tcpdump
tcpdump
一款可以根据使用者定义的规则对网络上的数据包进行截获的包分析工具。
使用场景
- 网络应用程序崩溃时,需要确认应用程序收发的数据包格式和内容是否符合设计规范;
- 网络应用程序响应慢,需要确认是否存在网络传输问题或者程序对于输入数据处理慢;
- 用户无法使用网络应用程序时,需要判断是否存在网络连通性问题
- 服务器受到网络攻击时,需要分析攻击包的格式和内容,以便采取针对性措施
tcpdump的工作原理
Telnet、TFTP等应用程序的网络通信收发数据,会通过完整的Linux网络协议栈,由操作系统完成数据的封装和解封装,应用程序只需要对应用层的数据进行读写,不需要关心TCP、IP以及数据链路层的头部封装和解封装。
下图为基于TCP的客户端和应用程序间的调用
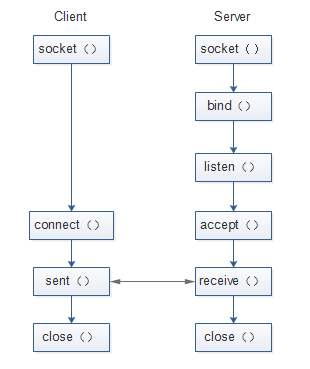
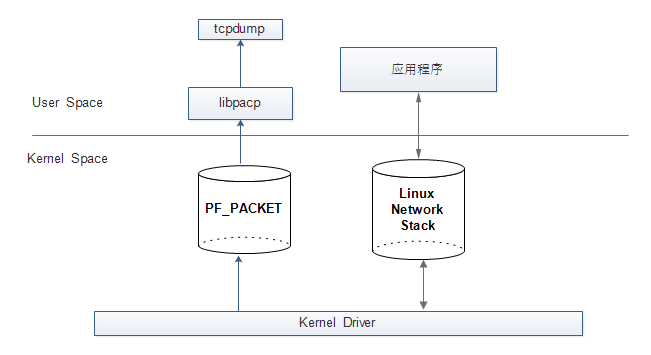
tcpdump是依赖的libpacp,libpacp使用的是设备层的包接口,这种技术使应用程序直接读写内核驱动层的数据,而不经过完整的Linux网络协议栈。
PF_PACKET套接口被用于接受和发送在设备驱动层的数据包
下图为tcpdump的工作原理:
tcpdump和iptables的关系
tcpdump能否抓取到被 iptables 的INPUT和OUTPUT禁止的数据包?
由于iptables依赖的netfilter模块,该模块工作在Linux的网络协议栈内,所以,iptables 的入栈策略不会对tcpdump抓取产生影响。但是iptables的出栈策略OUTPUT会将数据包发送到网络驱动层,所以对tcpdump产生影响。
- tcpdump可以抓取到被 iptables 在INPUT链上DROP的数据包
- tcpdump不可以抓取到被 iptables 在OUTPUT链上DROP的数据包
tcpdump的常用参数
| 参数名称 | 参数作用 |
| -i | 指定需要抓包的网卡。缺省时,tcpdump会自动搜索系统中状态为UP的最小数字的网卡 一般为eth0 |
| -nnn | 禁用tcpdump展示结果时,把IP、port转换成域名、端口对应服务名 |
| -w | 将结果保存到文件中,一般为.cap文件,以便wireshark可以进行分析 |
| -s | 指定抓包的大小,使用-s 0指定数据包大小为262144字节,可以使抓到的数据包不被截断 |
| -c | 指定抓包的数量 |
|
|
| -S | 使用绝对数值而非相对数值显示TCP关联数 |
|
|
tcpdump关键字
| 关键字 | 作用 | 举例 |
| host | 指定某一主机 | host 22.224.241.17 |
| net | 指明一个网络地址 | net 10.0.0.0 |
| port | 指明端口号 | tcp port 22 |
| src | 指明数据包源地址 | src 22.224.241.17 |
| dst | 指定目的地址 |
dst net 10.0.0.0 |
| dst or src | 缺省值 | |
| dst and src | ||
| fddi | ||
| ip | ||
| icmp | ||
| tcp | ||
| udp | ||
| arp | ||
| rarp | ||
| gateway | ||
| broadcast | ||
| 逻辑表达式,使用多个条件时要用括号 | ||
| && and | 与 | |
| ! not | 非 | |
| || or | 或 |
语法及举例
语法
先写参数,再写表达式
tcpdump [ -AbdDefhHIJKlLnNOpqStuUvxX# ] [ -B buffer_size ] [ -c count ] [ -C file_size ] [ -G rotate_seconds ] [ -F file ] [ -i interface ] [ -j tstamp_type ] [ -m module ] [ -M secret ] [ --number ] [ -Q|-P in|out|inout ] [ -r file ] [ -V file ] [ -s snaplen ] [ -T type ] [ -w file ] [ -W filecount ] [ -E spi@ipaddr algo:secret,... ] [ -y datalinktype ] [ -z postrotate-command ] [ -Z user ] [ --time-stamp-precision=tstamp_precision ] [ --immediate-mode ] [ --version ] [ expression ]
1、抓取所有经过指定网络接口的数据包,一般为eth0接口

[root@master ~]# tcpdump -i eth0 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 11:47:25.478332 IP master.ssh > 10.0.0.1.52069: Flags [P.], seq 834237551:834237763, ack 3924413123, win 273, length 212 11:47:25.479010 IP master.49925 > public1.alidns.com.domain: 32392+ PTR? 1.0.0.10.in-addr.arpa. (39) 11:47:25.490291 IP public1.alidns.com.domain > master.49925: 32392 NXDomain 0/1/0 (116) 11:47:25.491379 IP master.45829 > public1.alidns.com.domain: 55984+ PTR? 50.0.0.10.in-addr.arpa. (40) 11:47:25.498166 IP public1.alidns.com.domain > master.45829: 55984 NXDomain 0/1/0 (117) 11:47:25.498637 IP master.45586 > public1.alidns.com.domain: 56011+ PTR? 5.5.5.223.in-addr.arpa. (40) 11:47:25.498855 IP master.ssh > 10.0.0.1.52069: Flags [P.], seq 212:392, ack 1, win 273, length 180 11:47:25.499004 IP 10.0.0.1.52069 > master.ssh: Flags [.], ack 392, win 4103, length 0 11:47:25.506610 IP public1.alidns.com.domain > master.45586: 56011 1/0/0 PTR public1.alidns.com. (72) 11:47:25.506976 IP master.ssh > 10.0.0.1.52069: Flags [P.], seq 392:1228, ack 1, win 273, length 836 11:47:25.507114 IP master.ssh > 10.0.0.1.52069: Flags [P.], seq 1228:1392, ack 1, win 273, length 164 11:47:25.507200 IP 10.0.0.1.52069 > master.ssh: Flags [.], ack 1392, win 4106, length 0
2、抓取经过指定主机的网络接口的数据包

