DNS正、反向解析+负载均衡+智能DNS+密钥认证
| 主机名 | IP | 软件包 | 系统版本 | 内核版本 | 实验环境 |
| master | 192.168.30.130 |
bind.x86_64 32:9.8.2-0.17.rc1.el6_4.6 bind-chroot.x86_64 32:9.8.2-0.17.rc1.el6_4.6 bind-utils.x86_64 32:9.8.2-0.17.rc1.el6_4.6 |
|
2.6.32-431.el6.x86_64 | 关闭SElinux、清空iptables ,并设置开机关闭 |
| slave1 | 192.168.30.131 |
软件包介绍:
| 软件包名 | 简介 |
| bind.x86_64 32:9.8.2-0.17.rc1.el6_4.6 | DNS服务主程序包,Berkeley Internet Name Domain 伯克利英特网名称域系统,有BIND4.8.9三个版本BIND8融合了许多提高效率和安全性的技术,BIND9支持IPv6,密钥加密,多处理器支持,线程安全操作,增量区传送等 |
| bind-chroot.x86_64 32:9.8.2-0.17.rc1.el6_4.6 | 使bind运行时的/目录不是系统真正的/,而是系统的一个子目录,这样提高了系统的安全性。Bind访问的范围仅限于这个子目录的范围内,无法进一步提升,进入系统其它目录中 |
| bind-utils.x86_64 32:9.8.2-0.17.rc1.el6_4.6 | 包客户端工具,默认安装,用于搜索域名指令 |
| bind-libs-9.8.2-0.17.rc1.el6_4.6.x86_64 | 提供一些库文件 |
| bind-dyndb-ldap-2.3-5.el6.x86_64.rpm | LDAP的插件,提供主机名IP动态更新(非必装) |
安装:
[root@master ~]# yum install -y bind bind-utils bind-chroot
设置开机启动:
[root@master ~]# chkconfig named on
[root@master ~]# chkconfig named --list
named 0:off 1:off 2:on 3:on 4:on 5:on 6:off
启动named服务并查看
[root@master ~]# /etc/init.d/named start Generating /etc/rndc.key: [ OK ] Starting named: [ OK ] [root@master ~]# mount /dev/mapper/vg_master-LogVol00 on / type ext4 (rw) proc on /proc type proc (rw) sysfs on /sys type sysfs (rw) devpts on /dev/pts type devpts (rw,gid=5,mode=620) tmpfs on /dev/shm type tmpfs (rw) /dev/sda1 on /boot type ext4 (rw) none on /proc/sys/fs/binfmt_misc type binfmt_misc (rw) /dev/sr0 on /media/cdrom type iso9660 (ro) /etc/named on /var/named/chroot/etc/named type none (rw,bind) /var/named on /var/named/chroot/var/named type none (rw,bind) /etc/named.conf on /var/named/chroot/etc/named.conf type none (rw,bind) /etc/named.rfc1912.zones on /var/named/chroot/etc/named.rfc1912.zones type none (rw,bind) /etc/rndc.key on /var/named/chroot/etc/rndc.key type none (rw,bind) /usr/lib64/bind on /var/named/chroot/usr/lib64/bind type none (rw,bind) /etc/named.iscdlv.key on /var/named/chroot/etc/named.iscdlv.key type none (rw,bind) /etc/named.root.key on /var/named/chroot/etc/named.root.key type none (rw,bind)
可以验证下配置文件与chroot下挂载的文件是否为同一配置文件
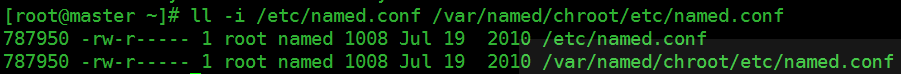
可以看出inode的值相同,所以这两个文件实际是同一个文件。
配置named.conf(正向解析)
[root@master ~]# vim /var/named/chroot/etc/named.conf //尽量使用此路径修改,若修改文件出现错误,重启named服务后,该路径下会没有文件,要去/etc/目录下修改
