prometheus学习系列十六: Prometheus 安全
prometheus安全
我们这里说的安全主要是基本认证和https2种, 目前这2种安全在prometheus中都没有的, 需要借助第三方软件实现, 这里以nginx为例。
基本认证
配置基本认证
在前面的部署中,我们部署完毕prometheus server 后, 可以通过对应的http://192.168.100.10:9090就可以访问到我们的 表达式浏览器, 进行promql的查询了。 这是很不安全, 必要情况下,我们需要加入基本认证, 只有认证过的用户才能访问页面,进行数据的查询。
[root@node00 ~]# yum install httpd-tools nginx [root@node00 ~]# cd /etc/nginx [root@node00 nginx]# htpasswd -c /etc/nginx/.htpasswd admin [root@node00 conf.d]# cat prometheus.linuxpanda.tech.conf server { listen 80; server_name prometheus.linuxpanda.tech ; location / { auth_basic "Prometheus"; auth_basic_user_file /etc/nginx/.htpasswd; proxy_pass http://localhost:9090/; } } [root@node00 conf.d]# pwd /etc/nginx/conf.d [root@node00 conf.d]# cat prometheus.linuxpanda.tech.conf server { listen 80; server_name prometheus.linuxpanda.tech ; location / { auth_basic "Prometheus"; auth_basic_user_file /etc/nginx/.htpasswd; proxy_pass http://localhost:9090/; } } [root@node00 conf.d]# systemctl restart nginx [root@node00 conf.d]# systemctl status nginx [root@node00 system]# pwd /usr/lib/systemd/system [root@node00 system]# cat prometheus.service [Unit] Description=prometheus After=network.target [Service] User=prometheus Group=prometheus WorkingDirectory=/usr/local/prometheus/prometheus ExecStart=/usr/local/prometheus/prometheus/prometheus --web.external-url=http://prometheus.linuxpanda.tech [Install] WantedBy=multi-user.target [root@node00 system]# systemctl daemon-reload [root@node00 system]# sytemctl restart prometheus -bash: sytemctl: command not found [root@node00 system]# systemctl restart prometheus [root@node00 system]# systemctl status prometheus
测试
配置域名解析
由于我们使用的是prometheus.linuxpanda.tech 这个域名, 我们需要确保这个域名能正常解析到对应的ip地址上面, 这里使用host绑定方式。
# 在我宿主机的hosts文件中加入如下行 192.168.100.10 prometheus.linuxpanda.tech
登陆
在浏览器输入prometheus.linuxpanda.tech 这个域名后, 效果图如下,
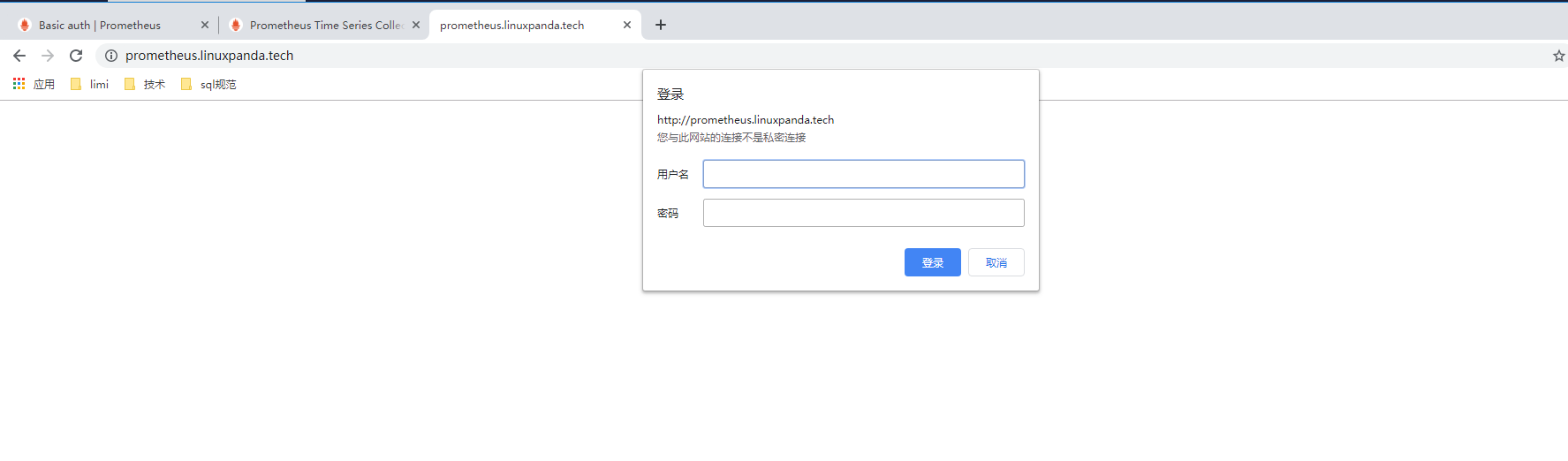
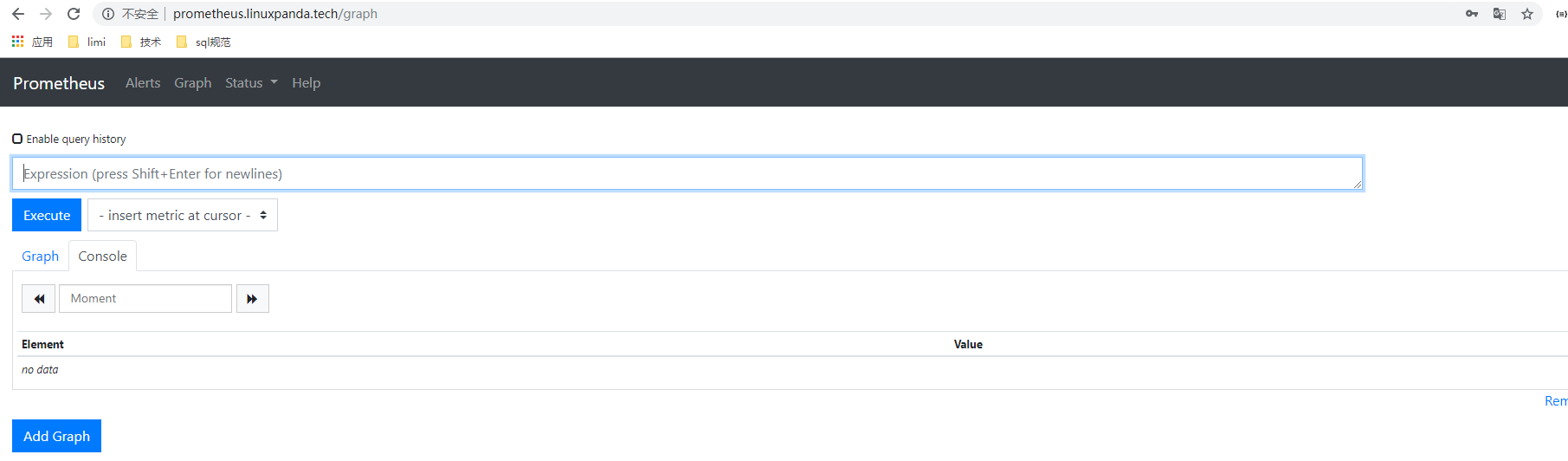
输入我们前面设置的账户和密码 admin/admin 登陆后,效果如下。
https
配置https是需要证书的, 正式环境中的域名是需要花钱的,我们这里使用openssl这个软件来生成一个自签证书测试使用。
https配置
[root@node00 nginx]# cd /etc/nginx/ [root@node00 nginx]# mkdir ssl [root@node00 nginx]# cd ssl/ [root@node00 ssl]# openssl req -x509 -newkey rsa:4096 -nodes -keyout prometheus.linuxpanda.tech.key -out prometheus.linuxpanda.tech.crt Generating a 4096 bit RSA private key .............................................................++ ...................................................................................................................................................++ writing new private key to 'prometheus.linuxpanda.tech.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:Bei Locality Name (eg, city) [Default City]:^C [root@node00 ssl]# openssl req -x509 -newkey rsa:4096 -nodes -keyout prometheus.linuxpanda.tech.key -out prometheus.linuxpanda.tech.crt Generating a 4096 bit RSA private key ..............................................................................................................................................................