[root@master ~]# tcpdump -i eth0 -s 0 -c 10 src 10.0.0.50 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 11:42:47.686996 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 531080703:531080915, ack 2322487864, win 273, length 212 11:42:47.687722 IP master.60683 > public1.alidns.com.domain: 60966+ PTR? 1.0.0.10.in-addr.arpa. (39) 11:42:47.706465 IP master.56123 > public1.alidns.com.domain: 46823+ PTR? 50.0.0.10.in-addr.arpa. (40) 11:42:47.722262 IP master.41245 > public1.alidns.com.domain: 59392+ PTR? 5.5.5.223.in-addr.arpa. (40) 11:42:47.722490 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 212:392, ack 1, win 273, length 180 11:42:47.734392 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 392:860, ack 1, win 273, length 468 11:42:47.734743 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 860:1024, ack 1, win 273, length 164 11:42:47.735009 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 1024:1188, ack 1, win 273, length 164 11:42:47.735197 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 1188:1352, ack 1, win 273, length 164 11:42:47.735385 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 1352:1516, ack 1, win 273, length 164 10 packets captured 10 packets received by filter 0 packets dropped by kernel
抓取主机发送的所有数据包

[root@master ~]# tcpdump -i eth0 -s 0 -c 10 src 10.0.0.51 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 11:43:28.774327 IP 10.0.0.51.ssh > 10.0.0.1.51001: Flags [.], ack 3281257366, win 273, length 0 11:43:29.696320 IP 10.0.0.51.53616 > a.chl.la.ntp: NTPv4, Client, length 48 11:43:33.785147 ARP, Request who-has 10.0.0.1 tell 10.0.0.51, length 46 11:43:33.916293 ARP, Reply 10.0.0.51 is-at 00:0c:29:b6:82:ce (oui Unknown), length 46 11:43:34.706675 ARP, Request who-has gateway tell 10.0.0.51, length 46 11:43:44.092741 IP 10.0.0.51.40730 > 203.107.6.88.ntp: NTPv4, Client, length 48 11:43:46.002706 IP 10.0.0.51.38142 > tick.ntp.infomaniak.ch.ntp: NTPv4, Client, length 48 ^C 7 packets captured 7 packets received by filter 0 packets dropped by kernel

[root@master ~]# tcpdump -i eth0 -s 0 -c 10 dst 10.0.0.51 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 11:47:48.771957 IP 10.0.0.1.51001 > 10.0.0.51.ssh: Flags [P.], seq 3281257522:3281257574, ack 1917953, win 4101, length 52 11:47:53.785028 ARP, Reply 10.0.0.1 is-at 00:50:56:c0:00:08 (oui Unknown), length 46 11:47:53.915671 ARP, Request who-has 10.0.0.51 (00:0c:29:b6:82:ce (oui Unknown)) tell 10.0.0.1, length 46 11:47:53.955714 ARP, Reply gateway is-at 00:50:56:f8:14:ba (oui Unknown), length 46 11:48:06.853160 ARP, Request who-has 10.0.0.51 tell gateway, length 46 11:48:06.853684 IP tick.ntp.infomaniak.ch.ntp > 10.0.0.51.56503: NTPv4, Server, length 48 11:48:53.668330 IP a.chl.la.ntp > 10.0.0.51.48359: NTPv4, Server, length 48 11:48:53.772869 IP 10.0.0.1.51001 > 10.0.0.51.ssh: Flags [P.], seq 52:104, ack 1, win 4101, length 52 11:48:58.405601 ARP, Reply gateway is-at 00:50:56:f8:14:ba (oui Unknown), length 46 11:48:58.793533 ARP, Reply 10.0.0.1 is-at 00:50:56:c0:00:08 (oui Unknown), length 46 10 packets captured 10 packets received by filter 0 packets dropped by kernel
3、抓取主机间的通信

[root@master ~]# tcpdump -c 10 host 10.0.0.50 and host 10.0.0.51 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 11:54:40.604636 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 160, length 64 11:54:40.605318 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 160, length 64 11:54:41.607789 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 161, length 64 11:54:41.608270 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 161, length 64 11:54:41.616139 ARP, Request who-has 10.0.0.51 tell master, length 28 11:54:41.617208 ARP, Reply 10.0.0.51 is-at 00:0c:29:b6:82:ce (oui Unknown), length 46 11:54:42.609166 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 162, length 64 11:54:42.609900 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 162, length 64 11:54:43.610172 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 163, length 64 11:54:43.610706 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 163, length 64 10 packets captured 10 packets received by filter 0 packets dropped by kernel

[root@master ~]# tcpdump -c 10 src 10.0.0.50 and dst 10.0.0.51 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 11:52:46.994172 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 47, length 64 11:52:47.997304 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 48, length 64 11:52:48.999176 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 49, length 64 11:52:50.003331 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 50, length 64 11:52:51.004637 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 51, length 64 11:52:52.006195 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 52, length 64 11:52:53.006609 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 53, length 64 11:52:54.010974 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 54, length 64 11:52:55.023343 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 55, length 64 11:52:56.039875 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 56, length 64 10 packets captured 10 packets received by filter 0 packets dropped by kernel
4、抓取主机10.0.0.50和主机10.0.0.51或10.0.0.52之间的通信

[root@master ~]# tcpdump -c 100 host 10.0.0.50 and \(10.0.0.51 or 10.0.0.52\) tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 12:23:09.088682 ARP, Request who-has 10.0.0.51 tell master, length 28 12:23:09.088969 ARP, Reply 10.0.0.51 is-at 00:0c:29:b6:82:ce (oui Unknown), length 46 12:23:09.095121 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 1859, length 64 12:23:09.095601 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 1859, length 64 12:23:10.096708 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 1860, length 64 12:23:10.097016 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 1860, length 64 12:23:11.099065 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 1861, length 64 12:23:11.099694 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 1861, length 64 12:23:11.500997 IP master.34416 > node2.http: Flags [S], seq 2677329114, win 29200, options [mss 1460,sackOK,TS val 35888380 ecr 0,nop,wscale 7], length 0 12:23:11.501450 IP node2.http > master.34416: Flags [S.], seq 2236593106, ack 2677329115, win 28960, options [mss 1460,sackOK,TS val 1190089 ecr 35888380,nop,wscale 7], length 0 12:23:11.501539 IP master.34416 > node2.http: Flags [.], ack 1, win 229, options [nop,nop,TS val 35888381 ecr 1190089], length 0 12:23:11.501608 IP master.34416 > node2.http: Flags [P.], seq 1:74, ack 1, win 229, options [nop,nop,TS val 35888381 ecr 1190089], length 73: HTTP: GET / HTTP/1.1 12:23:11.501857 IP node2.http > master.34416: Flags [.], ack 74, win 227, options [nop,nop,TS val 1190089 ecr 35888381], length 0 12:23:11.502376 IP node2.http > master.34416: Flags [P.], seq 1:5074, ack 74, win 227, options [nop,nop,TS val 1190090 ecr 35888381], length 5073: HTTP: HTTP/1.1 200 OK 12:23:11.502458 IP master.34416 > node2.http: Flags [.], ack 5074, win 308, options [nop,nop,TS val 35888382 ecr 1190090], length 0 12:23:11.502890 IP master.34416 > node2.http: Flags [F.], seq 74, ack 5074, win 308, options [nop,nop,TS val 35888382 ecr 1190090], length 0 12:23:11.503628 IP node2.http > master.34416: Flags [F.], seq 5074, ack 75, win 227, options [nop,nop,TS val 1190091 ecr 35888382], length 0 12:23:11.503660 IP master.34416 > node2.http: Flags [.], ack 5075, win 308, options [nop,nop,TS val 35888383 ecr 1190091], length 0 12:23:12.101890 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 1862, length 64 12:23:12.102140 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 1862, length 64 12:23:13.103801 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 1863, length 64 12:23:13.104231 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 1863, length 64 12:23:14.106143 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 1864, length 64 12:23:14.106591 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 1864, length 64 ^C 24 packets captured 24 packets received by filter 0 packets dropped by kernel
5、抓取主机10.0.0.50和10.0.0.0/24网段但不包括主机10.0.0.52之间的通信

