Nginx+Lua实现WAF应⽤防⽕墙
Nginx+Lua实现WAF应⽤防⽕墙
- 1.常⻅的恶意⾏为
- 爬⾍⾏为和恶意抓取,资源盗取
- 防护⼿段
- 1.基础防盗链功能不让恶意⽤户能够轻易的爬取⽹站对外数据
- 2.access_moudle->对后台,部分⽤户服务的数据提供IP防护
解决⽅法
192.168.1.170
[root@180-143 conf.d]# cat /soft/openresty/nginx/conf/conf.d/luawaf.conf
server {
listen 80;
server_name luawaf.yuansredevsecops.top;
set $ip 0;
if ($http_x_forward_for = "192.168.1.129"){
set $ip 1;
}
if ($remote_addr = "192.168.1.129"){
set $ip 1;
}
if ($ip = 0){
return 403;
}
location /hello {
default_type application/json;
return 200 '{"status":"success"}';
}
}
- 2.常⻅的攻击⼿段
- 后台密码撞库,通过猜测密码字典不断对后台系统登陆性尝试,获取后台登陆密码
- 防护⼿段
- 1.后台登陆密码复杂度
- 2.使⽤access_module-对后台提供IP防控
- 3.预警机制
- ⽂件上传漏洞,利⽤上传接⼝将恶意代码植⼊到服务器中,再通过url去访问执⾏代码
- 执⾏⽅式 luawaf.yuansredevsecops.top/1.jpg/1.php
解决办法
location ^~ /upload {
root /soft/code/upload;
if ($request_filename ~* (.*)\.php){
return 403;
}
}
- 3.常⻅的攻击⼿段
- 利⽤未过滤/未审核的⽤户输⼊进⾏Sql注⼊的攻击⽅法, 让应⽤运⾏本不应该运⾏的SQL代码
- 防护⼿段
- 1.php配置开启安全相关限制
- 2.开发⼈员对sql提交进⾏审核,屏蔽常⻅的注⼊⼿段
- 3.Nginx+Lua构建WAF应⽤层防⽕墙, 防⽌Sql注⼊

1.快速安装 lnmp 架构
[root@nginx ~]# yum install mariadb mariadb-server php php-fpm php-mysql -y
2.配置 Nginx + php
[root@nginx conf.d]# cat lnmp.conf
server {
server_name lnmp.yuansredevsecops.top;
root /soft/code/lnmp/;
index index.html index.php;
location ~ \.php$ {
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
}
}
3.配置 MySQL
[root@nginx ~]# systemctl start mariadb
[root@nginx ~]# mysql -uroot -p'123456'
MariaDB [(none)]> create database info;
MariaDB [(none)]> use info;
MariaDB [info]> create table user(id int(11),username varchar(64), password varchar(64), email varchar(64));
MariaDB [info]> desc user;
+----------+-------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+----------+-------------+------+-----+---------+-------+
| id | int(11) | YES | | NULL | |
| username | varchar(64) | YES | | NULL | |
| password | varchar(64) | YES | | NULL | |
| email | varchar(64) | YES | | NULL | |
+----------+-------------+------+-----+---------+-------+
#插⼊数据
MariaDB [info]> insert into user (id,username,password,email) values(1,'yuan',('123'),'yuan@qq.com');
MariaDB [info]> select * from info.user;
+------+----------+----------------------------------+-----------------+
| id | username | password | email |
+------+----------+----------------------------------+-----------------+
| 1 | yuan | 123 | yuan@foxmail.com |
+------+----------+----------------------------------+-----------------+
1 row in set (0.00 sec)
4.配置php代码
[root@nginx conf.d]# cat /soft/code/lnmp/login.html
<html>
<head>
<title> Sql注⼊演示场景 </title>
<meta http-equiv="content-type"content="text/html;charset=utf-8">
</head>
<body>
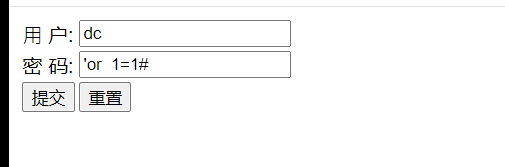
<form action="sql.php" method="post">