//
// // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // options { listen-on port 53 { any; }; //设置侦听端口和IP listen-on-v6 port 53 { ::1; }; //IPv6的端口和地址 directory "/var/named"; //DNS的工作目录 dump-file "/var/named/data/cache_dump.db"; //缓存信息保存地址 statistics-file "/var/named/data/named_stats.txt"; //服务器的数据信息 memstatistics-file "/var/named/data/named_mem_stats.txt"; //记录日志相关 allow-query { any; }; //允许谁来查 recursion yes; //允许递归查询 dnssec-enable yes; //安全相关 dnssec-validation yes; //安全相关 dnssec-lookaside auto; //安全相关 /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; //key文件 managed-keys-directory "/var/named/dynamic"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { //13个根域服务器地址 type hint; //type类型,hint为根 file "named.ca"; }; include "/etc/named.rfc1912.zones"; //include中的文件也是主配置文件 include "/etc/named.root.key";
include配置文件
[root@master ~]# cp /etc/named.rfc1912.zones{,.bak} [root@master ~]# vim /var/named/chroot/etc/named.rfc1912.zones // named.rfc1912.zones: // // Provided by Red Hat caching-nameserver package // // ISC BIND named zone configuration for zones recommended by // RFC 1912 section 4.1 : localhost TLDs and address zones // and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02. txt // (c)2007 R W Franks // // See /usr/share/doc/bind*/sample/ for example named configuration files. // //在原有基础上添加如下内容 zone "sishen.cn" IN { //域名 type master; //type类型:master file "sishen.cn.zone"; //区域文件保存位置 allow-update { none; };//是否允许动态更新(DNS和DHCP结合时使用) };
建立zone记录文件
[root@master ~]# cd /var/named/chroot/var/named/ [root@master named]# cp -p named.localhost sishen.cn.zone //使用-p参数带上权限 [root@master named]# vim sishen.cn.zone $TTL 1D #最大生存时间,1D就是1天,TTL:缓存时间 time to live @ IN SOA dns.sishen.cn. root.sishen.cn. ( #@代表去域名,此表示sishen.cn, IN-->Internet Name; SOA-->起始授权记录,Start of Authority Record; 主机名 -->DNS名称 DNS管理员邮箱地址,@用.代替,@有其他含义 0 ; serial #序列号,手工改,同步用 1D ; refresh#1天更新,多久请求更新 1H ; retry#1天联系不上,过一个小时再试 1W ; expire#1周时间过期,一直联系不上时 3H ) ; minimum#最短过期时间,3小时,不需要更新 #下面写的内内容没有写@符号,代表继承了上层 NS dns.sishen.cn. #最好跟上面同步,. 一定要跟上 #主机头,这里填写主机头,注意要对上面的NS记录做一条主机记录 dns A 192.168.30.130 ftp A 192.168.30.200 www1 CNAME ftp.sishen.cn.
检查zone文件是否有错
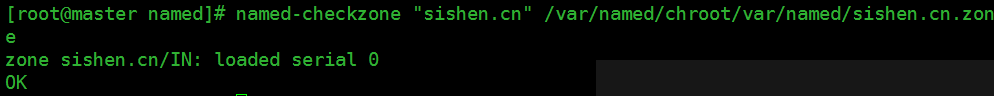
检查主配置文件是否有错(没有任何提示表示正常)
[root@master ~]# named-checkconf
[root@master ~]# echo $?
