TLS Version 1.0 Protocol Detection
1. 漏洞报告
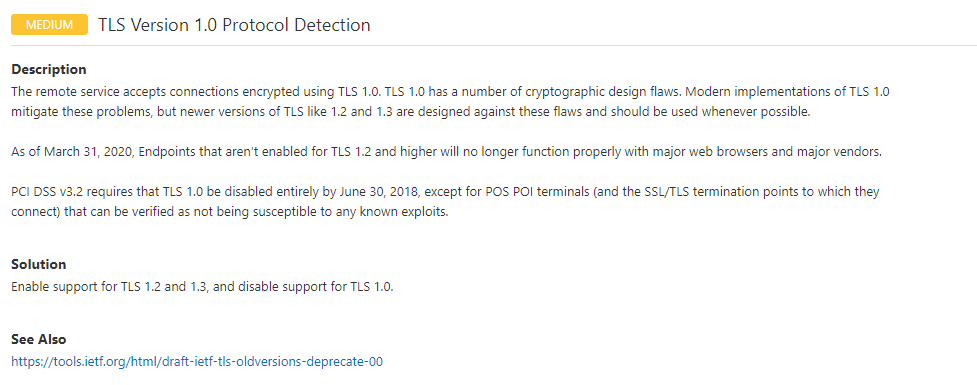
2. 漏洞介绍
SSL经过几年发展,于1999年被IETF纳入标准化,改名叫TLS 1.0,和SSLv3.0相比几乎没有做什么改动。2006年提出了TLS v1.1,修复了一些bug,支持更多参数。2008年提出了TLS v1.2做了更多的扩展和算法改进,是目前(2019年)几乎所有新设备的标配。TLS v1.3在2014年已经提出,2016年开始草案制定,然而由于TLS v1.2的广泛应用,必须要考虑到支持v1.2的网络设备能够兼容v1.3,因此反复修改直到第28个草案才于2018年正式纳入标准。TLSv1.3改善了握手流程,减少了时延,并采用完全前向安全的密钥交换算法。
3. 漏洞危害
远程服务接受使用TLS 1.0加密的连接。TLS 1.0具有许多密码设计缺陷。为了符合支付卡行业数据安全标准(PCI DSS)并符合行业最佳实践,PCI标准规定TLS1 .0安全通信于2018年6月30日不再生效。自2020年3月31日起,尚未启用TLS 1.2及更高版本的端点将不再与主流的Web浏览器和主要的供应商一起正常运行。
4. 漏洞检测
λ nmap -sS --script="ssl-enum-ciphers" -p 443 192.168.43.58
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-20 16:58 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.43.58
Host is up (0.0019s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA - E
| TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA (dh 1024) - D
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) - A
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 1024) - A
| TLS_DHE_RSA_WITH_DES_CBC_SHA (dh 1024) - D
| TLS_RSA_EXPORT_WITH_DES40_CBC_SHA - E
| TLS_RSA_EXPORT_WITH_RC2_CBC_40_MD5 - E
| TLS_RSA_EXPORT_WITH_RC4_40_MD5 - E
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 1024) - D
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_DES_CBC_SHA (rsa 1024) - D
| TLS_RSA_WITH_RC4_128_MD5 (rsa 1024) - D
| TLS_RSA_WITH_RC4_128_SHA (rsa 1024) - D
| compressors:
| NULL
| cipher preference: client
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
| 64-bit block cipher DES vulnerable to SWEET32 attack
| 64-bit block cipher DES40 vulnerable to SWEET32 attack
| 64-bit block cipher RC2 vulnerable to SWEET32 attack
| Broken cipher RC4 is deprecated by RFC 7465
| Ciphersuite uses MD5 for message integrity
| Weak certificate signature: SHA1
|_ least strength: E
MAC Address: 00:0C:29:3E:BA:70 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.30 seconds
5. 漏洞修复
1. Apache 漏洞修复
## 为了对SSLProtocol使用TLSv1.1和TLSv1.2,
## 至少需要Apache 2.2.23版本。
## 至少需要OpenSSL 1.0.1版本。
## 然后将/etc/httpd/conf.d/ssl.conf 修改为 SSLProtocol TLSv1.2。
## 重新启动Apache服务。
## 漏洞复测
λ nmap -sS --script="ssl-enum-ciphers" -p 443 192.168.43.58
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-20 16:58 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.43.58
Host is up (0.0019s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (secp256r1) - C
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| 64-bit block cipher 3DES vulnerable to SWEET32 attack
|_ least strength: C
MAC Address: 00:0C:29:3E:BA:70 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.30 seconds


