第五周作业
2、作业解答
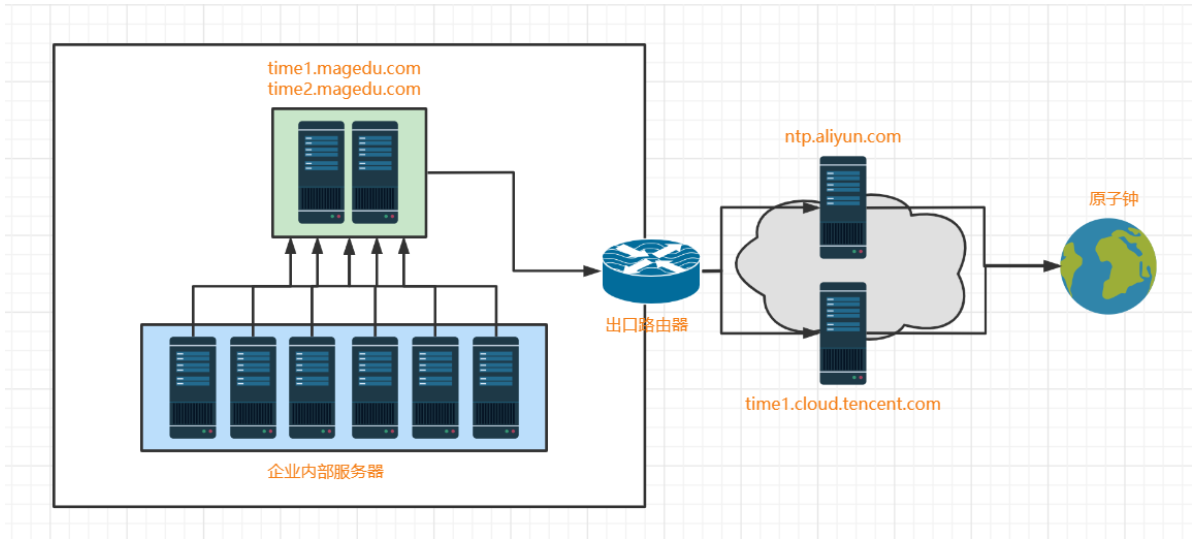
#网络拓扑 chrony-server: 192.168.100.202、192.168.100.203 chrony-client: 192.168.100.204、192.168.100.205 互联网上级时钟源: ntp.aliyun.com、time1.cloud.tencent.com #安装chrony软件包 [root@chrony-server01 ~]#yum install -y chrony [root@chrony-server02 ~]#yum install -y chrony [root@chrony-client01 ~]#yum install -y chrony [root@chrony-client02 ~]#yum install -y chrony #chrony-server修改配置 [root@chrony-server01 ~]#cat /etc/chrony.conf | grep -vE "^#|^$" server ntp.aliyun.com iburst server time1.cloud.tencent.com iburst driftfile /var/lib/chrony/drift makestep 1.0 3 rtcsync allow 192.168.100.0/24 local stratum 10 logdir /var/log/chrony [root@chrony-server02 ~]#cat /etc/chrony.conf | grep -vE "^#|^$" server ntp.aliyun.com iburst server time1.cloud.tencent.com iburst driftfile /var/lib/chrony/drift makestep 1.0 3 rtcsync allow 192.168.100.0/24 local stratum 10 logdir /var/log/chrony [root@chrony-server02 ~]# #chrony-client修改配置 [root@chrony-client01 ~]#cat /etc/chrony.conf | grep -vE "^#|^$" server time1.magedu.com iburst server time2.magedu.com iburst driftfile /var/lib/chrony/drift makestep 1.0 3 rtcsync logdir /var/log/chrony [root@chrony-client01 ~]#cat /etc/hosts | grep time[12].magedu.com 192.168.100.202 time1.magedu.com 192.168.100.203 time2.magedu.com [root@chrony-client02 ~]#cat /etc/chrony.conf | grep -vE "^#|^$" server time1.magedu.com iburst server time2.magedu.com iburst driftfile /var/lib/chrony/drift makestep 1.0 3 rtcsync logdir /var/log/chrony [root@chrony-client02 ~]#cat /etc/hosts | grep time[12].magedu.com 192.168.100.202 time1.magedu.com 192.168.100.203 time2.magedu.com #启动chrony服务 [root@chrony-server01 ~]#systemctl restart chronyd [root@chrony-server02 ~]#systemctl restart chronyd [root@chrony-client01 ~]#systemctl restart chronyd [root@chrony-client02 ~]#systemctl restart chronyd #检查时间同步情况 [root@chrony-server01 ~]#chronyc sources -v 210 Number of sources = 2 =============================================================================== ^+ 203.107.6.88 2 7 377 31 +2465us[+2465us] +/- 33ms ^* 139.199.215.251 2 6 327 33 -407us[ -315us] +/- 53ms [root@chrony-server01 ~]# [root@chrony-server02 ~]#chronyc sources -v 210 Number of sources = 2 =============================================================================== ^+ 203.107.6.88 2 6 377 8 -6999us[-8441us] +/- 29ms ^* 139.199.215.251 2 6 377 6 +2483us[+1039us] +/- 26ms [root@chrony-client01 ~]#chronyc sources -v 210 Number of sources = 2 =============================================================================== ^+ time1.magedu.com 3 6 377 6 -599us[ -37us] +/- 20ms ^* time2.magedu.com 3 6 377 5 +934us[+1510us] +/- 27ms [root@chrony-client02 ~]#chronyc sources -v 210 Number of sources = 2 =============================================================================== ^* time1.magedu.com 3 6 377 53 +6391us[+8113us] +/- 25ms ^- time2.magedu.com 3 6 377 52 +8114us[+8114us] +/- 20ms
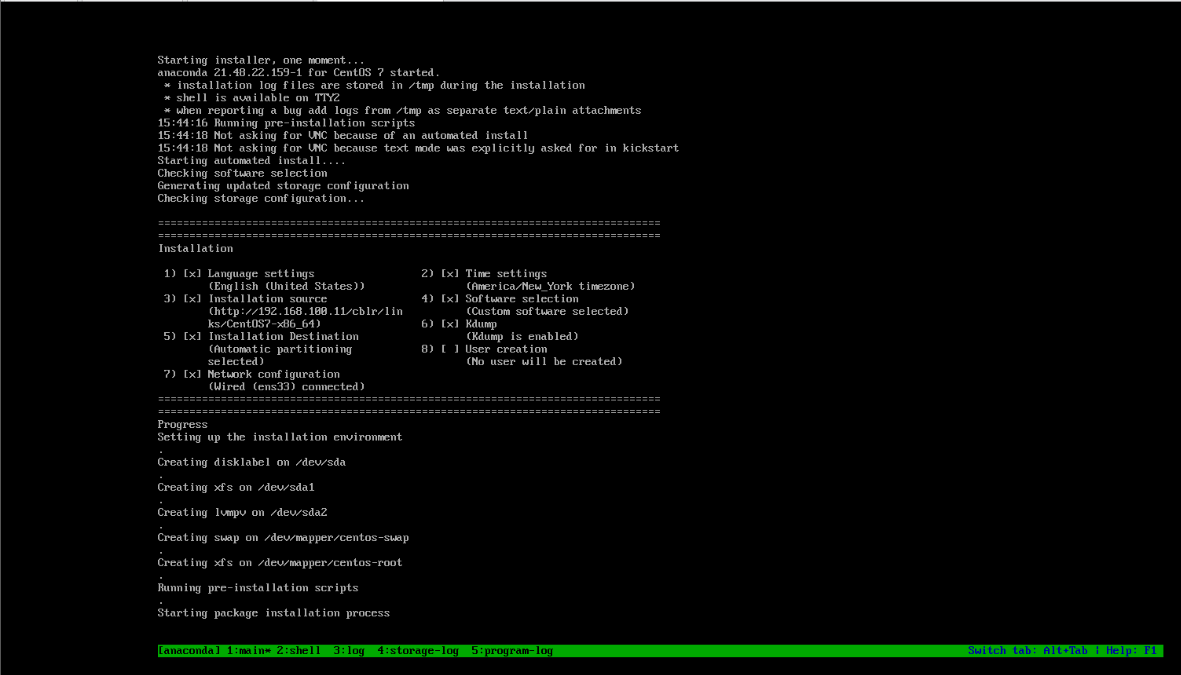
#Cobbler服务器信息 OSVersion: CentOS 7.9 kernel: 3.10.0-1160.el7.x86_64 Ipaddr: 192.168.100.11 Netmode: NAT #安装软件包 [root@centos7 ~]#wget -O /etc/yum.repos.d/epel.repo https://mirrors.aliyun.com/repo/epel-7.repo [root@centos7 ~]#yum clean all [root@centos7 ~]#yum makecache [root@centos7 ~]#yum install -y cobbler httpd tftp dhcp #启动服务 [root@centos7 yum.repos.d]#systemctl start cobblerd [root@centos7 yum.repos.d]#systemctl start httpd [root@centos7 yum.repos.d]#systemctl start tftp [root@centos7 yum.repos.d]#systemctl start dhcpd Job for dhcpd.service failed because the control process exited with error code. See "systemctl status dhcpd.service" and "journalctl -xe" for details. 说明:dhcp服务启动失败,是由于默认配置文件不正确导致,后面再进行修改。 #修改cobbler配置 vim /etc/cobbler/settings next_server: 192.168.100.11 #把127.0.0.1修改为cobbler服务器IP server: 192.168.100.11 #把127.0.0.1修改为cobbler服务器IP manage_dhcp: 1 #把0修改为1 default_password_crypted: "$1$mF86/UHC$WvcIcX2t6crBz2onWxyac." #默认root密码为cobbler 如果需要修改默认密码,可以使用openssl命令生成加密密码: openssl passwd -1 -salt 'random-phrase-here' 'abc1234567' $1$random-p$iQiGTzUqqxSGzqdf8w9YM1 #重启cobbler服务 [root@centos7 cobbler]#systemctl restart cobblerd #配置dhcp服务 [root@centos7 ~]#vim /etc/cobbler/dhcp.template [root@centos7 ~]#vim /etc/dhcp/dhcpd.conf subnet 192.168.100.0 netmask 255.255.255.0 { option routers 192.168.100.2; option domain-name-servers 192.168.100.2; option subnet-mask 255.255.255.0; range dynamic-bootp 192.168.100.100 192.168.100.254; default-lease-time 21600; max-lease-time 43200; next-server 192.168.100.11; class "pxeclients" { match if substring (option vendor-class-identifier, 0, 9) = "PXEClient"; if option pxe-system-type = 00:02 { filename "ia64/elilo.efi"; } else if option pxe-system-type = 00:06 { filename "grub/grub-x86.efi"; } else if option pxe-system-type = 00:07 { filename "grub/grub-x86_64.efi"; } else if option pxe-system-type = 00:09 { filename "grub/grub-x86_64.efi"; } else { filename "pxelinux.0"; } } } [root@centos7 ~]#systemctl restart dhcpd #同步文件至tftp目录 [root@centos7 ~]#cobbler sync task started: 2022-12-13_143752_sync task started (id=Sync, time=Tue Dec 13 14:37:52 2022) running pre-sync triggers cleaning trees removing: /var/lib/tftpboot/pxelinux.cfg/default removing: /var/lib/tftpboot/grub/images removing: /var/lib/tftpboot/grub/efidefault removing: /var/lib/tftpboot/s390x/profile_list copying bootloaders copying distros to tftpboot copying images generating PXE configuration files generating PXE menu structure rendering DHCP files generating /etc/dhcp/dhcpd.conf rendering TFTPD files generating /etc/xinetd.d/tftp cleaning link caches running post-sync triggers running python triggers from /var/lib/cobbler/triggers/sync/post/* running python trigger cobbler.modules.sync_post_restart_services