部署ingress及使用
一、下载yaml文件 https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/mandatory.yaml # 国内需要修改镜像
#修改amndatory.yaml文件(211行)使用宿主机网络:hostNetwork: true serviceAccountName: nginx-ingress-serviceaccount hostNetwork: true #添加这行 containers:
二、导入yaml文件 kubectl apply -f mandatory.yaml #查看 [root@k8s-m yaml]# kubectl get pods -n ingress-nginx NAME READY STATUS RESTARTS AGE nginx-ingress-controller-766c77b7d4-nn4c7 1/1 Running 0 49s 三、# 创建一个基于service和Deployment [root@k8s-m yaml]# cat ingress-deploy-demo.yaml apiVersion: v1 kind: Service metadata: name: nginx-svc spec: selector: #标签选择 name: nginx ports: - port: 80 #服务器端口 name: http #名称 targetPort: 80 #容器端口 protocol: TCP #协议,默认TCP --- apiVersion: apps/v1 kind: Deployment metadata: name: my-nginx-deploy spec: replicas: 3 selector: matchLabels: name: nginx template: metadata: labels: name: nginx spec: containers: - name: nginx image: nginx:alpine #镜像 ports: - name: http containerPort: 80 #容器端口 #导入yaml文件 [root@k8s-m yaml]# kubectl apply -f ingress-deploy-demo.yaml service/nginx-svc unchanged deployment.apps/my-nginx-deploy created #查看 [root@k8s-m yaml]# kubectl get pods NAME READY STATUS RESTARTS AGE my-nginx-deploy-799879696c-7rlhl 1/1 Running 0 41s my-nginx-deploy-799879696c-99v5g 1/1 Running 0 41s my-nginx-deploy-799879696c-ljqjd 1/1 Running 0 41s [root@k8s-m yaml]# kubectl get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 44m nginx-svc ClusterIP 10.96.182.50 <none> 80/TCP 3m43s # 创建一个 基于 my-nginx-deploy的 ingress [root@k8s-m yaml]# cat nginx-ingress.yaml apiVersion: extensions/v1beta1 kind: Ingress metadata: name: ingress-nginx spec: rules: - host: haha.zhang.com http: paths: - backend: serviceName: nginx-svc servicePort: 80 #查看 [root@k8s-m yaml]# kubectl get ingress NAME HOSTS ADDRESS PORTS AGE ingress-nginx haha.zhang.com 80 21s #测试 [root@k8s-m yaml]# curl haha.zhang.com -I HTTP/1.1 200 OK Server: nginx Date: Thu, 20 Dec 2018 07:01:18 GMT Content-Type: text/html Connection: keep-alive Keep-Alive: timeout=20 X-DIS-Request-ID: e21475c0d2fa20399819dbb15f21304a P3P: CP="NON DSP COR ADMa OUR IND UNI COM NAV INT" Cache-Control: no-cache
HTTPS
[root@k8s-m yaml]# cat ssl-www.yaml
apiVersion: v1
kind: Service
metadata:
name: ssl-www
namespace: default
spec:
selector:
app: myhttps
ports:
- name: http
targetPort: 80
port: 80
- name: https
targetPort: 443
port: 443
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: myapp-deploy
namespace: default
spec:
replicas: 3
selector:
matchLabels:
app: myhttps
template:
metadata:
labels:
app: myhttps
spec:
containers:
- name: myhttps
image: nginx:alpine
ports:
- name: http
containerPort: 80
- name: https
containerPort: 443
#导入
kubectl apply -f ssl-www.yaml
二、创建ssl的证书
# 创建一个基于自身域名的证书
openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -keyout hahassl.zhang.me-key.key -out hahassl.zhang.me.pem -subj "/CN=hahassl.zhang.me"
# 导入 域名的证书到secret 中
kubectl create secret tls hahassl-secret --cert hahassl.zhang.me.pem --key hahassl.zhang.me-key.key
#查看
[root@k8s-m x2]# kubectl get secret -n kube-system|grep haha
hahassl-secret kubernetes.io/tls 2 42s
#配置https的ingress
[root@k8s-m yaml]# cat https-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: https-www
spec:
tls:
- hosts:
- hahassl.zhang.me
secretName: hahassl-secret
rules:
- host: hahassl.zhang.me
http:
paths:
- path: /
backend:
serviceName: ssl-www
servicePort: 443
backend:
serviceName: ssl-www
servicePort: 80
#导入
kubectl apply -f https-ingress.yaml
#配置hosts解析(解析为宿主机的公网ip)
#访问
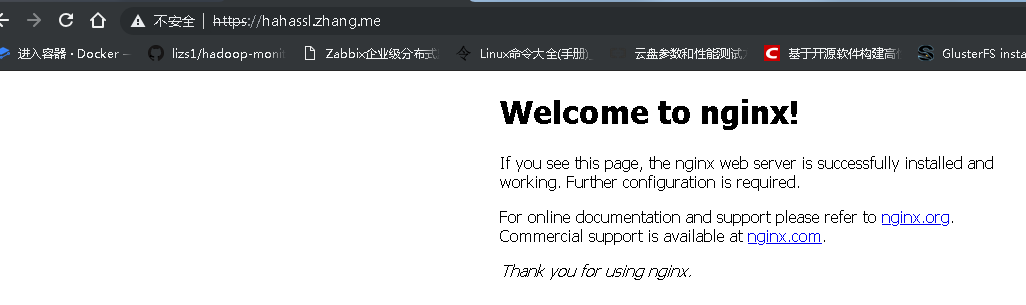
[root@k8s-m yaml]# curl -k -I https://hahassl.zhang.me
HTTP/1.1 200 OK
Server: nginx/1.15.6
Date: Sat, 29 Dec 2018 05:48:00 GMT
Content-Type: text/html
Content-Length: 612
Connection: keep-alive
Vary: Accept-Encoding
Last-Modified: Wed, 26 Dec 2018 23:21:49 GMT
ETag: "5c240d0d-264"
Accept-Ranges: bytes
Strict-Transport-Security: max-age=15724800; includeSubDomains
#浏览器访问