Saltstack_使用指南18_API
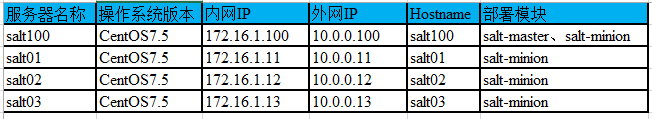
1. 主机规划
salt 版本
1 [root@salt100 ~]# salt --version 2 salt 2018.3.3 (Oxygen) 3 [root@salt100 ~]# salt-minion --version 4 salt-minion 2018.3.3 (Oxygen)
netapi modules
https://docs.saltstack.com/en/latest/ref/netapi/all/index.html
rest_cherrypy
https://docs.saltstack.com/en/latest/ref/netapi/all/salt.netapi.rest_cherrypy.html
文章参考:
参考GitHub
https://github.com/yueyongyue/saltshaker
2. 必要的准备
2.1. 安装部署Python3
1 [root@salt100 Python-3.7.3]# yum install -y libffi-devel # 提前安装 2 [root@salt100 Python-3.7.3]# pwd 3 /root/software/ 4 [root@salt100 software]# ll 5 total 22436 6 -rw-r--r-- 1 root root 22973527 Apr 1 00:15 Python-3.7.3.tgz 7 [root@salt100 software]# tar xf Python-3.7.3.tgz 8 [root@salt100 software]# cd Python-3.7.3/ 9 [root@salt100 Python-3.7.3]# ./configure # 配置 10 [root@salt100 Python-3.7.3]# make && make install # 编译 与 安装 11 # 建立软连接 12 [root@salt100 ~]# ln -s /usr/local/bin/python3.7 /usr/bin/python3 13 [root@salt100 ~]# ll /usr/bin/python3 14 lrwxrwxrwx 1 root root 24 Apr 1 20:33 /usr/bin/python3 -> /usr/local/bin/python3.7
2.2. 安装salt-api
等到配置完毕后才能启动salt-api
1 [root@salt100 ~]# yum install -y salt-api 2 [root@salt100 ~]# systemctl enable salt-api.service # 开机自启动
2.3. 新建saltapi用户
[root@salt100 ~]# useradd -M -s /sbin/nologin -u 1010 saltapi && echo '123456' | /usr/bin/passwd --stdin saltapi
2.4. 安装pip和CherryPy
1 [root@salt100 software]# wget https://bootstrap.pypa.io/get-pip.py 2 [root@salt100 software]# python3 get-pip.py 3 [root@salt100 software]# pip -V # 查看pip版本 4 [root@salt100 software]# pip install CherryPy==3.2.6 # 注意版本
3. 添加https证书
1 [root@salt100 certs]# pwd 2 /etc/pki/tls/certs 3 [root@salt100 certs]# ll 4 total 12 5 lrwxrwxrwx. 1 root root 49 Nov 14 05:41 ca-bundle.crt -> /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem 6 lrwxrwxrwx. 1 root root 55 Nov 14 05:41 ca-bundle.trust.crt -> /etc/pki/ca-trust/extracted/openssl/ca-bundle.trust.crt 7 -rwxr-xr-x. 1 root root 610 Apr 11 2018 make-dummy-cert 8 -rw-r--r--. 1 root root 2516 Apr 11 2018 Makefile 9 -rwxr-xr-x. 1 root root 829 Apr 11 2018 renew-dummy-cert 10 [root@salt100 certs]# make testcert 11 umask 77 ; \ 12 /usr/bin/openssl genrsa -aes128 2048 > /etc/pki/tls/private/localhost.key 13 Generating RSA private key, 2048 bit long modulus 14 .........................................................................+++ 15 ........................+++ 16 e is 65537 (0x10001) 17 Enter pass phrase: # 键入加密短语 18 Verifying - Enter pass phrase: # 确认加密短语 19 umask 77 ; \ 20 /usr/bin/openssl req -utf8 -new -key /etc/pki/tls/private/localhost.key -x509 -days 365 -out /etc/pki/tls/certs/localhost.crt 21 Enter pass phrase for /etc/pki/tls/private/localhost.key: # 再次输入相同的加密短语 22 You are about to be asked to enter information that will be incorporated 23 into your certificate request. 24 What you are about to enter is what is called a Distinguished Name or a DN. 25 There are quite a few fields but you can leave some blank 26 For some fields there will be a default value, 27 If you enter '.', the field will be left blank. 