SSH Weak Algorithms Supported
1. 漏洞报告
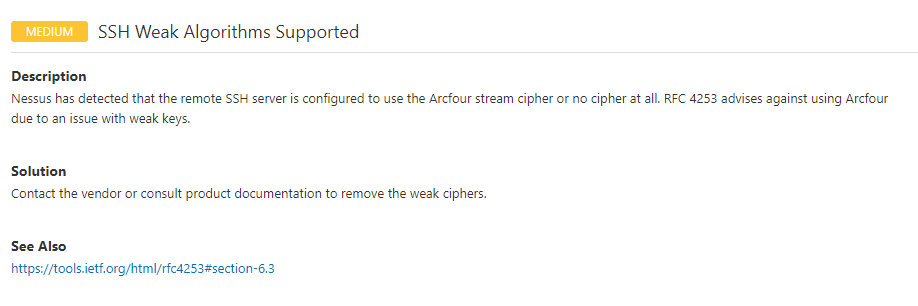
2. 漏洞介绍
在密码学领域,RC4( 又名ARC4 或者ARCFOUR )是应用最广泛的流加密算法,应用在安全套接字层和WEP上。它加解密使用相同的密钥,因此也属于对称加密算法。RC4是由罗纳德·李维斯特在1987年开发出来的,开始时是商业密码,没有公开发表出来,但是在1994年9月份的时候,它被人匿名公开在了Cypherpunks 邮件列表上,很快它就被发到了sci.crypt 新闻组上,随后从这传播到了互联网的许多站点。随之贴出的代码后来被证明是真实的,因为它的输出跟取得了RC4版权的私有软件的输出是完全相同的。由于算法已经公开,RC4也就不再是商业秘密了,只是它的名字“RC4”仍然是一个注册商标。分布式代码管理网站Github从2015年1月5日将停止对RC4的支持,RC4作为一种老旧的验证和加密算法易于受到黑客攻击。这意味着,用户在使用Windows XP系统上的IE浏览器时将无法进入github.com网站。
3. 漏洞危害
由于RC4算法加密是采用的xor,所以,一旦子密钥序列出现了重复,密文就有可能被破解。2015年,比利时鲁汶大学的研究人员Mathy Vanhoef及Frank Piessens,公布了针对RC4加密算法的新型攻击程式,可在75小时内取得cookie的内容。
4. 漏洞检测
λ nmap --script="ssh2-enum-algos" -p 22 192.168.43.58
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-20 18:29 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.43.58
Host is up (0.0013s latency).
PORT STATE SERVICE
22/tcp open ssh
| ssh2-enum-algos:
| kex_algorithms: (4)
| diffie-hellman-group-exchange-sha256
| diffie-hellman-group-exchange-sha1
| diffie-hellman-group14-sha1
| diffie-hellman-group1-sha1
| server_host_key_algorithms: (2)
| ssh-rsa
| ssh-dss
| encryption_algorithms: (13)
| aes128-cbc
| 3des-cbc
| blowfish-cbc
| cast128-cbc
| arcfour128 //******there******//
| arcfour256 //******there******//
| arcfour //******there******//
| aes192-cbc
| aes256-cbc
| rijndael-cbc@lysator.liu.se
| aes128-ctr
| aes192-ctr
| aes256-ctr
| mac_algorithms: (7)
| hmac-md5
| hmac-sha1
| umac-64@openssh.com
| hmac-ripemd160
| hmac-ripemd160@openssh.com
| hmac-sha1-96
| hmac-md5-96
| compression_algorithms: (2)
| none
|_ zlib@openssh.com
MAC Address: 00:0C:29:3E:BA:70 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.39 seconds
5. 漏洞修复
## 将Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
## 添加到/etc/ssh/sshd_config 文件的最后一行,保存后重新启动服务。
root@bee-box:/# tail -1 /etc/ssh/sshd_config
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
root@bee-box:/# /etc/init.d/sshd restart
bash: /etc/init.d/sshd: No such file or directory
root@bee-box:/# /etc/init.d/ssh restart
* Restarting OpenBSD Secure Shell server sshd
## 漏洞复测
λ nmap sS --script="ssl-enum-ciphers" -p 443 182.92.105.110
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-20 18:38 ?D1ú±ê×?ê±??
Nmap scan report for 182.92.105.110
Host is up (0.056s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (secp256r1) - C
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| TLSv1.1:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (secp256r1) - C
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (secp256r1) - C
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
|_ least strength: C
Nmap done: 1 IP address (1 host up) scanned in 14.40 seconds