0
重启named服务
测试
[root@master ~]# vim /etc/sysconfig/network-scripts/ifcfg-eth0 DEVICE=eth0 TYPE=Ethernet UUID=6712b6c4-a50e-4181-a986-7012c8b2e3c4 ONBOOT=yes NM_CONTROLLED=yes BOOTPROTO=none HWADDR=00:0C:29:14:68:DC IPADDR=192.168.30.130 PREFIX=24 GATEWAY=192.168.30.2 DNS1=192.168.30.130 #修改为自己的IP DOMAIN=119.29.29.29 DEFROUTE=yes IPV4_FAILURE_FATAL=yes IPV6INIT=no NAME="System eth0"
重启网络服务
[root@master ~]# service network restart Shutting down interface eth0: [ OK ] Shutting down loopback interface: [ OK ] Bringing up loopback interface: [ OK ] Bringing up interface eth0: Determining if ip address 192.168.30.130 is already in use for device eth0... [ OK ] [root@master ~]# cat /etc/resolv.conf # Generated by NetworkManager nameserver 192.168.30.130 search 119.29.29.29
测试ping命令
[root@master ~]# ping -c 3 dns.sishen.cn PING dns.sishen.cn (192.168.30.130) 56(84) bytes of data. 64 bytes from 192.168.30.130: icmp_seq=1 ttl=64 time=0.038 ms 64 bytes from 192.168.30.130: icmp_seq=2 ttl=64 time=0.009 ms 64 bytes from 192.168.30.130: icmp_seq=3 ttl=64 time=0.036 ms --- dns.sishen.cn ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 7167ms rtt min/avg/max/mdev = 0.009/0.027/0.038/0.014 ms
使用dig命令测试DNS解析
[root@master ~]# dig ftp.sishen.cn @localhost ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> ftp.sishen.cn @localhost ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19758 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;ftp.sishen.cn. IN A ;; ANSWER SECTION: ftp.sishen.cn. 86400 IN A 192.168.30.200 ;; AUTHORITY SECTION: sishen.cn. 86400 IN NS dns.sishen.cn. ;; ADDITIONAL SECTION: dns.sishen.cn. 86400 IN A 192.168.30.130 ;; Query time: 1 msec ;; SERVER: ::1#53(::1) ;; WHEN: Mon May 14 22:38:20 2018 ;; MSG SIZE rcvd: 81
查询别名相关信息
[root@master ~]# dig www1.sishen.cn @localhost ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> www1.sishen.cn @localhost ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41306 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;www1.sishen.cn. IN A ;; ANSWER SECTION: www1.sishen.cn. 86400 IN CNAME ftp.sishen.cn. ftp.sishen.cn. 86400 IN A 192.168.30.200 ;; AUTHORITY SECTION: sishen.cn. 86400 IN NS dns.sishen.cn. ;; ADDITIONAL SECTION: dns.sishen.cn. 86400 IN A 192.168.30.130 ;; Query time: 1 msec ;; SERVER: ::1#53(::1) ;; WHEN: Mon May 14 22:39:20 2018 ;; MSG SIZE rcvd: 100
DNS正向解析一般思路:1)named.conf 2)include,named.rfc..... 3) 修改区域记录文件 XXX.cn.zone 4)检查配置文件 named-checkconf named-checkzone 5)重启服务 6)dig解析测试
DNS反向解析
[root@master ~]# vim /etc/named.rfc1912.zones #添加如下内容 zone "132.30.168.192.in-addr.arpa"IN { type master; file "sishen.cn.rev"; allow-update { none; }; };
[root@master named]# vim sishen.cn.rev $TTL 1D @ IN SOA dns.sishen.cn. root.sishen.cn. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS dns.sishen.cn. 100 IN PTR aa.sishen.cn. 101 IN PTR bb.sishen.cn. #PTR指针 ,反向解析记录
检查配置文件
[root@master named]# named-checkzone "30.168.192.in-addr,arpa" /var/named/sishen.cn.rev
zone 30.168.192.in-addr,arpa/IN: loaded serial 0
OK
[root@master named]# cd
[root@master ~]# named-checkconf
[root@master ~]# echo $?