[root@master ~]# tcpdump -c 100 host 10.0.0.50 and \(net 10.0.0.0/24 and host ! 10.0.0.52\) tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 12:29:29.172010 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 531154747:531154959, ack 2322529948, win 273, length 212 12:29:29.172627 IP master.32788 > public1.alidns.com.domain: 59397+ PTR? 1.0.0.10.in-addr.arpa. (39) 12:29:29.211684 ARP, Request who-has master tell gateway, length 46 12:29:29.211702 ARP, Reply master is-at 00:0c:29:3e:e4:31 (oui Unknown), length 28 12:29:29.211764 IP public1.alidns.com.domain > master.32788: 59397 NXDomain 0/1/0 (116) 12:29:29.213063 IP master.54094 > public1.alidns.com.domain: 64114+ PTR? 50.0.0.10.in-addr.arpa. (40) 12:29:29.214915 IP 10.0.0.1.51000 > master.ssh: Flags [.], ack 212, win 4101, length 0 12:29:29.217179 IP master > 10.0.0.51: ICMP echo request, id 2683, seq 2237, length 64 12:29:29.217461 IP 10.0.0.51 > master: ICMP echo reply, id 2683, seq 2237, length 64 12:29:29.217561 IP master.ssh > 10.0.0.1.52069: Flags [P.], seq 834614971:834615087, ack 3924416171, win 273, length 116 12:29:29.227217 IP public1.alidns.com.domain > master.54094: 64114 NXDomain 0/1/0 (117) 12:29:29.227555 IP master.41599 > public1.alidns.com.domain: 17631+ PTR? 5.5.5.223.in-addr.arpa. (40) 12:29:29.227877 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 212:392, ack 1, win 273, length 180 12:29:29.235614 IP public1.alidns.com.domain > master.41599: 17631 1/0/0 PTR public1.alidns.com. (72) 12:29:29.235859 IP master.57573 > public1.alidns.com.domain: 25223+ PTR? 226.0.0.10.in-addr.arpa. (41) 12:29:29.236035 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 392:556, ack 1, win 273, length 164 12:29:29.236166 IP 10.0.0.1.51000 > master.ssh: Flags [.], ack 556, win 4106, length 0 12:29:29.261590 IP 10.0.0.1.52069 > master.ssh: Flags [.], ack 116, win 4103, length 0 12:29:29.431682 IP public1.alidns.com.domain > master.57573: 25223 NXDomain 0/1/0 (118) 12:29:29.432162 IP master.37523 > public1.alidns.com.domain: 44235+ PTR? 51.0.0.10.in-addr.arpa. (40) 12:29:29.432521 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 556:1040, ack 1, win 273, length 484 12:29:29.440847 IP public1.alidns.com.domain > master.37523: 44235 NXDomain 0/1/0 (117) 12:29:29.441392 IP master.ssh > 10.0.0.1.51000: Flags [P.], seq 1040:2548, ack 1, win 273, length 1508 12:29:29.441570 IP 10.0.0.1.51000 > master.ssh: Flags [.], ack 2500, win 4106, length 0
6、抓取主机10.0.0.50和除了10.0.0.51以外的所有主机的通信

[root@master ~]# tcpdump -c 10 host 10.0.0.50 and ! 10.0.0.51 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 13:35:30.238186 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 990440464:990440676, ack 2223416956, win 273, length 212 13:35:30.238888 IP master.55900 > public1.alidns.com.domain: 61787+ PTR? 1.0.0.10.in-addr.arpa. (39) 13:35:30.247759 IP public1.alidns.com.domain > master.55900: 61787 NXDomain 0/1/0 (116) 13:35:30.249258 IP master.39274 > public1.alidns.com.domain: 59606+ PTR? 50.0.0.10.in-addr.arpa. (40) 13:35:30.282539 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 212, win 4103, length 0 13:35:30.392824 IP public1.alidns.com.domain > master.39274: 59606 NXDomain 0/1/0 (117) 13:35:30.393418 IP master.59445 > public1.alidns.com.domain: 17170+ PTR? 5.5.5.223.in-addr.arpa. (40) 13:35:30.393639 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 212:392, ack 1, win 273, length 180 13:35:30.402371 IP public1.alidns.com.domain > master.59445: 17170 1/0/0 PTR public1.alidns.com. (72) 13:35:30.402881 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 392:1228, ack 1, win 273, length 836
7、抓取主机某端口接收的所有数据包

[root@master ~]# tcpdump -nnn -c 10 host 10.0.0.50 and tcp port 80 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 13:57:27.590965 IP 10.0.0.50.36606 > 10.0.0.52.80: Flags [S], seq 4170432404, win 29200, options [mss 1460,sackOK,TS val 41544470 ecr 0,nop,wscale 7], length 0 13:57:27.591476 IP 10.0.0.52.80 > 10.0.0.50.36606: Flags [S.], seq 1415011476, ack 4170432405, win 28960, options [mss 1460,sackOK,TS val 6503801 ecr 41544470,nop,wscale 7], length 0 13:57:27.591497 IP 10.0.0.50.36606 > 10.0.0.52.80: Flags [.], ack 1, win 229, options [nop,nop,TS val 41544471 ecr 6503801], length 0 13:57:27.591783 IP 10.0.0.50.36606 > 10.0.0.52.80: Flags [P.], seq 1:74, ack 1, win 229, options [nop,nop,TS val 41544471 ecr 6503801], length 73: HTTP: GET / HTTP/1.1 13:57:27.592083 IP 10.0.0.52.80 > 10.0.0.50.36606: Flags [.], ack 74, win 227, options [nop,nop,TS val 6503802 ecr 41544471], length 0 13:57:27.592249 IP 10.0.0.52.80 > 10.0.0.50.36606: Flags [P.], seq 1:5074, ack 74, win 227, options [nop,nop,TS val 6503802 ecr 41544471], length 5073: HTTP: HTTP/1.1 200 OK 13:57:27.592278 IP 10.0.0.50.36606 > 10.0.0.52.80: Flags [.], ack 5074, win 308, options [nop,nop,TS val 41544472 ecr 6503802], length 0 13:57:27.593217 IP 10.0.0.50.36606 > 10.0.0.52.80: Flags [F.], seq 74, ack 5074, win 308, options [nop,nop,TS val 41544473 ecr 6503802], length 0 13:57:27.594094 IP 10.0.0.52.80 > 10.0.0.50.36606: Flags [F.], seq 5074, ack 75, win 227, options [nop,nop,TS val 6503803 ecr 41544473], length 0 13:57:27.594112 IP 10.0.0.50.36606 > 10.0.0.52.80: Flags [.], ack 5075, win 308, options [nop,nop,TS val 41544474 ecr 6503803], length 0 10 packets captured 10 packets received by filter 0 packets dropped by kernel
8、抓取所有经过指定接口的指定端口的数据包

