zzh@ZZHPC:~$ openssl req --help
Usage: req [options]
General options:
-help Display this summary
-engine val Use engine, possibly a hardware device
-keygen_engine val Specify engine to be used for key generation operations
-in infile X.509 request input file (default stdin)
-inform PEM|DER Input format - DER or PEM
-verify Verify self-signature on the request
Certificate options:
-new New request
-config infile Request template file
-section val Config section to use (default "req")
-utf8 Input characters are UTF8 (default ASCII)
-nameopt val Certificate subject/issuer name printing options
-reqopt val Various request text options
-text Text form of request
-x509 Output an X.509 certificate structure instead of a cert request
-CA infile Issuer cert to use for signing a cert, implies -x509
-CAkey val Issuer private key to use with -CA; default is -CA arg
(Required by some CA's)
-subj val Set or modify subject of request or cert
-subject Print the subject of the output request or cert
-multivalue-rdn Deprecated; multi-valued RDNs support is always on.
-days +int Number of days cert is valid for
-set_serial val Serial number to use
-copy_extensions val copy extensions from request when using -x509
-addext val Additional cert extension key=value pair (may be given more than once)
-extensions val Cert extension section (override value in config file)
-reqexts val Request extension section (override value in config file)
-precert Add a poison extension to the generated cert (implies -new)
Keys and Signing options:
-key val Key for signing, and to include unless -in given
-keyform format Key file format (ENGINE, other values ignored)
-pubkey Output public key
-keyout outfile File to write private key to
-passin val Private key and certificate password source
-passout val Output file pass phrase source
-newkey val Generate new key with [<alg>:]<nbits> or <alg>[:<file>] or param:<file>
-pkeyopt val Public key options as opt:value
-sigopt val Signature parameter in n:v form
-vfyopt val Verification parameter in n:v form
-* Any supported digest
Output options:
-out outfile Output file
-outform PEM|DER Output format - DER or PEM
-batch Do not ask anything during request generation
-verbose Verbose output
-noenc Don't encrypt private keys
-nodes Don't encrypt private keys; deprecated
-noout Do not output REQ
-newhdr Output "NEW" in the header lines
-modulus RSA modulus
Random state options:
-rand val Load the given file(s) into the random number generator
-writerand outfile Write random data to the specified file
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
zzh@ZZHPC:~$ openssl x509 --help
Usage: x509 [options]
General options:
-help Display this summary
-in infile Certificate input, or CSR input file with -req (default stdin)
-passin val Private key and cert file pass-phrase source
-new Generate a certificate from scratch
-x509toreq Output a certification request (rather than a certificate)
-req Input is a CSR file (rather than a certificate)
-copy_extensions val copy extensions when converting from CSR to x509 or vice versa
-inform format CSR input file format (DER or PEM) - default PEM
-vfyopt val CSR verification parameter in n:v form
-key val Key for signing, and to include unless using -force_pubkey
-signkey val Same as -key
-keyform PEM|DER|ENGINE Key input format (ENGINE, other values ignored)
-out outfile Output file - default stdout
-outform format Output format (DER or PEM) - default PEM
-nocert No cert output (except for requested printing)
-noout No output (except for requested printing)
Certificate printing options:
-text Print the certificate in text form
-dateopt val Datetime format used for printing. (rfc_822/iso_8601). Default is rfc_822.
