ldap配置系列一:ldap的安装
ldap的安装
ldap的简介
LDAP是轻量目录访问协议,英文全称是Lightweight Directory Access Protocol,一般都简称为LDAP。它是基于X.500标准的,但是简单多了并且可以根据需要定制。与X.500不同,LDAP支持TCP/IP,这对访问Internet是必须的。LDAP的核心规范在RFC中都有定义,所有与LDAP相关的RFC都可以在LDAPman RFC网页中找到。
选择一个域名
我个人的域名为linuxpanda.tech,我给ldap服务配置一个域名为ldap.aibeike.com。通过dns解析添加一个A记录值为我自己的ldap服务器的外网ip。
测试域名正确性。
[root@VM_0_15_centos ~]# ping -c 2 ldap.linuxpanda.tech PING ldap.linuxpanda.tech (39.106.157.220) 56(84) bytes of data. 64 bytes from 39.106.157.220 (39.106.157.220): icmp_seq=1 ttl=52 time=3.40 ms 64 bytes from 39.106.157.220 (39.106.157.220): icmp_seq=2 ttl=52 time=3.37 ms --- ldap.linuxpanda.tech ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1000ms rtt min/avg/max/mdev = 3.370/3.385/3.401/0.060 ms
安装openldap服务端
[root@VM_0_15_centos ~]# yum install openldap-servers openldap-clients -y ^C [root@VM_0_15_centos ~]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG [root@VM_0_15_centos ~]# chown -R ldap.ldap /var/lib/ldap [root@VM_0_15_centos ~]# systemctl enable slapd Created symlink from /etc/systemd/system/multi-user.target.wants/slapd.service to /usr/lib/systemd/system/slapd.service. [root@VM_0_15_centos ~]# systemctl start slapd
[root@VM_0_15_centos ~]# systemctl status slapd
设置ldap的管理员用户的密码
# 设置ldap的管理员密码,用户名为root
[root@VM_0_15_centos ~]# slappasswd New password: Re-enter new password: {SSHA}6qygfSS2fBqjb0KhiaPo21btIt9+8EbL
# 创建ldif文件 [root@VM_0_15_centos ldap]# cd /etc/openldap/ [root@VM_0_15_centos openldap]# mkdir myself [root@VM_0_15_centos openldap]# cd myself/ [root@VM_0_15_centos myself]# vim chrootpw.ldif dn: olcDatabase={0}config,cn=config changetype: modify add: olcRootPW olcRootPW: {SSHA}6qygfSS2fBqjb0KhiaPo21btIt9+8EbL
# 根据文件导入 [root@VM_0_15_centos myself]# ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 modifying entry "olcDatabase={0}config,cn=config"
添加基础的schema
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
设置根域和数据库超级管理员
这里的根域和上面提到的linuxpanda.tech不是一回事,我们这里为了和自身域名还是保持一致好些,设置为dc=linuxpanda.tech,dc=com。
这里的数据库管理员和上面的超级管理员也不是一回事,为了方便,我们还是使用上面的管理员密码来设置数据库库的密码。
[root@VM_0_15_centos myself]# vim domain-dbadmin.ldif [root@VM_0_15_centos myself]# cat domain-dbadmin.ldif dn: olcDatabase={1}monitor,cn=config changetype: modify replace: olcAccess olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.base="cn=admin,dc=linuxpanda,dc=tech" read by * none dn: olcDatabase={2}hdb,cn=config changetype: modify replace: olcSuffix olcSuffix: dc=linuxpanda,dc=tech dn: olcDatabase={2}hdb,cn=config changetype: modify replace: olcRootDN olcRootDN: cn=admin,dc=linuxpanda,dc=tech dn: olcDatabase={2}hdb,cn=config changetype: modify add: olcRootPW olcRootPW: {SSHA}6qygfSS2fBqjb0KhiaPo21btIt9+8EbL dn: olcDatabase={2}hdb,cn=config changetype: modify add: olcAccess olcAccess: {0}to attrs=userPassword,shadowLastChange by dn="cn=admin,dc=linuxpanda,dc=tech" write by anonymous auth by self write by * none olcAccess: {1}to dn.base="" by * read olcAccess: {2}to * by dn="cn=admin,dc=linuxpanda,dc=tech" write by * read [root@VM_0_15_centos myself]# ldapadd -Y EXTERNAL -H ldapi:/// -f domain-dbadmin.ldif
创建基本的用户节点,组节点,数据库管理员
[root@VM_0_15_centos myself]# vim basedomain.ldif [root@VM_0_15_centos myself]# cat basedomain.ldif dn: dc=linuxpanda,dc=tech objectClass: top objectClass: dcObject objectclass: organization o: Example Inc. dc: linuxpanda dn: ou=people,dc=linuxpanda,dc=tech objectClass: organizationalUnit ou: user dn: ou=group,dc=linuxpanda,dc=tech objectClass: organizationalUnit ou: group dn: cn=admin,dc=linuxpanda,dc=tech objectClass: organizationalRole cn: admin description: Directory Administrator [root@VM_0_15_centos myself]# ldapadd -x -D cn=admin,dc=linuxpanda,dc=tech -W -f basedomain.ldif Enter LDAP Password: adding new entry "dc=linuxpanda,dc=tech" adding new entry "ou=people,dc=linuxpanda,dc=tech" adding new entry "ou=group,dc=linuxpanda,dc=tech" adding new entry "cn=admin,dc=linuxpanda,dc=tech"
防火墙设置
[root@VM_0_15_centos myself]# firewall-cmd --permanent --add-service=ldap success [root@VM_0_15_centos myself]# firewall-cmd --reload success
配置日志
[root@VM_0_15_centos myself]# vim log.ldif [root@VM_0_15_centos myself]# cat log.ldif dn: cn=config changetype: modify add: olcLogLevel olcLogLevel: 32 "log.ldif" [New] 4L, 66C written [root@VM_0_15_centos myself]# ldapmodify -Y EXTERNAL -H ldapi:/// -f log.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 modifying entry "cn=config" [root@VM_0_15_centos myself]# mkdir -p /var/log/slapd [root@VM_0_15_centos myself]# chown ldap:ldap /var/log/slapd/ [root@VM_0_15_centos myself]# echo "local4.* /var/log/slapd/slapd.log" >> /etc/rsyslog.conf [root@VM_0_15_centos myself]# systemctl restart rsyslog
[root@VM_0_15_centos myself]# systemctl restart slapd [root@VM_0_15_centos myself]# tail -n 4 /var/log/slapd/slapd.log Sep 5 20:43:31 VM_0_15_centos slapd[4520]: => test_filter Sep 5 20:43:31 VM_0_15_centos slapd[4520]: PRESENT Sep 5 20:43:31 VM_0_15_centos slapd[4520]: <= test_filter 6 Sep 5 20:43:31 VM_0_15_centos slapd[4523]: slapd starting
使用工具连接
有些人喜欢安装套ldap环境来管理ldap用户, 我这里使用ldapadmin.exe来管理。下载地址为:
连接信息如下:
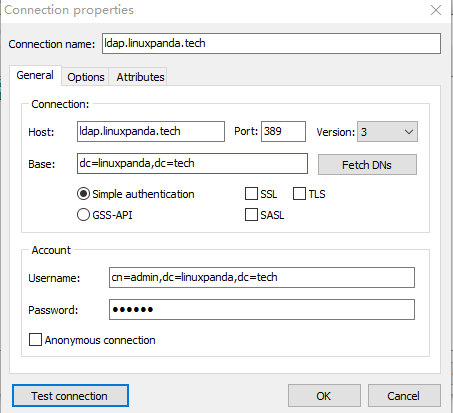
主界面如下:

这里强烈建议给每个用户配置邮箱。
添加用户或者测试组

常用查询命令
# 查询主域下的信息
[root@VM_0_15_centos ~]# ldapsearch -LLL -w oracle oracle -x -H ldap://58.87.98.84 -D"cn=admin,dc=linuxpanda,dc=tech" -b "dc=linuxpanda,dc=tech" dn: dc=linuxpanda,dc=tech dn: ou=people,dc=linuxpanda,dc=tech dn: ou=group,dc=linuxpanda,dc=tech dn: cn=admin,dc=linuxpanda,dc=tech dn: uid=test01,ou=people,dc=linuxpanda,dc=tech # 查询people组下面的uid=test01的用户 [root@VM_0_15_centos ~]# ldapsearch -LLL -w oracle oracle -x -H ldap://58.87.98.84 -D"cn=admin,dc=linuxpanda,dc=tech" -b "ou=people,dc=linuxpanda,dc=tech" "(uid=test01)" dn: ou=people,dc=linuxpanda,dc=tech dn: uid=test01,ou=people,dc=linuxpanda,dc=tech # 备份 [root@VM_0_15_centos ~]# ldapsearch -LLL -w oracle oracle -x -H ldap://58.87.98.84 -D"cn=admin,dc=linuxpanda,dc=tech" -b "dc=linuxpanda,dc=tech" "(uid=test01)" >linuxpanda.tech.ldap.bak
参考
李广慧: https://www.jianshu.com/p/dc7112873e68
ldap-how-to: https://www.itzgeek.com/how-tos/linux/centos-how-tos/step-step-openldap-server-configuration-centos-7-rhel-7.html
wiki: https://en.wikipedia.org/wiki/Lightweight_Directory_Access_Protocol
posted on 2018-09-06 13:20 LinuxPanda 阅读(26252) 评论(5) 收藏 举报

 浙公网安备 33010602011771号
浙公网安备 33010602011771号