[root@master ~]# tcpdump -i eth0 -c 10 port 22 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 14:10:13.087881 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 991097360:991097572, ack 2223442120, win 273, length 212 14:10:13.088085 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 212, win 4103, length 0 14:10:13.113893 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 212:472, ack 1, win 273, length 260 14:10:13.114024 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 472:636, ack 1, win 273, length 164 14:10:13.114151 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 636, win 4101, length 0 14:10:13.114258 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 636:880, ack 1, win 273, length 244 14:10:13.114372 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 880:1044, ack 1, win 273, length 164 14:10:13.114430 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 1044, win 4106, length 0 14:10:13.114508 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1044:1288, ack 1, win 273, length 244 14:10:13.114611 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1288:1452, ack 1, win 273, length 164 10 packets captured 11 packets received by filter 0 packets dropped by kernel

[root@master ~]# tcpdump -i eth0 -c 10 src port 22 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 14:10:36.565180 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 991099948:991100160, ack 2223442992, win 273, length 212 14:10:36.614912 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 212:392, ack 1, win 273, length 180 14:10:36.615156 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 392:556, ack 1, win 273, length 164 14:10:36.615405 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 556:720, ack 1, win 273, length 164 14:10:36.615523 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 720:884, ack 1, win 273, length 164 14:10:36.615828 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 884:1048, ack 1, win 273, length 164 14:10:36.616005 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1048:1212, ack 1, win 273, length 164 14:10:36.616201 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1212:1376, ack 1, win 273, length 164 14:10:36.616315 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1376:1540, ack 1, win 273, length 164 14:10:36.616474 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1540:1704, ack 1, win 273, length 164 10 packets captured 10 packets received by filter 0 packets dropped by kernel

[root@master ~]# tcpdump -i eth0 -c 10 dst port 22 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 14:11:05.512918 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 991103988, win 4102, length 0 14:11:05.607646 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 149, win 4101, length 0 14:11:05.651225 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 297, win 4101, length 0 14:11:05.695707 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 445, win 4100, length 0 14:11:05.740200 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 593, win 4106, length 0 14:11:05.784651 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 741, win 4105, length 0 14:11:05.829269 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 889, win 4105, length 0 14:11:05.872816 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 1037, win 4104, length 0 14:11:05.917255 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 1185, win 4103, length 0 14:11:05.960635 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 1333, win 4103, length 0 10 packets captured 10 packets received by filter 0 packets dropped by kernel
9、抓取经过某一网段的数据包

[root@master ~]# tcpdump -i eth0 -c 10 net 10 and dst port 22 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 14:12:14.292262 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 991108984, win 4100, length 0 14:12:14.522789 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 149, win 4106, length 0 14:12:14.567287 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 297, win 4105, length 0 14:12:14.611427 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 445, win 4105, length 0 14:12:14.655852 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 593, win 4104, length 0 14:12:14.700586 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 741, win 4103, length 0 14:12:14.745224 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 889, win 4103, length 0 14:12:14.789886 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 1037, win 4102, length 0 14:12:14.833065 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 1185, win 4102, length 0 14:12:14.876945 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 1333, win 4101, length 0 10 packets captured 10 packets received by filter 0 packets dropped by kernel

[root@master ~]# tcpdump -i eth0 -c 10 net 10.0.0.0/24 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 14:23:15.137303 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 991117612:991117824, ack 2223453684, win 273, length 212 14:23:15.137507 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 212, win 4101, length 0 14:23:15.137982 IP master.45356 > public1.alidns.com.domain: 52305+ PTR? 1.0.0.10.in-addr.arpa. (39) 14:23:15.159690 IP public1.alidns.com.domain > master.45356: 52305 NXDomain 0/1/0 (116) 14:23:15.160883 IP master.40536 > public1.alidns.com.domain: 65448+ PTR? 50.0.0.10.in-addr.arpa. (40) 14:23:15.169457 IP public1.alidns.com.domain > master.40536: 65448 NXDomain 0/1/0 (117) 14:23:15.169874 IP master.45300 > public1.alidns.com.domain: 23363+ PTR? 5.5.5.223.in-addr.arpa. (40) 14:23:15.170039 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 212:472, ack 1, win 273, length 260 14:23:15.178722 IP public1.alidns.com.domain > master.45300: 23363 1/0/0 PTR public1.alidns.com. (72) 14:23:15.179023 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 472:1212, ack 1, win 273, length 740 10 packets captured 10 packets received by filter 0 packets dropped by kernel
10、抓取eth0网卡,目的地址是10.0.0.51 或10.0.0.52,且端口是80的tcp协议数据包

[root@master ~]# tcpdump -nnn -c 10 -i eth0 tcp port 80 and \( dst host 10.0.0.51 or dst host 10.0.0.52\) tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 14:39:07.775716 IP 10.0.0.50.38210 > 10.0.0.52.80: Flags [S], seq 676509379, win 29200, options [mss 1460,sackOK,TS val 44044655 ecr 0,nop,wscale 7], length 0 14:39:07.776114 IP 10.0.0.50.38210 > 10.0.0.52.80: Flags [.], ack 2662973090, win 229, options [nop,nop,TS val 44044656 ecr 9003990], length 0 14:39:07.776250 IP 10.0.0.50.38210 > 10.0.0.52.80: Flags [P.], seq 0:73, ack 1, win 229, options [nop,nop,TS val 44044656 ecr 9003990], length 73: HTTP: GET / HTTP/1.1 14:39:07.776737 IP 10.0.0.50.38210 > 10.0.0.52.80: Flags [.], ack 4345, win 296, options [nop,nop,TS val 44044656 ecr 9003990], length 0 14:39:07.776773 IP 10.0.0.50.38210 > 10.0.0.52.80: Flags [.], ack 5074, win 319, options [nop,nop,TS val 44044656 ecr 9003991], length 0 14:39:07.777182 IP 10.0.0.50.57620 > 10.0.0.51.80: Flags [S], seq 3591770109, win 29200, options [mss 1460,sackOK,TS val 44044657 ecr 0,nop,wscale 7], length 0 14:39:07.778437 IP 10.0.0.50.57620 > 10.0.0.51.80: Flags [.], ack 2602778227, win 229, options [nop,nop,TS val 44044657 ecr 23781049], length 0 14:39:07.779476 IP 10.0.0.50.57620 > 10.0.0.51.80: Flags [P.], seq 0:73, ack 1, win 229, options [nop,nop,TS val 44044659 ecr 23781049], length 73: HTTP: GET / HTTP/1.1 14:39:07.781218 IP 10.0.0.50.57620 > 10.0.0.51.80: Flags [.], ack 5074, win 308, options [nop,nop,TS val 44044661 ecr 23781052], length 0 14:39:07.781617 IP 10.0.0.50.38210 > 10.0.0.52.80: Flags [F.], seq 73, ack 5074, win 319, options [nop,nop,TS val 44044661 ecr 9003991], length 0 10 packets captured 13 packets received by filter 0 packets dropped by kernel
11、抓取目的MAC的icmp数据包

