redis主从复制
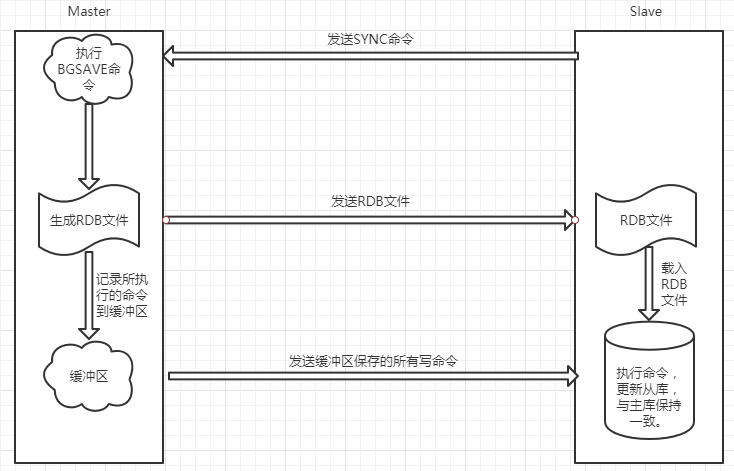
一、redis主从复制原理
1、从服务器向主服务器发送SYNC命令;
2、当主服务器收到SYNC命令后,执行BGSAVE命令,在后台生成RDB文件,使用缓冲区记录从现在开始执行的所有写命令;当主服务器的BGSAVE命令执行完成后,主服务器将BGSAVE命令生成的RDB文件发送给从服务器,从服务器接收并载入RDB文件,将自己的数据库状态更新至主服务器执行BGSAVE命令时的数据库状态。
3、主服务器将记录在缓冲区里所有的写命令发送给从服务器,从服务器执行这些命令,将自己的数据库状态更新至主服务器数据库当前所处状态;
11:01:19.231675 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 780:819, ack 29, win 229, options [nop,nop,TS val 1113163530 ecr 849387959], length 39: RESP "REPLCONF" "ACK" "237147" 11:01:19.232150 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 819, win 235, options [nop,nop,TS val 849388964 ecr 1113163530], length 0 11:01:20.100528 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [P.], seq 29:73, ack 819, win 235, options [nop,nop,TS val 849389833 ecr 1113163530], length 44: RESP "set" "name4" "hello,world1!"
#这是redis主从复制的抓包过程,0.91是从库,0.183是主库;
第一条是从库向主库发送SYNC命令(REPLCONF);
第二条是主库向从库发送RDB文件;
第三条是主库向从库发送写命令(set name4 hello,world!);
二、具体配置方法
1、环境介绍
操作系统:CentOS7.6
Redis版本:redis-5.0.12
主库:192.168.0.183
从库:192.168.0.91
2、配置
2.1、主库配置
#主库配置一个认证密码
requirepass 123.com
2.2、从库配置
# replicaof <masterip> <masterport> replicaof 192.168.0.183 6379 # masterauth <master-password> masterauth 123.com
3、验证
3.1、在主库插入数据
[root@master]# redis
127.0.0.1:6379> auth 123.com
OK
127.0.0.1:6379> set name7 hello,world7!
OK
127.0.0.1:6379> set name8 hello,world8!
OK
127.0.0.1:6379> info replication
# Replication
role:master
connected_slaves:1
slave0:ip=192.168.0.91,port=6379,state=online,offset=254937,lag=0
master_replid:4c33dba5cd92bf97ec4a023d759d82e6ab7080d3
master_replid2:0000000000000000000000000000000000000000
master_repl_offset:254937
second_repl_offset:-1
repl_backlog_active:1
repl_backlog_size:1048576
repl_backlog_first_byte_offset:1
repl_backlog_histlen:254937
3.2、在从库查看
[root@node1 bin]# redis
127.0.0.1:6379> get name7
"hello,world7!"
127.0.0.1:6379> get name8
"hello,world8!"
