制到要使用仓库的Docker宿主机:
[root@Docker1 ~]# scp -r -p /opt/docker/registry/certs/domain.crt 192.168.27.135:/etc/docker/certs.d/registry.Docker.com:5000/ca.crt
The authenticity of host '192.168.27.135 (192.168.27.135)' can't be established.
ECDSA key fingerprint is SHA256:OuD2KXokT075Gi40zZEaDtpJSIfKcCOtVPV5kXqSYmk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.27.135' (ECDSA) to the list of known hosts.
root@192.168.27.135's password:
domain.crt 100% 1980 669.1KB/s 00:00
[root@Docker1 ~]#
[root@Docker2 ~]# ls /etc/docker/certs.d/registry.Docker.com\:5000/
ca.crt
[root@Docker2 ~]#
(5)使用docker2推送镜像到私有仓库
[root@Docker2 ~]# docker tag busybox:latest registry.Docker.com:5000/busybox:latest
Error response from daemon: No such image: busybox:latest
#报错原因:没有本地的busybox:latest镜像,所以要拉去一个
[root@Docker2 ~]# docker pull busybox:latest
latest: Pulling from library/busybox
5cc84ad355aa: Pull complete
Digest: sha256:5acba83a746c7608ed544dc1533b87c737a0b0fb730301639a0179f9344b1678
Status: Downloaded newer image for busybox:latest
docker.io/library/busybox:latest
[root@Docker2 ~]# docker tag busybox:latest registry.Docker.com:5000/busybox:latest
-
push
[root@Docker2 ~]# docker push registry.Docker.com:5000/busybox:latest The push refers to repository [registry.Docker.com:5000/busybox] Get "https://registry.Docker.com:5000/v2/": tls: failed to verify certificate: x509: certificate relies on legacy Common Name field, use SANs instead
报错了,解决如下:
-
删掉原来的证书:
[root@Docker1 docker]# cd /opt/docker/registry/ [root@Docker1 registry]# ls certs [root@Docker1 registry]# cd certs/ [root@Docker1 certs]# ls domain.crt domain.key [root@Docker1 certs]# rm -fr * -
重新生成证书:在最后添加:-addext "subjectAltName = DNS:registry.Docker.com"选项
[root@Docker1 certs]openssl req -newkey rsa:4096 -nodes -sha256 -keyout /opt/docker/registry/certs/domain.key -x509 -days 365 -out /opt/docker/registry/certs/domain.crt -addext "subjectAltName = DNS:registry.Docker.com" Generating a RSA private key .............................................................................................++++ .............................................................................................................................++++ writing new private key to '/opt/docker/registry/certs/domain.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:xj Locality Name (eg, city) [Default City]:cj Organization Name (eg, company) [Default Company Ltd]: Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) []:registry.Docker.com Email Address []: [root@Docker1 certs]# ls domain.crt domain.key -
重新创建证书仓库:
[root@Docker1 certs]# docker run -it -d \ > --name registry-TLS \ > -p 5000:5000 \ > -v /opt/docker/registry/certs/:/certs \ > -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \ > -e REGISTRY_HTTP_TLS_KEY=/certs/domain.key registry d1e6848048953e8da3667fe3413fb3d15546e641b96661f23cc7b9585d61dae7 [root@Docker1 certs]# docker ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES d1e684804895 registry "/entrypoint.sh /etc…" 4 seconds ago Up 3 seconds 0.0.0.0:5000->5000/tcp, :::5000->5000/tcp registry-TLS 848628d717f6 registry "/entrypoint.sh /etc…" 3 hours ago Exited (2) 4 minutes ago registry -
删除宿主机原来的证书
[root@Docker2 registry.Docker.com:5000]# rm -fr ca.crt -
重新复制证书到宿主机
[root@Docker1 certs]# scp -r -p /opt/docker/registry/certs/domain.crt 192.168.27.135:/etc/docker/certs.d/registry.Docker.com:5000/ca.crt root@192.168.27.135's password: domain.crt [root@Docker2 registry.Docker.com:5000]# ls ca.crt -
使用docker2推送镜像到私有仓库