-certopt val Various certificate text printing options
-fingerprint Print the certificate fingerprint
-alias Print certificate alias
-serial Print serial number value
-startdate Print the notBefore field
-enddate Print the notAfter field
-dates Print both notBefore and notAfter fields
-subject Print subject DN
-issuer Print issuer DN
-nameopt val Certificate subject/issuer name printing options
-email Print email address(es)
-hash Synonym for -subject_hash (for backward compat)
-subject_hash Print subject hash value
-subject_hash_old Print old-style (MD5) subject hash value
-issuer_hash Print issuer hash value
-issuer_hash_old Print old-style (MD5) issuer hash value
-ext val Restrict which X.509 extensions to print and/or copy
-ocspid Print OCSP hash values for the subject name and public key
-ocsp_uri Print OCSP Responder URL(s)
-purpose Print out certificate purposes
-pubkey Print the public key in PEM format
-modulus Print the RSA key modulus
Certificate checking options:
-checkend intmax Check whether cert expires in the next arg seconds
Exit 1 (failure) if so, 0 if not
-checkhost val Check certificate matches host
-checkemail val Check certificate matches email
-checkip val Check certificate matches ipaddr
Certificate output options:
-set_serial val Serial number to use, overrides -CAserial
-next_serial Increment current certificate serial number
-days int Number of days until newly generated certificate expires - default 30
-preserve_dates Preserve existing validity dates
-subj val Set or override certificate subject (and issuer)
-force_pubkey infile Place the given key in new certificate
-clrext Do not take over any extensions from the source certificate or request
-extfile infile Config file with X509V3 extensions to add
-extensions val Section of extfile to use - default: unnamed section
-sigopt val Signature parameter, in n:v form
-badsig Corrupt last byte of certificate signature (for test)
-* Any supported digest, used for signing and printing
Micro-CA options:
-CA infile Use the given CA certificate, conflicts with -key
-CAform PEM|DER CA cert format (PEM/DER/P12); has no effect
-CAkey val The corresponding CA key; default is -CA arg
-CAkeyform PEM|DER|ENGINE CA key format (ENGINE, other values ignored)
-CAserial val File that keeps track of CA-generated serial number
-CAcreateserial Create CA serial number file if it does not exist
Certificate trust output options:
-trustout Mark certificate PEM output as trusted
-setalias val Set certificate alias (nickname)
-clrtrust Clear all trusted purposes
-addtrust val Trust certificate for a given purpose
-clrreject Clears all the prohibited or rejected uses of the certificate
-addreject val Reject certificate for a given purpose
Random state options:
-rand val Load the given file(s) into the random number generator
-writerand outfile Write random data to the specified file
-engine val Use engine, possibly a hardware device
Provider options:
-provider-path val Provider load path (must be before 'provider' argument if required)
-provider val Provider to load (can be specified multiple times)
-propquery val Property query used when fetching algorithms
We will use the OpenSSL (https://www.openssl.org/source/) tool to generate self-signed certificates. A certificate authority (CA) is responsible for storing, signing, and issuing digital certificates. This means we will first generate a private key and a self-signed certificate for the certificate authority:
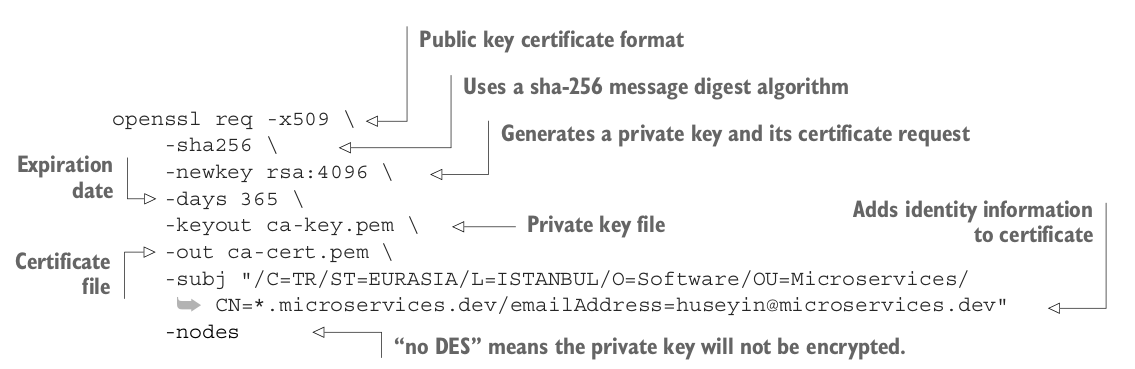
The -subj parameter contains identity information about the certificate:
/C is used for country.
/ST is the state information.
/L states city information.
/O means organization.
/OU is for the organization unit to explain which department.
/CN is used for the domain name, the short version of common name.