running: dhcpd -t -q received on stdout: received on stderr: running: service dhcpd restart received on stdout: received on stderr: Redirecting to /bin/systemctl restart dhcpd.service running shell triggers from /var/lib/cobbler/triggers/sync/post/* running python triggers from /var/lib/cobbler/triggers/change/* running python trigger cobbler.modules.manage_genders running python trigger cobbler.modules.scm_track running shell triggers from /var/lib/cobbler/triggers/change/* *** TASK COMPLETE *** #挂载安装光盘镜像 [root@centos7 ~]#mount /dev/sr0 /mnt mount: /dev/sr0 is write-protected, mounting read-only [root@centos7 ~]#df -h Filesystem Size Used Avail Use% Mounted on devtmpfs 979M 0 979M 0% /dev tmpfs 991M 0 991M 0% /dev/shm tmpfs 991M 9.6M 981M 1% /run tmpfs 991M 0 991M 0% /sys/fs/cgroup /dev/mapper/centos-root 50G 4.6G 46G 10% / /dev/md1 9.8G 106M 9.1G 2% /backup /dev/sda1 1014M 141M 874M 14% /boot /dev/md0 9.8G 37M 9.2G 1% /mydata /dev/mapper/testvg-testlv 2.9G 16M 2.7G 1% /users /dev/mapper/centos-home 147G 33M 147G 1% /home tmpfs 199M 0 199M 0% /run/user/0 /dev/sr0 4.4G 4.4G 0 100% /mnt #拷贝光盘镜像到cobbler的http文件目录(/var/www/cobbler) [root@centos7 ~]#cobbler import --path=/mnt/ --name=CentOS7 --arch=x86_64 task started: 2022-12-13_145249_import task started (id=Media import, time=Tue Dec 13 14:52:49 2022) Found a candidate signature: breed=suse, version=opensuse15.0 Found a candidate signature: breed=suse, version=opensuse15.1 Found a candidate signature: breed=redhat, version=rhel6 Found a candidate signature: breed=redhat, version=rhel7 Found a matching signature: breed=redhat, version=rhel7 Adding distros from path /var/www/cobbler/ks_mirror/CentOS7-x86_64: creating new distro: CentOS7-x86_64 trying symlink: /var/www/cobbler/ks_mirror/CentOS7-x86_64 -> /var/www/cobbler/links/CentOS7-x86_64 creating new profile: CentOS7-x86_64 associating repos checking for rsync repo(s) checking for rhn repo(s) checking for yum repo(s) starting descent into /var/www/cobbler/ks_mirror/CentOS7-x86_64 for CentOS7-x86_64 processing repo at : /var/www/cobbler/ks_mirror/CentOS7-x86_64 need to process repo/comps: /var/www/cobbler/ks_mirror/CentOS7-x86_64 looking for /var/www/cobbler/ks_mirror/CentOS7-x86_64/repodata/*comps*.xml Keeping repodata as-is :/var/www/cobbler/ks_mirror/CentOS7-x86_64/repodata
创建一台虚拟机,规格:4C2G20G,网卡选择NAT模式。

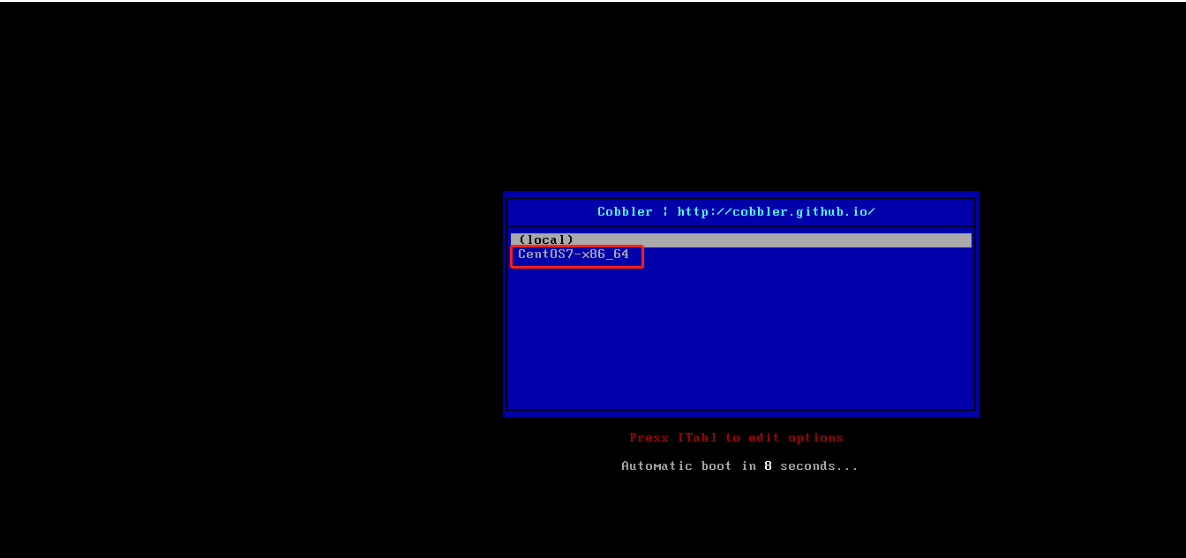
加电开启此虚拟机:
2.3 搭建配置主从DNS服务器,实现区域传送,并实现智能DNS
2.3.1、主从DNS实验拓扑图
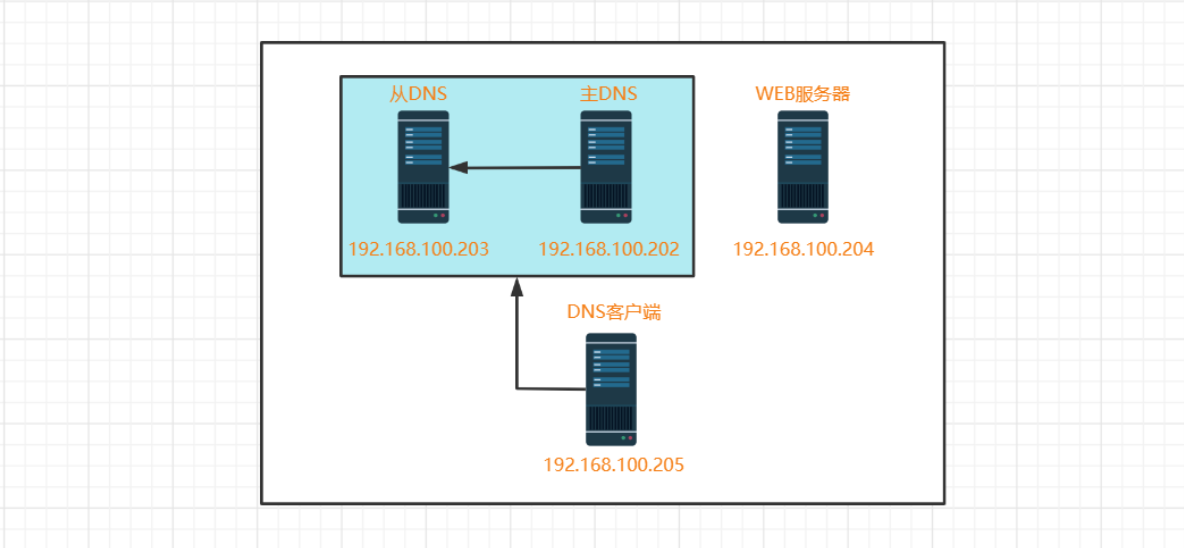
#主从DNS实验步骤 #环境准备 主DNS服务器: 192.168.100.202 从DNS服务器: 192.168.100.203 WEB服务器: 192.168.100.204 DNS客户端: 192.168.100.205 #主DNS服务器安装软件包 [root@dns-master ~]#yum install -y bind bind-utils Installed: bind.x86_64 32:9.11.4-26.P2.el7_9.10 Dependency Installed: audit-libs-python.x86_64 0:2.8.5-4.el7 checkpolicy.x86_64 0:2.5-8.el7 libcgroup.x86_64 0:0.41-21.el7 libsemanage-python.x86_64 0:2.5-14.el7 policycoreutils-python.x86_64 0:2.5-34.el7 python-IPy.noarch 0:0.75-6.el7 python-ply.noarch 0:3.4-11.el7 setools-libs.x86_64 0:3.3.8-4.el7 Updated: bind-utils.x86_64 32:9.11.4-26.P2.el7_9.10 Dependency Updated: bind-libs.x86_64 32:9.11.4-26.P2.el7_9.10 bind-libs-lite.x86_64 32:9.11.4-26.P2.el7_9.10 bind-license.noarch 32:9.11.4-26.P2.el7_9.10 Complete! #主DNS服务器配置 #修改主配置文件(options里面注释如下3行内容,增加只允许从DNS服务器进行区域传送) [root@dns-master ~]#vim /etc/named.conf options { // listen-on port 53 { 127.0.0.1; }; // listen-on-v6 port 53 { ::1; }; // allow-query { localhost; }; allow-transfer { 192.168.100.203; }; }; #定义区域magedu.org vim /etc/named.rfc1912.zones zone "magedu.org" IN { type master; file "magedu.org.zone"; }; #创建DNS区域数据库文件 [root@dns-master ~]#cp -p /var/named/named.localhost /var/named/magedu.org.zone [root@dns-master ~]#ls -l /var/named/ total 20 drwxrwx---. 2 named named 6 Oct 4 15:06 data drwxrwx---. 2 named named 6 Oct 4 15:06 dynamic -rw-r-----. 1 root named 152 Jun 21 2007 magedu.org.zone -rw-r-----. 1 root named 2253 Apr 5 2018 named.ca -rw-r-----. 1 root named 152 Dec 15 2009 named.empty -rw-r-----. 1 root named 152 Jun 21 2007 named.localhost -rw-r-----. 1 root named 168 Dec 15 2009 named.loopback drwxrwx---. 2 named named 6 Oct 4 15:06 slaves #配置DNS区域数据库文件 vim /var/named/magedu.org.zone $TTL 1D @ IN SOA master admin.magedu.org. ( 1 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum NS master NS slave master A 192.168.100.202 salve A 192.168.100.203 www A 192.168.100.204 #备DNS服务器安装软件包 [root@dns-slave ~]#yum install -y bind bind-utils Installed: bind.x86_64 32:9.11.4-26.P2.el7_9.10 Dependency Installed: audit-libs-python.x86_64 0:2.8.5-4.el7 checkpolicy.x86_64 0:2.5-8.el7 libcgroup.x86_64 0:0.41-21.el7 libsemanage-python.x86_64 0:2.5-14.el7 policycoreutils-python.x86_64 0:2.5-34.el7 python-IPy.noarch 0:0.75-6.el7 python-ply.noarch 0:3.4-11.el7 setools-libs.x86_64 0:3.3.8-4.el7 Updated: bind-utils.x86_64 32:9.11.4-26.P2.el7_9.10 Dependency Updated: bind-libs.x86_64 32:9.11.4-26.P2.el7_9.10 bind-libs-lite.x86_64 32:9.11.4-26.P2.el7_9.10 bind-license.noarch 32:9.11.4-26.P2.el7_9.10 Complete! #备DNS服务器配置 #修改主配置文件(options里面注释如下3行内容,增加不允许其他服务器进行区域传送) [root@dns-slave ~]#vim /etc/named.conf options { // listen-on port 53 { 127.0.0.1; }; // listen-on-v6 port 53 { ::1; }; // allow-query { localhost; }; allow-transfer { none; }; }; #定义从区域magedu.org [root@dns-slave ~]#vim /etc/named.rfc1912.zones zone "magedu.org" IN { type slave; masters { 192.168.100.202; }; file "slaves/magedu.org.slave"; }; #检查主从DNS服务器配置文件和数据库文件格式 [root@dns-master ~]#named-checkconf [root@dns-master ~]#named-checkzone magedu.org /var/named/magedu.org.zone zone magedu.org/IN: loaded serial 1 OK [root@dns-slave ~]#named-checkconf #主从DNS服务器启动DNS服务 [root@dns-master ~]#systemctl start named [root@dns-slave ~]#systemctl start named [root@dns-slave ~]#ls -l /var/named/slaves/ total 4 -rw-r--r--. 