28 ----- 29 Country Name (2 letter code) [XX]: 30 State or Province Name (full name) []: 31 Locality Name (eg, city) [Default City]: 32 Organization Name (eg, company) [Default Company Ltd]: 33 Organizational Unit Name (eg, section) []: 34 Common Name (eg, your name or your server's hostname) []: 35 Email Address []: 36 [root@salt100 certs]# ll 37 total 16 38 lrwxrwxrwx. 1 root root 49 Nov 14 05:41 ca-bundle.crt -> /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem 39 lrwxrwxrwx. 1 root root 55 Nov 14 05:41 ca-bundle.trust.crt -> /etc/pki/ca-trust/extracted/openssl/ca-bundle.trust.crt 40 -rw------- 1 root root 1220 Mar 31 22:53 localhost.crt 41 -rwxr-xr-x. 1 root root 610 Apr 11 2018 make-dummy-cert 42 -rw-r--r--. 1 root root 2516 Apr 11 2018 Makefile 43 -rwxr-xr-x. 1 root root 829 Apr 11 2018 renew-dummy-cert 44 [root@salt100 certs]# cd /etc/pki/tls/private/ # 进入目录 45 [root@salt100 private]# ll 46 total 4 47 -rw------- 1 root root 1766 Mar 31 22:52 localhost.key 48 [root@salt100 private]# openssl rsa -in localhost.key -out localhost_nopass.key # 生成无密码秘钥 49 Enter pass phrase for localhost.key: # 输入和之前一样的加密短语 50 writing RSA key 51 [root@salt100 private]# ll 52 total 8 53 -rw------- 1 root root 1766 Mar 31 22:52 localhost.key 54 -rw-r--r-- 1 root root 1679 Mar 31 22:56 localhost_nopass.key
4. 添加配置文件
配置文件存放位置
1 [root@salt100 ~]# vim /etc/salt/master 2 ##### Primary configuration settings ##### 3 ########################################## 4 # This configuration file is used to manage the behavior of the Salt Master. 5 # Values that are commented out but have an empty line after the comment are 6 # defaults that do not need to be set in the config. If there is no blank line 7 # after the comment then the value is presented as an example and is not the 8 # default. 9 10 # Per default, the master will automatically include all config files 11 # from master.d/*.conf (master.d is a directory in the same directory 12 # as the main master config file). 13 #default_include: master.d/*.conf # 默认配置即可 14 …………
添加配置文件
1 [root@salt100 master.d]# pwd 2 /etc/salt/master.d 3 [root@salt100 master.d]# ll 4 total 8 5 -rw-r--r-- 1 root root 126 Mar 31 23:29 api.conf 6 -rw-r--r-- 1 root root 239 Mar 31 23:38 eauth.conf 7 [root@salt100 master.d]# cat eauth.conf 8 external_auth: 9 pam: 10 saltapi: 11 - .* 12 - '@wheel' # to allow access to all wheel modules 13 - '@runner' # to allow access to all runner modules 14 - '@jobs' # to allow access to the jobs runner and/or wheel module 15 [root@salt100 master.d]# cat api.conf 16 rest_cherrypy: 17 port: 8000 18 ssl_crt: /etc/pki/tls/certs/localhost.crt 19 ssl_key: /etc/pki/tls/private/localhost_nopass.key
5. 重启salt-master
[root@salt100 ~]# systemctl restart salt-master.service # 使配置生效
6. 启动salt-api
