Kubernetes系统安全-认证(Authentication)
Kubernetes系统安全-认证(Authentication)
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
一.Kubernetes 系统安全概述
1>.Kubernetes API Server的访问控制(Controlling Access)概述
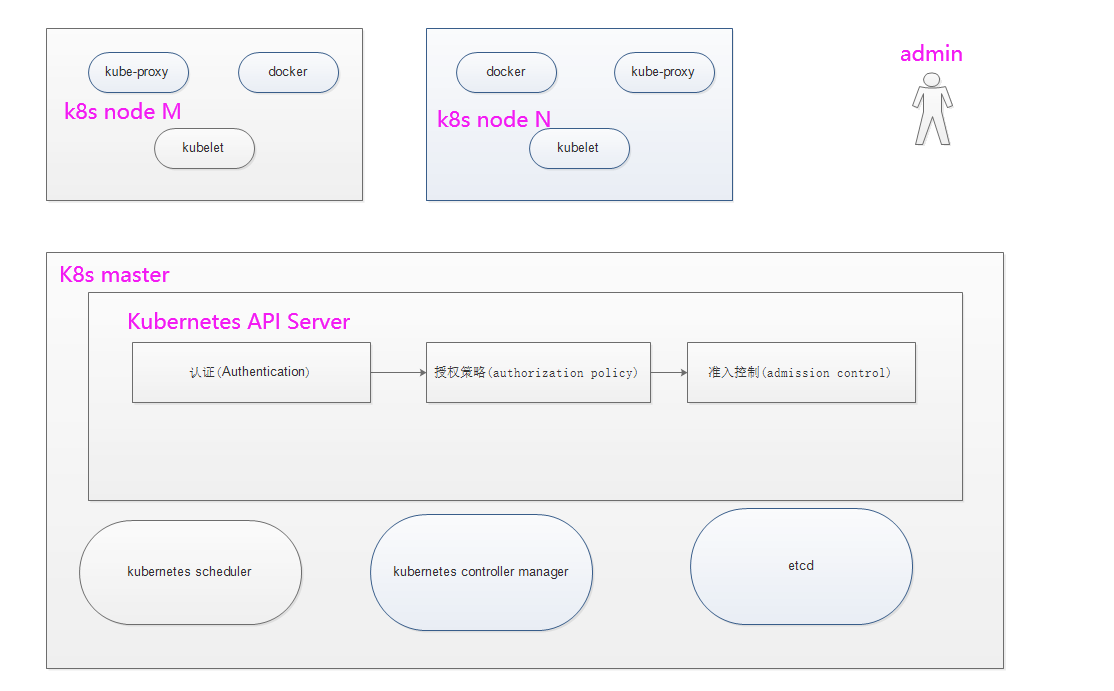
用户可以使用kubectl、客户端库或通过发出REST请求来访问API。 人工用户和Kubernetes服务帐户都可以被授权访问API。 当一个请求到达API时,API Server将通过认证(Authentication),授权策略(authorization policy),准入控制(admission control)三类插件来分别实现访问控制,如下图所示。 认证(Authentication):
验证客户端是否是API Server所认可的访问者。即需要账号密码登录。 授权策略(authorization policy):
通过认证后,需要基于资源的管理逻辑实现权限分配,说白了就是不同的用户登录拥有的权限是不同的。 准入控制(admission control):
功能一是检查客户端定义的资源是否合乎规范,如果合乎规范则按照客户端定义的规则执行,如果不合乎规范,例如缺少字段设置,则会自动补全字段的默认值。
功能二是验证用户的合法性,即检查用户的行为是否合法,默认值补全,比如经历过认证和授权策略可能客户端已经有创建Pod的权限,准入控制可以限制该客户端可以创建的Pod所申请的资源限制,比如CPU,内存,磁盘使用空间等。
2>.Kubernetes 认证(Authentication)
在典型的Kubernetes集群中,端口443上的API服务器。API服务器提供一个证书。一旦建立了TLS,HTTP请求就移动到身份验证步骤。 群集创建脚本或群集管理将API服务器配置为运行一个或多个身份验证器模型。 身份验证步骤的输入是整个HTTP请求,但是,它通常只检查头和/或客户端证书。
身份验证模块包括客户端证书(Client Certificates)、密码(Password)和普通令牌(Plain Tokens)、引导令牌(Bootstrap Tokens)和JWT令牌(用于服务帐户)。
可以指定多个身份验证模块,在这种情况下,依次尝试每个模块,直到其中一个成功为止。
如果请求无法通过身份验证,则会使用HTTP状态代码401拒绝该请求。
否则,用户将作为特定用户名进行身份验证,该用户名可供后续步骤在其决策中使用。
一些身份验证器还提供用户的组成员身份,而其他身份验证器则不提供。
3>.Kubernetes 授权策略(authorization policy)
紧随认证环节之后的是"授权"检查环境;一个常规请求必须在其请求报文中包含用户名,请求的动作以及目标对象;若存在某授权策略对于此请求给予了许可授权,即授权成功。 Kubernetes授权要求使用通用REST属性与现有的组织范围或云提供商范围的访问控制系统进行交互。 Kubernetes支持多种授权模块,如ABAC模式、RBAC模式和Webhook模式,当管理员创建集群时,他们配置了应该在API服务器中使用的授权模块。 如果配置了多个授权模块,Kubernetes将检查每个模块,如果有任何模块授权请求,则可以继续请求,如果所有模块拒绝请求,则拒绝请求(HTTP状态代码403)。 博主推荐阅读: https://www.cnblogs.com/yinzhengjie/p/12310192.html
4>.Kubernetes 准入控制(admission control)
博主推荐阅读:
5>.Kubernetes的用户
一个API请求要么以常规用户的身份进行,要么以某特定账号的身份进行,否则统一被视作匿名用户。换句话说,所有Kubernetes集群都有两类用户:由Kubernetes管理的服务帐户和普通(常规)用户。
普通(常规)用户(User Account,即有权限操作集群的用户):
常规用户被认为是由外部的独立服务管理的,换句话说,这个用户是给人用的,就好像Linux操作系统的普通用户,需要管理员手动创建。
一个分发私钥的管理员,一个类似Keystone或Google帐户的用户存储,甚至一个包含用户名和密码列表的文件。
在这方面,Kubernetes没有表示普通用户帐户的对象,普通用户不能通过API调用添加到集群中。
服务账号(Service Account):