1 named named 319 Dec 13 17:23 magedu.org.slave #WEB服务安装配置 [root@web-server ~]#yum install -y httpd #配置WEB服务器主页 [root@web-server ~]#echo "<h1>wwww.magedu.org</h1>" > /var/www/html/index.html #启动httpd服务 [root@web-server ~]#systemctl start httpd #dns-client配置和验证 #增加DNS配置 vim /etc/sysconfig/network-scripts/ifcfg-ens33 DNS1=192.168.100.202 DNS2=192.168.100.203 #生效DNS配置 [root@dns-client ~]#nmcli con reload [root@dns-client ~]#nmcli con up ens33 Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/2) [root@dns-client ~]#cat /etc/resolv.conf # Generated by NetworkManager nameserver 192.168.100.202 nameserver 192.168.100.203 #客户端验证DNS解析 [root@dns-client ~]#dig www.magedu.org ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7 <<>> www.magedu.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34278 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.magedu.org. IN A ;; ANSWER SECTION: www.magedu.org. 86400 IN A 192.168.100.204 ;; AUTHORITY SECTION: magedu.org. 86400 IN NS master.magedu.org. magedu.org. 86400 IN NS slave.magedu.org. ;; ADDITIONAL SECTION: master.magedu.org. 86400 IN A 192.168.100.202 slave.magedu.org. 86400 IN A 192.168.100.203 ;; Query time: 0 msec ;; SERVER: 192.168.100.202#53(192.168.100.202) <--------确认主DNS服务器提供了解析服务 ;; WHEN: Tue Dec 13 17:33:22 CST 2022 ;; MSG SIZE rcvd: 132 [root@dns-client ~]#curl www.magedu.org <h1>wwww.magedu.org</h1> #停止主DNS服务 [root@dns-master ~]#systemctl stop named [root@dns-master ~]#systemctl status named ● named.service - Berkeley Internet Name Domain (DNS) Loaded: loaded (/usr/lib/systemd/system/named.service; disabled; vendor preset: disabled) Active: inactive (dead) Dec 13 17:23:28 dns-master named[1768]: client @0x7f4a600b7690 192.168.100.203#41330 (magedu.org): transfer of 'magedu.org/IN': AXFR started (serial 1) Dec 13 17:23:28 dns-master named[1768]: client @0x7f4a600b7690 192.168.100.203#41330 (magedu.org): transfer of 'magedu.org/IN': AXFR ended Dec 13 17:35:01 dns-master systemd[1]: Stopping Berkeley Internet Name Domain (DNS)... Dec 13 17:35:01 dns-master named[1768]: received control channel command 'stop' Dec 13 17:35:01 dns-master named[1768]: shutting down: flushing changes Dec 13 17:35:01 dns-master named[1768]: stopping command channel on 127.0.0.1#953 Dec 13 17:35:01 dns-master named[1768]: stopping command channel on ::1#953 Dec 13 17:35:01 dns-master named[1768]: no longer listening on 127.0.0.1#53 Dec 13 17:35:01 dns-master named[1768]: no longer listening on 192.168.100.202#53 Dec 13 17:35:01 dns-master systemd[1]: Stopped Berkeley Internet Name Domain (DNS). #客户端验证DNS是否可以正常解析 [root@dns-client ~]#dig www.magedu.org ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7 <<>> www.magedu.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44098 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.magedu.org. IN A ;; ANSWER SECTION: www.magedu.org. 86400 IN A 192.168.100.204 ;; AUTHORITY SECTION: magedu.org. 86400 IN NS master.magedu.org. magedu.org. 86400 IN NS slave.magedu.org. ;; ADDITIONAL SECTION: master.magedu.org. 86400 IN A 192.168.100.202 slave.magedu.org. 86400 IN A 192.168.100.203 ;; Query time: 3 msec ;; SERVER: 192.168.100.203#53(192.168.100.203) <--------确认从DNS服务器提供了解析服务 ;; WHEN: Tue Dec 13 17:36:13 CST 2022 ;; MSG SIZE rcvd: 132 [root@dns-client ~]#curl www.magedu.org <h1>wwww.magedu.org</h1>
2.3.2、智能DNS实验拓扑图:
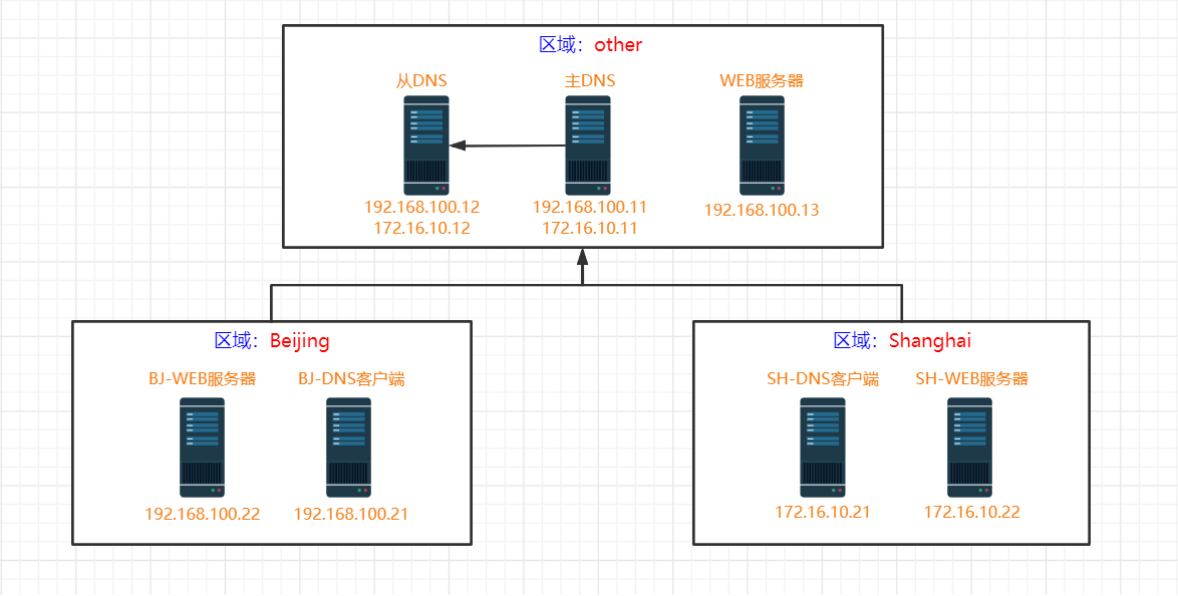
#智能DNS实验步骤 #环境准备共7台服务器 主DNS服务器: 192.168.100.11(172.16.10.11) 从DNS服务器: 192.168.100.12(172.16.10.12) WEB服务器: 192.168.100.13 BJ-DNS客户端: 192.168.100.21 BJ-WEB服务器: 192.168.100.22 SH-DNS客户端: 172.16.10.21 SH-WEB服务器: 172.16.10.22 #主DNS服务器配置 #主DNS修改主配置文件(只允许从DNS服务器进行区域传送,定义ACL网段配置和VIEW配置) [root@dns-master ~]#vim /etc/named.conf acl beijingnet { 192.168.100.0/24; }; acl shanghainet { 172.16.10.0/24; }; acl othernet { any; }; options { // listen-on port 53 { 127.0.0.1; }; // listen-on-v6 port 53 { ::1; }; // allow-query { localhost; }; allow-transfer { 192.168.100.12; }; }; ...(其他配置略) view beijingview { match-clients { beijingnet; }; include "/etc/named.rfc1912.zones.bj"; }; view shanghaiview { match-clients { shanghainet; }; include "/etc/named.rfc1912.zones.sh"; }; view otherview { match-clients { othernet; }; include "/etc/named.rfc1912.zones.other"; }; include "/etc/named.root.key"; #主DNS实现区域配置文件 [root@dns-master ~]#vim /etc/named.rfc1912.zones.bj zone "." IN { type hint; file "named.ca"; }; zone "magedu.org" IN { type master; file "magedu.org.zone.bj"; }; [root@dns-master ~]#vim /etc/named.rfc1912.zones.sh zone "." IN { type hint; file "named.ca"; }; zone "magedu.org" IN { type master; file "magedu.org.zone.sh"; }; [root@dns-master ~]#vim /etc/named.rfc1912.zones.other zone "." IN { type hint; file "named.ca"; }; zone "magedu.org" IN { type master; file "magedu.org.zone.other"; }; #主DNS修改区域配置文件属组和权限 [root@dns-master ~]#chgrp named /etc/named.rfc1912.zones.bj [root@dns-master ~]#chgrp named /etc/named.rfc1912.zones.sh [root@dns-master ~]#chgrp named /etc/named.rfc1912.zones.other [root@dns-master ~]#chmod 640 /etc/named.rfc1912.zones.bj [root@dns-master ~]#chmod 640 /etc/named.rfc1912.zones.sh [root@dns-master ~]#chmod 640 /etc/named.rfc1912.zones.other #主DNS创建区域数据库文件 [root@dns-master ~]#vim /var/named/magedu.org.zone.bj $TTL 1D @ IN SOA master admin.magedu.org. ( 1 ; 1D ; 1H ; 1W ; 3H ) NS master NS slave master A 192.168.100.11 slave A 192.168.100.12 websrv A 192.168.100.22 www CNAME websrv [root@dns-master ~]#vim /var/named/magedu.org.zone.sh $TTL 1D @ IN SOA master admin.magedu.org. ( 1 ; 1D ; 1H ; 1W ; 3H ) NS master NS slave master A 192.168.100.11 slave A 192.168.100.12 websrv A 172.16.10.22 www