[root@master ~]# tcpdump -nnn -c 10 -i eth0 tcp port 80 and \( ether dst host 00:0c:29:4b:4d:ee\) tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 14:44:55.858754 IP 10.0.0.50.38670 > 10.0.0.52.80: Flags [S], seq 2676273323, win 29200, options [mss 1460,sackOK,TS val 44392738 ecr 0,nop,wscale 7], length 0 14:44:55.859226 IP 10.0.0.50.38670 > 10.0.0.52.80: Flags [.], ack 196001962, win 229, options [nop,nop,TS val 44392739 ecr 9352073], length 0 14:44:55.859829 IP 10.0.0.50.38670 > 10.0.0.52.80: Flags [P.], seq 0:73, ack 1, win 229, options [nop,nop,TS val 44392739 ecr 9352073], length 73: HTTP: GET / HTTP/1.1 14:44:55.860715 IP 10.0.0.50.38670 > 10.0.0.52.80: Flags [.], ack 5074, win 308, options [nop,nop,TS val 44392740 ecr 9352075], length 0 14:44:55.867186 IP 10.0.0.50.38670 > 10.0.0.52.80: Flags [F.], seq 73, ack 5074, win 308, options [nop,nop,TS val 44392747 ecr 9352075], length 0 14:44:55.867938 IP 10.0.0.50.38670 > 10.0.0.52.80: Flags [.], ack 5075, win 308, options [nop,nop,TS val 44392748 ecr 9352082], length 0 14:44:58.880298 IP 10.0.0.50.38674 > 10.0.0.52.80: Flags [S], seq 2891714571, win 29200, options [mss 1460,sackOK,TS val 44395760 ecr 0,nop,wscale 7], length 0 14:44:58.880833 IP 10.0.0.50.38674 > 10.0.0.52.80: Flags [.], ack 2172568837, win 229, options [nop,nop,TS val 44395760 ecr 9355095], length 0 14:44:58.880963 IP 10.0.0.50.38674 > 10.0.0.52.80: Flags [P.], seq 0:73, ack 1, win 229, options [nop,nop,TS val 44395761 ecr 9355095], length 73: HTTP: GET / HTTP/1.1 14:44:58.881593 IP 10.0.0.50.38674 > 10.0.0.52.80: Flags [.], ack 5074, win 308, options [nop,nop,TS val 44395761 ecr 9355096], length 0 10 packets captured 10 packets received by filter 0 packets dropped by kernel
12、抓取eth0网卡,目标网络是10.0.0.0/24不包括10.0.0.52主机的tcp80端口的数据包