0
重启服务测试
[root@master ~]# service named restart
Stopping named: . [ OK ]
Starting named: [ OK ]
[root@master ~]# dig -x 192.168.30.100 @localhost ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> -x 192.168.30.100 @localhost ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52975 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;100.30.168.192.in-addr.arpa. IN PTR ;; ANSWER SECTION: 100.30.168.192.in-addr.arpa. 86400 IN PTR aa.sishen.cn. ;; AUTHORITY SECTION: 30.168.192.in-addr.arpa. 86400 IN NS dns.sishen.cn. ;; ADDITIONAL SECTION: dns.sishen.cn. 86400 IN A 192.168.30.130 ;; Query time: 1 msec ;; SERVER: ::1#53(::1) ;; WHEN: Mon May 14 22:55:08 2018 ;; MSG SIZE rcvd: 105
到此,反向解析已成功实现。
配置递归查询
[root@master ~]# vim /var/named/chroot/etc/named.conf ................. recursion yes; //允许递归查询,默认支持递归查询 # dnssec-enable yes; //安全相关 # dnssec-validation yes; //安全相关 # dnssec-lookaside auto; //安全相关 .......................
#实验环境需要注释掉安全相关的三条内容,客户端才能进行DNS递归查询,其他内容不用管,同时关闭了加密
通讯功能,才可以和根服务器进行迭代查询
配置DNS转发
再配置一台slave
[root@slave ~]# yum install -y bind bind-chroot bind-utils
启动服务

[root@slave ~]# cp /etc/named.conf{,.bak} [root@slave ~]# vim /var/named/chroot/etc/named.conf
......................... options { listen-on port 53 { any; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { any; }; recursion yes; # dnssec-enable yes; # dnssec-validation yes; # dnssec-lookaside auto; forward only; //only,仅转发,first,先查找再转发,实验效果,仅转发 forwarders { 192.168.30.130; };
.................其他不需要更改
测试:
[root@slave ~]# named-checkconf [root@slave ~]# echo $? 0 [root@slave ~]# service named reload Reloading named: [ OK ] [root@slave ~]# dig @localhost ftp.sishen.cn ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> @localhost ftp.sishen.cn ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 22292 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 13, ADDITIONAL: 0 ;; QUESTION SECTION: ;ftp.sishen.cn. IN A ;; ANSWER SECTION: ftp.sishen.cn. 86400 IN A 192.168.30.200 ;; AUTHORITY SECTION: . 516529 IN NS m.root-servers.net. . 516529 IN NS d.root-servers.net. . 516529 IN NS j.root-servers.net. . 516529 IN NS e.root-servers.net. . 516529 IN NS h.root-servers.net. . 516529 IN NS l.root-servers.net. . 516529 IN NS a.root-servers.net. . 516529 IN NS g.root-servers.net. . 516529 IN NS c.root-servers.net. . 516529 IN NS b.root-servers.net. . 516529 IN NS f.root-servers.net. . 516529 IN NS k.root-servers.net. . 516529 IN NS i.root-servers.net. ;; Query time: 331 msec ;; SERVER: ::1#53(::1) ;; WHEN: Mon May 14 23:38:47 2018 ;; MSG SIZE rcvd: 258
从服务器配置
[root@slave ~]# cp /etc/named.rfc1912.zones{,.bak} [root@slave ~]# vim /etc/named.rfc1912.zones ...........................原有基础上添加如下内容 zone "sishen.cn" IN { type slave; file "slaves/sishen.cn.zone.slave"; masters { 192.168.30.130; }; }; ...................