服务帐户是由Kubernetes API管理的用户,换句话说,这个用户是给服务器上的守护进程使用的,就好像Linux操作系统的内置系统用户,基本上无需人工创建。
它们绑定到特定的名称空间,并由API服务器自动创建或通过API调用手动创建。
服务帐户绑定到存储为secert的一组凭据(一般是generic类型),这些凭据被装载到pods中,允许集群中的进程与Kubernetes API进行对话。
你们用户(Anoymous requests):
启用时,未被其他配置的身份验证方法拒绝的请求将被视为匿名请求,并为其指定用户名system:anonymous和一组system:unauthenticated。
在1.6+中,如果使用AlwaysLow以外的授权模式,则默认启用匿名访问,并且可以通过将--annonymous auth=false选项传递给API服务器来取消匿名访问。
从1.6开始,ABAC和RBAC授权程序要求对系统进行显式授权:匿名用户或系统:未经身份验证的组,因此授予对*用户或*组的访问权限的旧策略规则不包括匿名用户。
无论来自于Kubernetes集群内或集群外的任何进程的请求,都必须由API Server事先完成认证;常见的客户端进程包括:
(1)kube-scheduler
(2)kube-controller-manager
(3)kubectl
(4)kubelet
(5)kub-proxy
(6)Dashboard
(7)CoreDNS
(8)flannel
集群上运行于Pod中的进程认证时使用的账号即Service Account。
6>.Kubernetes集群组件间ssl/tls通信
kube-apiserver和etcd集群基于ssl/tls通信最少需要四个证书(此时kube-apiserver充当客户端): etcd-ca: etcd的自签证书。 Peer Cert: etcd集群数据同步所需的证书。 Serever key: 所有etcd公用同一套私钥证书。当然,你也可以每个etcd节点用一个服务端证书,那么客户端想要连接到对应的服务器需要使用相应的私钥进行认证。不过为了减少试验的复杂性,建议大家在etcd集群中使用一套私钥即可。 Client cert: 客户端的公钥证书,在Kubernetes集群中etcd的客户端就只有一个,那就是kube-apiserver。 kube-apiserver和Kubernetes集群的其它组件通信最少需要七个证书(此时kube-apiserver充当服务端): kubernetes-ca: 即kube-apiserver的自签证书。 kube-apiserver-key: kube-apiserver的私钥证书。 kube-apiserver Client cert: kube-apiserver的客户端证书,而且每个组件类型对应客户端证书的CN名称都不一样,因此每个组件都需要一个客户端证书,常见的有以下几个组件均需要配置证书: kubectl kube-controller-manager kube-scheduler kube-proxy kubelet kubelet API(注意哈,kubelet和kube-apiserver是双向的,kubelet连接kube-apiserver时需要做认证,而kube-apiserver指挥kubelet做操作时也需要被kubelet API进行认证,此时kube-apiserver充当kubelet API的客户端,该过程也需要证书认证的哟。) 自定义kube-apiserver相关的认证(尤其是前端页面的监控代理必须配置安全认证的): kube-apiserver内部是分层的,里面有一个kube-aggregator组件和kube-apiserver组件,默认情况下所有请求都是从kube-aggregator组件反向代理到内置的kube-apiserver。 由于Kubernetes开源的kube-apiserver内置的一些功能可能无法满足咱们的生产环境需求,比如自定义一些资源类型等。此时如果我们代码能力比较强的,完全可以使用Golang语言编写一套自定义的kube-apiserver,我们称之为扩展的apiserver,即extension-apiserver。
我们可以在kube-aggregtor组件上配置两个反向代理,一个是内置的kube-apiserver,另一个是咱们自己写的extension-apiserver,
综上所述,kube-aggregator和extension-apiserver组件通信最少需要3各证书:
front-prox-ca:
kube-apiserver内部框架自谦证书.
