certificate
1.创建一个根 CA,包括生成私钥和根证书。分析证书和0015,0034标准的符合情况
yoga@yoga:~$ openssl genrsa -out rootCA.key 2048
yoga@yoga:~$ openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 1024 -out rootCA.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Fujian
Locality Name (eg, city) []:zhangzhou
Organization Name (eg, company) [Internet Widgits Pty Ltd]:hyj
Organizational Unit Name (eg, section) []:20211211
Common Name (e.g. server FQDN or YOUR name) []:HYJ
Email Address []:111@qq.com
yoga@yoga:~$ openssl -x5009 -in rootCA.pem -text -noout
Invalid command '-x5009'; type "help" for a list.
yoga@yoga:~$ openssl -x509 -in rootCA.pem -text -noout
Invalid command '-x509'; type "help" for a list.
yoga@yoga:~$ openssl x509 -in rootCA.pem -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
0e:c9:a8:ce:d5:af:77:df:1c:7d:40:f7:90:80:08:a8:29:9a:7e:15
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=Fujian, L=zhangzhou, O=hyj, OU=20211211, CN=HYJ, emailAddress=111@qq.com
Validity
Not Before: Jun 1 04:42:38 2024 GMT
Not After : Mar 22 04:42:38 2027 GMT
Subject: C=CN, ST=Fujian, L=zhangzhou, O=hyj, OU=20211211, CN=HYJ, emailAddress=111@qq.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b5:7f:41:de:ae:14:a9:95:42:14:5b:33:4b:a4:
a9:15:27:75:8a:fe:c2:53:31:bf:18:e4:09:c3:a0:
05:ec:15:c0:31:99:89:24:25:72:29:7a:de:28:5a:
03:bb:fd:2b:2c:1a:0a:9d:74:cb:90:b0:22:b5:ed:
bc:c9:42:70:ca:c9:0a:c2:af:41:76:9c:98:0a:bf:
71:3b:8a:5b:c4:52:bc:b1:90:72:23:74:0a:68:1b:
27:e9:15:fb:2e:1e:10:65:50:1e:ec:33:b4:52:49:
f6:00:d4:b6:11:be:13:9a:2b:7b:47:64:bf:79:8b:
07:b1:72:05:d7:4e:8c:cc:9a:f0:f9:98:d1:58:11:
c7:48:8a:82:34:1f:57:46:fb:85:0d:10:8c:08:c5:
d7:47:ad:f7:83:15:71:d4:34:ad:49:08:26:08:5a:
7e:e9:4e:39:b4:39:93:98:b7:86:e2:29:77:77:72:
70:4d:26:57:6f:74:f6:89:34:e3:e7:9b:0d:f7:ad:
75:bb:c0:f8:69:d8:e4:b5:c7:a8:c5:05:b4:ca:d9:
9c:6e:18:e8:eb:7f:b8:ef:8b:25:77:c9:63:6b:e1:
cf:18:40:ef:1f:40:6a:1e:18:34:57:f4:da:25:19:
13:34:64:04:0f:41:e8:71:38:07:21:ed:ff:20:06:
6f:b3
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
BD:B6:D6:CD:B0:65:9B:44:BB:86:A6:CE:61:20:00:C3:20:44:06:01
X509v3 Authority Key Identifier:
BD:B6:D6:CD:B0:65:9B:44:BB:86:A6:CE:61:20:00:C3:20:44:06:01
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
47:f8:20:aa:96:74:44:2c:d9:67:15:bd:ce:92:05:69:98:11:
65:69:49:7f:be:39:37:70:3b:11:dc:ed:e3:92:90:94:16:02:
5d:c2:8b:9c:73:19:4a:2b:bd:71:df:d8:d5:7b:12:68:ef:c1:
b2:4b:b1:a0:75:85:7e:fd:14:9c:35:b7:e6:e0:44:b3:b2:16:
9a:29:9e:29:20:45:f3:24:7a:fb:f4:d4:eb:38:22:3b:df:a5:
f5:99:68:fc:44:0c:f2:5a:54:ce:ed:74:17:b1:02:87:0d:c6:
f3:22:94:c6:6a:cc:6f:b9:b6:72:8c:39:f3:28:dc:1c:7f:82:
42:c6:d7:5a:2b:0f:72:65:f6:0d:43:82:50:07:87:c6:79:7c:
7f:e2:72:10:16:1a:64:e3:67:e8:fb:cf:10:3e:6b:f4:a0:aa:
b7:1b:bc:53:e0:3b:f9:f6:dd:39:03:d6:e2:21:de:50:ee:1b:
f8:27:b4:85:97:a3:68:e6:59:fe:4d:e6:90:b7:a7:ef:67:6c:
75:84:70:40:e0:b3:e9:6d:89:9e:ab:69:49:31:63:42:c9:13:
5c:df:69:f0:bd:de:3e:4f:b5:85:9a:20:42:c3:4b:30:7c:06:
24:70:d1:63:ab:5c:ba:40:89:3e:ff:04:67:2c:eb:f8:58:5b:
cb:9f:1b:60
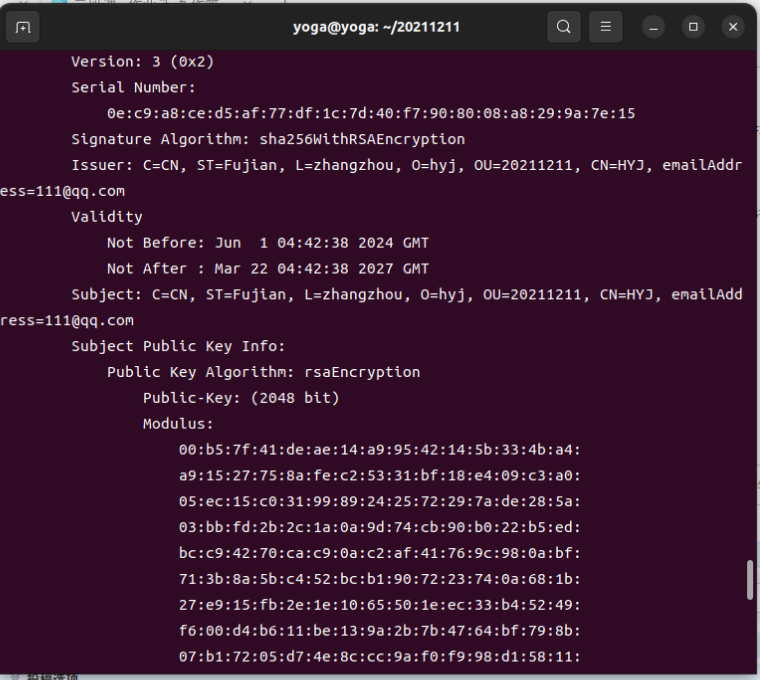
2.为一台服务器生成一个私钥和证书签署请求(CSR)。
创建CA证书扩展信息
echo "subjectKeyIdentifier=hash" > ca/certs/ca_cert_extensions
echo "authorityKeyIdentifier=keyid:always,issuer" >> ca/certs/ca_cert_extensions
echo "basicConstraints=critical,CA:true" >> ca/certs/ca_cert_extensions