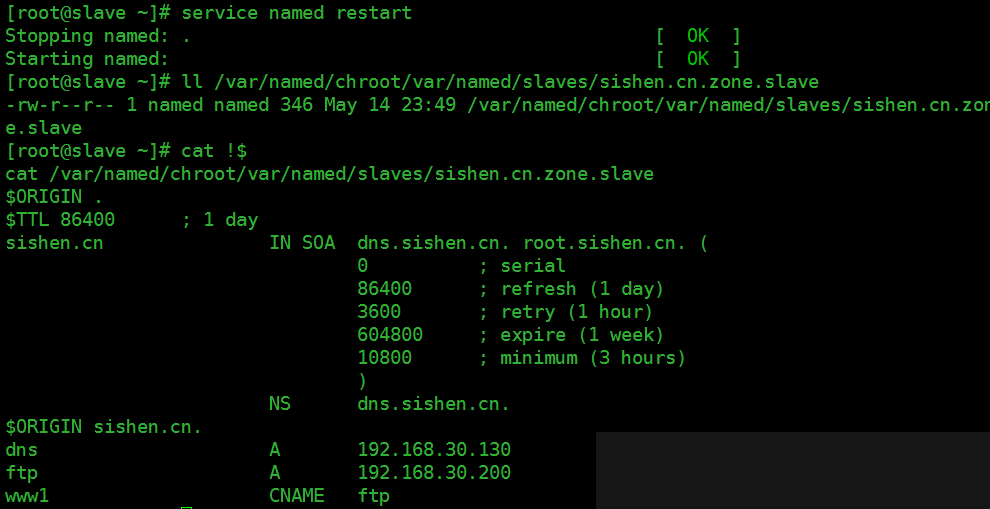
重启named服务,sishen.cn.zone.slave文件会自动生成
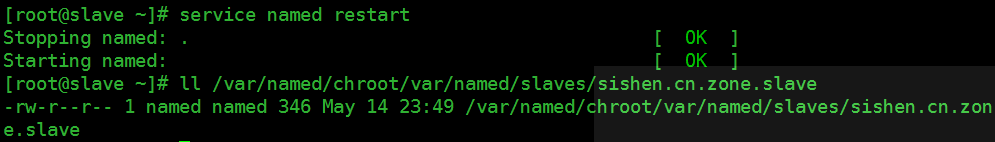
查看sishen.cn.zone.slave文件内容
配置主从密钥认证
主从都需要同步时间
[root@master ~]# ntpdate cn.ntp.org.cn
[root@slave ~]# ntpdate cn.ntp.org.cn
准备密钥
[root@master ~]# cd /var/named/chroot/ [root@master chroot]# dnssec-keygen -a hmac-md5 -b 128 -n HOST dnssec Kdnssec.+157+11286
ps: -a,algorithm 算法的意思,这里采用Hmac-MD5的加散发 -b,keysize 生成密钥的长度 128位 -n,nametype 密钥类型,主机类型 HOST,常用的:ZONE,HOST,ENTITY,USER,OTHER 默认认证是ZONE类型 dnssec,生成密钥的名字
查看密钥对
[root@master chroot]# ll Kdnssec.+157+11286.*
-rw------- 1 root root 50 May 14 16:07 Kdnssec.+157+11286.key
-rw------- 1 root root 165 May 14 16:07 Kdnssec.+157+11286.private
查看密钥
[root@master chroot]# cat Kdnssec.+157+11286.key
dnssec. IN KEY 512 3 157 NMSksEfOw6QCrptK1DPPZA==
修改named.conf文件支持密钥认证
[root@master ~]# vim /var/named/chroot/etc/named.conf ..............取消安全相关的注释 dnssec-enable yes; //安全相关 dnssec-validation yes; //安全相关 dnssec-lookaside auto; //安全相关 //添加如下内容 key dnsseckey { //定义传输过程中使用的密钥名字 algorithm hmac-md5; //使用的算法 secret "NMSksEfOw6QCrptK1DPPZA=="; //密钥 };
配置zone使用密钥传输
[root@master ~]# vim /var/named/chroot/etc/named.rfc1912.zones ...................将原zone"sishen.cn"修改为如下内容 zone "sishen.cn" IN { //域名 type master; //type类型:master file "sishen.cn.zone"; //区域文件保存位置 allow-transfer { key dnsseckey; }; //允许使用密钥传输,采用密钥同步 };
检查配置文件:

从服务器配置文件
[root@slave ~]# vim /var/named/chroot/etc/named.conf //取消dnssec三行注释 dnssec-enable yes; dnssec-validation yes; dnssec-lookaside auto; //添加如下内容: key dnsseckey { algorithm hmac-md5; secret "NMSksEfOw6QCrptK1DPPZA==";
修改named.rfc1912.zones文件
[root@slave ~]# vim /var/named/chroot/etc/named.rfc1912.zones ..........................将原zone"sishen.cn"修改为如下内容 zone "sishen.cn" IN { type slave; file "slaves/sishen.cn.zone.sec"; masters { 192.168.30.130 key dnsseckey; }; };
检查配置文件:
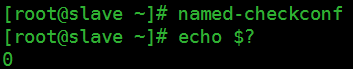
重启服务测试:
sishen.cn.zone.sec文件已生成

测试:
[root@slave ~]# dig @localhost ftp.sishen.cn ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> @localhost ftp.sishen.cn ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 45294 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;ftp.sishen.cn. IN A ;; ANSWER SECTION: ftp.sishen.cn. 86400 IN A 192.168.30.200 ;; AUTHORITY SECTION: sishen.cn. 86400 IN NS dns.sishen.cn. ;; ADDITIONAL SECTION: dns.sishen.cn. 86400 IN A 192.168.30.130 ;; Query time: 1 msec ;; SERVER: ::1#53(::1) ;; WHEN: Mon May 14 16:47:11 2018 ;; MSG SIZE rcvd: 81
配置DNS负载均衡
在主上修改named.conf
[root@master ~]# vim /var/named/chroot/var/named/sishen.cn.zone $TTL 1D @ IN SOA dns.sishen.cn. root.sishen.cn. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS dns.sishen.cn. dns A 192.168.30.130 ftp A 192.168.30.200 www1 CNAME ftp.sishen.cn. www.sishen.cn. 1 A 192.168.30.100 www.sishen.cn. 1 A 192.168.30.101 www.sishen.cn. 1 A 192.168.30.102 www.sishen.cn. 1 A 192.168.30.103