/emailAddress is used for an email address to contact the certificate owner.
zzh@ZZHPC:/zdata/Github/grpc-go/server$ openssl req -x509 -newkey rsa:4096 -keyout ca-key.pem -out ca-cert.pem -subj "/C=CN/ST=Tianjin/L=Tianjin/O=ZhangZhihui/OU=AAA/CN=*.ZhangZhihuiAAA.dev/emailAddress=Admin@ZhangZhihuiAAA.dev" -days 365 -nodes -sha256
.+.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.......+.....+...+....+...+..+.....................+............+.......+.....+...............+.+............+..+......+....+........+.+...........+...+.+.....+.........+...+.........................+...+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
...+..+....+.........+..+...+...............+....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.+......+......+.+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.......+..+....+...+......+...........+.........+.+...+..+.+.....+....+........................+....................+.+...........+.........+.+..+.............+..+.+.....+.+........+...+...............+.........+....+......+...+.....+.+..+.......+......+..+............+......+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-----
zzh@ZZHPC:/zdata/Github/grpc-go/server$ lh -rw------- 1 zzh zzh 3.2K Apr 8 17:13 ca-key.pem -rw-rw-r-- 1 zzh zzh 2.2K Apr 8 17:13 ca-cert.pem
You can verify the generated self-certificate for the CA with the following command:
openssl x509 -in ca-cert.pem -noout -text
zzh@ZZHPC:/zdata/Github/grpc-go/server$ openssl x509 -in ca-cert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
75:8b:78:03:fc:39:31:4c:b0:56:78:ed:d1:a2:cd:5d:2f:59:f5:9a
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
Validity
Not Before: Apr 8 09:13:13 2024 GMT
Not After : Apr 8 09:13:13 2025 GMT
Subject: C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:d7:1f:ab:d2:de:df:81:24:88:27:16:6d:8e:da:
fe:19:d3:64:1d:e8:ac:bf:be:71:e9:17:d4:f9:62:
48:b7:4c:23:75:2a:67:30:c6:c0:fc:9b:93:6e:92:
c2:70:ed:44:9d:4a:04:d6:97:af:8b:d8:0b:f8:83:
90:cc:21:98:ca:26:b7:68:91:c6:c6:be:af:23:3f:
......
86:4c:e7
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
C1:6F:C0:F6:81:75:DD:2C:39:CB:AE:41:07:9F:1B:CC:14:F1:37:A8
X509v3 Authority Key Identifier:
C1:6F:C0:F6:81:75:DD:2C:39:CB:AE:41:07:9F:1B:CC:14:F1:37:A8
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
06:49:23:cc:73:67:69:07:8c:ba:18:d2:f9:66:59:7f:98:6a:
64:24:c5:cb:8a:61:ab:07:df:90:9e:c1:69:50:10:23:9d:f0:
9f:47:8f:26:1c:20:1b:84:4b:c3:6d:9d:8b:af:46:b6:cc:5e:
88:af:46:8f:b2:ea:c9:64:d3:ea:38:5f:6f:b7:90:a3:08:f9:
54:73:e6:ff:1f:73:b4:29:20:5b:b5:2e:e0:a5:8a:5c:af:c7:
......