<table>
<tr>
<td> ⽤ 户: </td>
<td><input type="text" name="username"></td>
</tr>
<tr>
<td> 密 码: </td>
<td><input type="text" name="password"></td>
</tr>
<tr>
<td><input type="submit" value="提交"></td>
<td><input type="reset" value="重置"></td>
</tr>
</table>
</form>
</body>
</html>
被html调⽤的sql.php⽂件
[root@nginx conf.d]# cat /soft/code/lnmp/sql.php
<?php
$conn = mysqli_connect("localhost", 'root', '123456', "info") or die("数据库连接失败! ");
$name = $_POST['username'];
$pwd = $_POST['password'];
// # sql注⼊核⼼问题
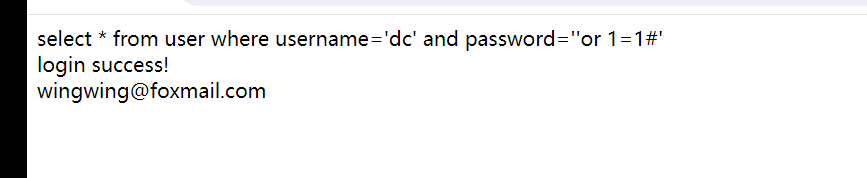
$sql = "select * from user where username='$name' and password='$pwd'";
echo $sql . "<br />";
$query = mysqli_query($conn, $sql);
$arr = mysqli_fetch_array($query);
if ($arr) {
echo "login success!<br />";
echo $arr[1];
echo $arr[3] . "<br /><br />";
} else {
echo "login failed!";
}
mysqli_close($conn);
?>
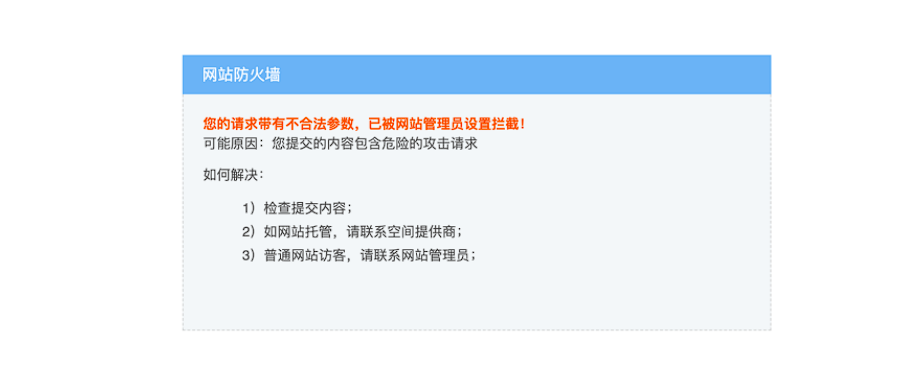
部署Waf相关防护代码
[root@nginx ~]# cd /soft/src/
[root@nginx src]# git clone https://github.com/loveshell/ngx_lua_waf.git
#克隆不下了直接从github上⼿动下载上传解压
[root@nginx src]# rz ngx_lua_waf-master.zip
[root@nginx src]# unzip ngx_lua_waf-master.zip
Archive: ngx_lua_waf-master.zip
314a2f62ec350eba9b5d25b55b5b0a723e20a8d0
creatyuan: ngx_lua_waf-master/
inflatyuan: ngx_lua_waf-master/.gitattributes
inflatyuan: ngx_lua_waf-master/.gitignore
inflatyuan: ngx_lua_waf-master/README.md
inflatyuan: ngx_lua_waf-master/config.lua
inflatyuan: ngx_lua_waf-master/init.lua
inflatyuan: ngx_lua_waf-master/install.sh
inflatyuan: ngx_lua_waf-master/waf.lua
creatyuan: ngx_lua_waf-master/wafconf/
inflatyuan: ngx_lua_waf-master/wafconf/args
inflatyuan: ngx_lua_waf-master/wafconf/cookie
inflatyuan: ngx_lua_waf-master/wafconf/post
inflatyuan: ngx_lua_waf-master/wafconf/url
inflatyuan: ngx_lua_waf-master/wafconf/user-agent
extractyuan: ngx_lua_waf-master/wafconf/whiteurl
# mkdir -p /soft/openresty/nginx/logs/waf/
//把ngx_lua_waf复制到nginx的⽬录下,解压命名为waf
[root@nginx ~]# cp -r ngx_lua_waf-master /soft/openresty/nginx/lua/waf
//在nginx.conf的http段添加(注意路径)
lua_package_path "/soft/openresty/nginx/lua/waf/?.lua";
lua_shared_dict limit 10m;
init_by_lua_file /soft/openresty/nginx/lua/waf/init.lua;
access_by_lua_file /soft/openresty/nginx/lua/waf/waf.lua;
//配置config.lua⾥的waf规则⽬录(⼀般在waf/wafconf/⽬录下)
RulePath = "/soft/openresty/nginx/lua/waf/wafconf/"
logdir = "/soft/openresty/nginx/logs/waf/"
#绝对路径如有变动,需对应修改, 然后重启nginx即可
7.Nginx + lua 防⽌ Sql注⼊
[root@nginx ~]# vim /soft/openresty/nginx/lua/waf/wafconf/post
\sor\s+
这个正则表达式有两部分:
- \s: 表示匹配任意空⽩字符,包括空格、制表符、换⾏符等。
- or: 表示匹配这三个字⺟的顺序,即 or。
- \s+: 表示匹配⼀个或多个任意空⽩字符,即与\s类似,但⽐\s更加宽松,可以匹配多个连续的空⽩字符。
整个正则表达式的含义是匹配字符串中的⼀个空⽩字符或多个空⽩字符,后跟or,再后跟⼀个或多个空⽩字
符。这个正则表达式通常⽤于匹配字符串中的特定分隔符。