++ ...............................................................++ writing new private key to 'prometheus.linuxpanda.tech.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:BEIJING Locality Name (eg, city) [Default City]:BEIJING Organization Name (eg, company) [Default Company Ltd]: Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) []:prometheus.linuxpanda.tech Email Address []: [root@node00 conf.d]# pwd /etc/nginx/conf.d [root@node00 conf.d]# cat prometheus.linuxpanda.tech.conf server { listen 80; listen 443 ssl; server_name prometheus.linuxpanda.tech ; ssl_certificate ssl/prometheus.linuxpanda.tech.crt; ssl_certificate_key ssl/prometheus.linuxpanda.tech.key; location / { auth_basic "Prometheus"; auth_basic_user_file /etc/nginx/.htpasswd; proxy_pass http://localhost:9090/; } } [root@node00 conf.d]# systemctl restart nginx [root@node00 conf.d]# systemctl status nginx
测试
在浏览器输入https://prometheus.linuxpanda.tech 这个域名后,也是会提示不安全的, 那是因为我们使用的是openssl自签证书,忽略证书信息,继续访问,可以访问到如下页面。
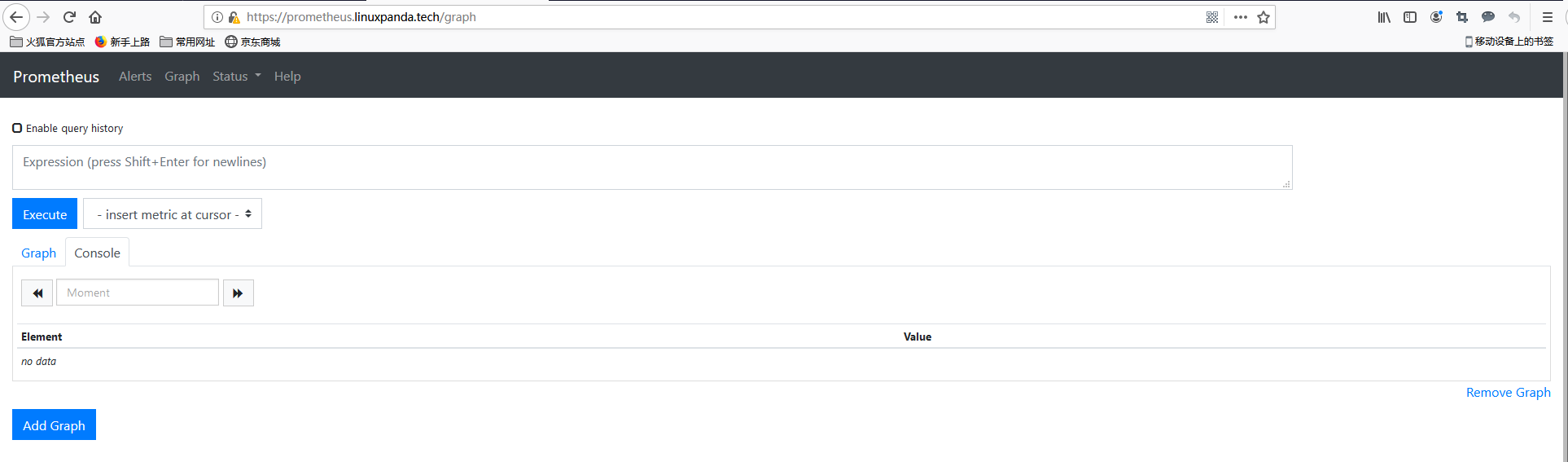
posted on 2019-10-12 09:58 LinuxPanda 阅读(4330) 评论(0) 编辑 收藏 举报




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 2025年我用 Compose 写了一个 Todo App
· 张高兴的大模型开发实战:(一)使用 Selenium 进行网页爬虫