[root@Docker2 registry.Docker.com:5000]# docker pull busybox:latest latest: Pulling from library/busybox 5cc84ad355aa: Already exists Digest: sha256:5acba83a746c7608ed544dc1533b87c737a0b0fb730301639a0179f9344b1678 Status: Image is up to date for busybox:latest docker.io/library/busybox:latest [root@Docker2 registry.Docker.com:5000]# docker tag busybox:latest registry.Docker.com:5000/busybox:latest [root@Docker2 registry.Docker.com:5000]# docker push registry.Docker.com:5000/busybox:latest The push refers to repository [registry.Docker.com:5000/busybox] 01fd6df81c8e: Pushed latest: digest: sha256:62ffc2ed7554e4c6d360bce40bbcf196573dd27c4ce080641a2c59867e732dee size: 527 [root@Docker2 registry.Docker.com:5000]#
2、基本身份验证
(1)创建用户密码文件
-
注意:此处registry使用2.6版本,新版本不支持以下命令
-
删掉原测试registry
[root@Docker1 auth]# docker rm registry -
registry:2.6
[root@Docker1 auth]# docker ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES d1e684804895 registry "/entrypoint.sh /etc…" 43 minutes ago Exited (2) 3 minutes ago registry-TLS [root@Docker1 auth]# docker run --entrypoint htpasswd registry:2.6 -Bbn testuser testpassword > /opt/docker/registry/auth/htpasswd [root@Docker1 auth]# cat htpasswd testuser:$2y$05$k1OMohWxM1MLJ7sWwp0UduG/0vujbkpxY1afKr2YGpxhXYVmLDUl2 [root@Docker1 auth]#以上创建了用户密码文件testuser与testpassword
(2)运行仓库容器,并指定TLS证书与身份验证目录:
[root@Docker1 auth]# docker run -d -it \
> --name registry-auth \
> -p 5000:5000 \
> -v /opt/docker/registry/auth/:/auth \
> -e "REGISTRY_AUTH=htpasswd" \
> -e "REGISTRY_AUTH_HTPASSWD_REALM=Registry Realm" \
> -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd \
> -v /opt/docker/registry/certs:/certs \
> -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \
> -e REGISTRY_HTTP_TLS_KEY=/certs/domain.key registry
f71a0cd44ed3c8d5a83449a51d271be7ec10226bccb6e4617787b26523355418
[root@Docker1 auth]#
(3)Docker2 上尝试推送镜像
[root@Docker2 auth]# docker push 192.168.27.134:5000/busybox
Using default tag: latest
The push refers to repository [192.168.27.134:5000/busybox]
95c4a60383f7: Preparing
no basic auth credentials
[root@Docker2 auth]#
(4)在Docker2通过用户名和密码登录
[root@Docker2 registry.Docker.com:5000]# docker login registry.Docker.com:5000
Username: testuser
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
(5)重新推送
[root@Docker2 registry.Docker.com:5000]# docker tag busybox:latest registry.Docker.com:5000/busybox
[root@Docker2 registry.Docker.com:5000]# docker push registry.Docker.com:5000/busybox
Using default tag: latest
The push refers to repository [registry.Docker.com:5000/busybox]
01fd6df81c8e: Pushed
latest: digest: sha256:62ffc2ed7554e4c6d360bce40bbcf196573dd27c4ce080641a2c59867e732dee size: 527
[root@Docker2 registry.Docker.com:5000]#
FINISH
三、Nginx反向代理仓库
1、安装nginx
(1)yum -y install nginx
[root@Docker1 auth]# yum -y install nginx
......
Installed:
dejavu-fonts-common-2.35-7.el8.noarch dejavu-sans-fonts-2.35-7.el8.noarch
fontconfig-2.13.1-4.el8.x86_64 fontpackages-filesystem-1.44-22.el8.noarch
gd-2.2.5-7.el8.x86_64 jbigkit-libs-2.1-14.el8.x86_64
libX11-1.6.8-5.el8.x86_64 libX11-common-1.6.8-5.el8.noarch
libXau-1.0.9-3.el8.x86_64 libXpm-3.5.12-8.el8.x86_64
libtiff-4.0.9-20.el8.x86_64 libwebp-1.0.0-5.el8.x86_64
libxcb-1.13.1-1.el8.x86_64 nginx-1:1.14.1-9.module_el8.0.0+184+e34fea82.x86_64
nginx-all-modules-1:1.14.1-9.module_el8.0.0+184+e34fea82.noarch nginx-filesystem-1:1.14.1-9.module_el8.0.0+184+e34fea82.noarch
nginx-mod-http-image-filter-1:1.14.1-9.module_el8.0.0+184+e34fea82.x86_64 nginx-mod-http-perl-1:1.14.1-9.module_el8.0.0+184+e34fea82.x86_64
nginx-mod-http-xslt-filter-1:1.14.1-9.module_el8.0.0+184+e34fea82.x86_64 nginx-mod-mail-1:1.14.1-9.module_el8.0.0+184+e34fea82.x86_64
nginx-mod-stream-1:1.14.1-9.module_el8.0.0+184+e34fea82.x86_64
Complete!
