描述
- 编写一个burpsuite的模糊测试插件,对拦截到的http载荷进行变异测试
分析
- 用python写bp插件的话,需要安装一个Jython环境——一个用java编写的python2实现
- 接口部分代码由Jython提供,我们只需要编写payload变异部分的实现
代码
- burp插件类:固定写法,getGeneratorName返回插件名,createNewInstance返回一个载荷生成器
class BurpExtender(IBurpExtender, IIntruderPayloadGeneratorFactory):
def registerExtenderCallbacks(self, callbacks):
self._callbacks = callbacks
self._helpers = callbacks.getHelpers()
callbacks.registerIntruderPayloadGeneratorFactory(self)
return
def getGeneratorName(self):
return "BHP Payload Generator"
def createNewInstance(self, attack):
return BHPFuzzer(self, attack)
- 载荷生成器类:hasMorePayloads用来判断什么时候截止,getNextPayload获取原始载荷,返回新生成的载荷,reset在Intruder进入下一个载荷位置时调用,mutate_payload实现具体的变异
class BHPFuzzer(IIntruderPayloadGenerator):
def __init__(self, extender, attack):
self._extender = extender
self._helpers = extender._helpers
self._attack = attack
self.max_payloads = 100
self.num_iterations = 0
return
def hasMorePayloads(self):
if self.num_iterations >=self.max_payloads:
return False
else:
return True
def getNextPayload(self, current_payload):
payload = "".join(chr(x) for x in current_payload)
payload = self.mutate_payload(payload)
self.num_iterations += 1
return payload
def reset(self):
self.num_iterations = 0
return
def mutate_payload(self, original_payload):
payload_len = len(original_payload)
m = random.randint(0, payload_len-1)
n = random.randint(0, payload_len-1)
payload_list = list(original_payload)
payload_list[m] = original_payload[n]
payload_list[n] = original_payload[m]
new_payload = "".join(payload_list)
return new_payload
from burp import IBurpExtender
from burp import IIntruderPayloadGeneratorFactory
from burp import IIntruderPayloadGenerator