ba:60:02:53:ab:5d:4a:91
Once you verify it, we can proceed with the private key and certificate signing request:
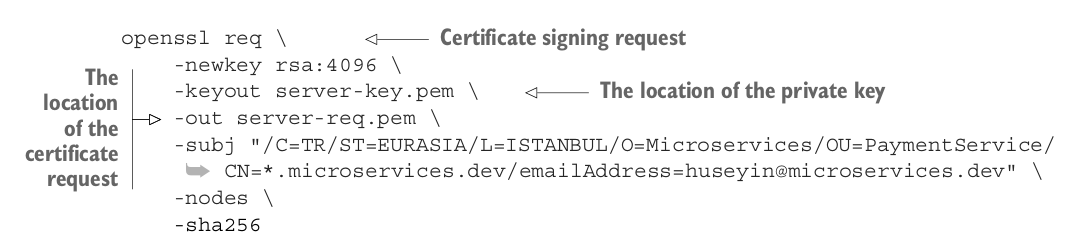
zzh@ZZHPC:/zdata/Github/grpc-go/server$ openssl req -newkey rsa:4096 -keyout server-key.pem -out server-req.pem -subj "/C=CN/ST=Tianjin/L=Tianjin/O=ZhangZhihui/OU=AAA/CN=*.ZhangZhihuiAAA.dev/emailAddress=Admin@ZhangZhihuiAAA.dev" -nodes -sha256
.....+.....+.+...+......+......+.....+...+.+........+......+.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.....+...+.+...........+......+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.........+.+..+....+......+.....+...............+......................+............+........+............+........................+.+...........+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
...+...+..+...+..........+.....+...+...+.......+...+.....+.+......+..+...+..........+.....+....+...+........+...+......+...+..........+..+..................+...+....+...+..+.+..+................+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*....+..+...+......+.+...+......+..+.........+.+............+..+....+..+..........+...+...........+.+........+.+.....+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.......+.+........+...................+...+.....+....+........+...+...+....+......+..+...+.+...+..+.+..+................+......+.....+.+........+.......+........+.........+..........+............+...........+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-----
zzh@ZZHPC:/zdata/Github/grpc-go/server$ lh -rw------- 1 zzh zzh 3.2K Apr 8 17:13 ca-key.pem -rw-rw-r-- 1 zzh zzh 2.2K Apr 8 17:13 ca-cert.pem -rw------- 1 zzh zzh 3.2K Apr 8 17:22 server-key.pem -rw-rw-r-- 1 zzh zzh 1.8K Apr 8 17:22 server-req.pem
Then we will use CA’s private key to sign the request:
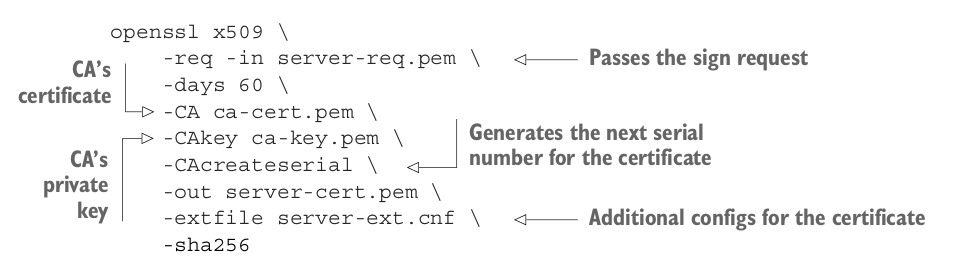
An example configuration for ext file option is as follows:
subjectAltName=DNS:*.microservices.dev,DNS:*.microservices.dev,IP:0.0.0.0
zzh@ZZHPC:/zdata/Github/grpc-go/server$ openssl x509 -req -in server-req.pem -CA ca-cert.pem -CAkey ca-key.pem -CAcreateserial -out server-cert.pem -extfile server-ext.cnf -days 60 -sha256
Certificate request self-signature ok
subject=C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
zzh@ZZHPC:/zdata/Github/grpc-go/server$ lh -rw------- 1 zzh zzh 3.2K Apr 8 17:13 ca-key.pem -rw-rw-r-- 1 zzh zzh 2.2K Apr 8 17:13 ca-cert.pem -rw------- 1 zzh zzh 3.2K Apr 8 17:22 server-key.pem -rw-rw-r-- 1 zzh zzh 1.8K Apr 8 17:22 server-req.pem -rw-rw-r-- 1 zzh zzh 2.1K Apr 8 17:31 server-cert.pem
Now you can verify the server’s self-signed certificate:
openssl x509 -in server-cert.pem -noout -text
zzh@ZZHPC:/zdata/Github/grpc-go/server$ openssl x509 -in server-cert.pem -noout -text
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
7a:21:9a:4f:91:c2:bb:14:d3:cc:ae:51:47:c5:ae:05:0a:db:28:a9
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
Validity
Not Before: Apr 8 03:48:49 2024 GMT
Not After : Jun 7 03:48:49 2024 GMT
Subject: C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:d0:cf:5a:77:f5:0f:19:66:0a:75:ea:3c:ee:b2:
1c:e9:60:3a:c0:5d:af:93:b4:3e:2c:76:31:04:8b:
1b:b0:fd:17:dd:85:d6:4e:6a:97:e6:be:5b:1f:33:
e3:05:45:e1:2b:7e:25:7b:25:a8:b4:0d:cf:69:4a:
4f:24:74:ce:d1:53:85:42:5f:65:3f:08:55:0f:6b:
......