1 [root@salt100 master.d]# systemctl start salt-api.service 2 [root@salt100 ~]# netstat -lntup | grep 'salt' # 端口查看 3 tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 22078/salt-api 4 tcp 0 0 0.0.0.0:4505 0.0.0.0:* LISTEN 19802/salt-master Z 5 tcp 0 0 0.0.0.0:4506 0.0.0.0:* LISTEN 19808/salt-master M
7. 使用PAM进行登录验证
1 [root@salt100 master.d]# curl -k https://172.16.1.100:8000/login \ 2 -H 'Accept: application/x-yaml' \ 3 -d username='saltapi' \ 4 -d password='123456' \ 5 -d eauth='pam' 6 return: 7 - eauth: pam 8 expire: 1554173316.621825 9 perms: 10 - .* 11 - '@wheel' 12 - '@runner' 13 - '@jobs' 14 start: 1554130116.621824 15 token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a 16 user: saltapi
这个token使我们需要的,方便后文操作
8. 得到指定minion的grains信息
1 [root@salt100 master.d]# curl -k https://172.16.1.100:8000/minions/salt01 \ 2 -H 'Accept: application/x-yaml' \ 3 -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a' 4 ## 返回如下信息 5 return: 6 - salt01: 7 SSDs: [] 8 biosreleasedate: 05/19/2017 9 biosversion: '6.00' 10 cpu_flags: 11 ………………
9. 获取minion状态【上下线状态】
1 ## 备注: client='runner' 代表在master执行 client='local' 代表在minion执行 2 [root@salt100 ~]# curl -k https://172.16.1.100:8000/ \ 3 -H 'Accept: application/x-yaml' \ 4 -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a' \ 5 -d client='runner' \ 6 -d fun='manage.status' 7 ## 返回如下信息 8 return: 9 - down: [] 10 up: 11 - salt01 12 - salt02 13 - salt03 14 - salt100
10. test.ping测试
1 curl -k https://172.16.1.100:8000 \ 2 -H 'Accept: application/x-yaml' \ 3 -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a'\ 4 -d client=local \ 5 -d tgt='*' \ 6 -d fun=test.ping 7 ## 返回如下信息 8 return: 9 - salt01: true 10 salt02: true 11 salt03: true 12 salt100: true
11. 查看jobs信息
在标签1执行
[root@salt100 ~]# salt 'salt01' cmd.run 'whoami && sleep 300'
在标签2执行
1 [root@salt100 ~]# curl -k https://172.16.1.100:8000/jobs \ 2 > -H 'Accept: application/x-yaml' \ 3 > -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a' 4 return: 5 - '20190401225621862530': 6 Arguments: [] 7 Function: test.ping 8 StartTime: 2019, Apr 01 22:56:21.862530 9 Target: '*' 10 Target-type: glob 11 User: sudo_yun 12 '20190401232000770358': 13 Arguments: [] 14 Function: test.ping 15 StartTime: 2019, Apr 01 23:20:00.770358 16 Target: '*' 17 Target-type: glob 18 User: saltapi 19 '20190401232353892493': 20 Arguments: 21 - whoami && sleep 300 22 Function: cmd.run 23 StartTime: 2019, Apr 01 23:23:53.892493 24 Target: salt01 25 Target-type: glob 26 User: sudo_yun 27 '20190401232358925816': 28 Arguments: 29 - '20190401232353892493' 30 Function: saltutil.find_job 31 StartTime: 2019, Apr 01 23:23:58.925816 32 Target: 33 - salt01 34 Target-type: list 35 User: sudo_yun 36 '20190401232406139505': 37 Arguments: [] 38 Function: saltutil.running 39 StartTime: 2019, Apr 01 23:24:06.139505 40 Target: '*' 41 Target-type: glob 42 User: root 43 '20190401232408955596': 44 Arguments: 45 - '20190401232353892493' 46 Function: saltutil.find_job 47 StartTime: 2019, Apr 01 23:24:08.955596 48 Target: 49 - salt01 50 Target-type: list 51 User: sudo_yun 52 '20190401232418970482': 53 Arguments: 54 - '20190401232353892493' 55 Function: saltutil.find_job 56 StartTime: 2019, Apr 01 23:24:18.970482 57 Target: 58 - salt01 59 Target-type: list 60 User: sudo_yun 61 [root@salt100 ~]# 62 [root@salt100 ~]# curl -k https://172.16.1.100:8000/jobs/20190401232353892493 \ 63 -H 'Accept: application/x-yaml' \ 64 -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a' 65 ## 返回如下信息 66 info: 67 - Arguments: 68 - whoami && sleep 300 69 Function: cmd.run 70 Minions: 71 - salt01 72 Result: {} 73 StartTime: 2019, Apr 01 23:23:53.892493 74 Target: salt01 75 Target-type: glob 76 User: sudo_yun 77 jid: '20190401232353892493' 78 return: 79 - {}
12. 其他常用操作
1 # salt 'salt01' state.sls web.apache ,执行 apache.sls # yum 部署httpd 2 curl -k https://172.16.1.100:8000/ \ 3 -H 'Accept: application/x-yaml' \ 4 -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a' \ 5 -d client=local \ 6 -d tgt='salt01' \ 7 -d fun=state.sls \ 8 -d arg='web.apache' 9 10 11 # salt -L 'salt01,salt02,salt03' test.ping 12 curl -k https://172.16.1.100:8000 \ 13 -H 'Accept: application/x-yaml' \ 14 -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a'\ 15 -d client=local \ 16 -d tgt='salt01,salt02,salt03' \ 17 -d expr_form='list' \ 18 -d fun=test.ping 19 20 21 # salt -G 'host:salt01' cmd.run ifconfig 22 curl -k https://172.16.1.100:8000 \ 23 -H 'Accept: application/x-yaml' \ 24 -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a'\ 25 -d client=local \ 26 -d tgt='host:salt01' \ 27 -d expr_form='grain' \ 28 -d fun=cmd.run \ 29 -d arg='ifconfig' 30 31 32 # 以json格式输出 33 # salt -G 'host:salt01' cmd.run ifconfig 34 curl -k https://172.16.1.100:8000 \ 35 -H 'Accept: application/json' \ 36 -H 'X-Auth-Token: 6bb11fd17c3476cb7d07373113c93faaa9c27f9a'\ 37 -d client=local \ 38 -d tgt='host:salt01' \ 39 -d expr_form='grain' \ 40 -d fun=cmd.run \ 41 -d arg='ifconfig'
13. 参数解释
1 client : 模块,python处理salt-api的主要模块,‘client interfaces <netapi-clients>’ 2 local : 使用‘LocalClient <salt.client.LocalClient>’ 发送命令给受控主机,等价于saltstack命令行中的'salt'命令 3 local_async : 和local不同之处在于,这个模块是用于异步操作的,即在master端执行命令后返回的是一个jobid,任务放在后台运行,通过产看jobid的结果来获取命令的执行结果。 4 runner : 使用'RunnerClient<salt.runner.RunnerClient>' 调用salt-master上的runner模块,等价于saltstack命令行中的'salt-run'命令 5 runner_async : 异步执行runner模块 6 wheel : 使用'WheelClient<salt.wheel.WheelClient>', 调用salt-master上的wheel模块,wheel模块没有在命令行端等价的模块,但它通常管理主机资源,比如文件状态,pillar文件,salt配置文件,以及关键模块<salt.wheel.key>功能类似于命令行中的salt-key。 7 wheel_async : 异步执行wheel模块 8 备注:一般情况下local模块,需要tgt和arg(数组),kwarg(字典),因为这些值将被发送到minions并用于执行所请求的函数。而runner和wheel都是直接应用于master,不需要这些参数。 9 tgt : minions 10 fun : 函数 11 arg : 参数 12 expr_form : tgt的匹配规则 13 'glob' - Bash glob completion - Default 14 'pcre' - Perl style regular expression 15 'list' - Python list of hosts 16 'grain' - Match based on a grain comparison 17 'grain_pcre' - Grain comparison with a regex 18 'pillar' - Pillar data comparison 19 'nodegroup' - Match on nodegroup 20 'range' - Use a Range server for matching 21 'compound' - Pass a compound match string