CNAME websrv [root@dns-master ~]#vim /var/named/magedu.org.zone.other $TTL 1D @ IN SOA master admin.magedu.org. ( 1 ; 1D ; 1H ; 1W ; 3H ) NS master NS slave master A 192.168.100.11 slave A 192.168.100.12 websrv A 192.168.100.13 www CNAME websrv #主DNS修改区域数据库文件属组和权限 [root@dns-master ~]#chgrp named /var/named/magedu.org.zone.bj [root@dns-master ~]#chgrp named /var/named/magedu.org.zone.sh [root@dns-master ~]#chgrp named /var/named/magedu.org.zone.other [root@dns-master ~]#chmod 640 /var/named/magedu.org.zone.bj [root@dns-master ~]#chmod 640 /var/named/magedu.org.zone.sh [root@dns-master ~]#chmod 640 /var/named/magedu.org.zone.other #从DNS配置 #从DNS修改主配置文件(不允许其他服务器进行区域传送,定义ACL网段配置和VIEW配置) [root@dns-slave ~]#vim /etc/named.conf acl beijingnet { 192.168.100.0/24; }; acl shanghainet { 172.16.10.0/24; }; acl othernet { any; }; options { // listen-on port 53 { 127.0.0.1; }; // listen-on-v6 port 53 { ::1; }; // allow-query { localhost; }; allow-transfer { none; }; }; view beijingview { match-clients { beijingnet; }; include "/etc/named.rfc1912.zones.bj"; }; view shanghaiview { match-clients { shanghainet; }; include "/etc/named.rfc1912.zones.sh"; }; view otherview { match-clients { othernet; }; include "/etc/named.rfc1912.zones.other"; }; include "/etc/named.root.key"; #从DNS实现区域配置文件 [root@dns-slave ~]#vim /etc/named.rfc1912.zones.bj zone "." IN { type hint; file "named.ca"; }; zone "magedu.org" IN { type slave; masters { 192.168.100.11; }; file "slaves/magedu.org.zone.bj.slave"; }; [root@dns-slave ~]#vim /etc/named.rfc1912.zones.sh zone "." IN { type hint; file "named.ca"; }; zone "magedu.org" IN { type slave; masters { 192.168.100.11; }; file "slaves/magedu.org.zone.sh.slave"; }; [root@dns-slave ~]#vim /etc/named.rfc1912.zones.other zone "." IN { type hint; file "named.ca"; }; zone "magedu.org" IN { type slave; masters { 192.168.100.11; }; file "slaves/magedu.org.zone.other.slave"; }; #从DNS修改区域配置文件属组和权限 [root@dns-slave ~]#chgrp named /etc/named.rfc1912.zones.bj [root@dns-slave ~]#chgrp named /etc/named.rfc1912.zones.sh [root@dns-slave ~]#chgrp named /etc/named.rfc1912.zones.other [root@dns-slave ~]#chmod 640 /etc/named.rfc1912.zones.bj [root@dns-slave ~]#chmod 640 /etc/named.rfc1912.zones.sh [root@dns-slave ~]#chmod 640 /etc/named.rfc1912.zones.other #主从DNS服务器启动服务 [root@dns-master ~]#named-checkconf [root@dns-master ~]#systemctl start named [root@dns-slave ~]#named-checkconf [root@dns-slave ~]#systemctl start named #WEB服务器配置 [root@web-server ~]#echo "www.magedu.org in Other" > /var/www/html/index.html [root@web-server ~]#systemctl start httpd [root@bj-web-server ~]#echo "www.magedu.org in Beijing" > /var/www/html/index.html [root@bj-web-server ~]#systemctl start httpd [root@sh-web-server ~]#echo "www.magedu.org in Shanghai" > /var/www/html/index.html [root@sh-web-server ~]#systemctl start httpd #DNS客户端测试 [root@bj-dns-client ~]#cat /etc/resolv.conf # Generated by NetworkManager nameserver 192.168.100.11 nameserver 192.168.100.12 [root@bj-dns-client ~]#curl www.magedu.org www.magedu.org in Beijing [root@sh-dns-client ~]#cat /etc/resolv.conf # Generated by NetworkManager nameserver 172.16.10.11 nameserver 172.16.10.12 [root@sh-dns-client ~]#curl www.magedu.org www.magedu.org in Shanghai [root@dns-master ~]#cat /etc/resolv.conf # Generated by NetworkManager nameserver 127.0.0.1 [root@dns-master ~]#curl www.magedu.org www.magedu.org in Other #DNS主从测试 #DNS客户端测试域名解析 [root@bj-dns-client ~]#dig www.magedu.org ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7 <<>> www.magedu.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 51517 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.magedu.org. IN A ;; ANSWER SECTION: www.magedu.org. 86400 IN CNAME websrv.magedu.org. websrv.magedu.org. 86400 IN A 192.168.100.22 ;; AUTHORITY SECTION: magedu.org. 86400 IN NS master.magedu.org. magedu.org. 86400 IN NS slave.magedu.org. ;; ADDITIONAL SECTION: master.magedu.org. 86400 IN A 192.168.100.11 slave.magedu.org. 86400 IN A 192.168.100.12 ;; Query time: 0 msec ;; SERVER: 192.168.100.11#53(192.168.100.11) <--------确认主DNS服务器提供了解析服务 ;; WHEN: Mon Dec 19 13:02:51 CST 2022 ;; MSG SIZE rcvd: 153 #停止主DNS服务 [root@dns-master ~]#systemctl stop named #DNS客户端测试域名解析 [root@bj-dns-client ~]#dig www.magedu.org ; <<>> DiG 9.11.4-P2-RedHat-9.11.4-26.P2.el7 <<>> www.magedu.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52745 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 3 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.magedu.org. IN A ;; ANSWER SECTION: www.magedu.org. 86400 IN CNAME websrv.magedu.org. websrv.magedu.org. 86400 IN A 192.168.100.22 ;; AUTHORITY SECTION: magedu.org. 86400 IN NS slave.magedu.org. magedu.org. 86400 IN NS master.magedu.org. ;; ADDITIONAL SECTION: master.magedu.org. 86400 IN A 192.168.100.11 slave.magedu.org. 86400 IN A 192.168.100.12 ;; Query time: 0 msec ;; SERVER: 192.168.100.12#53(192.168.100.12) <--------确认从DNS服务器提供了解析服务 ;; WHEN: Mon Dec 19 13:03:14 CST 2022 ;; MSG SIZE rcvd: 153
2.4 iptables配置
2.4.1 配置iptables 打开常用端口加固linux
