【java】【jenkins】PKIX:unable to find valid certification path to requested target !问题解决。
场景:jenkin导入或安装插件报错!
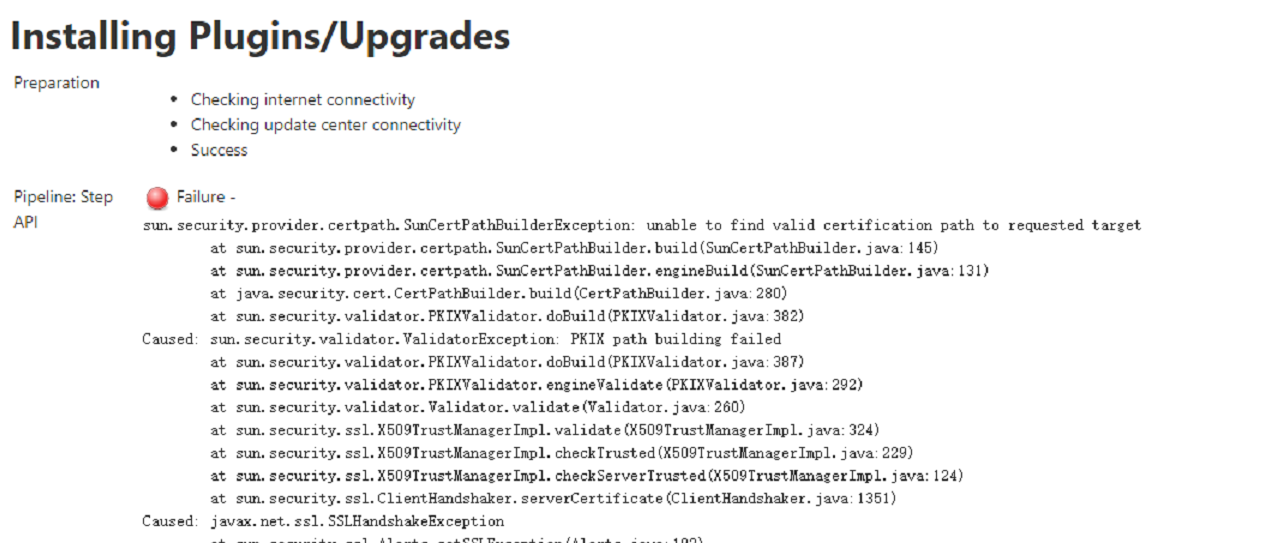
网上找了好多攻略都一半一半的,现在组织一下,意思就是要访问的插件下载/更新的服务端需要客户端安装证书。
步骤:
1、首先如果非jenkins访问也报这个错误,可以去访问目标网站直接下载安装证书到windows/linux的{JAVA_HOME}/jre/lib/security目录下
详见:https://www.cnblogs.com/zoro-zero/p/11607674.html
2、若是无法下载证书,则可再windows/linux直接通过命令安装证书
①首先需要创建一个InstallCert.java的java文件
import java.io.BufferedReader; import java.io.File; import java.io.FileInputStream; import java.io.FileOutputStream; import java.io.InputStream; import java.io.InputStreamReader; import java.io.OutputStream; import java.security.KeyStore; import java.security.MessageDigest; import java.security.cert.CertificateException; import java.security.cert.X509Certificate; import javax.net.ssl.SSLContext; import javax.net.ssl.SSLException; import javax.net.ssl.SSLSocket; import javax.net.ssl.SSLSocketFactory; import javax.net.ssl.TrustManager; import javax.net.ssl.TrustManagerFactory; import javax.net.ssl.X509TrustManager; public class InstallCert { public static void main(String[] args) throws Exception { String host; int port; char[] passphrase; if ((args.length == 1) || (args.length == 2)) { String[] c = args[0].split(":"); host = c[0]; port = (c.length == 1) ? 443 : Integer.parseInt(c[1]); String p = (args.length == 1) ? "changeit" : args[1]; passphrase = p.toCharArray(); } else { System.out .println("Usage: java InstallCert <host>[:port] [passphrase]"); return; } File file = new File("jssecacerts"); if (file.isFile() == false) { char SEP = File.separatorChar; File dir = new File(System.getProperty("java.home") + SEP + "lib" + SEP + "security"); file = new File(dir, "jssecacerts"); if (file.isFile() == false) { file = new File(dir, "cacerts"); } } System.out.println("Loading KeyStore " + file + "..."); InputStream in = new FileInputStream(file); KeyStore ks = KeyStore.getInstance(KeyStore.getDefaultType()); ks.load(in, passphrase); in.close(); SSLContext context = SSLContext.getInstance("TLS"); TrustManagerFactory tmf = TrustManagerFactory .getInstance(TrustManagerFactory.getDefaultAlgorithm()); tmf.init(ks); X509TrustManager defaultTrustManager = (X509TrustManager) tmf .getTrustManagers()[0]; SavingTrustManager tm = new SavingTrustManager(defaultTrustManager); context.init(null, new TrustManager[] { tm }, null); SSLSocketFactory factory = context.getSocketFactory(); System.out .println("Opening connection to " + host + ":" + port + "..."); SSLSocket socket = (SSLSocket) factory.createSocket(host, port); socket.setSoTimeout(10000); try { System.out.println("Starting SSL handshake..."); socket.startHandshake(); socket.close(); System.out.println(); System.out.println("No errors, certificate is already trusted"); } catch (SSLException e) { System.out.println(); e.printStackTrace(System.out); } X509Certificate[] chain = tm.chain; if (chain == null) { System.out.println("Could not obtain server certificate chain"); return; } BufferedReader reader = new BufferedReader(new InputStreamReader( System.in)); System.out.println(); System.out.println("Server sent " + chain.length + " certificate(s):"); System.out.println(); MessageDigest sha1 = MessageDigest.getInstance("SHA1"); MessageDigest md5 = MessageDigest.getInstance("MD5"); for (int i = 0; i < chain.length; i++) { X509Certificate cert = chain[i]; System.out.println(" " + (i + 1) + " Subject " + cert.getSubjectDN()); System.out.println(" Issuer " + cert.getIssuerDN()); sha1.update(cert.getEncoded()); System.out.println(" sha1 " + toHexString(sha1.digest())); md5.update(cert.getEncoded()); System.out.println(" md5 " + toHexString(md5.digest())); System.out.println(); } System.out .println("Enter certificate to add to trusted keystore or 'q' to quit: [1]"); String line = reader.readLine().trim(); int k; try { k = (line.length() == 0) ? 0 : Integer.parseInt(line) - 1; } catch (NumberFormatException e) { System.out.println("KeyStore not changed"); return; } X509Certificate cert = chain[k]; String alias = host + "-" + (k + 1); ks.setCertificateEntry(alias, cert); OutputStream out = new FileOutputStream("jssecacerts"); ks.store(out, passphrase); out.close(); System.out.println(); System.out.println(cert); System.out.println(); System.out .println("Added certificate to keystore 'jssecacerts' using alias '" + alias + "'"); } private static final char[] HEXDIGITS = "0123456789abcdef".toCharArray(); private static String toHexString(byte[] bytes) { StringBuilder sb = new StringBuilder(bytes.length * 3); for (int b : bytes) { b &= 0xff; sb.append(HEXDIGITS[b >> 4]); sb.append(HEXDIGITS[b & 15]); sb.append(' '); } return sb.toString(); } private static class SavingTrustManager implements X509TrustManager { private final X509TrustManager tm; private X509Certificate[] chain; SavingTrustManager(X509TrustManager tm) { this.tm = tm; } @Override public X509Certificate[] getAcceptedIssuers() { return new X509Certificate[0]; //throw new UnsupportedOperationException(); } public void checkClientTrusted(X509Certificate[] chain, String authType) throws CertificateException { throw new UnsupportedOperationException(); } public void checkServerTrusted(X509Certificate[] chain, String authType) throws CertificateException { this.chain = chain; tm.checkServerTrusted(chain, authType); } } }
②然后打开cmd或者linux的终端运行javac InstallCert.java会生成以下文件(以下以linux为例)
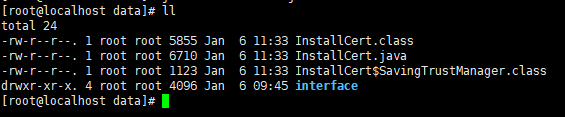
③再执行java InstallCert.java targetHost
例如:java InstallCert.java updates.jenkins.io 或 java InstallCert.java get.jenkins.io 或 java InstallCert mirrors.tuna.tsinghua.edu.cn
注意:取决于你要访问的目标服务的域名host,如果是jenkins插件地址,则是你在Manage Jenkins -> Manage Plugins -> Advanced ->Update Site ->配置的URL的域名host
注意:默认插件下载/更新地址为 https://updates.jenkins.io/update-center.json,网上方法是吧https修改为http,但更好的方法是修改为国内镜像(清华)地址https://mirrors.tuna.tsinghua.edu.cn/jenkins/updates/update-center.json
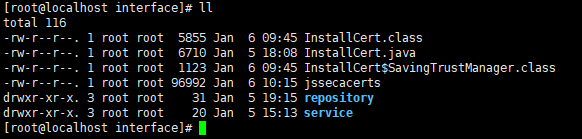
此时会多出jssecacerts文件,每个人可能会有不同,该文件即是证书文件,把他移动到{JAVA_HOME}/jre/lib/security目录下,然后重启tomcat即可生效
④例:cp jssecacerts /usr/local/jdk1.8.0_11/jre/lib/security/
3、后续问题,重启后再次安装插件,若出现
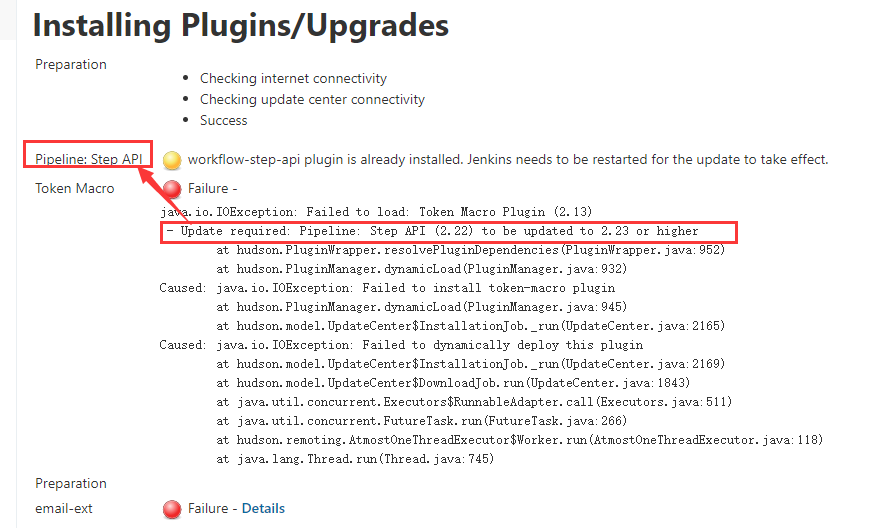
表示Pipeline: Step API插件需要更新到更高版本,而且上面已经提示更新成功,需要再次重启tomcat/jenkins
4、到此为止问题基本解决,后续安装插件后都需要重新才可生效。
5、问题适用场景【java服务访问远程服务需要证书】
引用:
https://blog.csdn.net/faye0412/article/details/6883879
https://www.cnblogs.com/zoro-zero/p/11607674.html