[root@master ~]# tcpdump -nnn -c 10 -i eth0 tcp port 80 and \(src net 10 and ! dst host 10.0.0.52\) tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 14:53:36.033538 IP 10.0.0.52.80 > 10.0.0.50.39358: Flags [S.], seq 2841379096, ack 3540005207, win 28960, options [mss 1460,sackOK,TS val 9872248 ecr 44912912,nop,wscale 7], length 0 14:53:36.033967 IP 10.0.0.52.80 > 10.0.0.50.39358: Flags [.], ack 74, win 227, options [nop,nop,TS val 9872249 ecr 44912913], length 0 14:53:36.034164 IP 10.0.0.52.80 > 10.0.0.50.39358: Flags [.], seq 1:4345, ack 74, win 227, options [nop,nop,TS val 9872249 ecr 44912913], length 4344: HTTP: HTTP/1.1 200 OK 14:53:36.034390 IP 10.0.0.52.80 > 10.0.0.50.39358: Flags [P.], seq 4345:5074, ack 74, win 227, options [nop,nop,TS val 9872249 ecr 44912913], length 729: HTTP 14:53:36.035044 IP 10.0.0.50.58768 > 10.0.0.51.80: Flags [S], seq 3257648545, win 29200, options [mss 1460,sackOK,TS val 44912914 ecr 0,nop,wscale 7], length 0 14:53:36.035547 IP 10.0.0.51.80 > 10.0.0.50.58768: Flags [S.], seq 3962588812, ack 3257648546, win 28960, options [mss 1460,sackOK,TS val 24649306 ecr 44912914,nop,wscale 7], length 0 14:53:36.035601 IP 10.0.0.50.58768 > 10.0.0.51.80: Flags [.], ack 1, win 229, options [nop,nop,TS val 44912915 ecr 24649306], length 0 14:53:36.035725 IP 10.0.0.50.58768 > 10.0.0.51.80: Flags [P.], seq 1:74, ack 1, win 229, options [nop,nop,TS val 44912915 ecr 24649306], length 73: HTTP: GET / HTTP/1.1 14:53:36.036152 IP 10.0.0.51.80 > 10.0.0.50.58768: Flags [.], ack 74, win 227, options [nop,nop,TS val 24649307 ecr 44912915], length 0 14:53:36.037193 IP 10.0.0.51.80 > 10.0.0.50.58768: Flags [P.], seq 1:5074, ack 74, win 227, options [nop,nop,TS val 24649307 ecr 44912915], length 5073: HTTP: HTTP/1.1 200 OK 10 packets captured 11 packets received by filter 0 packets dropped by kernel
抓取标志位的数据包
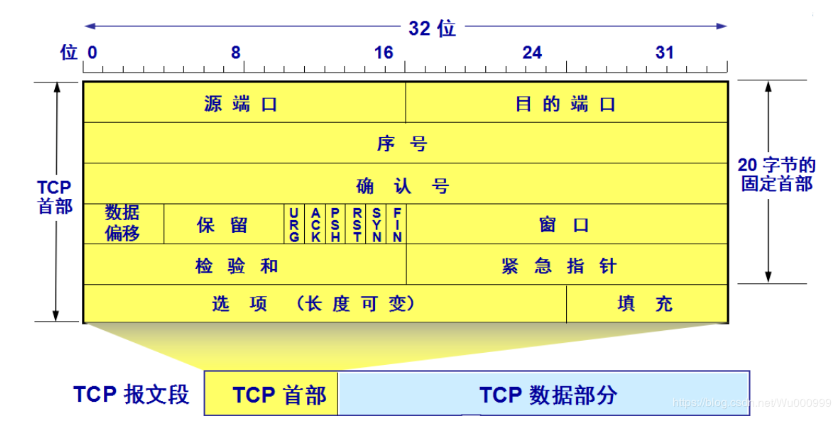
源端口和目的端口 各占2个字节,分别写入源端口和目的端口。 序号 占4字节。序号范围是【0,2^32 - 1】,共2^32 (即4294967296)个序号。序号增加到2^32-1后,下一个序号就又回到0。也就是说,序号使用mod 2^32运算。TCP是面向字节流的。在一个TCP连接中传送的字节流中的每一个字节都按顺序编号。整个要传送的字节流的起始序号必须在连接建立时设置。首部中的序号字段值则是指的是本报文段所发送的数据的第一个字节的序号。例如,一报文段的序号是301,而接待的数据共有100字节。这就表明:本报文段的数据的第一个字节的序号是301,最后一个字节的序号是400。显然,下一个报文段(如果还有的话)的数据序号应当从401开始,即下一个报文段的序号字段值应为401。这个字段的序号也叫“报文段序号”。 确认号 占4字节,是期望收到对方下一个报文段的第一个数据字节的序号。例如,B正确收到了A发送过来的一个报文段,其序号字段值是501,而数据长度是200字节(序号501~700),这表明B正确收到了A发送的到序号700为止的数据。因此,B期望收到A的下一个数据序号是701,于是B在发送给A的确认报文段中把确认号置为701。注意,现在确认号不是501,也不是700,而是701。 总之:若确认号为= N,则表明:到序号N-1为止的所有数据都已正确收到。 数据偏移 占4位,它指出TCP报文段的数据起始处距离TCP报文段的起始处有多远。这个字段实际上是指出TCP报文段的首部长度。由于首部中还有长度不确定的选项字段,因此数据偏移字段是必要的,但应注意,“数据偏移”的单位是32位字(即以4字节的字为计算单位)。由于4位二进制数能表示的最大十进制数字是15,因此数据偏移的最大值是60字节,这也是TCP首部的最大字节(即选项长度不能超过40字节)。 保留 占6位,保留为今后使用,但目前应置为0 。
下面有6个控制位,用来说明本报文段的性质。 1、紧急URG(URGent) 当URG=1时,表明紧急指针字段有效。它告诉系统此报文段中有紧急数据,应尽快发送(相当于高优先级的数据),而不要按原来的排队顺序来传送。
例如,已经发送了很长的一个程序要在远地的主机上运行。但后来发现了一些问题,需要取消该程序的运行,因此用户从键盘发出中断命令。如果不使用紧急数据,那么这两个字符将存储在接收TCP的缓存末尾。只有在所有的数据被处理完毕后这两个字符才被交付接收方的应用进程。这样做就浪费了很多时间。 当URG置为1时,发送应用进程就告诉发送方的TCP有紧急数据要传送。于是发送方TCP就把紧急数据插入到本报文段数据的最前面,而在紧急数据后面的数据仍然是普通数据。这时要与首部中紧急指针(Urgent Pointer)字段配合使用。 2、确认ACK(ACKnowledgment) 仅当ACK = 1时确认号字段才有效,当ACK = 0时确认号无效。TCP规定,在连接建立后所有的传送的报文段都必须把ACK置为1。 3、推送 PSH(PuSH) 当两个应用进程进行交互式的通信时,有时在一端的应用进程希望在键入一个命令后立即就能收到对方的响应。在这种情况下,TCP就可以使用推送(push)操作。这时,发送方TCP把PSH置为1,并立即创建一个报文段发送出去。接收方TCP收到PSH=1的报文段,就尽快地(即“推送”向前)交付接收应用进程。而不用再等到整个缓存都填满了后再向上交付。 4、复位RST(ReSeT) 当RST=1时,表名TCP连接中出现了严重错误(如由于主机崩溃或其他原因),必须释放连接,然后再重新建立传输连接。RST置为1还用来拒绝一个非法的报文段或拒绝打开一个连接。 5、同步SYN(SYNchronization) 在连接建立时用来同步序号。当SYN=1而ACK=0时,表明这是一个连接请求报文段。对方若同意建立连接,则应在响应的报文段中使SYN=1和ACK=1,因此SYN置为1就表示这是一个连接请求或连接接受报文。 6、终止FIN(FINis,意思是“完”“终”) 用来释放一个连接。当FIN=1时,表明此报文段的发送发的数据已发送完毕,并要求释放运输连接。 窗口 占2字节。窗口值是【0,2^16-1】之间的整数。窗口指的是发送本报文段的一方的接受窗口(而不是自己的发送窗口)。窗口值告诉对方:从本报文段首部中的确认号算起,接收方目前允许对方发送的数据量(以字节为单位)。之所以要有这个限制,是因为接收方的数据缓存空间是有限的。总之,窗口值作为接收方让发送方设置其发送窗口的依据。 例如,发送了一个报文段,其确认号是701,窗口字段是1000.这就是告诉对方:“从701算起,我(即发送方报文段的一方)的接收缓存空间还可接受1000个字节数据(字节序号是701~1700),你在给我发数据时,必须考虑到这一点。” 总之:窗口字段明确指出了现在允许对方发送的数据量。窗口值经常在动态变化。 检验和 占2字节。检验和字段检验的范围包括首部和数据这两部分。和UDP用户数据报一样,在计算检验和时,要在TCP报文段的前面加上12字节的伪首部。伪首部的格式和UDP用户数据报的伪首部一样。但应把伪首部第4个字段中的17改为6(TCP的协议号是6);把第5字段中的UDP中的长度改为TCP长度。接收方收到此报文段后,仍要加上这个伪首部来计算检验和。若使用TPv6,则相应的伪首部也要改变。 紧急指针 占2字节。紧急指针仅在URG=1时才有意义,它指出本报文段中的紧急数据的字节数(紧急数据结束后就是普通数据) 。因此,在紧急指针指出了紧急数据的末尾在报文段中的位置。当所有紧急数据都处理完时,TCP就告诉应用程序恢复到正常操作。值得注意的是,即使窗口为0时也可以发送紧急数据。 原文链接:https://blog.csdn.net/Wu000999/article/details/88623240
tcp[13]表示在tcp header中的偏移位置13开始、后边代表的是匹配的字节数
1、抓取SYN包

[root@master ~]# tcpdump -i eth0 'tcp[tcpflags]= tcp-syn' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 15:17:08.528633 IP master.41226 > node2.http: Flags [S], seq 1102588012, win 29200, options [mss 1460,sackOK,TS val 46325408 ecr 0,nop,wscale 7], length 0 15:17:08.530215 IP master.60636 > 10.0.0.51.http: Flags [S], seq 2904442455, win 29200, options [mss 1460,sackOK,TS val 46325410 ecr 0,nop,wscale 7], length 0 15:17:11.549923 IP master.41230 > node2.http: Flags [S], seq 2323420220, win 29200, options [mss 1460,sackOK,TS val 46328429 ecr 0,nop,wscale 7], length 0 15:17:11.553129 IP master.60640 > 10.0.0.51.http: Flags [S], seq 148256788, win 29200, options [mss 1460,sackOK,TS val 46328432 ecr 0,nop,wscale 7], length 0 15:17:14.578311 IP master.41234 > node2.http: Flags [S], seq 1972292849, win 29200, options [mss 1460,sackOK,TS val 46331458 ecr 0,nop,wscale 7], length 0 15:17:14.579514 IP master.60644 > 10.0.0.51.http: Flags [S], seq 3826340367, win 29200, options [mss 1460,sackOK,TS val 46331459 ecr 0,nop,wscale 7], length 0 ^C 6 packets captured 6 packets received by filter 0 packets dropped by kernel
S=SYN,同步序列编号,Synchronize Sequence Numbers;发起连接标志。
P=PUSH,传送数据标志。
F=FIN,关闭连接标志。
ack,表示确认包,确认编号,Acknowledgement Number。
RST=RESET,异常关闭连接。
.,表示没有任何标志。
2、 显示所有的urgent包(URG)
[root@master ~]# tcpdump -i eth0 'tcp[13] & 32!=0' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
3、显示所有的ACK包