#加固WEB服务器 #INPUT放通本地回环lo所有流量,放通icmp,只对运维堡垒机放通ssh,只对172.16.10.0/24放通http服务,最后一条拒绝策略。 [root@web-server ~]#iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT [root@web-server ~]#iptables -A INPUT -i lo -j ACCEPT [root@web-server ~]#iptables -A INPUT -p icmp -m icmp --icmp-type 8 -j ACCEPT [root@web-server ~]#iptables -A INPUT -p icmp -m icmp --icmp-type 11 -j ACCEPT [root@web-server ~]#iptables -A INPUT -s 172.16.10.1 -p tcp --dport 22 -j ACCEPT [root@web-server ~]#iptables -A INPUT -s 172.16.10.0/24 -p tcp --dport 80 -j ACCEPT [root@web-server ~]#iptables -A INPUT -j REJECT #OUTPUT放通到本地DNS的访问请求,其他udp请求拒绝。 [root@web-server ~]#iptables -A OUTPUT -p udp --dport 53 -m iprange --dst-range 172.16.10.11-172.16.10.12 -j ACCEPT [root@web-server ~]#iptables -A OUTPUT -p udp -j REJECT [root@web-server ~]#iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 52 4960 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 11 0 0 ACCEPT tcp -- * * 172.16.10.1 0.0.0.0/0 tcp dpt:22 0 0 ACCEPT tcp -- * * 172.16.10.0/24 0.0.0.0/0 tcp dpt:80 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 16 packets, 2272 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 destination IP range 172.16.10.11-172.16.10.12 0 0 REJECT udp -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable #客户端测试 [root@web-client ~]#ping -c 4 172.16.10.22 PING 172.16.10.22 (172.16.10.22) 56(84) bytes of data. 64 bytes from 172.16.10.22: icmp_seq=1 ttl=64 time=0.306 ms 64 bytes from 172.16.10.22: icmp_seq=2 ttl=64 time=0.220 ms 64 bytes from 172.16.10.22: icmp_seq=3 ttl=64 time=0.313 ms 64 bytes from 172.16.10.22: icmp_seq=4 ttl=64 time=0.308 ms --- 172.16.10.22 ping statistics --- 4 packets transmitted, 4 received, 0% packet loss, time 3001ms rtt min/avg/max/mdev = 0.220/0.286/0.313/0.043 ms [root@web-client ~]#curl 172.16.10.22 Welcome to magedu [root@web-client ~]#ssh 172.16.10.22 ssh: connect to host 172.16.10.22 port 22: Connection refused
2.4.2 使用iptables DNAT完成暴露内网端口; 使用SNAT,让内网可以上网; 并抓包分析过程;
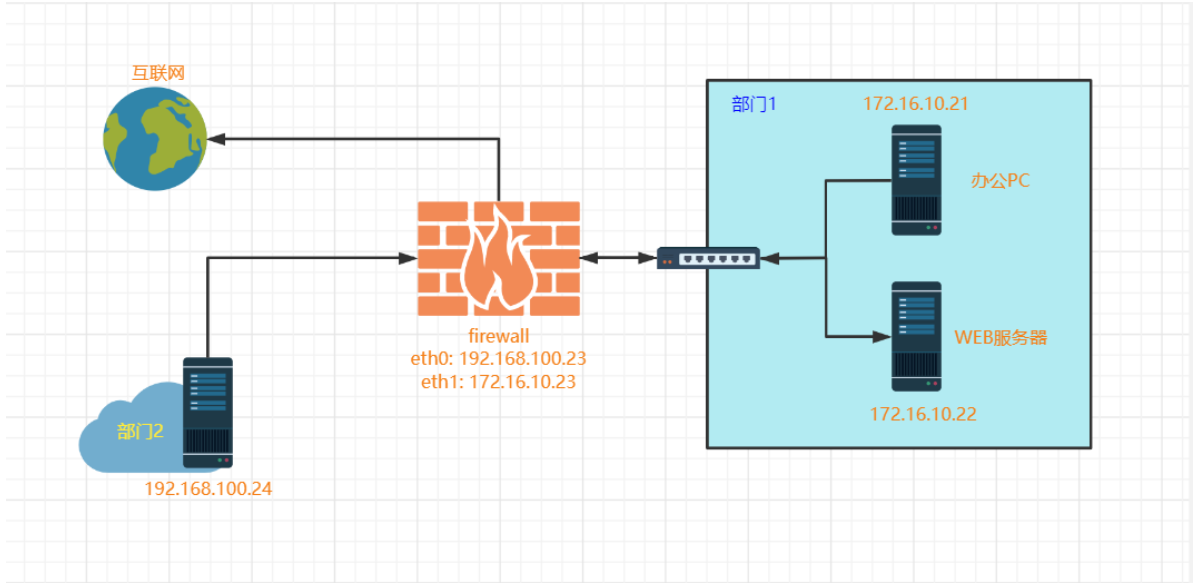
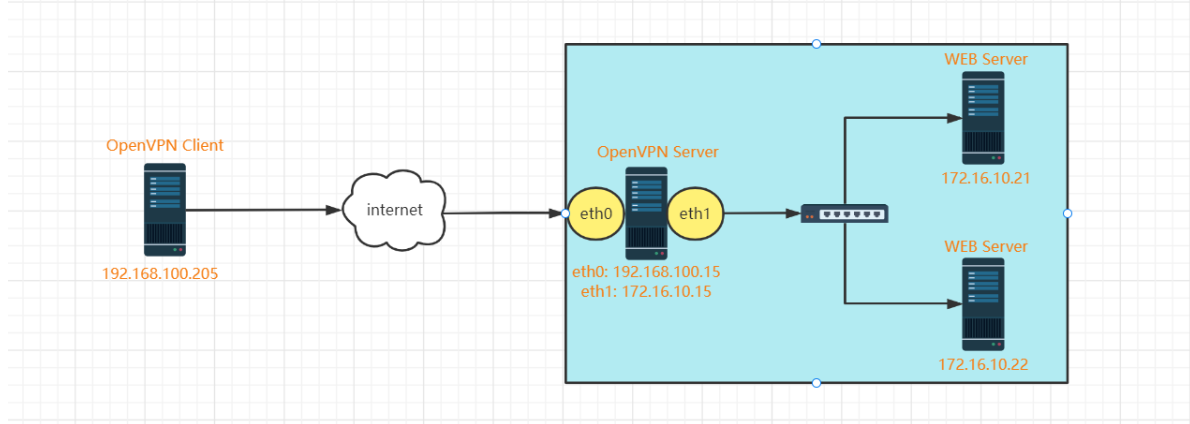
#环境准备4台服务器 部门1-office-pc: 172.16.10.21 部门1-WEB服务器: 172.16.10.22 边界防火墙: 192.168.100.23(172.16.10.23) 部门2-测试PC: 192.168.100.24 #业务需求: (1)部门1的办公PC(172.16.10.21)需要访问互联网; (2)部门2的测试PC(192.168.100.24)需要访问部门1的WEB服务器(172.16.10.22:8080); #部门1办公PC默认网关配置 [root@office-pc ~]#vim /etc/sysconfig/network-scripts/ifcfg-ens33 GATEWAY=172.16.10.23 [root@office-pc ~]#systemctl restart network [root@office-pc ~]#route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 172.16.10.23 0.0.0.0 UG 100 0 0 ens33 172.16.10.0 0.0.0.0 255.255.255.0 U 100 0 0 ens33 [root@office-pc ~]#ping -c 4 114.114.114.114 PING 114.114.114.114 (114.114.114.114) 56(84) bytes of data. --- 114.114.114.114 ping statistics --- 4 packets transmitted, 0 received, 100% packet loss, time 2999ms #防火墙开启forward转发 [root@firewall ~]#vi /etc/sysctl.conf net.ipv4.ip_forward = 1 [root@firewall ~]#sysctl -p net.ipv4.ip_forward = 1 #防火墙配置SNAT规则 [root@firewall ~]#iptables -t nat -A POSTROUTING -s 172.16.10.21/32 -j SNAT --to-source 172.16.10.23 [root@firewall ~]#iptables -nvL -t nat Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 SNAT all -- * * 172.16.10.21 0.0.0.0/0 to:172.16.10.23 #办公PC测试访问互联网 [root@office-pc ~]#ping -c 4 114.114.114.114 PING 114.114.114.114 (114.114.114.114) 56(84) bytes of data. 64 bytes from 114.114.114.114: icmp_seq=1 ttl=127 time=32.3 ms 64 bytes from 114.114.114.114: icmp_seq=2 ttl=127 time=30.0 ms 64 bytes from 114.114.114.114: icmp_seq=3 ttl=127 time=30.4 ms 64 bytes from 114.114.114.114: icmp_seq=4 ttl=127 time=30.1 ms --- 114.114.114.114 ping statistics --- 4 packets transmitted, 4 received, 0% packet loss, time 3005ms rtt min/avg/max/mdev = 30.033/30.742/32.364/0.961 ms #WEB服务器测试访问互联网 [root@web-server ~]#ping -c 4 114.114.114.114 PING 114.114.114.114 (114.114.114.114) 56(84) bytes of data. From 172.16.10.22 icmp_seq=1 Destination Host Unreachable From 172.16.10.22 icmp_seq=2 Destination Host Unreachable From 172.16.10.22 icmp_seq=3 Destination Host Unreachable From 172.16.10.22 icmp_seq=4 Destination Host Unreachable --- 114.114.114.114 ping statistics --- 4 packets transmitted, 0 received, +4 errors, 100% packet loss, time 3000ms pipe 4 #部门2测试服务器默认网关配置 [root@office2-test ~]#vim /etc/sysconfig/network-scripts/ifcfg-ens33 GATEWAY=192.168.100.23 [root@office2-test ~]#systemctl restart network [root@office2-test ~]#route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 192.168.100.23 0.0.0.0 UG 100 0 0 ens33 192.168.100.0 0.0.0.0 255.255.255.0 U 100 0 0 ens33 [root@office2-test ~]#curl 192.168.100.23:8080 curl: (7) Failed connect to 192.168.100.23:8080; Connection refused #防火墙配置DNAT规则 [root@firewall ~]#iptables -t nat -A PREROUTING -d 192.168.100.23 -p tcp --dport 8080 -j DNAT --to-destination 172.16.10.22:8080 [root@firewall ~]#iptables -t nat -nvL PREROUTING Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 9 540 DNAT tcp -- * * 0.0.0.0/0 192.168.100.23 tcp dpt:8080 to:172.16.10.22:8080 #部门2测试服务器 [root@office2-test ~]#curl 192.168.100.23:8080 Welcome to magedu
SNAT抓包分析
(1)办公PC 172.16.10.21 ping 114.114.114.114,VMnet1抓包如下:
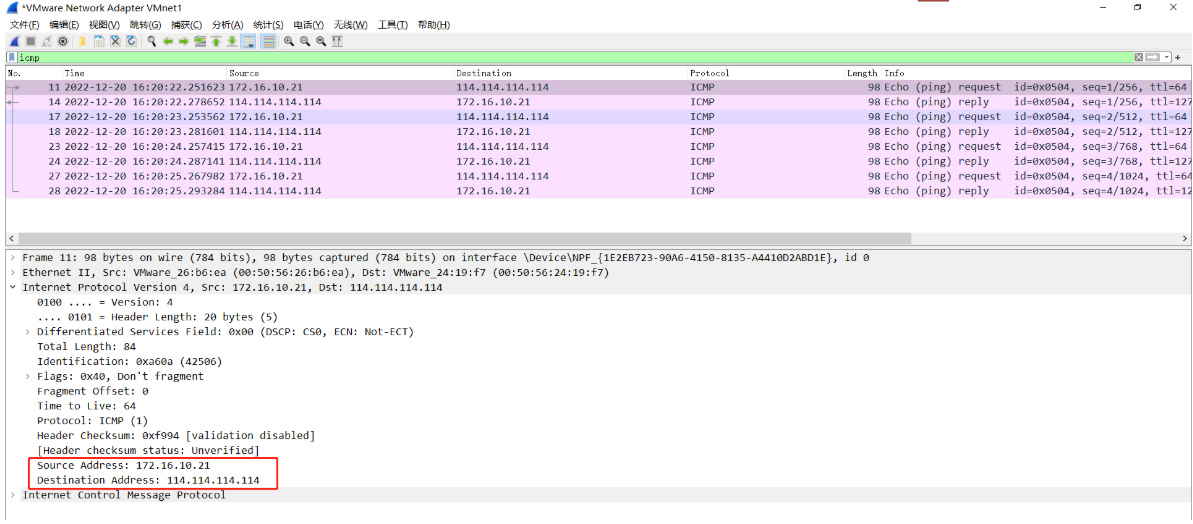
(2)经过防火墙SNAT处理后,源IP地址172.16.10.21变为172.16.10.23,VMnet8抓包如下:
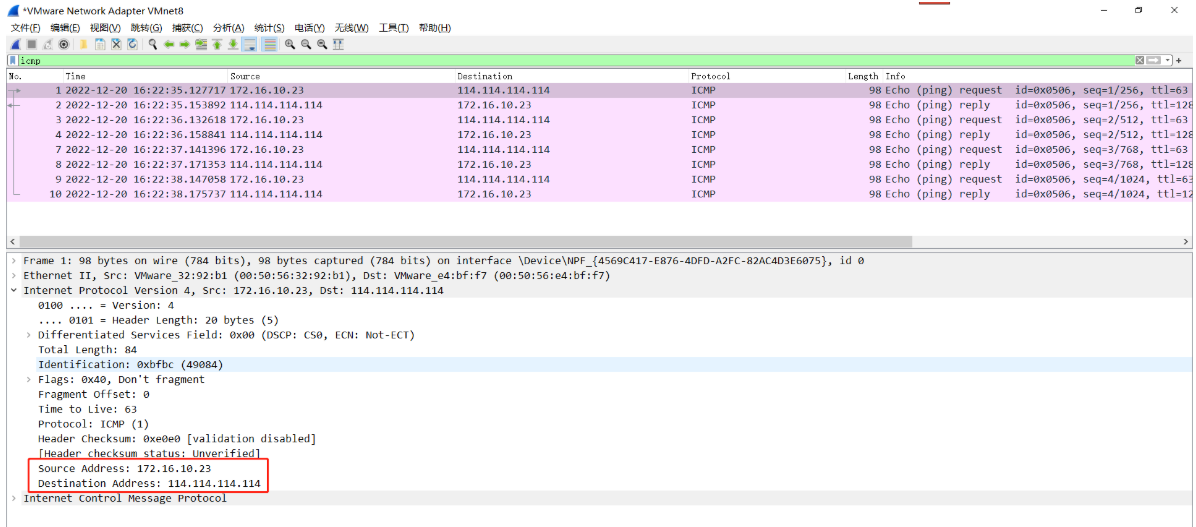
DNAT抓包分析:
(1)测试服务器 192.168.100.24 http访问 192.168.100.23,VMnet8抓包如下:
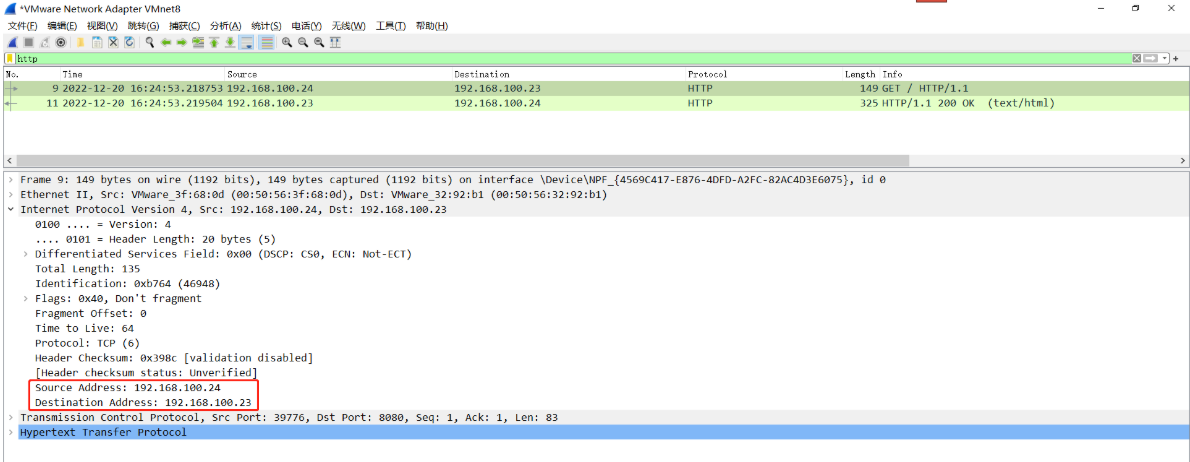
(2)经过防火墙DNAT处理后,目标IP地址192.168.100.23转换成172.16.0.22,VMnet1抓包如下:
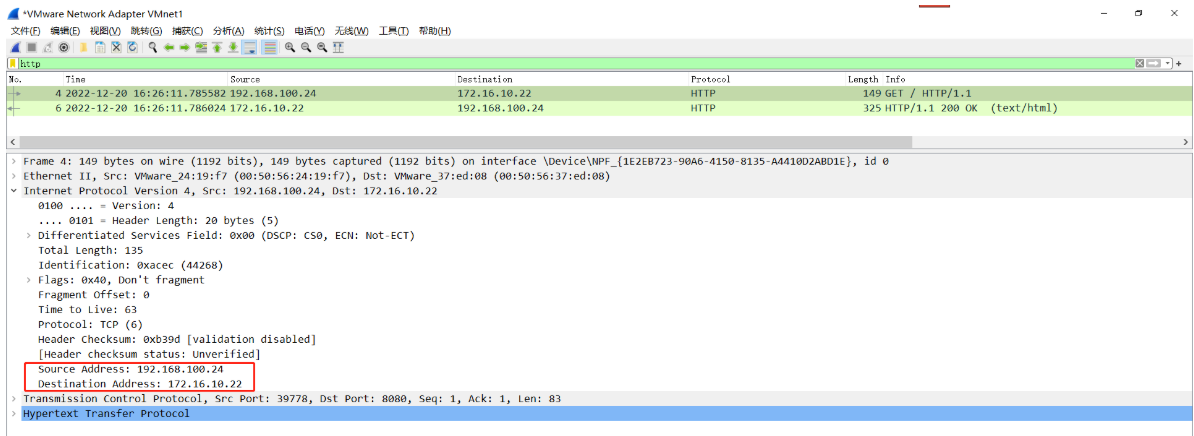
2.5.1 安装OpenVPN Server
#rocky8.6执行一键安装openvpn [root@rocky8 ~]#./install_openvpn.sh magedu01 01-starting install openvpn software Rocky Linux 8 - AppStream 17 kB/s | 4.8 kB 00:00 Rocky Linux 8 - AppStream 1.1 MB/s | 8.7 MB 00:07 Rocky Linux 8 - BaseOS 39 kB/s | 4.3 kB 00:00 Rocky Linux 8 - BaseOS 1.3 MB/s | 2.7 MB 00:02 Rocky Linux 8 - Extras 18 kB/s | 3.5 kB 00:00 Rocky Linux 8 - Extras 33 kB/s | 12 kB 00:00 Extra Packages for Enterprise Linux 8 - x86_64 14 kB/s | 5.3 kB 00:00 Extra Packages for Enterprise Linux 8 - x86_64 1.3 MB/s | 13 MB 00:09 Extra Packages for Enterprise Linux 8 - Next - x86_64 5.8 kB/s | 9.1 kB 00:01 Dependencies resolved. ====================================================================================================================================== Package Architecture Version Repository Size ====================================================================================================================================== Installing: openvpn x86_64 2.4.12-1.el8 epel 545 k Installing dependencies: pkcs11-helper x86_64 1.22-7.el8 epel 64 k Transaction Summary ====================================================================================================================================== Install 2 Packages Total download size: 609 k Installed size: 1.4 M Downloading Packages: (1/2): pkcs11-helper-1.22-7.el8.x86_64.rpm 165 kB/s | 64 kB 00:00 (2/2): openvpn-2.4.12-1.el8.x86_64.rpm 1.1 MB/s | 545 kB 00:00 -------------------------------------------------------------------------------------------------------------------------------------- Total 190 kB/s | 609 kB 00:03 Running transaction check Transaction check succeeded. Running transaction test Transaction test succeeded. Running transaction Preparing : 1/1 Installing : pkcs11-helper-1.22-7.el8.x86_64 1/2 Running scriptlet: openvpn-2.4.12-1.el8.x86_64 2/2 Installing : openvpn-2.4.12-1.el8.x86_64 2/2 Running scriptlet: openvpn-2.4.12-1.el8.x86_64 2/2 Verifying : openvpn-2.4.12-1.el8.x86_64 1/2 Verifying : pkcs11-helper-1.22-7.el8.x86_64 2/2 Installed: openvpn-2.4.12-1.el8.x86_64 pkcs11-helper-1.22-7.el8.x86_64 Complete! Last metadata expiration check: 0:00:09 ago on Tue 20 Dec 2022 12:42:29 PM CST. Dependencies resolved. ====================================================================================================================================== Package Architecture Version Repository Size ====================================================================================================================================== Installing: easy-rsa noarch 3.0.8-1.el8 epel 47 k Transaction Summary ====================================================================================================================================== Install 1 Package Total download size: 47 k Installed size: 120 k Downloading Packages: easy-rsa-3.0.8-1.el8.noarch.rpm 105 kB/s | 47 kB 00:00 -------------------------------------------------------------------------------------------------------------------------------------- Total 37 kB/s | 47 kB 00:01 Running transaction check Transaction check succeeded. Running transaction test Transaction test succeeded. Running transaction Preparing : 1/1 Installing : easy-rsa-3.0.8-1.el8.noarch 1/1 Verifying : easy-rsa-3.0.8-1.el8.noarch 1/1 Installed: easy-rsa-3.0.8-1.el8.noarch Complete! openvpn software install success! Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: /etc/openvpn/easy-rsa-server/3/pki Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 Generating RSA private key, 2048 bit long modulus (2 primes) ..................................+++++ .......+++++ e is 65537 (0x010001) You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [Easy-RSA CA]: CA creation complete and you may now import and sign cert requests. Your new CA certificate file for publishing is at: /etc/openvpn/easy-rsa-server/3/pki/ca.crt Certificate: Data: Version: 3 (0x2) Serial Number: 77:36:d5:2f:09:22:2c:fd:bc:6a:81:71:0b:94:da:98:b3:70:c1:e3 Signature Algorithm: sha256WithRSAEncryption Issuer: CN = Easy-RSA CA Validity Not Before: Dec 20 04:42:40 2022 GMT Not After : Dec 17 04:42:40 2032 GMT Subject: CN = Easy-RSA CA Subject Public Key Info: Public Key Algorithm: rsaEncryption RSA Public-Key: (2048 bit) Modulus: 00:c2:eb:8c:da:51:dd:00:48:df:6c:83:90:21:ea: 63:d5:51:6b:d5:12:7a:5e:ba:33:00:dc:36:6e:f0: c3:70:49:80:9e:03:93:cc:1c:bd:dc:82:82:6f:9e: 13:76:29:00:7b:44:3c:a5:01:96:fe:f7:49:8d:3c: d3:89:68:11:b0:be:ab:1c:a2:d0:3f:77:6b:6a:17: be:e5:e3:21:17:de:0d:fb:00:83:4d:1f:21:a9:e8: ef:f9:a5:ee:89:f3:81:1c:b5:db:1b:5e:5e:ce:78: ce:02:8f:ab:f2:1b:d0:fe:0a:81:ea:39:3a:df:c5: c6:0c:9f:f6:80:b9:80:d8:39:30:07:8b:16:97:e2: d9:5e:61:3e:73:8e:c7:90:1f:96:95:d2:3f:f1:c8: 94:67:29:c3:96:e0:ac:b8:38:b8:ce:e9:20:06:ab: 2a:3a:40:f7:f1:37:e3:89:6d:77:29:8c:40:2d:f5: c7:4a:58:1b:0f:6f:4f:70:e6:3b:ab:1f:48:f1:dc: 54:84:4c:94:0f:4c:30:ce:27:fe:dd:b8:41:d5:36: 1e:47:2f:d4:92:33:67:71:69:e3:85:a3:5a:94:f2: ca:5d:85:dd:c8:49:d3:d4:5b:e6:1c:bf:34:d7:a9: d3:aa:05:3c:c4:a5:cb:88:ce:a2:84:3f:88:ec:f5: af:77 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: 01:64:0D:66:5F:43:D3:92:95:CB:AA:2F:C0:6E:A0:85:92:99:A4:60 X509v3 Authority Key Identifier: keyid:01:64:0D:66:5F:43:D3:92:95:CB:AA:2F:C0:6E:A0:85:92:99:A4:60 DirName:/CN=Easy-RSA CA serial:77:36:D5:2F:09:22:2C:FD:BC:6A:81:71:0B:94:DA:98:B3:70:C1:E3 X509v3 Basic Constraints: CA:TRUE X509v3 Key Usage: Certificate Sign, CRL Sign Signature Algorithm: sha256WithRSAEncryption 58:b0:21:06:1f:ff:6c:0a:94:ff:e4:d7:f9:07:2d:ae:00:57: b6:ae:42:80:73:61:da:6e:05:6e:01:f4:a0:b6:74:2b:cf:7c: a4:0f:c8:6d:2f:9c:76:09:71:15:1e:8c:22:a5:1d:15:d4:3b: 66:b2:15:35:e6:34:79:24:40:fd:b7:31:cb:e8:5c:3e:11:34: 28:ca:19:a0:d4:15:46:dc:ff:d4:67:d9:0d:36:76:9e:c7:28: db:0a:cf:18:e2:53:70:4d:86:30:68:8f:d8:d1:df:5e:b4:27: 9e:48:3c:29:48:6d:47:e0:b1:cf:60:36:19:e1:c4:ed:11:87: 80:08:9b:63:e0:b5:c0:e4:2f:91:65:fc:f3:79:a2:44:f8:d9: 18:a4:52:79:ab:6c:37:a1:e7:85:41:da:6b:f0:73:eb:25:ba: 43:38:c8:f9:5a:db:81:84:a5:98:ab:71:86:62:95:7a:e5:db: b1:22:a5:89:93:81:fc:bd:1e:fc:62:31:68:3f:08:f9:39:30: 9d:25:13:17:ef:3b:16:53:a8:d0:01:da:20:c5:f6:3a:8e:7d: 99:c2:1f:5d:5a:f7:86:00:fc:c9:ca:f0:35:ef:b6:cc:2c:a3: 83:c8:b5:05:8f:f5:28:e2:18:d1:86:54:85:d8:07:ee:95:a0: 39:5f:89:86 Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 Generating a RSA private key ...+++++ ....................................................................................................................................................................................