92:0f:d1
Exponent: 65537 (0x10001)
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
3a:b2:67:3c:59:4d:9d:75:e6:a8:39:7d:42:24:72:f7:64:22:
95:71:1a:89:db:d6:31:00:50:3b:a5:93:91:a6:97:90:d7:ec:
8a:da:fe:cb:71:a6:78:0e:72:f3:de:2c:00:32:74:9b:33:39:
73:c4:09:62:79:d1:b3:4b:3d:90:86:da:c7:3f:4d:58:f8:0f:
0c:10:d6:1a:b9:3a:32:0c:25:c4:c8:f8:44:e4:85:fa:74:02:
......
de:82:a8:ff:70:db:b1:ac
For mTLS communication, we need to generate a certificate signing request for the client side, so let’s generate a private key and this self-signed certificate:
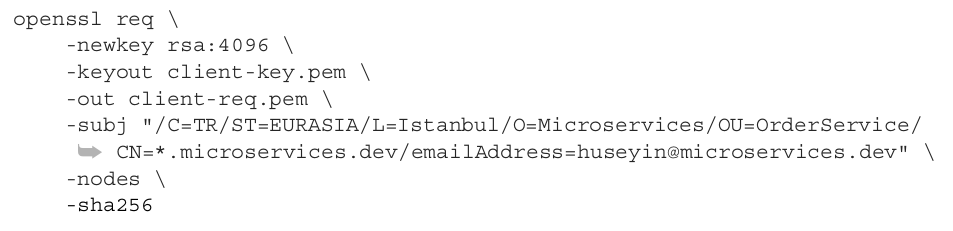
zzh@ZZHPC:/zdata/Github/grpc-go/client$ openssl req -newkey rsa:4096 -keyout client-key.pem -out client-req.pem -subj "/C=CN/ST=Tianjin/L=Tianjin/O=ZhangZhihui/OU=AAA/CN=*.ZhangZhihuiAAA.dev/emailAddress=Admin@ZhangZhihuiAAA.dev" -nodes -sha256
.+.+..+.+..+.......+......+.....+....+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.+....+......+.....+..........+......+.....+....+.....+....+.....+....+.....+.+.........+.....+.+..+..........+.....+..........+..+......+.......+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*...+....+......+...........+....+..+.........+...+.+.....................+........+.......+.........+..+....+.....+...+...+...+.+...+...............+...+..+..........+..+......+...+......................+........+...............+.+..................................................+...+.......+...+...+............+......+..............+.+.........+........+...+............+...+.......+............+............+..............+......+...+......+.+.........+..+...+.+........+..........+..+....+..+.......+..+...+.+.........+...............+........+..................+.+........+.+..+.......+...+........+......+.+............+...+...+.........+...........+.......+..+.+.........+...+..............+....+..+....+...+..+......+.........+.............+............+..................+...........+....+..+.........+......+...............+......+....+.........+.........+.....+..........+..+....+.....+.......+...+..............+......+.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
..+...+..................+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..........+...+...+.....+.+...+..+...................+..+.......+........+...+......+.+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*...+..+.......+......+...+............+........+...............+....+..+.+........+..........+...........+...+.+......+...+.....+.+.....+.+...+...........+............+....+...+........+.........+....+..+...+......+.+...+..............+..........+.....................+.....+......................+........+.+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-----
zzh@ZZHPC:/zdata/Github/grpc-go/client$ lh -rw------- 1 zzh zzh 3.2K Apr 8 17:41 client-key.pem -rw-rw-r-- 1 zzh zzh 1.8K Apr 8 17:41 client-req.pem