from java.util import List, ArrayList
import random
class BurpExtender(IBurpExtender, IIntruderPayloadGeneratorFactory):
def registerExtenderCallbacks(self, callbacks):
self._callbacks = callbacks
self._helpers = callbacks.getHelpers()
callbacks.registerIntruderPayloadGeneratorFactory(self)
return
def getGeneratorName(self):
return "BHP Payload Generator"
def createNewInstance(self, attack):
return BHPFuzzer(self, attack)
class BHPFuzzer(IIntruderPayloadGenerator):
def __init__(self, extender, attack):
self._extender = extender
self._helpers = extender._helpers
self._attack = attack
self.max_payloads = 100
self.num_iterations = 0
return
def hasMorePayloads(self):
if self.num_iterations >=self.max_payloads:
return False
else:
return True
def getNextPayload(self, current_payload):
payload = "".join(chr(x) for x in current_payload)
payload = self.mutate_payload(payload)
self.num_iterations += 1
return payload
def reset(self):
self.num_iterations = 0
return
def mutate_payload(self, original_payload):
payload_len = len(original_payload)
m = random.randint(0, payload_len-1)
n = random.randint(0, payload_len-1)
payload_list = list(original_payload)
payload_list[m] = original_payload[n]
payload_list[n] = original_payload[m]
new_payload = "".join(payload_list)
return new_payload
结果
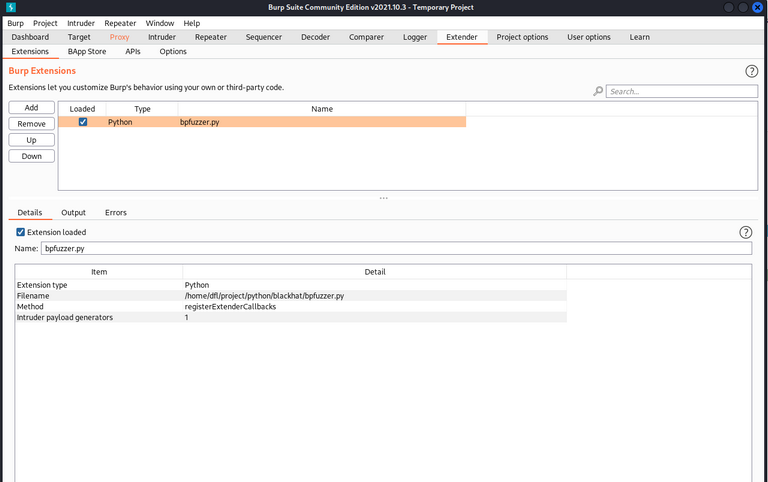
- bp加载自定义的插件
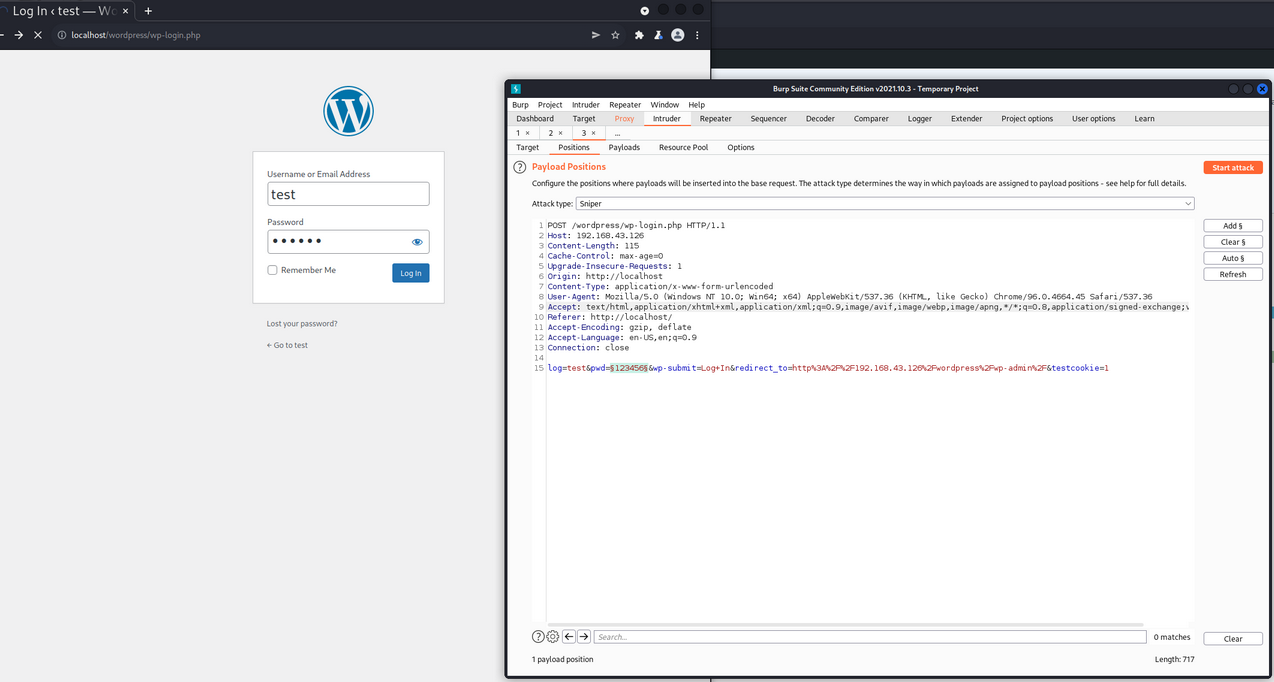
- bp拦截wordpress登录请求,并发送到Intruder,选择好payload位置
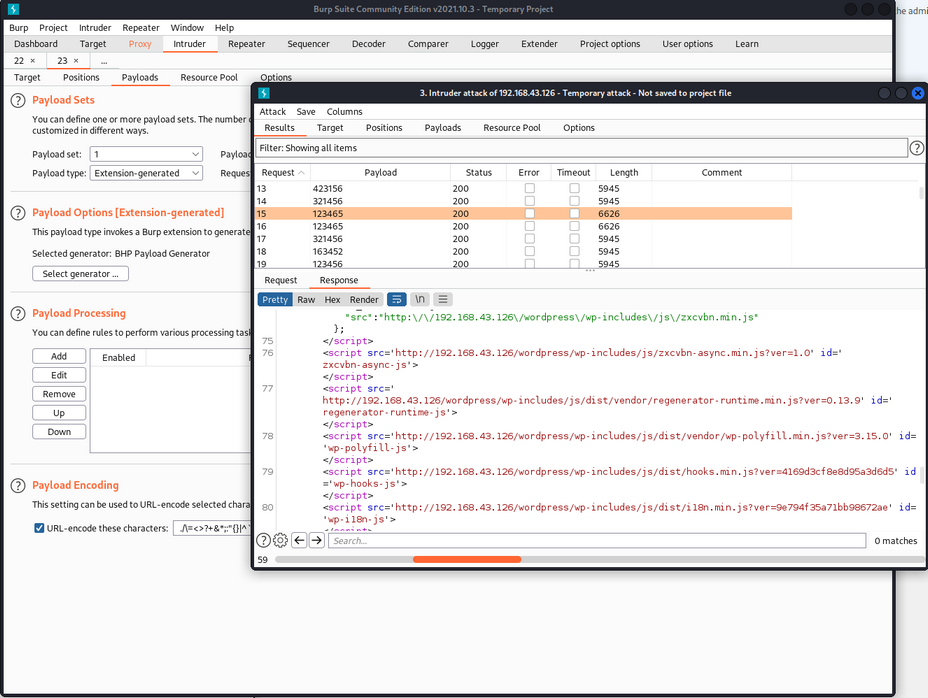
- 启动攻击,成功抓到特殊长度的响应,登录成功






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· AI与.NET技术实操系列(二):开始使用ML.NET
· 单线程的Redis速度为什么快?
· Pantheons:用 TypeScript 打造主流大模型对话的一站式集成库