+++++ writing new private key to '/etc/openvpn/easy-rsa-server/3/pki/easy-rsa-1403.hRU0PW/tmp.m4w5I7' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [server]: Keypair and certificate request completed. Your files are: req: /etc/openvpn/easy-rsa-server/3/pki/reqs/server.req key: /etc/openvpn/easy-rsa-server/3/pki/private/server.key Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a server certificate for 825 days: subject= commonName = server Type the word 'yes' to continue, or any other input to abort. Confirm request details: Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-1432.Cxgj3d/tmp.ERYPlt Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'server' Certificate is to be certified until Mar 24 04:42:41 2025 GMT (825 days) Write out database with 1 new entries Data Base Updated Certificate created at: /etc/openvpn/easy-rsa-server/3/pki/issued/server.crt Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 Generating DH parameters, 2048 bit long safe prime, generator 2 This is going to take a long time .........................+..............................................................................................................................................+...............................+....................................................+.............................................................................................................................+................................................+........................................................................................................................................+.............................................+...............................+......................................................+.............................................................................................................................................++*++*++*++* DH parameters of size 2048 created at /etc/openvpn/easy-rsa-server/3/pki/dh.pem init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: /etc/openvpn/easy-rsa-client/3/pki Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 Generating a RSA private key ..................................................................................................................................+++++ ..+++++ writing new private key to '/etc/openvpn/easy-rsa-client/3/pki/easy-rsa-1543.uGJ4vx/tmp.QYVKPj' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [magedu01]: Keypair and certificate request completed. Your files are: req: /etc/openvpn/easy-rsa-client/3/pki/reqs/magedu01.req key: /etc/openvpn/easy-rsa-client/3/pki/private/magedu01.key Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 The request has been successfully imported with a short name of: magedu01 You may now use this name to perform signing operations on this request. Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a client certificate for 825 days: subject= commonName = magedu01 Type the word 'yes' to continue, or any other input to abort. Confirm request details: Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-1592.OiTEJB/tmp.Aa66iK Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'magedu01' Certificate is to be certified until Mar 24 04:43:48 2025 GMT (825 days) Write out database with 1 new entries Data Base Updated Certificate created at: /etc/openvpn/easy-rsa-server/3/pki/issued/magedu01.crt openvpn:x:991:987:OpenVPN:/etc/openvpn:/sbin/nologin Created symlink /etc/systemd/system/multi-user.target.wants/openvpn@server.service → /usr/lib/systemd/system/openvpn@.service. ● openvpn@server.service - OpenVPN Robust And Highly Flexible Tunneling Application On server Loaded: loaded (/usr/lib/systemd/system/openvpn@.service; enabled; vendor preset: disabled) Active: active (running) since Tue 2022-12-20 12:43:49 CST; 24ms ago Main PID: 1722 (openvpn) Status: "Pre-connection initialization successful" Tasks: 1 (limit: 24384) Memory: 1.2M CGroup: /system.slice/system-openvpn.slice/openvpn@server.service └─1722 /usr/sbin/openvpn --cd /etc/openvpn/ --config server.conf Dec 20 12:43:49 rocky8.6 systemd[1]: Starting OpenVPN Robust And Highly Flexible Tunneling Application On server... Dec 20 12:43:49 rocky8.6 systemd[1]: Started OpenVPN Robust And Highly Flexible Tunneling Application On server. [root@rocky8 ~]# #查看客户端用户配置文件 [root@rocky8 ~]#cd /etc/openvpn/client/ [root@rocky8 client]#ll total 0 drwxr-xr-x 2 root root 79 Dec 20 12:43 magedu01 [root@rocky8 client]#cd magedu01/ [root@rocky8 magedu01]#ll total 20 -rw------- 1 root root 1204 Dec 20 12:43 ca.crt -rw-r--r-- 1 root root 236 Dec 20 12:43 client.ovpn -rw------- 1 root root 4494 Dec 20 12:43 magedu01.crt -rw------- 1 root root 1704 Dec 20 12:43 magedu01.key [root@rocky8 magedu01]# #打包下载客户端用户配置文件 [root@rocky8 magedu01]#tar cvf magedu01.tar ca.crt client.ovpn magedu01.crt magedu01.key ca.crt client.ovpn magedu01.crt magedu01.key
#将magedu01.tar解压后的文件上传至windows OpenVPN客户端的默认安装目录:C:\Program Files\OpenVPN\config
在OpenVPN客户端软件上发起连接:
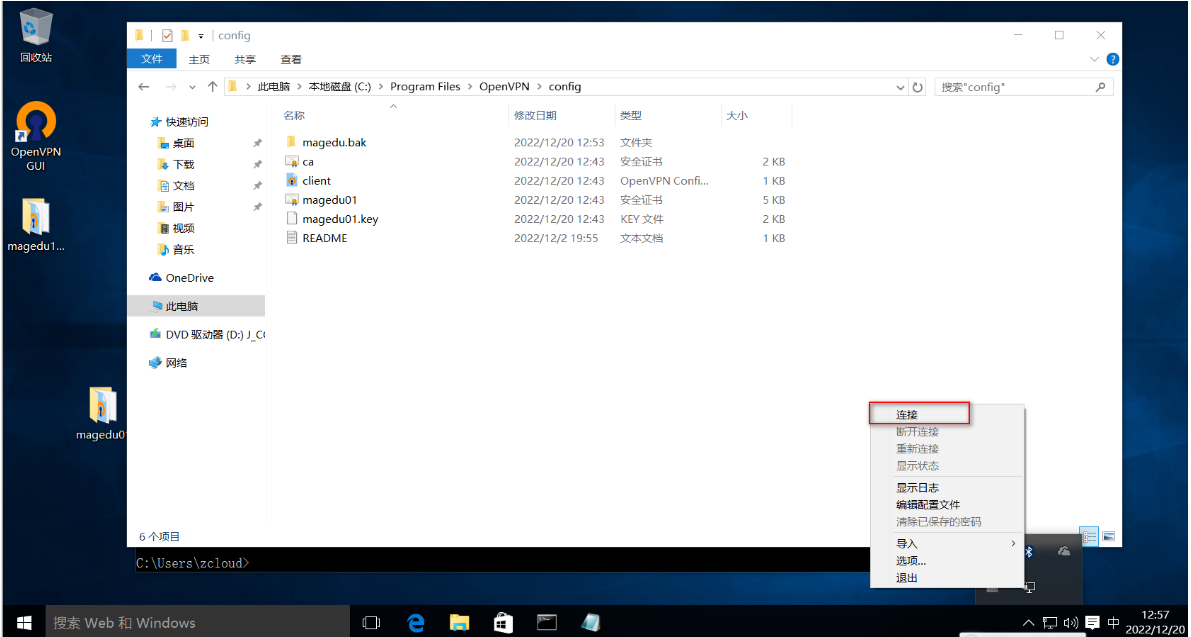
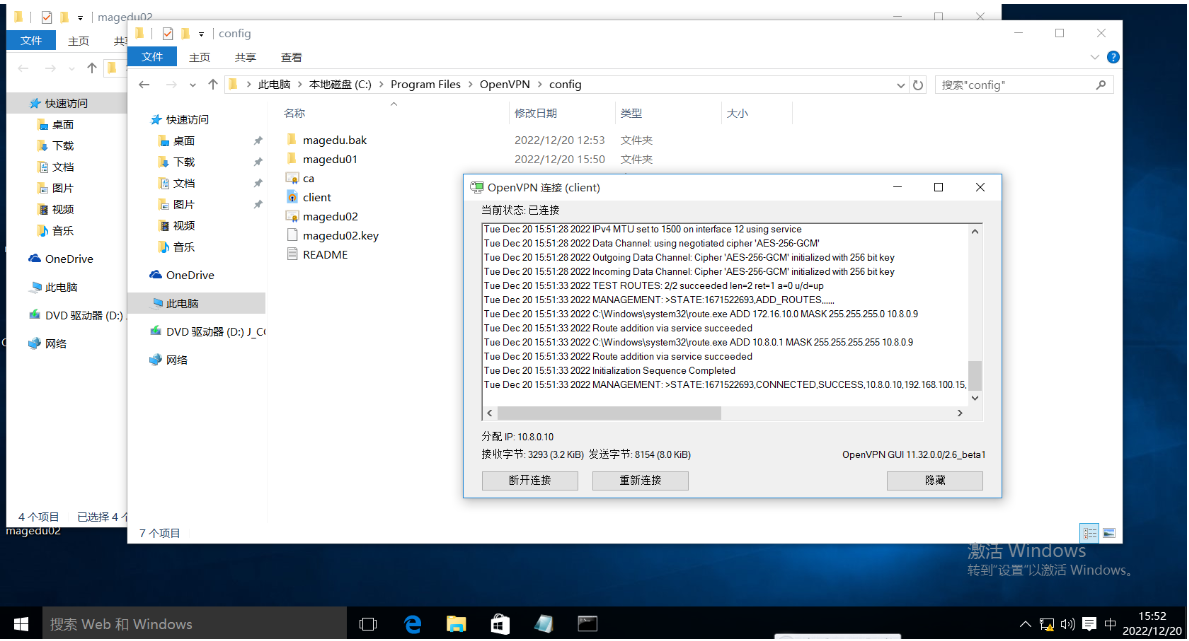
提示连接成功,分配了10.8.0.6的IP地址。
WEB服务器172.16.0.22配置路由:
[root@sh-web-server ~]#echo "<h1>Welcom to magedu</h1>" > /var/www/html/index.html [root@sh-web-server ~]#route add -net 10.8.0.0/24 gw 172.16.10.15 [root@sh-web-server ~]#route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 10.8.0.0 172.16.10.15 255.255.255.0 UG 0 0 0 ens33 172.16.10.0 0.0.0.0 255.255.255.0 U 100 0 0 ens33
OpenVPN Server配置SNAT转发:
[root@rocky8 magedu01]#echo net.ipv4.ip_forward = 1 >> /etc/sysctl.conf [root@rocky8 magedu01]#sysctl -p net.ipv4.ip_forward = 1 [root@rocky8 magedu01]#iptables -t nat -A POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to-source 172.16.10.15 [root@rocky8 magedu01]#iptables -nvL -t nat Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 11 612 SNAT all -- * * 10.8.0.0/24 !10.8.0.0/24 to:172.16.10.15 Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
