基于Nginx的https服务
1、HTTPS协议的实现
1、为什么需要HTTPS?
原因:HTTP不安全
- 1、传输数据被中间人盗用、信息泄露
- 2、数据内容劫持、篡改
对传输内容进行加密以及身份验证
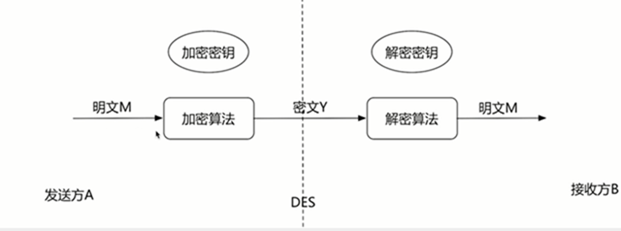
2、对称加密
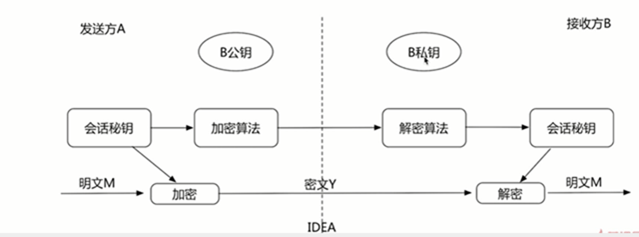
非对称加密
3、HTTPS加密协议原理
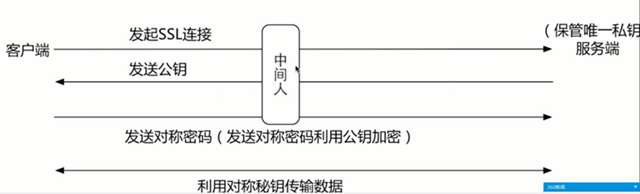
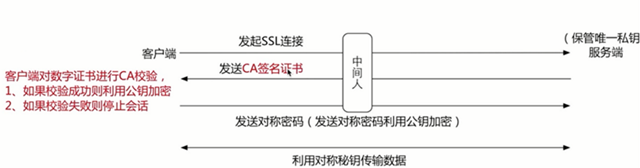
4、中间人伪造客户端和服务端
证书是在客户端的,进行校验。
2、生成密钥和CA证书
#openssl version
OpenSSL 1.0.1e-fips 11 Feb 2013
#nginx-v
-with-http_ssl_module
步骤一、生成key密钥

[root@web-01 ssl_key]# openssl genrsa -idea -out lewen.key 1024 Generating RSA private key, 1024 bit long modulus ......................................++++++ ..............................++++++ e is 65537 (0x10001) Enter pass phrase for lewen.key: #密码要写.或者不写 Verifying - Enter pass phrase for lewen.key:
步骤二、生成证书签名请求文件(csr文件)

[root@web-01 ssl_key]# openssl req -new -key lewen.key -out lewen.csr Enter pass phrase for lewen.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:SZ Locality Name (eg, city) [Default City]:futian Organization Name (eg, company) [Default Company Ltd]:fadewalk Organizational Unit Name (eg, section) []:fadewalk.com Common Name (eg, your name or your server's hostname) []:fadewalk.com Email Address []:fadewalk@163.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: #没有要求就为空 An optional company name []: [root@web-01 ssl_key]# ls lewen.csr lewen.key
步骤三、生成证书签名文件(CA文件)

[root@web-01 ssl_key]# openssl x509 -req -days 3650 -in lewen.csr -signkey lewen.key -out lewen.crt Signature ok subject=/C=CN/ST=SZ/L=futian/O=fadewalk/OU=fadewalk.com/CN=fadewalk.com/emailAddress=fadewalk@163.com Getting Private key Enter pass phrase for lewen.key: [root@web-01 ssl_key]# ls lewen.crt lewen.csr lewen.key
3、Nginx的HTTPS语法配置
例子
server {
listen 443 ssl;
keepalive_timeout 70;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers AES128-SHA:AES256-SHA:RC4-SHA:DES-CBC3-SHA:RC4-MD5;
ssl_certificate /usr/local/nginx/conf/cert.pem;
ssl_certificate_key /usr/local/nginx/conf/cert.key;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
...
}
[root@web-01 ~]# nginx -s reload
nginx: [warn] the "ssl" directive is deprecated, use the "listen ... ssl" directive instead in /etc/nginx/conf.d/cp4/test_https.conf:4
key设置了密码,每次重启都要输入密码很麻烦
4、场景-配置苹果要求的证书
a、服务器所有的连接使用TLS1.2以上版本(openssl 1.0.2)
b、HTTPS证书必须使用SHA 256以上哈希算法签名
C、HTTPS证书必须使用RSA 2048位或ECC256位以上公钥算法
d、使用前向加密技术
查看证书信息
[root@web-01 ssl_key]# openssl x509 -noout -text -in ./lewen_apple.crt
一键生成证书

[root@web-01 ssl_key]# openssl req -days 3650 -x509 -sha256 -nodes -newkey rsa:2048 -keyout lewen.key -out lewen_apple.crt Generating a 2048 bit RSA private key ......................................................................................+++ ..+++ writing new private key to 'lewen.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:guangdong Locality Name (eg, city) [Default City]:sz Organization Name (eg, company) [Default Company Ltd]:fadewlak Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) []: Email Address []: [root@web-01 ssl_key]# ls lewen_apple.crt lewen.key
nginx 1.15 以后开启ssl的正确姿势
2019/06/17 17:06:54 [warn] 36807#36807: the "ssl" directive is deprecated, use the "listen ... ssl" directive instead in /etc/nginx/conf.d/cp4/test_https.conf:4 不推荐使用“ssl”指令,而是在/etc/nginx/conf.d/cp4/test_https中使用“listen ... ssl”指令。CONF:4 ssl on 这种方式开启ssl已经不行了 listen 443 ssl 采用这种
测试网页自己生成的证书,会被提示不安全
去掉之前分步生成输入的保护码
openssl rsa -in ./lewen.key -out ./lewen_nopassword.key
5、HTTPS服务优化
方法一、激活keepalive长连接
方法二、设置ssl session缓存
server {
listen 443 ssl;
server_name web01.fadewalk.com;
# ssl on; nginx 1.15之后这样配置无效
keepalive_timeout 100;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_certificate /etc/nginx/ssl_key/lewen_apple.crt;
ssl_certificate_key /etc/nginx/ssl_key/lewen.key;
#ssl_certificate_key /etc/nginx/ssl_key/lewen_nopass.key;
location / {
root /opt/app/code/cp4/code;
index lewen.html lewen.htm;
}
}
本文来自博客园,作者:元贞,转载请注明原文链接:https://www.cnblogs.com/yuleicoder/p/11068304.html




 浙公网安备 33010602011771号
浙公网安备 33010602011771号