K8S创建用户RBAC授权
Kubernetes操作账号及权限设置
目前RBAC是k8s授权方式最常用的一种方式。在k8s上,一个客户端向apiserver发起请求,需要如下信息:
1)username,uid,
2) group,
3) extra(额外信息)
4) API
5) request path,例如:http:``//127.0.0.1:8080/apis/apps/v1/namespaces/kube-system/d
6)HTTP request action,如get,post,put,``delete``,
7)Http request action,如 get,list,create,udate,patch,watch,proxy,redirect,``delete``,deletecollection
8) Rresource
9)Subresource
10)Namespace
11)API group
创建serviceaccount
# In GKE need to get RBAC permissions first with
# kubectl create clusterrolebinding cluster-admin-binding --clusterrole=cluster-admin [--user=<user-name>|--group=<group-name>]
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: jenkins
namespace:jenkins
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: jenkins
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/exec"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/log"]
verbs: ["get","list","watch"]
- apiGroups: [""]
resources: ["events"]
verbs: ["watch"]
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: RoleBinding
metadata:
name: jenkins
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: jenkins
subjects:
- kind: ServiceAccount
name: jenkins
创建useraccount
一.生成账号
例如:给K8S集群创建一个gpu用户
在k8s的master节点上执行:
#创建证书
(umask 077; openssl genrsa -out gpu.key 2048)
openssl req -new -key gpu.key -out gpu.csr -subj "/CN=gpu"
openssl x509 -req -in gpu.csr -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -out gpu.crt -days 3650
openssl x509 -in gpu.crt -text -noout
#把用户账户信息添加到k8s集群中
kubectl config set-credentials gpu --client-certificate=./gpu.crt --client-key=./gpu.key --embed-certs=true
#创建账户,设置用户访问的集群
kubectl config set-context gpu@kubernetes --cluster=kubernetes --user=gpu
#切换用户
kubectl config use-context gpu@kubernetes
#验证权限
kubectl get pods
#切换成管理员
kubectl config use-context kubernetes-admin@kubernetes
查看所有用户
kubectl config get-contexts
查看集群角色
kubectl get ClusterRole
查看服务账户
kubectl get serviceAccount
二.设置权限
在管理员权限下创建角色和权限并绑定到用户(role 和role-binding)
role.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
namespace: gpu
name: gpu-reader
rules:
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["services"]
verbs: ["get", "watch", "list"]
- apiGroups: [""]
resources: ["pods"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/exec"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/log"]
verbs: ["get","list","watch"]
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get"]
- apiGroups: ["batch", "externsions"]
resources: ["jobs"]