OpenVPN Client测试访问172.16.0.22的WEB服务器:
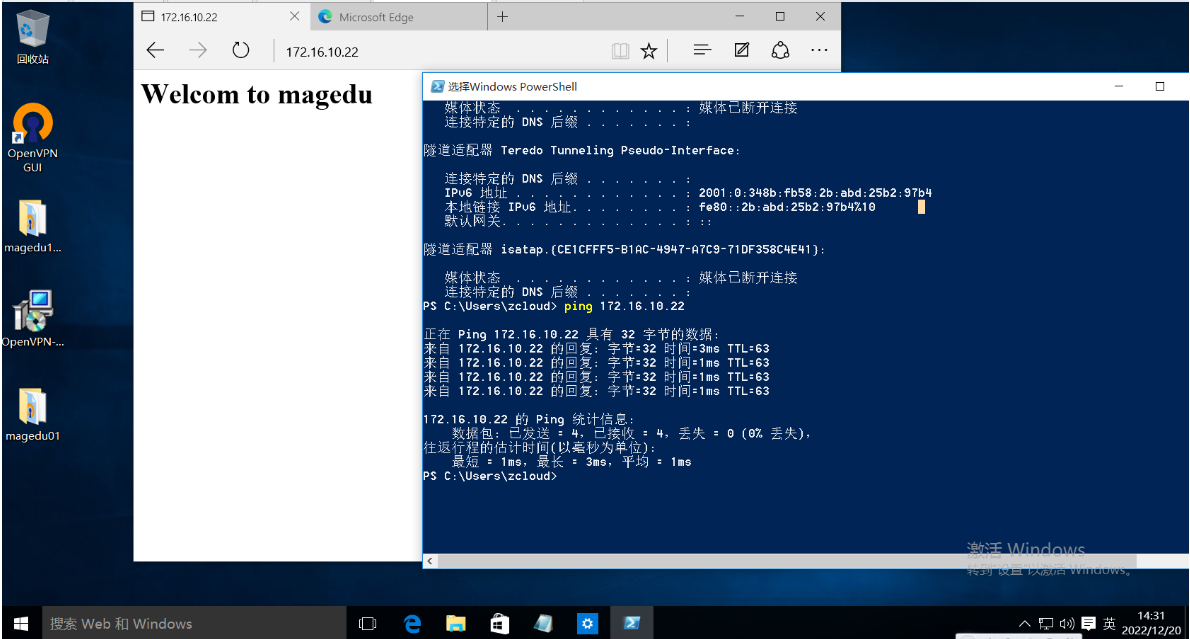
2.5.2 新增OpenVPN客户端用户
#新增OpenVPN客户端用户 [root@rocky8 ~]#./create_vpnuser.sh 请输入需要创建的OpenVPN客户端用户名:magedu02 Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 Generating a RSA private key ......................................+++++ .......................................+++++ writing new private key to '/etc/openvpn/easy-rsa-client/3/pki/easy-rsa-2129.yCGbhp/tmp.KoVUxR' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [magedu02]: Keypair and certificate request completed. Your files are: req: /etc/openvpn/easy-rsa-client/3/pki/reqs/magedu02.req key: /etc/openvpn/easy-rsa-client/3/pki/private/magedu02.key Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 The request has been successfully imported with a short name of: magedu02 You may now use this name to perform signing operations on this request. Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a client certificate for 825 days: subject= commonName = magedu02 Type the word 'yes' to continue, or any other input to abort. Confirm request details: Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-2178.DS9vQq/tmp.5UzCsI Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'magedu02' Certificate is to be certified until Mar 24 07:39:26 2025 GMT (825 days) Write out database with 1 new entries Data Base Updated Certificate created at: /etc/openvpn/easy-rsa-server/3/pki/issued/magedu02.crt OpenVPN客户端用户证书文件存放路径:/etc/openvpn/client/magedu02,证书文件如下: total 20 -rw------- 1 root root 1204 Dec 20 15:39 ca.crt -rw-r--r-- 1 root root 236 Dec 20 15:39 client.ovpn -rw------- 1 root root 4494 Dec 20 15:39 magedu02.crt -rw------- 1 root root 1704 Dec 20 15:39 magedu02.key
使用新创建的OpenVPN客户端用户magedu02连接:
2.5.3 吊销OpenVPN客户端用户
#查看当前证书的有效型,V为有效,R为无效 [root@rocky8 ~]#cat /etc/openvpn/easy-rsa-server/3/pki/index.txt V 250324044241Z 83A6B5416D432B68075EB2442FBACFC3 unknown /CN=server V 250324044348Z 20CD52F6B357F3F73E2652998317794C unknown /CN=magedu01 V 250324073926Z 7BC345A6CEF339E5DBD883736CF8884A unknown /CN=magedu02 #吊销指定用户的证书 [root@rocky8 ~]#cd /etc/openvpn/easy-rsa-server/3 [root@rocky8 3]#ll total 100 -rwxr-xr-x 1 root root 76946 Dec 20 12:42 easyrsa -rw-r--r-- 1 root root 4616 Dec 20 12:42 openssl-easyrsa.cnf drwx------ 8 root root 4096 Dec 20 15:39 pki -rw-r--r-- 1 root root 8925 Dec 20 12:42 vars drwxr-xr-x 2 root root 122 Dec 20 12:42 x509-types [root@rocky8 3]#./easyrsa revoke magedu01 Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 Please confirm you wish to revoke the certificate with the following subject: subject= commonName = magedu01 Type the word 'yes' to continue, or any other input to abort. Continue with revocation: yes Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-2267.u9gU1U/tmp.hR2mIX Revoking Certificate 20CD52F6B357F3F73E2652998317794C. Data Base Updated IMPORTANT!!! Revocation was successful. You must run gen-crl and upload a CRL to your infrastructure in order to prevent the revoked cert from being accepted. #查看当前证书的有效型,V为有效,R为无效 [root@rocky8 3]#cat /etc/openvpn/easy-rsa-server/3/pki/index.txt V 250324044241Z 83A6B5416D432B68075EB2442FBACFC3 unknown /CN=server R 250324044348Z 221220075546Z 20CD52F6B357F3F73E2652998317794C unknown /CN=magedu01 V 250324073926Z 7BC345A6CEF339E5DBD883736CF8884A unknown /CN=magedu02 #生成证书吊销列表 [root@rocky8 ~]#cd /etc/openvpn/easy-rsa-server/3 [root@rocky8 3]#./easyrsa gen-crl Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.8/vars Using SSL: openssl OpenSSL 1.1.1k FIPS 25 Mar 2021 Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-2311.dDJiZO/tmp.IPhmj4 An updated CRL has been created. CRL file: /etc/openvpn/easy-rsa-server/3/pki/crl.pem #发布证书吊销列表文件 [root@rocky8 3]#echo "crl-verify /etc/openvpn/easy-rsa-server/3/pki/crl.pem" >> /etc/openvpn/server.conf [root@rocky8 3]#systemctl restart openvpn@server.service
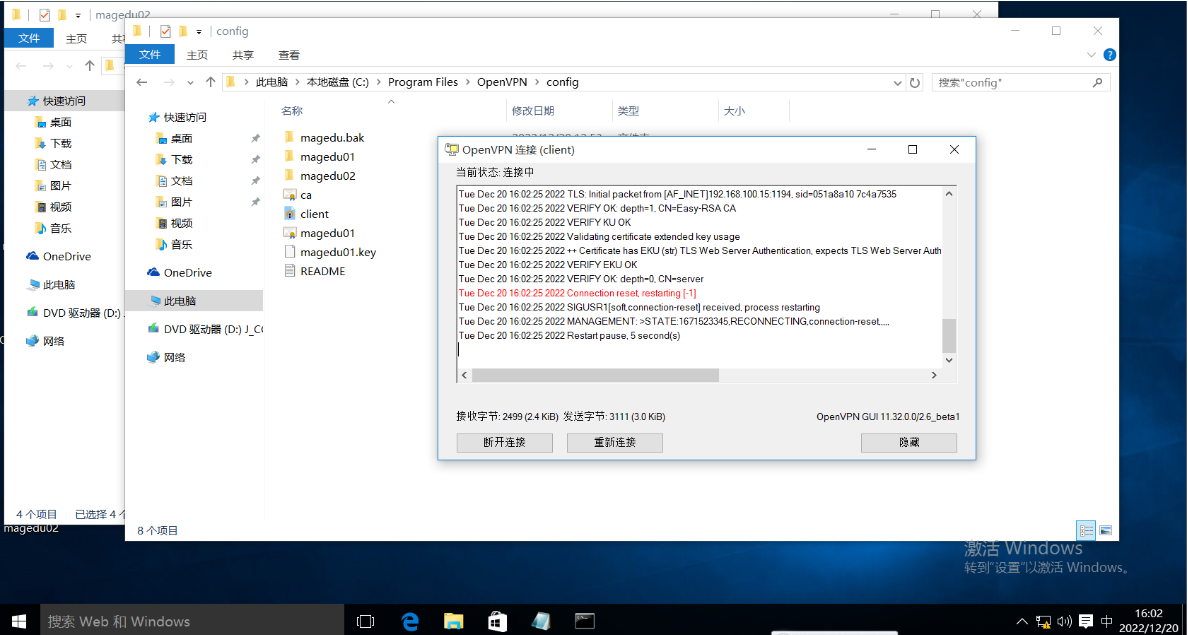
使用已吊销的OpenVPN客户端用户magedu01连接:
2.6 阿里云操作
#购买ECS, 做快照,重装系统,购买SLB,mysql. 在阿里上基于SLB, mysql,完成部署LAMP
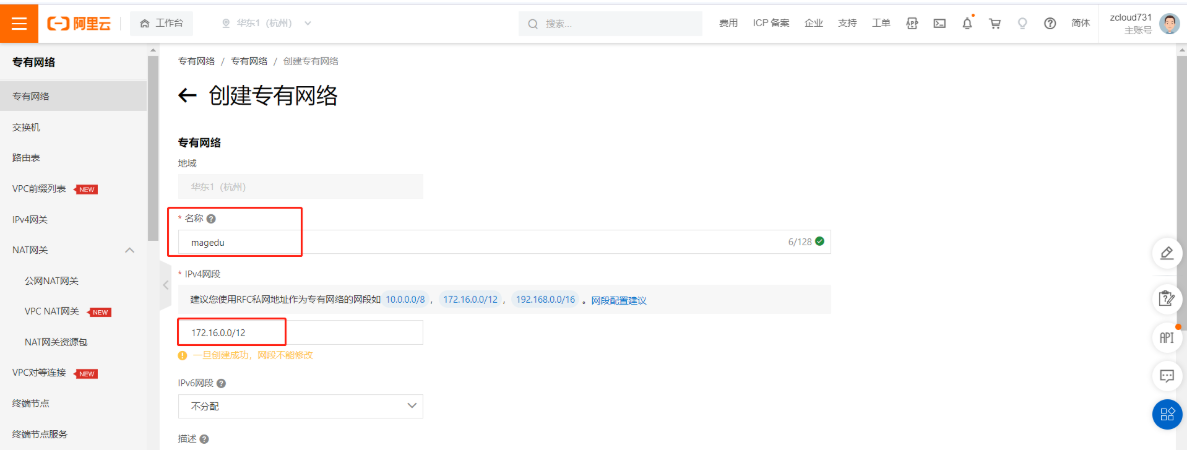
2.6.1 创建专有网络VPC
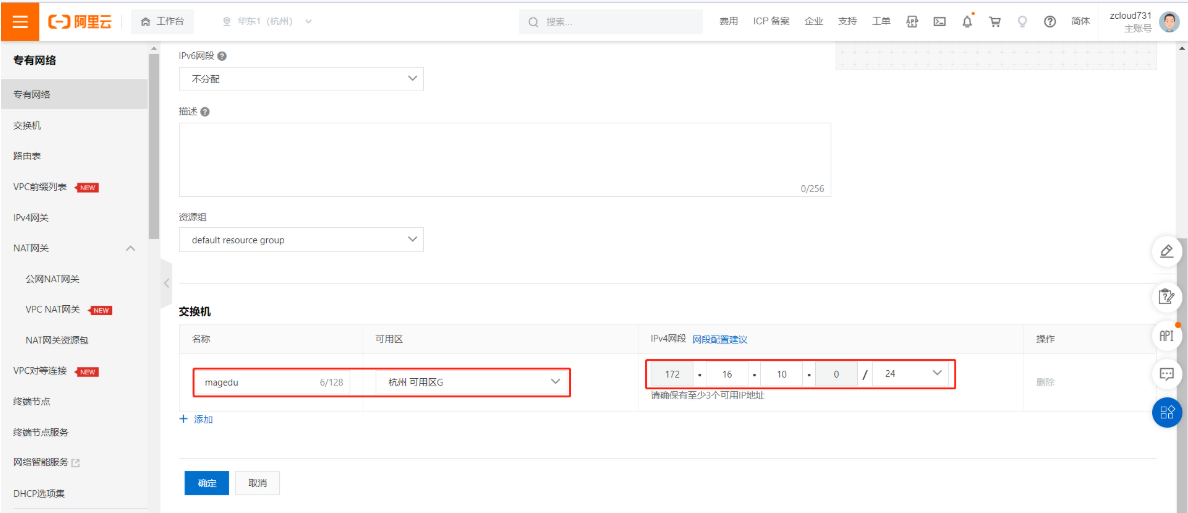
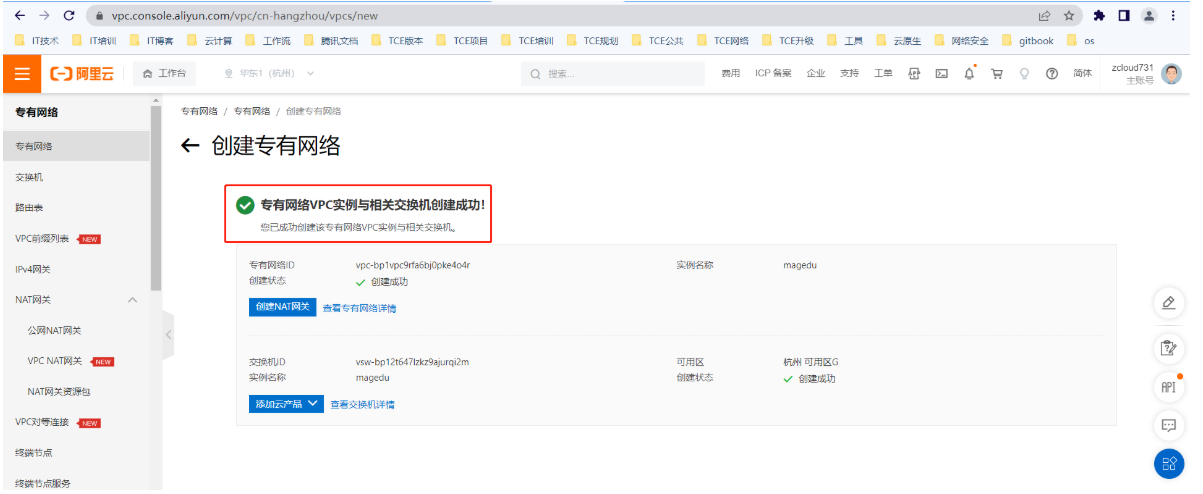
2.6.2 创建安全组
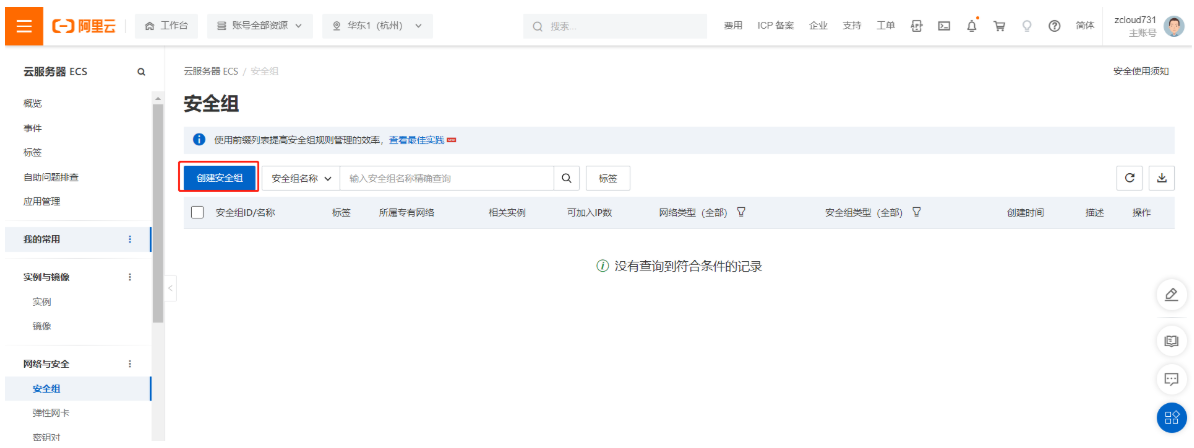
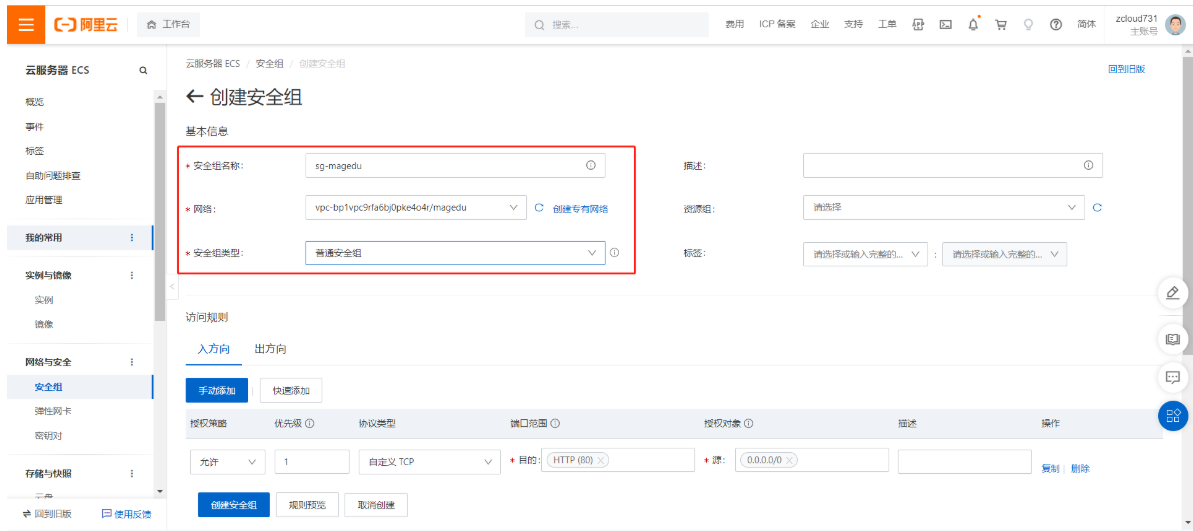
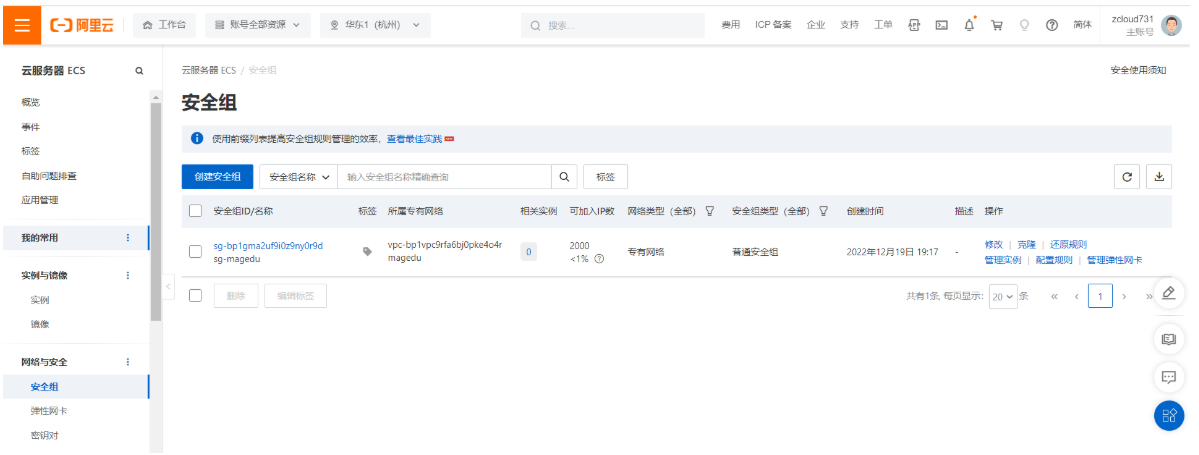
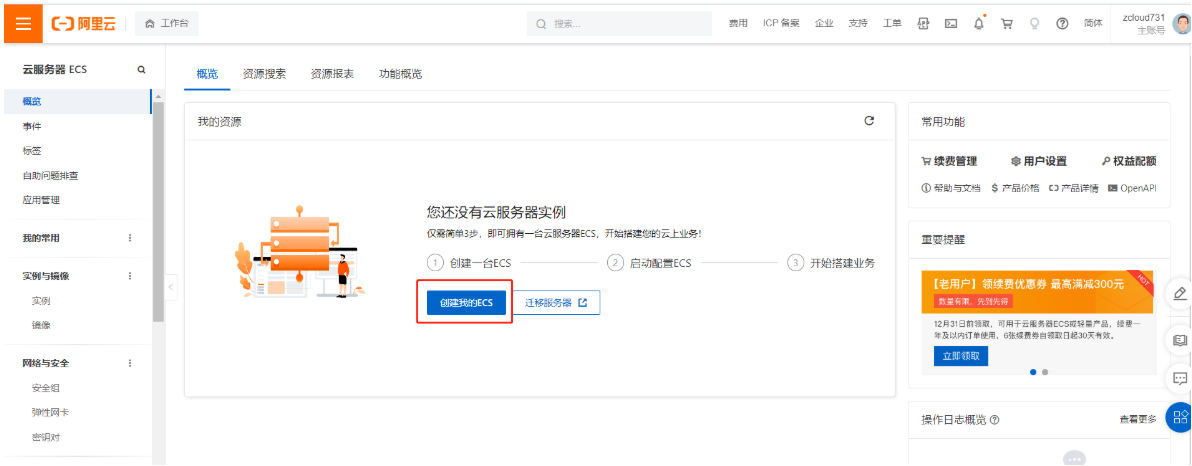
2.6.3 创建云服务器
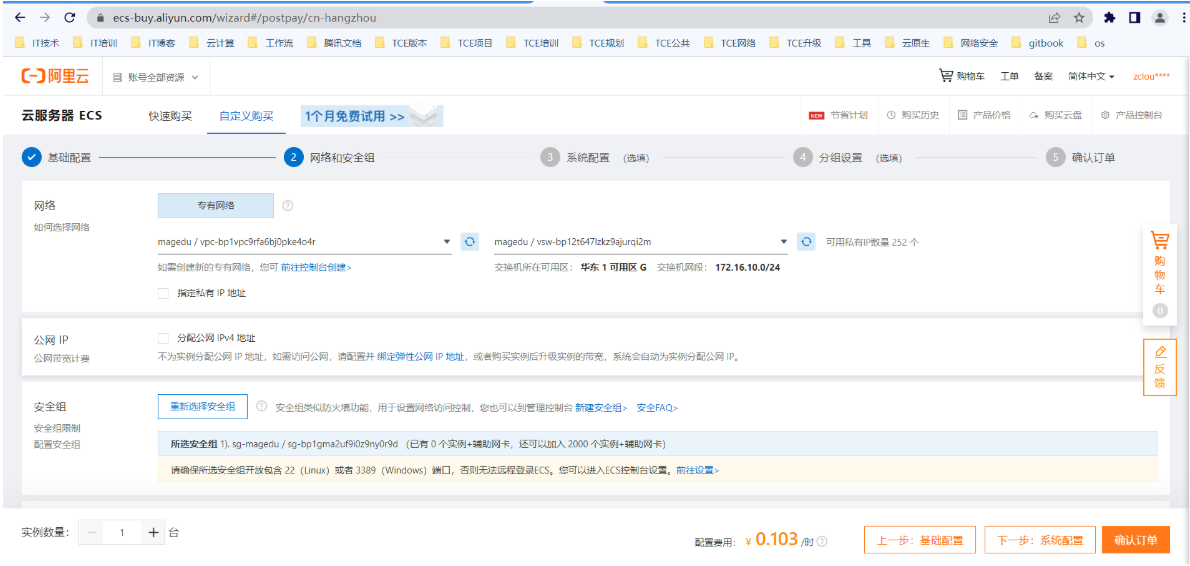
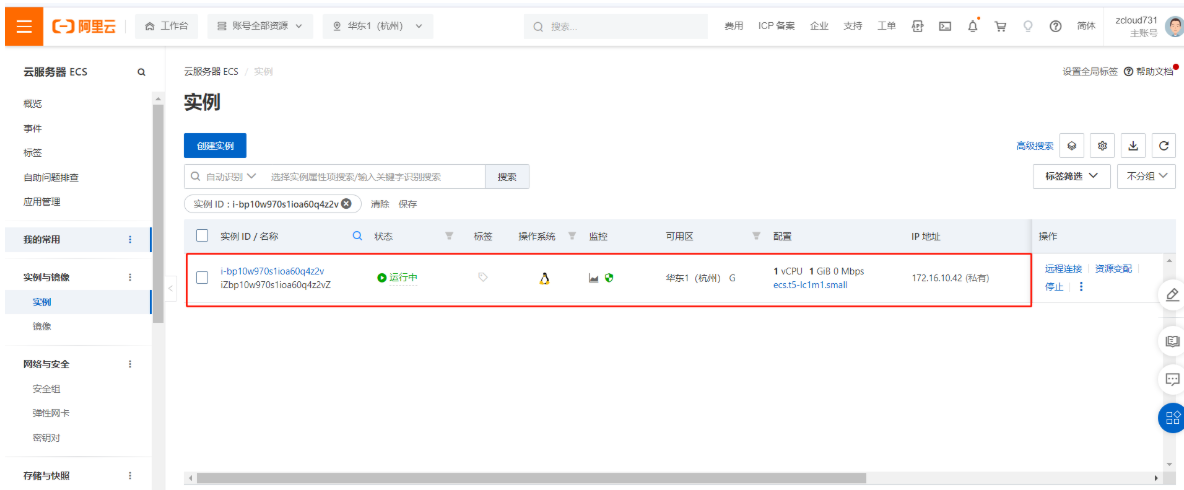
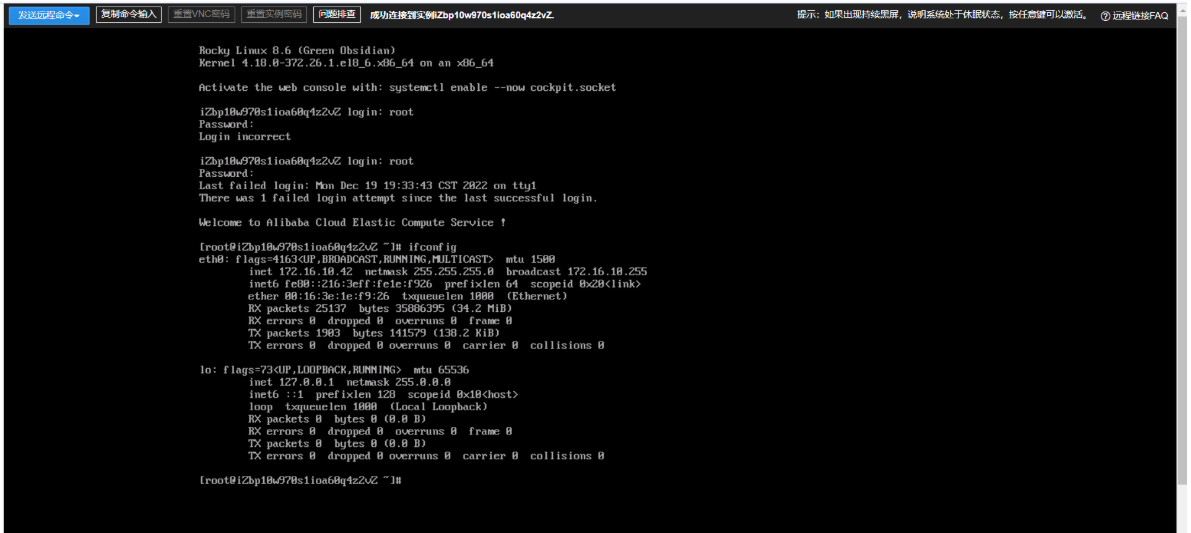
2.6.4 创建云硬盘快照
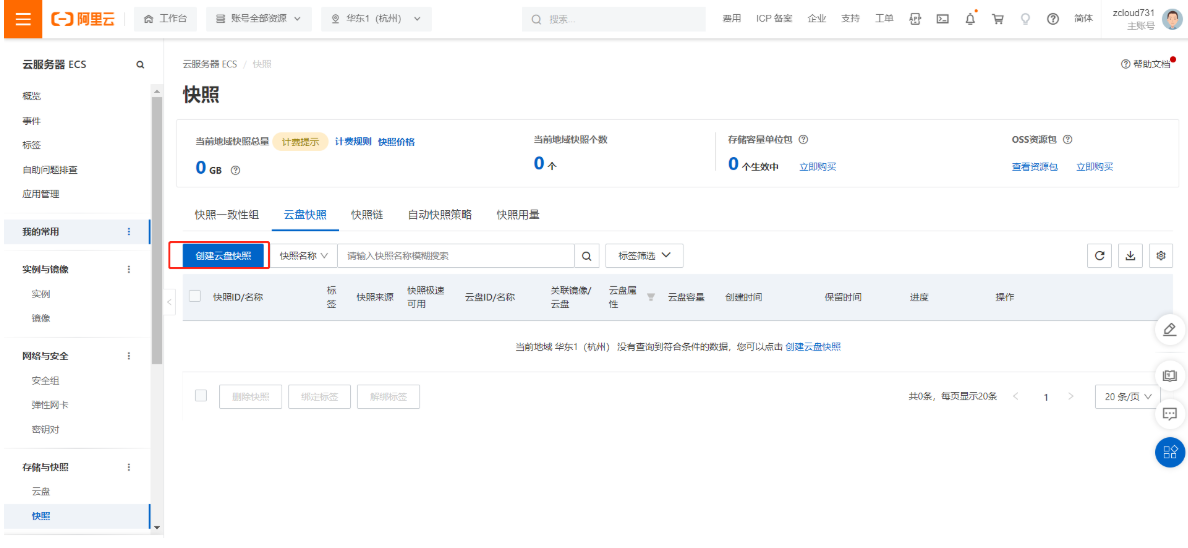
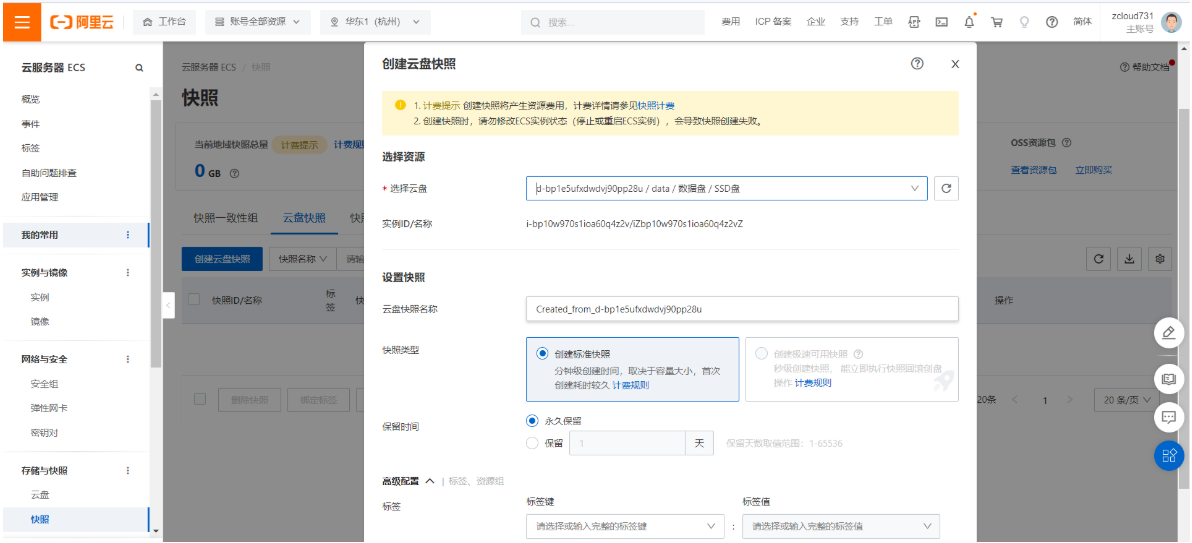
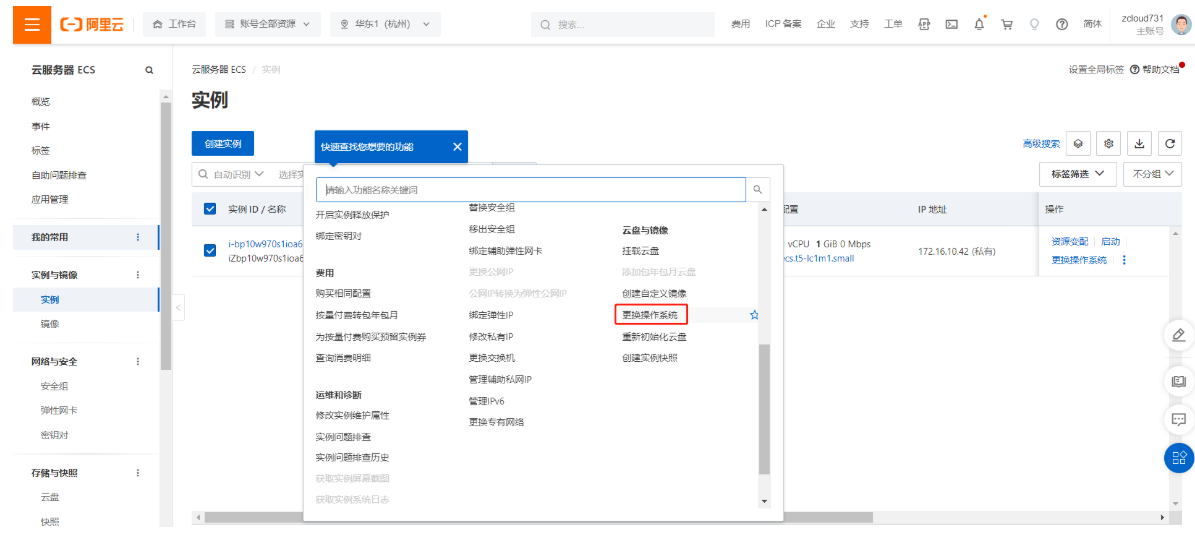
2.6.5 重装系统
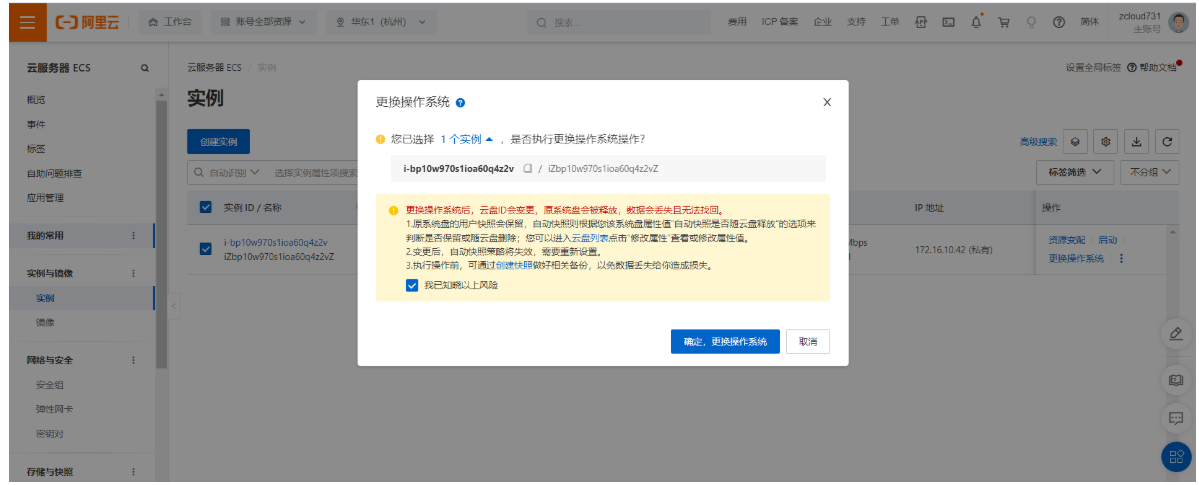
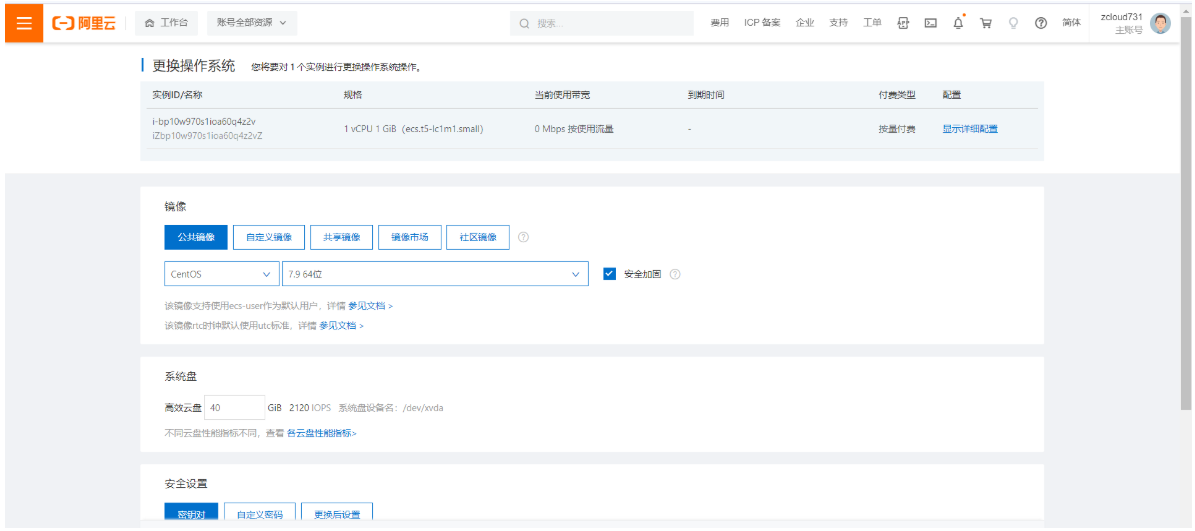
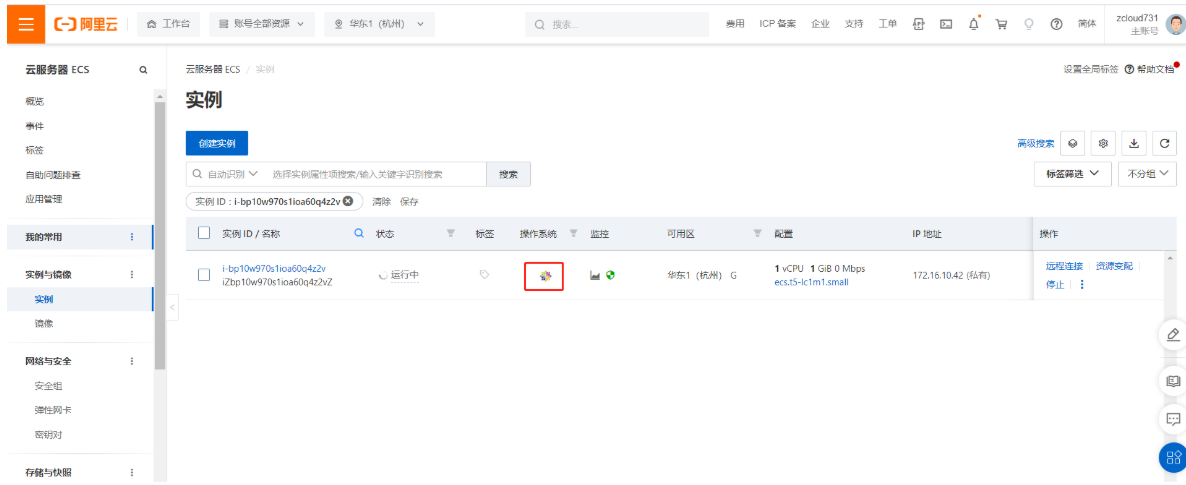
2.6.6 搭建LAMP
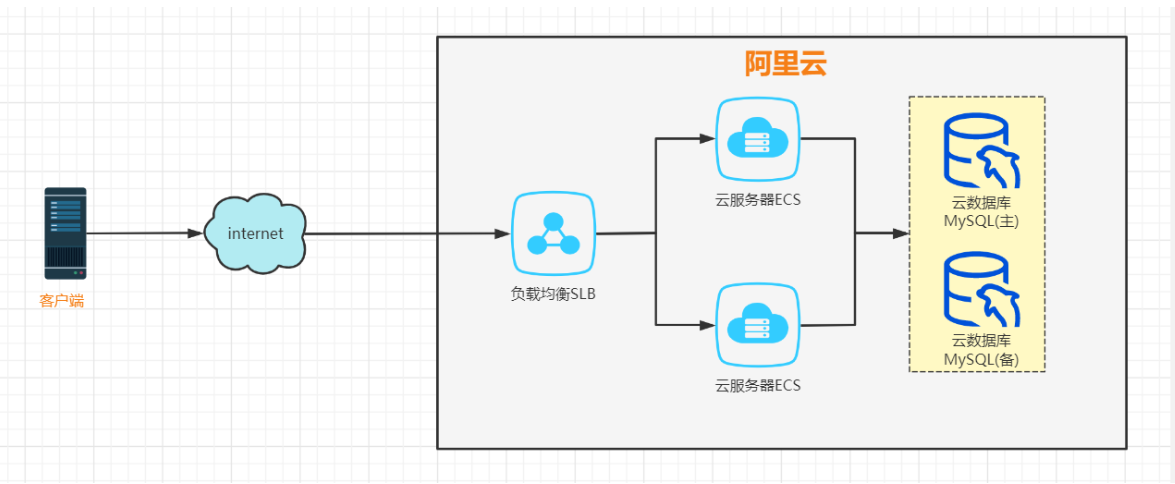
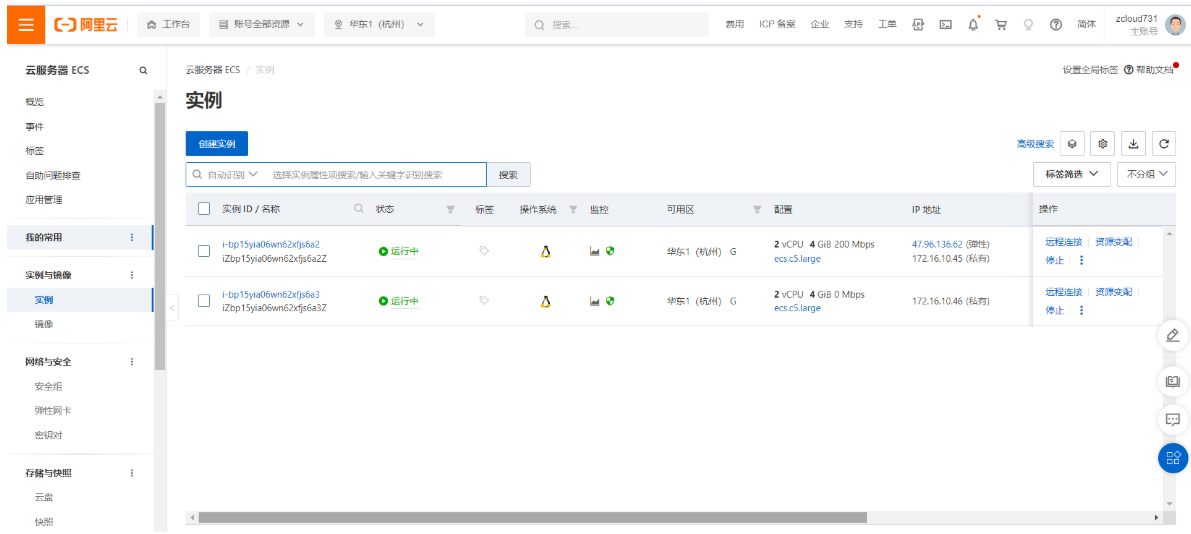
创建2台云服务器ECS:
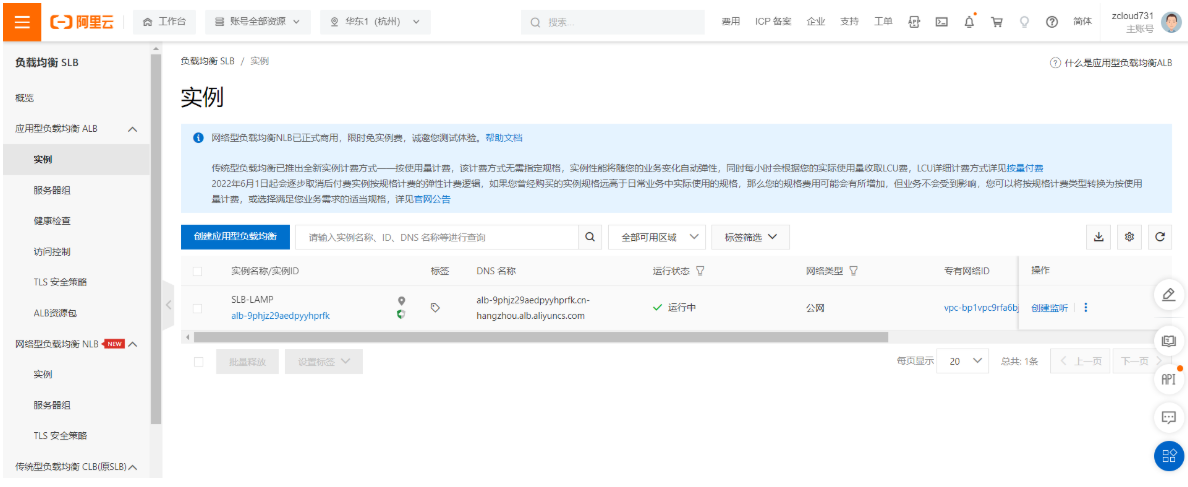
创建负载均衡SLB
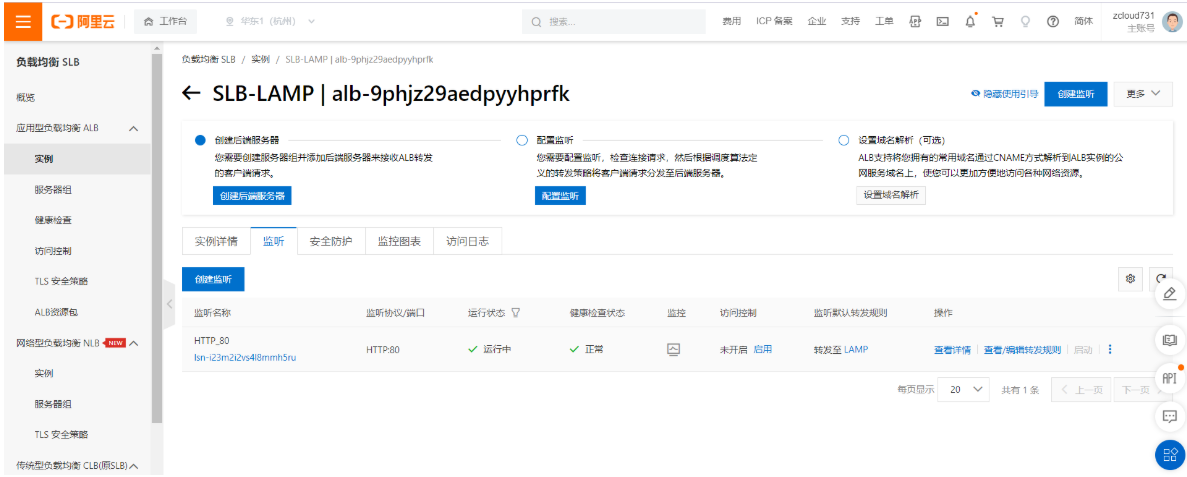
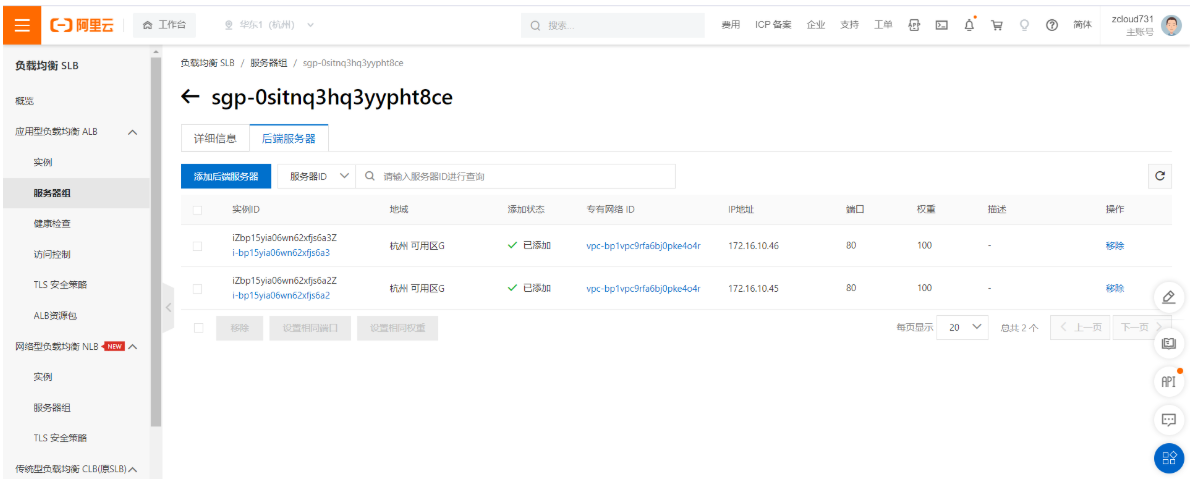
创建云数据库Mysql:
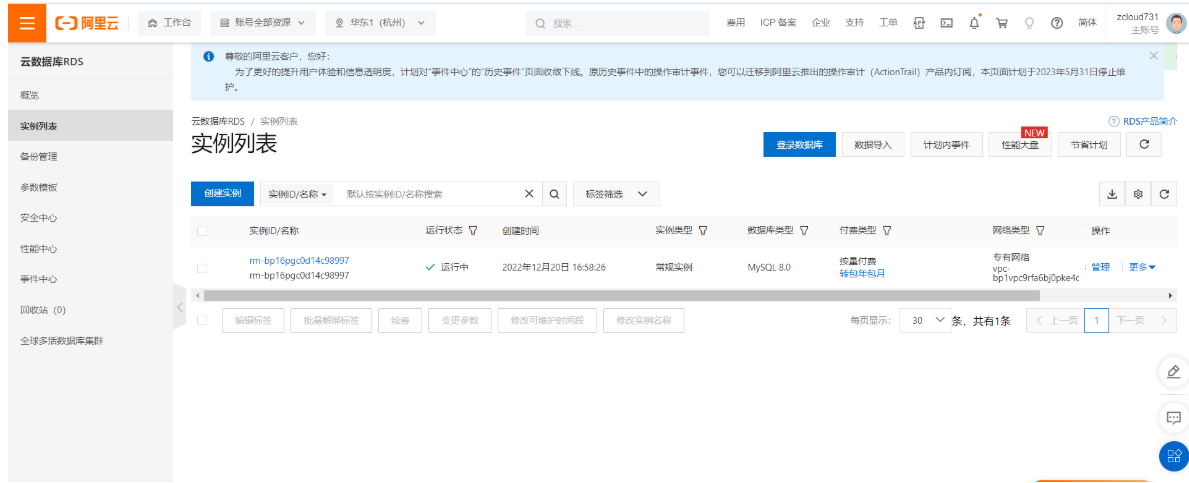
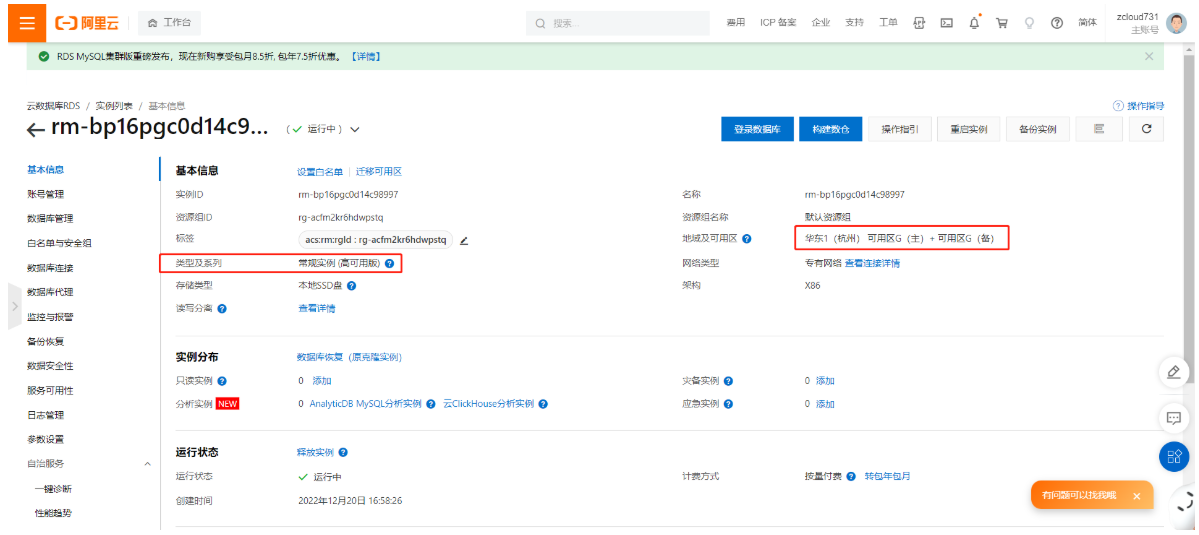
#部署LAMP yum install -y httpd yum install -y php vi /etc/httpd/conf/httpd.conf ServerName localhost:80 <Directory /> AllowOverride none Require all granted </Directory> <IfModule dir_module> DirectoryIndex index.php index.html </IfModule> AddType application/x-http-php .php AddType application/x-http-php-source .phps systemctl restart httpd
客户端测试访问:
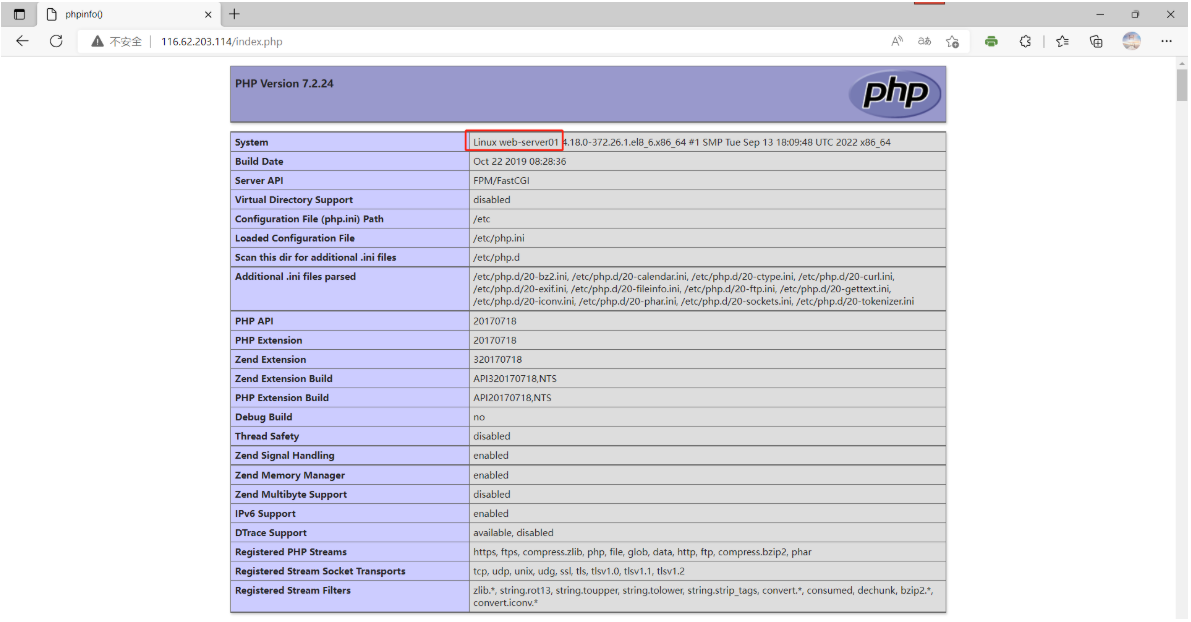
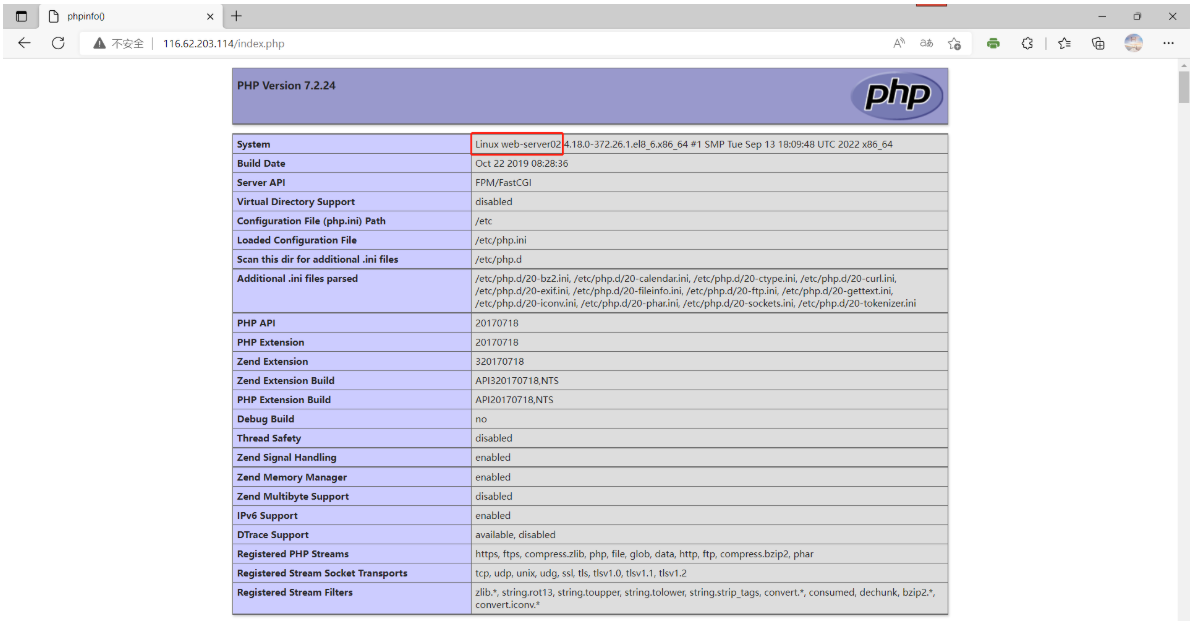
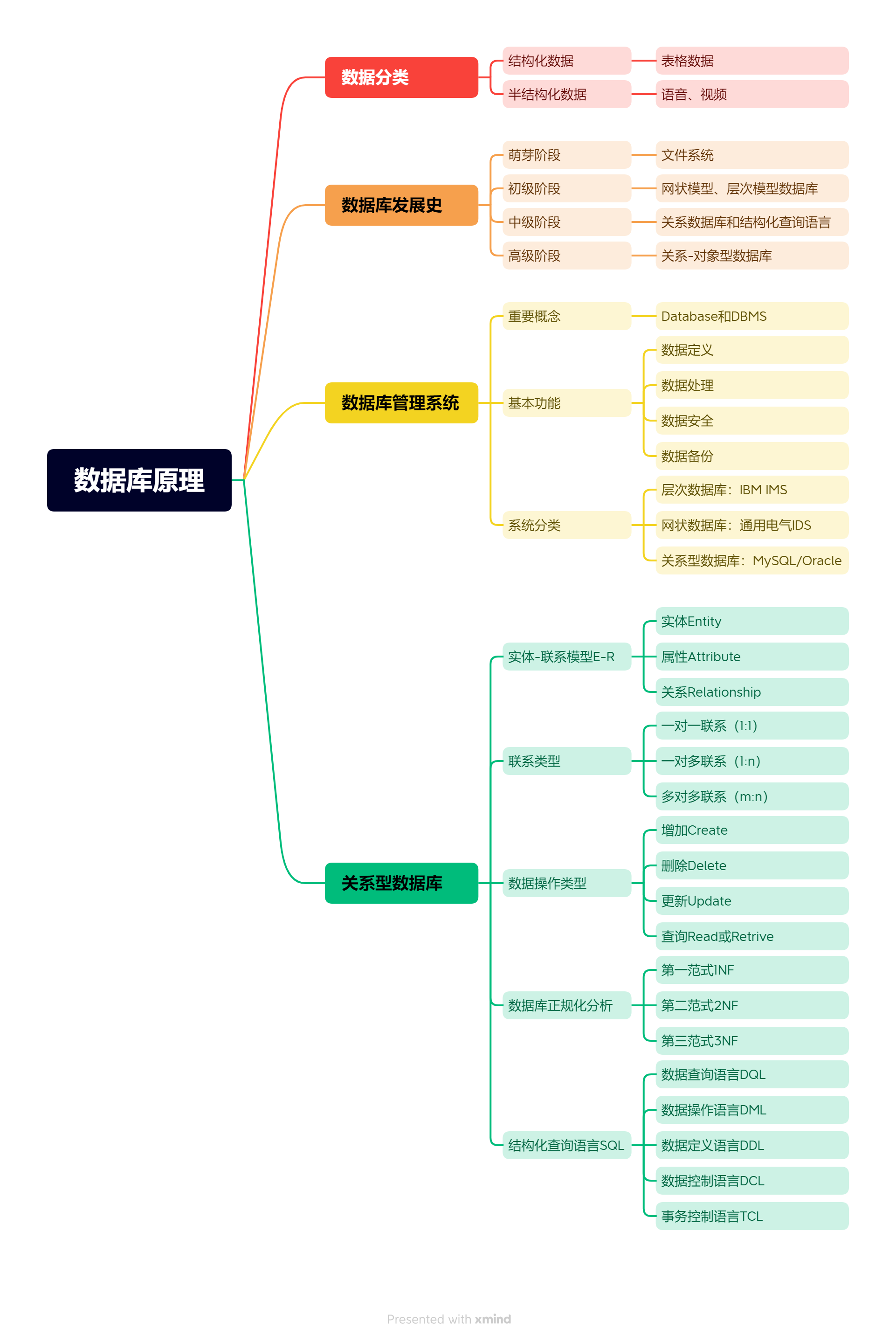
2.7 总结数据库原理


 浙公网安备 33010602011771号
浙公网安备 33010602011771号