kube-aggregator-key:
kube-aggregator的私钥证书。
kube-extension-apiserver Cert:
kube-aggregator的客户端证书,此时需要做客户端认证的就只有咱们自定义的apiserver,默认的apiserver就无需认证了。
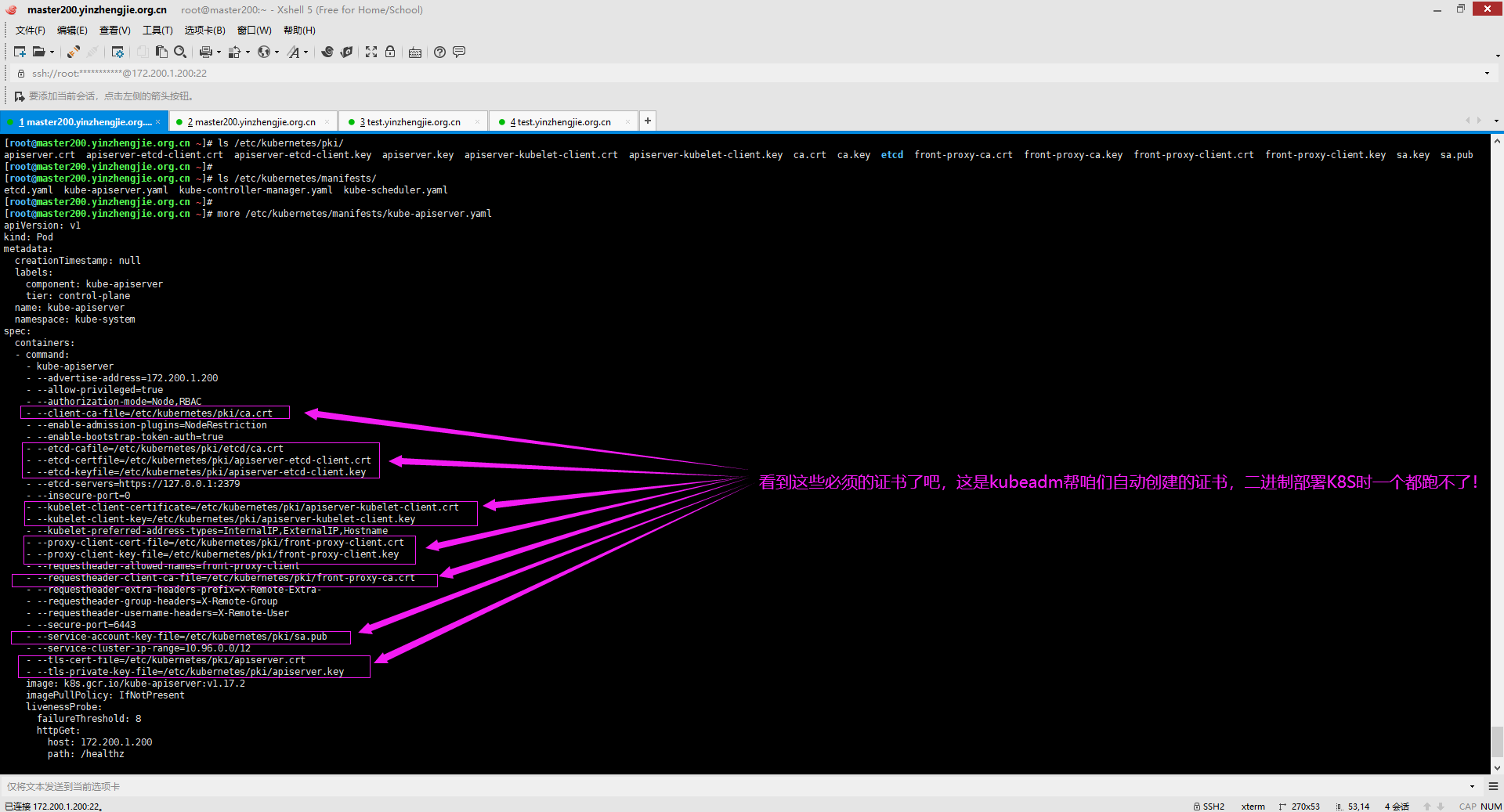
综上所述,kubernetes部署需要的证书文件可真不少啊,好在我们使用了kubeadm帮咱们部署的k8s集群,的确少了不少事情哟~如下图所示,都是kubeadm帮咱们自动创建的证书文件,不过这样为后期部署二进制K8S埋下伏笔,倒是该配置的证书一个都少不了。
二.kubeconfig文件相关概述
1>.kubeconfig文件的作用
kubeconfig文件是与kubectl命令行工具(或其他客户端)一起使用时用于配置对Kubernetes的访问的文件。 使用kubeconfig文件组织有关群集、用户、命名空间和身份验证机制的信息。 kubectl命令行工具使用kubeconfig文件来查找选择集群并与集群的API服务器通信所需的信息。 可以通过设置kubeconfig环境变量或设置--kubeconfig标志来指定其他kubeconfig文件,如果不指定默认是"~/.kube/config"

[root@master200.yinzhengjie.org.cn ~]# kubectl config -h Modify kubeconfig files using subcommands like "kubectl config set current-context my-context" The loading order follows these rules: 1. If the --kubeconfig flag is set, then only that file is loaded. The flag may only be set once and no merging takes place. 2. If $KUBECONFIG environment variable is set, then it is used as a list of paths (normal path delimiting rules for your system). These paths are merged. When a value is modified, it is modified in the file that defines the stanza. When a value is created, it is created in the first file that exists. If no files in the chain exist, then it creates the last file in the list. 3. Otherwise, ${HOME}/.kube/config is used and no merging takes place. Available Commands: current-context Displays the current-context delete-cluster Delete the specified cluster from the kubeconfig delete-context Delete the specified context from the kubeconfig get-clusters Display clusters defined in the kubeconfig get-contexts Describe one or many contexts rename-context Renames a context from the kubeconfig file. set Sets an individual value in a kubeconfig file set-cluster Sets a cluster entry in kubeconfig set-context Sets a context entry in kubeconfig set-credentials Sets a user entry in kubeconfig unset Unsets an individual value in a kubeconfig file use-context Sets the current-context in a kubeconfig file view Display merged kubeconfig settings or a specified kubeconfig file Usage: kubectl config SUBCOMMAND [options] Use "kubectl <command> --help" for more information about a given