echo "subjectAltName=DNS.1:localhost,DNS.2:ca.xxoo.com,IP:127.0.0.1" >> ca/certs/ca_cert_extensions
生成自签名的CA根证书
openssl x509 -req -days 3650 -sha256
-extfile ca/certs/ca_cert_extensions
-signkey ca/keys/ca.key
-in ca/certs/ca.csr -out ca/certs/ca.crt查看CA根证书
openssl x509 -text --noout -in ca/certs/ca.crt
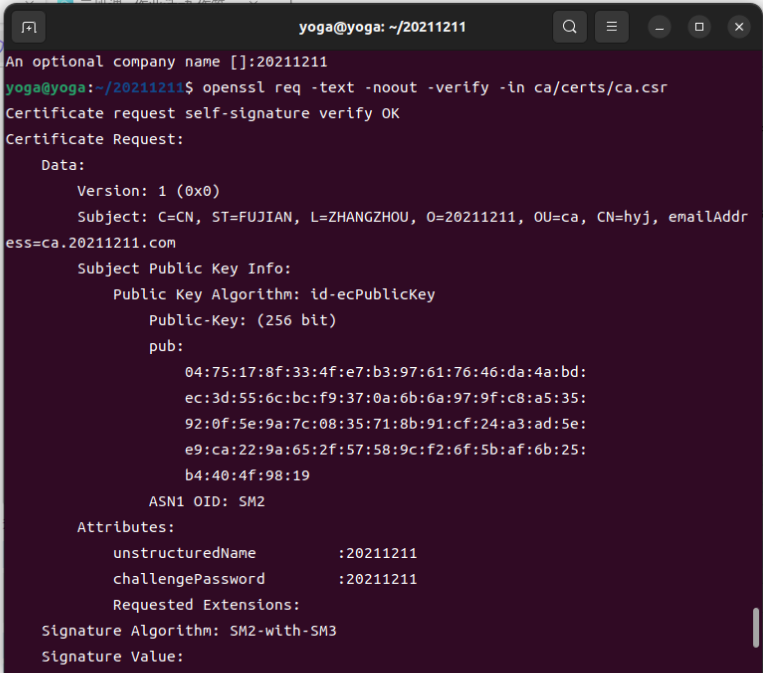
创建证书请求
openssl req -new
-subj "/C=CN/ST=Anhui/L=Hefei/O=xxoo/OU=server/CN=server.xxoo.com"
-key server/keys/server.key -out server/certs/server.csr
openssl req -text -noout -verify -in server/certs/server.csr
生成服务器证书扩展信息
echo "subjectKeyIdentifier = hash" > server/certs/server_cert_extensions
echo "authorityKeyIdentifier = keyid:always,issuer" >> server/certs/server_cert_extensions
echo "basicConstraints = CA:FALSE" >> server/certs/server_cert_extensions
echo "keyUsage = nonRepudiation, digitalSignature, keyEncipherment" >> server/certs/server_cert_extensions
echo "subjectAltName = DNS.1:localhost,DNS.2:server.xxoo.com,IP:127.0.0.1" >> server/certs/server_cert_extensions
生成服务器证书
openssl x509 -req -days 3650 -sha256 \
-extfile server/certs/server_cert_extensions \
-CA ca/certs/ca.crt -CAkey ca/keys/ca.key \
-in server/certs/server.csr -out server/certs/server.crt
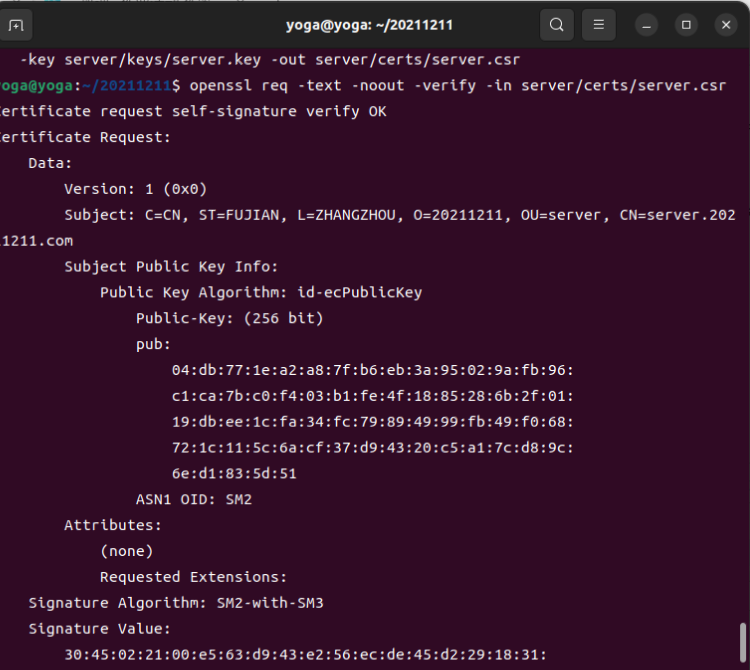
openssl x509 -text --noout -in server/certs/server.crt
吊销证书
openssl ca -config openssl.cnf -revoke server.crt -keyfile rootCA.key -cert rootCA.pem



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· winform 绘制太阳,地球,月球 运作规律
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 上周热点回顾(3.3-3.9)
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人