(2)查看nginx的配置文件
[root@Docker1 auth]# cat /etc/nginx/nginx.conf
# For more information on configuration, see:
# * Official English Documentation: http://nginx.org/en/docs/
# * Official Russian Documentation: http://nginx.org/ru/docs/
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamic modules. See /usr/share/doc/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024;
}
http {
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
include /etc/nginx/mime.types;
default_type application/octet-stream;
# Load modular configuration files from the /etc/nginx/conf.d directory.
# See http://nginx.org/en/docs/ngx_core_module.html#include
# for more information.
include /etc/nginx/conf.d/*.conf;
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name _;
root /usr/share/nginx/html;
# Load configuration files for the default server block.
include /etc/nginx/default.d/*.conf;
location / {
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
# Settings for a TLS enabled server.
#
# server {
# listen 443 ssl http2 default_server;
# listen [::]:443 ssl http2 default_server;
# server_name _;
# root /usr/share/nginx/html;
#
# ssl_certificate "/etc/pki/nginx/server.crt";
# ssl_certificate_key "/etc/pki/nginx/private/server.key";
# ssl_session_cache shared:SSL:1m;
# ssl_session_timeout 10m;
# ssl_ciphers PROFILE=SYSTEM;
# ssl_prefer_server_ciphers on;
#
# # Load configuration files for the default server block.
# include /etc/nginx/default.d/*.conf;
#
# location / {
# }
#
# error_page 404 /404.html;
# location = /40x.html {
# }
#
# error_page 500 502 503 504 /50x.html;
# location = /50x.html {
# }
# }
}
[root@Docker1 auth]#
(3)重新配置nginx的配置文件
[root@Docker1 auth]# cat /etc/nginx/nginx.conf
# For more information on configuration, see:
# * Official English Documentation: http://nginx.org/en/docs/
# * Official Russian Documentation: http://nginx.org/ru/docs/
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
# Load dynamic modules. See /usr/share/doc/nginx/README.dynamic.
include /usr/share/nginx/modules/*.conf;
events {
worker_connections 1024;
}
http{
upstream Docker-registry {
server 192.168.27.134:5000;
}
server{
listen 443;
server_name Docker.test.com;
ssl on;
ssl_certificate "/etc/nginx/ssl/nginx-selfsigned.crt";
ssl_certificate_key "/etc/nginx/ssl/nginx-selfsigned.key";
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
client_max_body_size 0;
chunked_transfer_encoding on;
add_header 'Docker-Distribution-Api-Version' 'registry/2.0' always;
location / {
auth_basic "Restricted";
auth_basic_user_file /etc/nginx/auth/htpasswd.txt;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_read_timeout 900;
proxy_pass http://Docker-registry;
}
location /_ping {
auth_basic off;
proxy_pass http://Docker-registry;
}
location /v2/_ping {
auth_basic off;
proxy_pass http://Docker-registry;
}
location /v2/_catalog {
auth_basic off;
proxy_pass http://Docker-registry;
}
}
}
[root@Docker1 ssl]# systemctl daemon-reload
[root@Docker1 ssl]# systemctl restart nginx
[root@Docker1 ssl]#
2、通过OpenSSL工具生成私钥和证书
代码示例
[root@Docker1 auth]# openssl req -x509 -nodes \
> -newkey rsa:2048 \
> -days 365 \
> -subj "/C=CN/ST=xj/L=cj/O=Test/OU=Test/CN=Docker.test.com" \
> -keyout /etc/nginx/ssl/nginx-selfsigned.key \
> -out /etc/nginx/ssl/nginx-selfsigned.crt
Generating a RSA private key
...............................................................+++++