[root@master ~]# tcpdump -c 10'tcp[13] & 16!=0' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 17:48:43.284873 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 994170940:994171152, ack 2223559164, win 316, length 212 17:48:43.285467 IP master.56470 > public1.alidns.com.domain: 49663+ PTR? 1.0.0.10.in-addr.arpa. (39) 17:48:43.298828 IP public1.alidns.com.domain > master.56470: 49663 NXDomain 0/1/0 (116) 17:48:43.299910 IP master.45325 > public1.alidns.com.domain: 51471+ PTR? 50.0.0.10.in-addr.arpa. (40) 17:48:43.328918 IP 10.0.0.1.52958 > master.ssh: Flags [.], ack 212, win 4103, length 0 17:48:43.399599 IP public1.alidns.com.domain > master.45325: 51471 NXDomain 0/1/0 (117) 17:48:43.399946 IP master.51305 > public1.alidns.com.domain: 46047+ PTR? 5.5.5.223.in-addr.arpa. (40) 17:48:43.400094 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 212:392, ack 1, win 316, length 180 17:48:43.410752 IP public1.alidns.com.domain > master.51305: 46047 1/0/0 PTR public1.alidns.com. (72) 17:48:43.410990 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 392:1228, ack 1, win 316, length 836 10 packets captured 11 packets received by filter 0 packets dropped by kernel
4、显示所有的push包
[root@master ~]# tcpdump -c 10 'tcp[13] & 8!=0' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 18:03:19.930562 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 994680268:994680480, ack 2223563920, win 316, length 212 18:03:20.001417 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 212:392, ack 1, win 316, length 180 18:03:20.001675 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 392:556, ack 1, win 316, length 164 18:03:20.001983 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 556:720, ack 1, win 316, length 164 18:03:20.002207 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 720:884, ack 1, win 316, length 164 18:03:20.002426 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 884:1048, ack 1, win 316, length 164 18:03:20.002653 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1048:1212, ack 1, win 316, length 164 18:03:20.002876 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1212:1376, ack 1, win 316, length 164 18:03:20.003181 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1376:1540, ack 1, win 316, length 164 18:03:20.003403 IP master.ssh > 10.0.0.1.52958: Flags [P.], seq 1540:1704, ack 1, win 316, length 164 10 packets captured 10 packets received by filter 0 packets dropped by kernel
5、显示所有的reset包
[root@master ~]# tcpdump -c 10 'tcp[13] & 4!=0'
6、显示所有的SYN包
[root@master ~]# tcpdump -c 10 'tcp[13] & 2!=0' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 18:05:43.913229 IP master.54602 > node2.http: Flags [S], seq 3335372511, win 29200, options [mss 1460,sackOK,TS val 56440793 ecr 0,nop,wscale 7], length 0 18:05:43.913655 IP node2.http > master.54602: Flags [S.], seq 3867520064, ack 3335372512, win 28960, options [mss 1460,sackOK,TS val 21400131 ecr 56440793,nop,wscale 7], length 0 18:05:43.914574 IP master.45780 > 10.0.0.51.http: Flags [S], seq 485029363, win 29200, options [mss 1460,sackOK,TS val 56440794 ecr 0,nop,wscale 7], length 0 18:05:43.915083 IP 10.0.0.51.http > master.45780: Flags [S.], seq 2518292057, ack 485029364, win 28960, options [mss 1460,sackOK,TS val 36177183 ecr 56440794,nop,wscale 7], length 0 18:05:46.922901 IP master.54606 > node2.http: Flags [S], seq 1682608267, win 29200, options [mss 1460,sackOK,TS val 56443802 ecr 0,nop,wscale 7], length 0 18:05:46.923426 IP node2.http > master.54606: Flags [S.], seq 4178843742, ack 1682608268, win 28960, options [mss 1460,sackOK,TS val 21403140 ecr 56443802,nop,wscale 7], length 0 18:05:46.924795 IP master.45784 > 10.0.0.51.http: Flags [S], seq 4043869085, win 29200, options [mss 1460,sackOK,TS val 56443804 ecr 0,nop,wscale 7], length 0 18:05:46.925798 IP 10.0.0.51.http > master.45784: Flags [S.], seq 405101428, ack 4043869086, win 28960, options [mss 1460,sackOK,TS val 36180194 ecr 56443804,nop,wscale 7], length 0 18:05:49.947576 IP master.54610 > node2.http: Flags [S], seq 782044865, win 29200, options [mss 1460,sackOK,TS val 56446826 ecr 0,nop,wscale 7], length 0 18:05:49.948091 IP node2.http > master.54610: Flags [S.], seq 3237395045, ack 782044866, win 28960, options [mss 1460,sackOK,TS val 21406165 ecr 56446826,nop,wscale 7], length 0 10 packets captured 10 packets received by filter 0 packets dropped by kernel
7、显示所有的FIN包
[root@master ~]# tcpdump -c 10 'tcp[13] & 1!=0' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 18:08:51.364607 IP master.54850 > node2.http: Flags [F.], seq 1062204211, ack 25776701, win 308, options [nop,nop,TS val 56628244 ecr 21587580], length 0 18:08:51.364694 IP master.46028 > 10.0.0.51.http: Flags [F.], seq 1028689265, ack 1393925015, win 319, options [nop,nop,TS val 56628244 ecr 36364633], length 0 18:08:51.364957 IP node2.http > master.54850: Flags [F.], seq 1, ack 1, win 227, options [nop,nop,TS val 21587582 ecr 56628244], length 0 18:08:51.365254 IP 10.0.0.51.http > master.46028: Flags [F.], seq 1, ack 1, win 227, options [nop,nop,TS val 36364633 ecr 56628244], length 0 18:08:54.377822 IP master.54854 > node2.http: Flags [F.], seq 4166887554, ack 185332322, win 308, options [nop,nop,TS val 56631257 ecr 21590593], length 0 18:08:54.377969 IP master.46032 > 10.0.0.51.http: Flags [F.], seq 1963511496, ack 1255743096, win 319, options [nop,nop,TS val 56631258 ecr 36367646], length 0 18:08:54.378210 IP 10.0.0.51.http > master.46032: Flags [F.], seq 1, ack 1, win 227, options [nop,nop,TS val 36367646 ecr 56631258], length 0 18:08:54.378398 IP node2.http > master.54854: Flags [F.], seq 1, ack 1, win 227, options [nop,nop,TS val 21590595 ecr 56631257], length 0 18:08:57.432880 IP master.54858 > node2.http: Flags [F.], seq 1417032744, ack 1614070477, win 308, options [nop,nop,TS val 56634312 ecr 21593648], length 0 18:08:57.432986 IP master.46036 > 10.0.0.51.http: Flags [F.], seq 4097800127, ack 1961935276, win 308, options [nop,nop,TS val 56634313 ecr 36370701], length 0 10 packets captured 12 packets received by filter 0 packets dropped by kernel