重启测试
[root@master ~]# ping -c 2 www.sishen.cn PING www.sishen.cn (192.168.30.102) 56(84) bytes of data. .................... [root@master ~]# ping -c 2 www.sishen.cn PING www.sishen.cn (192.168.30.103) 56(84) bytes of data. ..................... [root@master ~]# ping -c 2 www.sishen.cn PING www.sishen.cn (192.168.30.100) 56(84) bytes of data. ..................... [root@master ~]# ping -c 2 www.sishen.cn PING www.sishen.cn (192.168.30.101) 56(84) bytes of data. ..................... 会发现每次ping的IP地址都不一样
智能DNS
在主上修改named.conf
[root@master ~]# vim /var/named/chroot/etc/named.conf // // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // acl local { 127/8; }; acl network { 192.168.30/24; }; options { listen-on port 53 { any; }; //设置侦听端口和IP listen-on-v6 port 53 { ::1; }; //IPv6的端口和地址 directory "/var/named"; //DNS的工作目录 dump-file "/var/named/data/cache_dump.db"; //缓存信息保存地址 statistics-file "/var/named/data/named_stats.txt"; //服务器的数据信息 memstatistics-file "/var/named/data/named_mem_stats.txt"; //记录日志相关 allow-query { any; }; //允许谁来查 recursion yes; //允许递归查询 dnssec-enable yes; //安全相关 dnssec-validation yes; //安全相关 dnssec-lookaside auto; //安全相关 /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; //key文件 managed-keys-directory "/var/named/dynamic"; }; key dnsseckey { algorithm hmac-md5; secret "NMSksEfOw6QCrptK1DPPZA=="; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; view local { match-clients { local; }; recursion yes; include "/etc/named.local"; }; view network { match-clients { network; }; recursion yes; include "/etc/named.network"; }; //zone "." IN { //13个根域服务器地址 // type hint; //type类型,hint为根 // file "named.ca"; //}; //include "/etc/named.rfc1912.zones"; //include中的文件也是主配置文件 include "/etc/named.root.key";
include文件创建
[root@master ~]# cd /var/named/chroot/etc/ [root@master etc]# cp -a named.rfc1912.zones named.local [root@master etc]# cp -a named.rfc1912.zones named.network [root@master etc]# vim named.local // named.rfc1912.zones: // // Provided by Red Hat caching-nameserver package // // ISC BIND named zone configuration for zones recommended by // RFC 1912 section 4.1 : localhost TLDs and address zones // and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt // (c)2007 R W Franks // // See /usr/share/doc/bind*/sample/ for example named configuration files. // zone "." IN { type hint; file "named.ca"; }; zone "localhost" IN { type master; file "named.localhost"; allow-update { none; }; }; //zone "sishen.cn" IN { //域名 // type master; //type类型:master // file "sishen.cn.zone"; //区域文件保存位置 // allow-update { none; };//是否允许动态更新(DNS和DHCP结合时使用) //}; zone "sishen.cn" IN { //域名 type master; //type类型:master file "sishen.cn.local"; //区域文件保存位置 allow-transfer { key dnsseckey; }; //允许使用密钥传输,采用密钥同步 }; zone "30.168.192.in-addr.arpa"IN { type master; file "sishen.cn.rev"; allow-update { none; }; }; zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN { type master; file "named.loopback"; allow-update { none; }; }; zone "1.0.0.127.in-addr.arpa" IN { type master; file "named.loopback"; allow-update { none; }; }; zone "0.in-addr.arpa" IN { type master; file "named.empty"; allow-update { none; }; };