.................+++++
writing new private key to '/etc/nginx/ssl/nginx-selfsigned.key'
-----
[root@Docker1 nginx]#
3、使用htpasswd工具生成用户账户,并设置密码
[root@Docker1 /]# mkdir -p /etc/nginx/auth
[root@Docker1 /]# cd /etc/nginx/auth
[root@Docker1 auth]# htpasswd -c htpasswd.txt user
New password:
Re-type new password:
Adding password for user user
[root@Docker1 auth]# #passwd
[root@Docker1 auth]# cat htpasswd.txt
user:$apr1$mehAngvt$EYm66C0s.zEVnmqnQ02a/0
[root@Docker1 auth]#
4、启动nginx服务
[root@Docker1 auth]# systemctl restart nginx
[root@Docker1 auth]#
5、访问测试
-
关闭防火墙
[root@Docker1 auth]# systemctl status firewalld ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled) Active: active (running) since Mon 2024-04-22 13:53:54 CST; 1h 17min ago Docs: man:firewalld(1) Main PID: 975 (firewalld) Tasks: 2 (limit: 11218) Memory: 35.7M CGroup: /system.slice/firewalld.service └─975 /usr/libexec/platform-python -s /usr/sbin/firewalld --nofork --nopid Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t nat -F DOCKER' failed: iptables: No chain/target/match by that name. Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t nat -X DOCKER' failed: iptables: No chain/target/match by that name. Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t filter -F DOCKER' failed: iptables: No chain/target/match by that name. Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t filter -X DOCKER' failed: iptables: No chain/target/match by that name. Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t filter -F DOCKER-ISOLATION-STAGE-1' failed: iptables: No chain/target/match by that > Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t filter -X DOCKER-ISOLATION-STAGE-1' failed: iptables: No chain/target/match by that > Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t filter -F DOCKER-ISOLATION-STAGE-2' failed: iptables: No chain/target/match by that > Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t filter -X DOCKER-ISOLATION-STAGE-2' failed: iptables: No chain/target/match by that > Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t filter -F DOCKER-ISOLATION' failed: iptables: No chain/target/match by that name. Apr 22 13:54:07 Docker1 firewalld[975]: WARNING: COMMAND_FAILED: '/usr/sbin/iptables -w10 -t filter -X DOCKER-ISOLATION' failed: iptables: No chain/target/match by that name. [root@Docker1 auth]# systemctl stop firewalld [root@Docker1 auth]# -
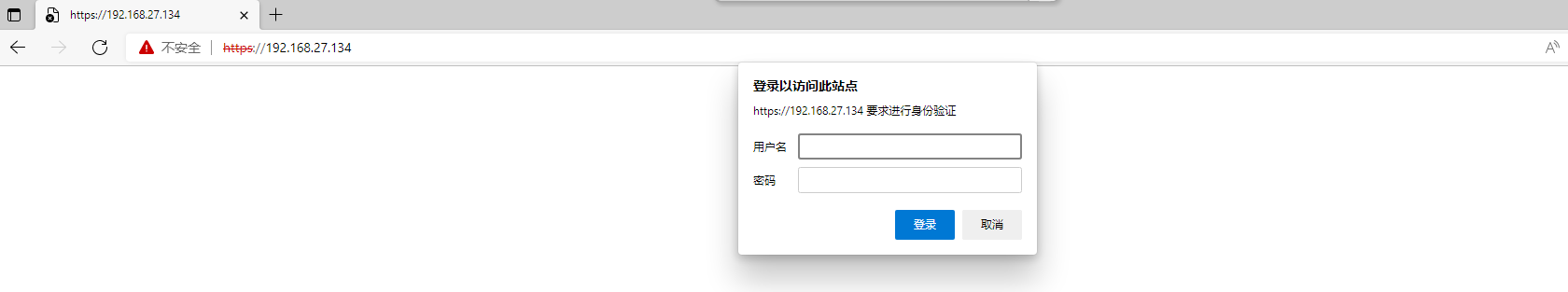
6、在Docker2登录仓库
[root@Docker2 ~]# vi /etc/hosts
[root@Docker2 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
#192.168.27.134 registry.Docker.com
192.168.27.134 Docker.test.com
[root@Docker2 ~]# scp -r 192.168.27.134:/etc/nginx/ssl/nginx-selfsigned.crt /etc/pki/ca-trust/source/anchors
The authenticity of host '192.168.27.134 (192.168.27.134)' can't be established.
ECDSA key fingerprint is SHA256:OuD2KXokT075Gi40zZEaDtpJSIfKcCOtVPV5kXqSYmk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.27.134' (ECDSA) to the list of known hosts.
root@192.168.27.134's password:
nginx-selfsigned.crt 100% 1318 421.2KB/s 00:00
[root@Docker2 ~]# update-ca-trust
[root@Docker2 ~]# systemctl daemon-reload
[root@Docker2 ~]# systemctl restart docker
[root@Docker2 ~]# docker login https://192.168.27.134:443
Username: user
Password:
login Succeeded


 浙公网安备 33010602011771号
浙公网安备 33010602011771号