127.0.0.1:6379> info replication
# Replication
role:slave
master_host:192.168.0.183
master_port:6379
master_link_status:up
master_last_io_seconds_ago:7
master_sync_in_progress:0
slave_repl_offset:254895
slave_priority:100
slave_read_only:1
connected_slaves:0
master_replid:4c33dba5cd92bf97ec4a023d759d82e6ab7080d3
master_replid2:0000000000000000000000000000000000000000
master_repl_offset:254895
second_repl_offset:-1
repl_backlog_active:1
repl_backlog_size:1048576
repl_backlog_first_byte_offset:17852
repl_backlog_histlen:237044
注意:
redis主从同步配置完成后,默认从库是只读的,之所以这样是为了保持主从之间数据的一致性;
三、redis的心跳探测
14:44:19.953848 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 156:195, ack 1, win 229, options [nop,nop,TS val 1126544252 ecr 862768673], length 39: RESP "REPLCONF" "ACK" "255945" 14:44:19.954432 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 195, win 235, options [nop,nop,TS val 862769683 ecr 1126544252], length 0 14:44:20.962297 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 195:234, ack 1, win 229, options [nop,nop,TS val 1126545261 ecr 862769683], length 39: RESP "REPLCONF" "ACK" "255945" 14:44:20.962717 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 234, win 235, options [nop,nop,TS val 862770692 ecr 1126545261], length 0 14:44:21.645281 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [P.], seq 1:15, ack 234, win 235, options [nop,nop,TS val 862771374 ecr 1126545261], length 14: RESP "PING" 14:44:21.645381 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [.], ack 15, win 229, options [nop,nop,TS val 1126545944 ecr 862771374], length 0 14:44:21.970501 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 234:273, ack 15, win 229, options [nop,nop,TS val 1126546269 ecr 862771374], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:21.970996 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 273, win 235, options [nop,nop,TS val 862771700 ecr 1126546269], length 0 14:44:22.979998 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 273:312, ack 15, win 229, options [nop,nop,TS val 1126547278 ecr 862771700], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:22.980590 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 312, win 235, options [nop,nop,TS val 862772709 ecr 1126547278], length 0 14:44:23.989624 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 312:351, ack 15, win 229, options [nop,nop,TS val 1126548288 ecr 862772709], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:23.990111 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 351, win 235, options [nop,nop,TS val 862773719 ecr 1126548288], length 0 14:44:24.998048 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 351:390, ack 15, win 229, options [nop,nop,TS val 1126549297 ecr 862773719], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:24.998808 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 390, win 235, options [nop,nop,TS val 862774727 ecr 1126549297], length 0 14:44:26.007953 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 390:429, ack 15, win 229, options [nop,nop,TS val 1126550306 ecr 862774727], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:26.008612 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 429, win 235, options [nop,nop,TS val 862775737 ecr 1126550306], length 0 14:44:27.014995 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 429:468, ack 15, win 229, options [nop,nop,TS val 1126551313 ecr 862775737], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:27.015458 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 468, win 235, options [nop,nop,TS val 862776744 ecr 1126551313], length 0 14:44:28.021899 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 468:507, ack 15, win 229, options [nop,nop,TS val 1126552320 ecr 862776744], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:28.022414 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 507, win 235, options [nop,nop,TS val 862777751 ecr 1126552320], length 0 14:44:29.029020 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 507:546, ack 15, win 229, options [nop,nop,TS val 1126553327 ecr 862777751], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:29.029532 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 546, win 235, options [nop,nop,TS val 862778758 ecr 1126553327], length 0 14:44:30.036071 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 546:585, ack 15, win 229, options [nop,nop,TS val 1126554335 ecr 862778758], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:30.036570 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 585, win 235, options [nop,nop,TS val 862779765 ecr 1126554335], length 0 14:44:31.042853 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 585:624, ack 15, win 229, options [nop,nop,TS val 1126555341 ecr 862779765], length 39: RESP "REPLCONF" "ACK" "255959" 14:44:31.043525 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 624, win 235, options [nop,nop,TS val 862780772 ecr 1126555341], length 0 14:44:31.730521 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [P.], seq 15:29, ack 624, win 235, options [nop,nop,TS val 862781459 ecr 1126555341], length 14: RESP "PING" 14:44:31.730616 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [.], ack 29, win 229, options [nop,nop,TS val 1126556029 ecr 862781459], length 0 14:44:32.050120 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 624:663, ack 29, win 229, options [nop,nop,TS val 1126556349 ecr 862781459], length 39: RESP "REPLCONF" "ACK" "255973" 14:44:32.050578 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 663, win 235, options [nop,nop,TS val 862781779 ecr 1126556349], length 0 14:44:33.056403 IP 192.168.0.91.53232 > 192.168.0.183.6379: Flags [P.], seq 663:702, ack 29, win 229, options [nop,nop,TS val 1126557355 ecr 862781779], length 39: RESP "REPLCONF" "ACK" "255973" 14:44:33.056918 IP 192.168.0.183.6379 > 192.168.0.91.53232: Flags [.], ack 702, win 235, options [nop,nop,TS val 862782786 ecr 1126557355], length 0
通过抓包,可以看到,一旦主从同步完成,主库会每隔10s发起一次PING包,来探测从库是否存活;
配置文件中,心跳机制的时间是由repl-ping-replica-period参数来控制的,默认10s;




 浙公网安备 33010602011771号
浙公网安备 33010602011771号