[root@master etc]# vim named.network
// named.rfc1912.zones:
//
// Provided by Red Hat caching-nameserver package
//
// ISC BIND named zone configuration for zones recommended by
// RFC 1912 section 4.1 : localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "." IN {
type hint;
file "named.ca";
};
//zone "sishen.cn" IN { //域名
// type master; //type类型:master
// file "sishen.cn.zone"; //区域文件保存位置
// allow-update { none; };//是否允许动态更新(DNS和DHCP结合时使用)
//};
zone "sishen.cn" IN { //域名
type master; //type类型:master
file "sishen.cn.network"; //区域文件保存位置
allow-transfer { key dnsseckey; }; //允许使用密钥传输,采用密钥同步
};
zone "30.168.192.in-addr.arpa"IN {
type master;
file "sishen.cn.rev";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
创建记录文件
[root@master named]# pwd /var/named [root@master named]# cp -a sishen.cn.zone sishen.cn.local [root@master named]# cp -a sishen.cn.zone sishen.cn.network [root@master named]# vim sishen.cn.local $TTL 1D @ IN SOA dns.sishen.cn. root.sishen.cn. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS dns.sishen.cn. dns A 192.168.30.130 www A 192.168.30.100 [root@master named]# vim sishen.cn.network $TTL 1D @ IN SOA dns.sishen.cn. root.sishen.cn. ( 0 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS dns.sishen.cn. dns A 192.168.30.130 www A 192.168.30.101
重启服务测试
[root@master ~]# service named restart Stopping named: [ OK ] Starting named: [ OK ] [root@master ~]# dig @127.0.0.1 www.sishen.cn ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> @127.0.0.1 www.sishen.cn ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23147 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;www.sishen.cn. IN A ;; ANSWER SECTION: www.sishen.cn. 86400 IN A 192.168.30.100 ;; AUTHORITY SECTION: sishen.cn. 86400 IN NS dns.sishen.cn. ;; ADDITIONAL SECTION: dns.sishen.cn. 86400 IN A 192.168.30.130 ;; Query time: 1 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Mon May 14 17:25:45 2018 ;; MSG SIZE rcvd: 8
[root@master ~]# dig @192.168.30.130 www.sishen.cn
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> @192.168.30.130 www.sishen.cn
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42496
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1
;; QUESTION SECTION:
;www.sishen.cn. IN A
;; ANSWER SECTION:
www.sishen.cn. 86400 IN A 192.168.30.101
;; AUTHORITY SECTION:
sishen.cn. 86400 IN NS dns.sishen.cn.
;; ADDITIONAL SECTION:
dns.sishen.cn. 86400 IN A 192.168.30.130
;; Query time: 1 msec
;; SERVER: 192.168.30.130#53(192.168.30.130)
;; WHEN: Mon May 14 17:26:52 2018
;; MSG SIZE rcvd: 81
---恢复内容结束---