8、显示所有的SYN/ACK包
[root@master ~]# tcpdump -c 10 'tcp[13]=18' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 19:15:38.730532 IP node2.http > master.60150: Flags [S.], seq 4214469296, ack 3583043559, win 28960, options [mss 1460,sackOK,TS val 25594947 ecr 60635610,nop,wscale 7], length 0 19:15:38.732512 IP 10.0.0.51.http > master.51328: Flags [S.], seq 69388121, ack 205501406, win 28960, options [mss 1460,sackOK,TS val 40372000 ecr 60635611,nop,wscale 7], length 0 19:15:41.755976 IP node2.http > master.60154: Flags [S.], seq 3471748168, ack 3054437199, win 28960, options [mss 1460,sackOK,TS val 25597972 ecr 60638635,nop,wscale 7], length 0 19:15:41.758065 IP 10.0.0.51.http > master.51332: Flags [S.], seq 1603343752, ack 3063722419, win 28960, options [mss 1460,sackOK,TS val 40375026 ecr 60638637,nop,wscale 7], length 0 19:15:44.784591 IP node2.http > master.60158: Flags [S.], seq 2427562648, ack 3710394382, win 28960, options [mss 1460,sackOK,TS val 25601001 ecr 60641664,nop,wscale 7], length 0 19:15:44.786144 IP 10.0.0.51.http > master.51336: Flags [S.], seq 1732574879, ack 1316852757, win 28960, options [mss 1460,sackOK,TS val 40378054 ecr 60641665,nop,wscale 7], length 0 19:15:47.808128 IP node2.http > master.60162: Flags [S.], seq 299635172, ack 3686152643, win 28960, options [mss 1460,sackOK,TS val 25604024 ecr 60644687,nop,wscale 7], length 0 19:15:47.809659 IP 10.0.0.51.http > master.51340: Flags [S.], seq 1275161858, ack 2936581416, win 28960, options [mss 1460,sackOK,TS val 40381078 ecr 60644689,nop,wscale 7], length 0 19:15:50.837391 IP node2.http > master.60166: Flags [S.], seq 1645429087, ack 1972895848, win 28960, options [mss 1460,sackOK,TS val 25607054 ecr 60647716,nop,wscale 7], length 0 19:15:50.838931 IP 10.0.0.51.http > master.51344: Flags [S.], seq 3856983258, ack 2914854144, win 28960, options [mss 1460,sackOK,TS val 40384107 ecr 60647718,nop,wscale 7], length 0 10 packets captured 10 packets received by filter 0 packets dropped by kernel
重要流量
1、过滤同时设置SYN和RST标识的包(这在正常情况下不应该发生)
[root@master ~]# tcpdump 'tcp[13] = 6'
2、过滤明文的HTTP GET请求
[root@master ~]# tcpdump 'tcp[32:4] = 0x47455420' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 19:20:38.151959 IP master.60546 > node2.http: Flags [P.], seq 3103068676:3103068749, ack 1335971831, win 229, options [nop,nop,TS val 60935032 ecr 25894368], length 73: HTTP: GET / HTTP/1.1 19:20:38.154113 IP master.51724 > 10.0.0.51.http: Flags [P.], seq 1680010040:1680010113, ack 2788905686, win 229, options [nop,nop,TS val 60935033 ecr 40671422], length 73: HTTP: GET / HTTP/1.1 19:20:41.164179 IP master.60550 > node2.http: Flags [P.], seq 2493108808:2493108881, ack 1208706287, win 229, options [nop,nop,TS val 60938044 ecr 25897380], length 73: HTTP: GET / HTTP/1.1 19:20:41.166441 IP master.51728 > 10.0.0.51.http: Flags [P.], seq 353162956:353163029, ack 4163428579, win 229, options [nop,nop,TS val 60938046 ecr 40674434], length 73: HTTP: GET / HTTP/1.1 19:20:44.184097 IP master.60554 > node2.http: Flags [P.], seq 207317367:207317440, ack 4039194775, win 229, options [nop,nop,TS val 60941064 ecr 25900400], length 73: HTTP: GET / HTTP/1.1 19:20:44.185717 IP master.51732 > 10.0.0.51.http: Flags [P.], seq 178997322:178997395, ack 105508896, win 229, options [nop,nop,TS val 60941065 ecr 40677453], length 73: HTTP: GET / HTTP/1.1
3、通过横幅文本过滤任意端口的SSH连接
[root@master ~]# tcpdump 'tcp[(tcp[12]>>2):4] = 0x5353482D' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 19:22:12.357225 IP node2.43492 > master.ssh: Flags [P.], seq 2781165453:2781165474, ack 3943380735, win 229, options [nop,nop,TS val 25988573 ecr 61029236], length 21 19:22:12.373475 IP master.ssh > node2.43492: Flags [P.], seq 1:22, ack 21, win 227, options [nop,nop,TS val 61029253 ecr 25988573], length 21
4、过滤TTL小于10的包(通常情况下是存在问题或者在使用traceroute)
[root@master ~]# tcpdump 'ip[8] < 10' tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 19:24:12.228726 IP 10.0.0.1.56059 > 239.255.255.250.ssdp: UDP, length 174 19:24:13.313277 IP 10.0.0.1.56059 > 239.255.255.250.ssdp: UDP, length 174 19:24:14.397109 IP 10.0.0.1.56059 > 239.255.255.250.ssdp: UDP, length 174 19:24:15.481278 IP 10.0.0.1.56059 > 239.255.255.250.ssdp: UDP, length 174 4 packets captured 4 packets received by filter
5、过滤恶意的包
[root@master ~]# tcpdump 'ip[6] & 128 != 0'
报文内容解释
19:22:12.357225 IP node2.43492 > master.ssh: Flags [P.], seq 2781165453:2781165474, ack 3943380735, win 229, options [nop,nop,TS val 25988573 ecr 61029236], length 21
19:22:12.357225 本地时间戳
IP 协议
node2.43492 源地址和端口
> 数据流向
master.ssh 目标地址和端口
win 229 表示接收缓冲区中可用的字节数,后跟 TCP 选项如 MSS(最大段大小)或者窗口比例值
seq 2781165453:2781165474
Flags [P.] 标志位
ack 3943380735 确认
length 21 代表数据包有效载荷字节长度
posted on 2020-03-22 21:11 hopeless-dream 阅读(614) 评论(0) 编辑 收藏 举报