Now, let’s sign it using the CA’s private key:
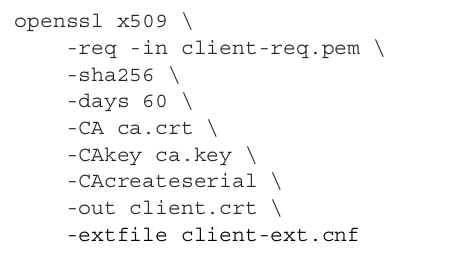
zzh@ZZHPC:/zdata/Github/grpc-go/client$ openssl x509 -req -in client-req.pem -sha256 -days 60 -CA ca.crt -CAkey ca.key -CAcreateserial -out client.crt
Certificate request self-signature ok
subject=C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
Could not open file or uri for loading CA certificate from ca.crt
40571AD16E7A0000:error:16000069:STORE routines:ossl_store_get0_loader_int:unregistered scheme:../crypto/store/store_register.c:237:scheme=file
40571AD16E7A0000:error:80000002:system library:file_open:No such file or directory:../providers/implementations/storemgmt/file_store.c:267:calling stat(ca.crt)
Unable to load CA certificate
zzh@ZZHPC:/zdata/Github/grpc-go/client$ openssl x509 -req -in client-req.pem -CA ../server/ca-cert.pem -CAkey ../server/ca-key.pem -CAcreateserial -out client.crt -days 60 -sha256
Certificate request self-signature ok
subject=C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
zzh@ZZHPC:/zdata/Github/grpc-go/client$ lh -rw------- 1 zzh zzh 3.2K Apr 8 17:41 client-key.pem -rw-rw-r-- 1 zzh zzh 1.8K Apr 8 17:41 client-req.pem -rw-rw-r-- 1 zzh zzh 2.1K Apr 8 17:46 client.crt
Finally, you can verify the client certificate with the following command:
openssl x509 -in client-cert.pem -noout -text
zzh@ZZHPC:/zdata/Github/grpc-go/client$ openssl x509 -in client.crt -noout -text
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
22:e1:af:ac:02:31:ab:13:62:7e:7c:d3:fa:91:60:77:84:9b:f3:26
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
Validity
Not Before: Apr 8 09:46:07 2024 GMT
Not After : Jun 7 09:46:07 2024 GMT
Subject: C = CN, ST = Tianjin, L = Tianjin, O = ZhangZhihui, OU = AAA, CN = *.ZhangZhihuiAAA.dev, emailAddress = Admin@ZhangZhihuiAAA.dev
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:a0:76:c8:b1:a2:51:71:a3:eb:64:ee:fb:d7:86:
20:0c:41:4f:ba:df:e1:f4:d4:14:ab:c1:2c:eb:d3:
97:80:bb:bd:84:ef:06:8f:e6:84:24:01:af:0c:b7:
57:91:33:3b:08:dd:7f:a3:66:12:aa:01:93:6a:c7:
05:78:10:c7:b3:5e:88:5f:36:5b:be:32:43:d3:89:
......
d1:59:0b
Exponent: 65537 (0x10001)
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
13:48:ef:63:86:22:f6:9d:be:96:81:e9:d1:85:9d:bd:4c:04:
b9:6d:2f:97:7d:82:11:e9:fc:dd:54:3e:a0:13:06:13:cd:f3:
ab:e5:07:b9:bd:e7:8f:f9:9b:a7:6f:11:2c:19:c8:8c:f3:28:
16:b4:56:7a:43:e5:31:8a:10:1b:84:50:a5:43:0c:74:0a:69:
65:57:fe:4a:15:3c:75:6d:44:23:d7:79:a7:5f:c4:85:02:46:
......
0e:a8:e0:23:b4:4d:8f:58
zzh@ZZHPC:/zdata/Github/grpc-go/server$ mv server-cert.pem server.crt zzh@ZZHPC:/zdata/Github/grpc-go/server$ mv ca-cert.pem ca.crt
Since the CA signs the certificate, those shared certificates ( client.crt, server.crt) are already in ca.crt.





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律