verbs: ["get","list","watch","create", "update","patch","delete"]
role-binding.yaml
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: read-pods
namespace: gpu
subjects:
- kind: User
name: gpu
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: gpu-reader
apiGroup: rbac.authorization.k8s.io
三.生成用户config文件
输出全部用户配置
kubectl config view --raw --output='json' >1.json
vim 1.json
删除users内除"name": "gpu"的其他内容
删除contexts内除"name": "gpu@kubernetes"的其他内容
mv 1.json config //分发config给用户
RBAC
一、基于角色的访问控制
rbac:role based ac,也就是我们把用户加入角色里面,这样用户就具有角色的权限了。
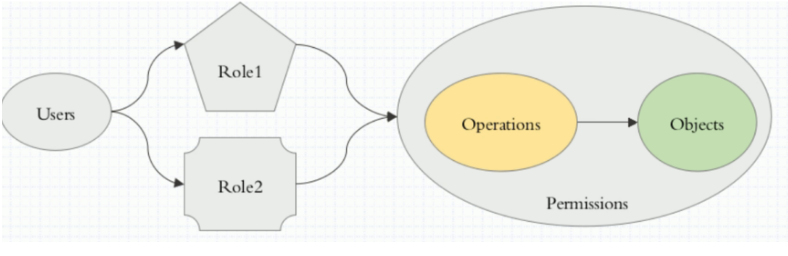
RBAC是通过rolebinding把user绑定到role上的。而role是基于namespace设定的,也就是这说这个user只能访问指定namespace下的pod资源。
而如果把user通过ClusterRoleBind绑定到ClusterRole上后,那么这个user就突破了namespace的限制,而拥有了集群级别的权限,即这个用户可以访问这个集群下所有namespace下的pod了。
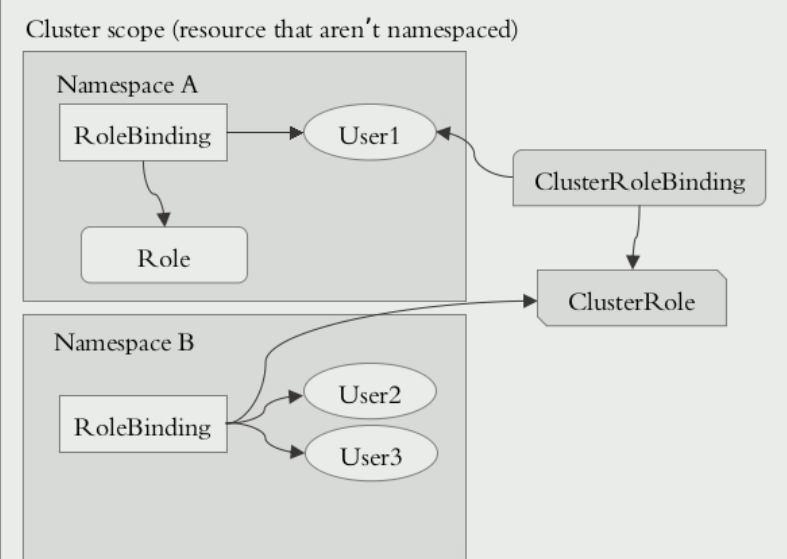
但是,我们也可以用RoleBinding去把user绑定到ClusteRrole。在下图中,我们把user1通过rolebinding绑定到ClusteRrole上,但是我们知道rolebinding只限制在namespace中,所以user1也只限定在namespace中,而不是整个集群中。
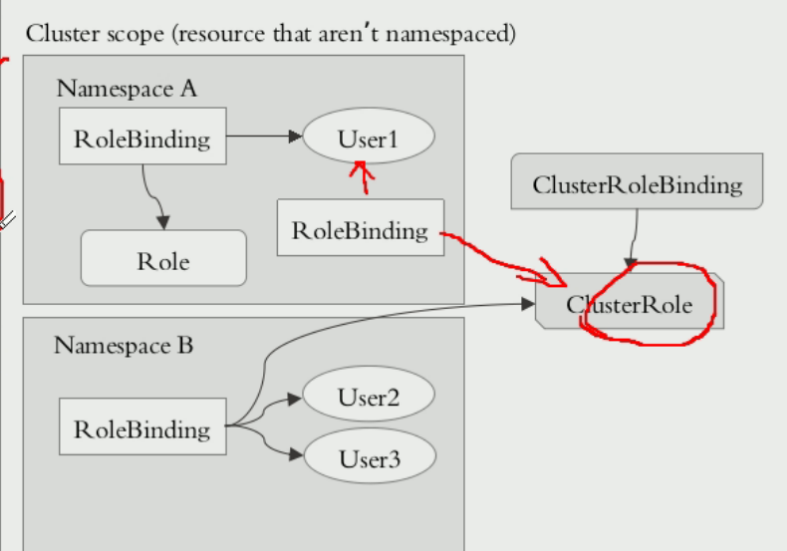
二、CluserRoleBinding和RoleBinding的区别
CluserRoleBinding是针对集群的,而RoleBinding是只针对namespace的。
三、useraccount和serviceaccount
k8s验证分为useraccount和serviceaccount。
个人理解serviceaccount是指服务账户,是指在POD的启动账户,serviceaccount设置的就是该POD启动后的权限。比如linux服务器下httpd服务可以指定http账户启动,但http账户本身没有对系统的登录权限。
useraccount就好比是linux服务器的登录账户,是有登录权限的。可以使用confi在客户端连接K8S集群的账户。
附录
一、使用create生成配置的yaml文件
kubectl create serviceaccount mysa -o yaml --dry-run > mysa.yaml
上面我们可以看到,只要是kubectl create的,只要加上-o yaml,就可以导出清单文件,这样我们以后就不用从头到尾写清单文件了,而是只要生产一个,然后改改就行了,这个很不错。
另外kubectl get 也可以导出yaml格式的,如下:
kubectl get pods myapp``-1` `-o yaml --export
二、创建jenkins的serviceaccount
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: jenkins
name: service-reader
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["services"]
verbs: ["get", "watch", "list"]
- apiGroups: [""]
resources: ["pods"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/exec"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/log"]
verbs: ["get","list","watch"]
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get"]
#在jenkins命名空间下创建一个服务账号jenkins
#kubectl create serviceaccount jenkins -n jenkins -o yaml
kubectl create serviceaccount jenkins -n servers
#创建一个名为“service-reader-pod”的集群角色绑定,它的“clusterrole”是“service-reader”,它的名字是“default:default”,其中第一个“default”是名空间(namespace),第二个“default”是服务账户名字
kubectl create clusterrolebinding service-reader-pod --clusterrole=service-reader --serviceaccount=servers:jenkins