command. Use "kubectl options" for a list of global command-line options (applies to all commands). [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# cat ~/.kube/config apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01ESXdOREV4TXpreE1sb1hEVE13TURJd01URXhNemt4TWxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0 FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTGZMCm1hcDRJVkt4YWFLdFY0c2lDdFp0dWVRczJGWWE0RVlWTGI1c1lSWUtZSUI4YnRRdExpMXVUMWw2QnBxcWIwQ3oKbCtaMVBIN0doRHBiR014NkEzYUYyOVEycFo1NnVVc0tiWTIwZGVIWVZmeFZEek40c0ZwSGF0a25nelNEVGxVTgpoUTgrd004amxnT0k0TTR6NENXY3ZnZUJ0cXZSaTFRYVZaRzRZYm5kZ3AzMVVLRHRsR1ljbzJZK21jY3AxL0VKClJHQ1NmTUt0aFpRMnpMZ1c3RG4rdzc5YkdZbjhXRU5MOGlVZ3dwa3dyY2ZRTngwa2dUNzZXQjFZQnJSc2V5R1IKZTFRcUgyNEpqdHRpRU1aME8zZ0x4UCsvWXRiWDJlbkZUa3VCVTlJZVQzb0Rvc0FDcVdrOGsyR1p6RW5VZHNENAppcmhLUFlDMHlJRHJwLzY0NnFFQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFFQmgzSEtZOHBqbndrcmx3d1NaQmdJT2x5NzAKZTR3UXk3c3BCL0tKdW1TdG9uY1ZTd2JLRHpiQm5vWmlBcWVWbFpFU0IxWnYwZEdUVmJmZ21MYkwvU1B0NHovNgpNczhUMVFERW9kalJ1dlI0M0RSd0phR2xENHh4cDh2d0o0TysrQ0tITUNKck54OHVKbTFXODBzOEJXbnNxNytQCkQxMEVOZ2JzZHVXZ3NXMjNJNmM0WVB0dCtHeEE0S2wxalVkZGcydFIyNFo5eHNhRHdXRGoxZUg2a2xNcXpqaEYKc295Qk0vODFkWnllbzdzUDh1WGl1MkRUVkpVWWFEV005VzY3TlRSRWZ6TndUbTh2bUFjSjJlVG9lR3Z1MC96RApPejVDSWVsbWJZaVUvclVLVFNNdm0reFlOOFRGVkRmVFVQMHY0cHB2QjBmL2RIQThMTVBRYnhldVJKOD0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= server: https://172.200.1.200:6443 name: kubernetes contexts: - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: kubernetes-admin user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM4akNDQWRxZ0F3SUJBZ0lJQ3NaaEJqaDJyWjB3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TURBeU1EUXhNVE01TVRKYUZ3MHlNVEF5TURNeE1UTTVNVFJhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUc HRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXdwL21nTndmcGJnVlJqUHIKaUF0Y25DeHZBZWh6S2ZjdlhWWEtMOWlKRERFWGFNT0lVVUt5U3JZNlhDOGh2a2xyY0puWGZQRk9WelpoVUk5cgpsbzVCa2UzUm5xbDRrT1pFeDNOejUyeTdpdEhPZHpIa2N1dEpoWjN0c0V5ck9qWlI4aHhxNlZ6eHcvWXpmemJSCmk2VTVEZ0lNQUxKbXoydWErdXVPYlhtcDlHNzhGWGxPdXQ0VFpKM1BkNUxOQWhwYWJnMlZuV0x4dXlTekNEaC8KU3FpMS9ua3d0WTdmYnR3dkNaN2J4eGF0OFpIZXF3cVJUSE9WdnBHaWZDNDV4Sjh5SUs3dzFrc0JqemtXYnhubwpBbU90TzBxM2ZnQ2JnVTF4L05Fc2NvVjJXMi91MnFqdXFIUnZUTEwra3hmbW1OcFBwVFJpMUJqNEFwYXF3eEFZCitVdGRXd0lEQVFBQm95Y3dKVEFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFCOHhmbVdUT1JGVE5yUVJDeVA4V1lUZFRzV1BWQ2R6TFZWdApEMWpOSGZWMkxreXB4bFFGZml2MHpnMFg1UHpkbUNnQXU0V3JVQjlUZGkvQU1zOTRPT1ozZUFmeGR1VDZFdVBHCkdmNm5OVXFOWlpIR3Z3NkpPeldNbUFCQzhxN3VQUHo3cWFOa0FFaDdwS1diMDE4cTFBRFdiYlVtRzhVMW1qOVgKQStnNDRoVVRTYlRKanVMaDFRMVVnbTNtbEZTZmM0VWZ5bDlheWlsQ2dXSXZlTU1TeFRyWDcvbGpSR2hLUUVaNgphcnVuMnVIbEIrODJIZ1NOZE9xdGhLaWlTZFBBZ2c2dDEvWTNxelZ1bmlSN01GdFNjSWkzQWxCeTJQdXE0cUpZCkJ6b3NMUitqclZGSitLUWx1TDlPTVVBUU5hZFd4OWpsUFBUK0VMazFkS0FCTDNRZTBQST0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBd3AvbWdOd2ZwYmdWUmpQcmlBdGNuQ3h2QWVoektmY3ZYVlhLTDlpSkRERVhhTU9JClVVS3lTclk2WEM4aHZrbHJjSm5YZlBGT1Z6WmhVSTlybG81QmtlM1JucWw0a09aRXgzTno1Mnk3aXRIT2R6SGsKY3V0SmhaM3RzRXlyT2paUjhoeHE2Vnp4d y9ZemZ6YlJpNlU1RGdJTUFMSm16MnVhK3V1T2JYbXA5Rzc4RlhsTwp1dDRUWkozUGQ1TE5BaHBhYmcyVm5XTHh1eVN6Q0RoL1NxaTEvbmt3dFk3ZmJ0d3ZDWjdieHhhdDhaSGVxd3FSClRIT1Z2cEdpZkM0NXhKOHlJSzd3MWtzQmp6a1dieG5vQW1PdE8wcTNmZ0NiZ1UxeC9ORXNjb1YyVzIvdTJxanUKcUhSdlRMTCtreGZtbU5wUHBUUmkxQmo0QXBhcXd4QVkrVXRkV3dJREFRQUJBb0lCQVFDVWNpZjdVMnBrR1ROSQoxNk1ub2hyaUY5WVhxM2ZqbzJFaUhLUlp1QnhZQ3oyaXI3bFMyYjlwMHZKU2k3UitFanY3cDZ1LzVjSHVMVkV1CmhDWDRzTXA4aHR0aTNEcFVzdjMwN3krUmJkTGlBRU10a1FXQlRjdEhPZjBvZ21IN3hhRGRQU1dpbHp6a1RlNWIKY3JHRGhPTXV0d3Iyb1J4Znl1QnIwSzFTL1FCUHFkNUNiL3hXU0tScWlDNjUrTGVsK0phQTEvL01ZcUtNUFlNNQplVHVjNVhhdWl6a0Y4K1pVTS9KMXNKVm5QR3VpR0VTR2NhRUlhTVY5bHc5ZC9OMDFwNnVuK255STY3NVJ2TlowCkszSlJoZ0tjNGxPTlpyb0dHS1dwOVloNnU2U2dZdWVYcUU2SUVyVnNvbzJDYWJ1dVJpTDhPM3hQOERJR2hQc1oKRjlmWEY2K1pBb0dCQU8xQXpTa0hNSWJISjduRFcwY250dVdaMUQyN29aajJ2RTZMbmprV0Fia3pkaXhSdGc0YQpmWnVOOTRpZUJSMzFEKy9QclM4WVkxTzdNOVhYaGdBN3BXcC80MnVYY0xFdGpGbUt1MFE5NHZGMnMvcGV2WDVhCncwdFkrNXFSaEliZytHU0tSZGZacHU4dCsreVVIZFVWcTFoYTVIaTVyb0ExWXh6RHJJdzE4SEF0QW9HQkFOSUEKelR6RENDTU5wV1pCc1A5bmhBMGNEWi9UQ01vbmRZcXVnMFllTWVLZ3lzR2tqM3ZoTHlUaEpkOWFTUmF1QzB5aApSSUhCZFpnYkl3V25VdnY2cDQ0alNTb2oyMWptcGpwSVg5c28rZ0dDd1NHRENOWUlFY1VvVG9Yd2ttWmhWQ2c0CjVySXoweXdmamgxQXU4V2xIa3R5ZmVGNHVQMEkwdXJIeUNER2FQQ25Bb0dCQU5jcXFlWEhxMjdRTjJyMWpWYWUKNGZTZzZpZUNmeS9tdFNqVzNvd1BOVWp0THdOS3A3MXFzUGZlYk52dDA5NHpYbHl6RC9GaVFOS3pPSE43bnYrZgpHSW5acWpydGdUcHVnSmJFaHNtQkJzek9Sck9PTUhUamc3SlY1UGx0ZDYrTFlEcHVYS0ZCdDIrN1dIcGFhaVBTCkh5OW1YMFpOdjhCdXFwQnZ0WkVEYWllUkFvR0FTeXJpUzVkN3VDQlFUYlBCeVFtaWFKYmNBWk1tR0VYYmV0SlEKUnE3VUtFeHBocnFDYVZNRzd1cHdCZXhwTU9jSFFGeVJDdWpXVUtXVitaWVV6QURDTE14UWlmYmZzb2lNZzF3WQpnM2U5VlFFYVpBWmxDVWRHSlEzeVhWcm83Q0IyWVJkTTdBaEUxQXhQY0FVVnNQOFRRdW91U0tCUGhySzczREc2ClhwRG1TdzBDZ1lFQTZDYW9HcnZVL21CTjNuSkp2bk41NGVtTGxkbVhGak1MQ2UraDA1RjFxSXVWT3VyQm1lbkEKMlhKMng0bFN6ODJBbVoxeTAxc1JMVXJWVGxJbWxkbW9Ldm92VmJETHMvSmZOUkRTQTFBTjY4ZzFNK0c3QVpNOQppaUNMTmFWS01ncUE0d3JlS2JieUROaGhuSjRjVGQwaWU2eTRLVUJvaFhnTXl4K2FnWUZwQnpNPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=[root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
2>.查看kubeconfig的配置文件格式
一个kubeconfig文件是YAML格式的配置文件,它通常由以下几个配置段组成: users: 用户账号及其认证信息列表。 cluster: 目标集群列表。 contexts: 以哪个user接入哪个cluster的连接组合。 curren-context: 当前使用的context。

[root@master200.yinzhengjie.org.cn ~]# cat /etc/kubernetes/admin.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01ESXdOREV4TXpreE1sb1hEVE13TURJd01URXhNemt4TWxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0 FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTGZMCm1hcDRJVkt4YWFLdFY0c2lDdFp0dWVRczJGWWE0RVlWTGI1c1lSWUtZSUI4YnRRdExpMXVUMWw2QnBxcWIwQ3oKbCtaMVBIN0doRHBiR014NkEzYUYyOVEycFo1NnVVc0tiWTIwZGVIWVZmeFZEek40c0ZwSGF0a25nelNEVGxVTgpoUTgrd004amxnT0k0TTR6NENXY3ZnZUJ0cXZSaTFRYVZaRzRZYm5kZ3AzMVVLRHRsR1ljbzJZK21jY3AxL0VKClJHQ1NmTUt0aFpRMnpMZ1c3RG4rdzc5YkdZbjhXRU5MOGlVZ3dwa3dyY2ZRTngwa2dUNzZXQjFZQnJSc2V5R1IKZTFRcUgyNEpqdHRpRU1aME8zZ0x4UCsvWXRiWDJlbkZUa3VCVTlJZVQzb0Rvc0FDcVdrOGsyR1p6RW5VZHNENAppcmhLUFlDMHlJRHJwLzY0NnFFQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFFQmgzSEtZOHBqbndrcmx3d1NaQmdJT2x5NzAKZTR3UXk3c3BCL0tKdW1TdG9uY1ZTd2JLRHpiQm5vWmlBcWVWbFpFU0IxWnYwZEdUVmJmZ21MYkwvU1B0NHovNgpNczhUMVFERW9kalJ1dlI0M0RSd0phR2xENHh4cDh2d0o0TysrQ0tITUNKck54OHVKbTFXODBzOEJXbnNxNytQCkQxMEVOZ2JzZHVXZ3NXMjNJNmM0WVB0dCtHeEE0S2wxalVkZGcydFIyNFo5eHNhRHdXRGoxZUg2a2xNcXpqaEYKc295Qk0vODFkWnllbzdzUDh1WGl1MkRUVkpVWWFEV005VzY3TlRSRWZ6TndUbTh2bUFjSjJlVG9lR3Z1MC96RApPejVDSWVsbWJZaVUvclVLVFNNdm0reFlOOFRGVkRmVFVQMHY0cHB2QjBmL2RIQThMTVBRYnhldVJKOD0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= server: https://172.200.1.200:6443 name: kubernetes contexts: - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: kubernetes-admin user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM4akNDQWRxZ0F3SUJBZ0lJQ3NaaEJqaDJyWjB3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TURBeU1EUXhNVE01TVRKYUZ3MHlNVEF5TURNeE1UTTVNVFJhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUc HRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXdwL21nTndmcGJnVlJqUHIKaUF0Y25DeHZBZWh6S2ZjdlhWWEtMOWlKRERFWGFNT0lVVUt5U3JZNlhDOGh2a2xyY0puWGZQRk9WelpoVUk5cgpsbzVCa2UzUm5xbDRrT1pFeDNOejUyeTdpdEhPZHpIa2N1dEpoWjN0c0V5ck9qWlI4aHhxNlZ6eHcvWXpmemJSCmk2VTVEZ0lNQUxKbXoydWErdXVPYlhtcDlHNzhGWGxPdXQ0VFpKM1BkNUxOQWhwYWJnMlZuV0x4dXlTekNEaC8KU3FpMS9ua3d0WTdmYnR3dkNaN2J4eGF0OFpIZXF3cVJUSE9WdnBHaWZDNDV4Sjh5SUs3dzFrc0JqemtXYnhubwpBbU90TzBxM2ZnQ2JnVTF4L05Fc2NvVjJXMi91MnFqdXFIUnZUTEwra3hmbW1OcFBwVFJpMUJqNEFwYXF3eEFZCitVdGRXd0lEQVFBQm95Y3dKVEFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFCOHhmbVdUT1JGVE5yUVJDeVA4V1lUZFRzV1BWQ2R6TFZWdApEMWpOSGZWMkxreXB4bFFGZml2MHpnMFg1UHpkbUNnQXU0V3JVQjlUZGkvQU1zOTRPT1ozZUFmeGR1VDZFdVBHCkdmNm5OVXFOWlpIR3Z3NkpPeldNbUFCQzhxN3VQUHo3cWFOa0FFaDdwS1diMDE4cTFBRFdiYlVtRzhVMW1qOVgKQStnNDRoVVRTYlRKanVMaDFRMVVnbTNtbEZTZmM0VWZ5bDlheWlsQ2dXSXZlTU1TeFRyWDcvbGpSR2hLUUVaNgphcnVuMnVIbEIrODJIZ1NOZE9xdGhLaWlTZFBBZ2c2dDEvWTNxelZ1bmlSN01GdFNjSWkzQWxCeTJQdXE0cUpZCkJ6b3NMUitqclZGSitLUWx1TDlPTVVBUU5hZFd4OWpsUFBUK0VMazFkS0FCTDNRZTBQST0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBd3AvbWdOd2ZwYmdWUmpQcmlBdGNuQ3h2QWVoektmY3ZYVlhLTDlpSkRERVhhTU9JClVVS3lTclk2WEM4aHZrbHJjSm5YZlBGT1Z6WmhVSTlybG81QmtlM1JucWw0a09aRXgzTno1Mnk3aXRIT2R6SGsKY3V0SmhaM3RzRXlyT2paUjhoeHE2Vnp4d y9ZemZ6YlJpNlU1RGdJTUFMSm16MnVhK3V1T2JYbXA5Rzc4RlhsTwp1dDRUWkozUGQ1TE5BaHBhYmcyVm5XTHh1eVN6Q0RoL1NxaTEvbmt3dFk3ZmJ0d3ZDWjdieHhhdDhaSGVxd3FSClRIT1Z2cEdpZkM0NXhKOHlJSzd3MWtzQmp6a1dieG5vQW1PdE8wcTNmZ0NiZ1UxeC9ORXNjb1YyVzIvdTJxanUKcUhSdlRMTCtreGZtbU5wUHBUUmkxQmo0QXBhcXd4QVkrVXRkV3dJREFRQUJBb0lCQVFDVWNpZjdVMnBrR1ROSQoxNk1ub2hyaUY5WVhxM2ZqbzJFaUhLUlp1QnhZQ3oyaXI3bFMyYjlwMHZKU2k3UitFanY3cDZ1LzVjSHVMVkV1CmhDWDRzTXA4aHR0aTNEcFVzdjMwN3krUmJkTGlBRU10a1FXQlRjdEhPZjBvZ21IN3hhRGRQU1dpbHp6a1RlNWIKY3JHRGhPTXV0d3Iyb1J4Znl1QnIwSzFTL1FCUHFkNUNiL3hXU0tScWlDNjUrTGVsK0phQTEvL01ZcUtNUFlNNQplVHVjNVhhdWl6a0Y4K1pVTS9KMXNKVm5QR3VpR0VTR2NhRUlhTVY5bHc5ZC9OMDFwNnVuK255STY3NVJ2TlowCkszSlJoZ0tjNGxPTlpyb0dHS1dwOVloNnU2U2dZdWVYcUU2SUVyVnNvbzJDYWJ1dVJpTDhPM3hQOERJR2hQc1oKRjlmWEY2K1pBb0dCQU8xQXpTa0hNSWJISjduRFcwY250dVdaMUQyN29aajJ2RTZMbmprV0Fia3pkaXhSdGc0YQpmWnVOOTRpZUJSMzFEKy9QclM4WVkxTzdNOVhYaGdBN3BXcC80MnVYY0xFdGpGbUt1MFE5NHZGMnMvcGV2WDVhCncwdFkrNXFSaEliZytHU0tSZGZacHU4dCsreVVIZFVWcTFoYTVIaTVyb0ExWXh6RHJJdzE4SEF0QW9HQkFOSUEKelR6RENDTU5wV1pCc1A5bmhBMGNEWi9UQ01vbmRZcXVnMFllTWVLZ3lzR2tqM3ZoTHlUaEpkOWFTUmF1QzB5aApSSUhCZFpnYkl3V25VdnY2cDQ0alNTb2oyMWptcGpwSVg5c28rZ0dDd1NHRENOWUlFY1VvVG9Yd2ttWmhWQ2c0CjVySXoweXdmamgxQXU4V2xIa3R5ZmVGNHVQMEkwdXJIeUNER2FQQ25Bb0dCQU5jcXFlWEhxMjdRTjJyMWpWYWUKNGZTZzZpZUNmeS9tdFNqVzNvd1BOVWp0THdOS3A3MXFzUGZlYk52dDA5NHpYbHl6RC9GaVFOS3pPSE43bnYrZgpHSW5acWpydGdUcHVnSmJFaHNtQkJzek9Sck9PTUhUamc3SlY1UGx0ZDYrTFlEcHVYS0ZCdDIrN1dIcGFhaVBTCkh5OW1YMFpOdjhCdXFwQnZ0WkVEYWllUkFvR0FTeXJpUzVkN3VDQlFUYlBCeVFtaWFKYmNBWk1tR0VYYmV0SlEKUnE3VUtFeHBocnFDYVZNRzd1cHdCZXhwTU9jSFFGeVJDdWpXVUtXVitaWVV6QURDTE14UWlmYmZzb2lNZzF3WQpnM2U5VlFFYVpBWmxDVWRHSlEzeVhWcm83Q0IyWVJkTTdBaEUxQXhQY0FVVnNQOFRRdW91U0tCUGhySzczREc2ClhwRG1TdzBDZ1lFQTZDYW9HcnZVL21CTjNuSkp2bk41NGVtTGxkbVhGak1MQ2UraDA1RjFxSXVWT3VyQm1lbkEKMlhKMng0bFN6ODJBbVoxeTAxc1JMVXJWVGxJbWxkbW9Ldm92VmJETHMvSmZOUkRTQTFBTjY4ZzFNK0c3QVpNOQppaUNMTmFWS01ncUE0d3JlS2JieUROaGhuSjRjVGQwaWU2eTRLVUJvaFhnTXl4K2FnWUZwQnpNPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=[root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
3>.使用命令行管理kubeconfg文件信息

[root@master200.yinzhengjie.org.cn ~]# cat /etc/kubernetes/admin.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01ESXdOREV4TXpreE1sb1hEVE13TURJd01URXhNemt4TWxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0 FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTGZMCm1hcDRJVkt4YWFLdFY0c2lDdFp0dWVRczJGWWE0RVlWTGI1c1lSWUtZSUI4YnRRdExpMXVUMWw2QnBxcWIwQ3oKbCtaMVBIN0doRHBiR014NkEzYUYyOVEycFo1NnVVc0tiWTIwZGVIWVZmeFZEek40c0ZwSGF0a25nelNEVGxVTgpoUTgrd004amxnT0k0TTR6NENXY3ZnZUJ0cXZSaTFRYVZaRzRZYm5kZ3AzMVVLRHRsR1ljbzJZK21jY3AxL0VKClJHQ1NmTUt0aFpRMnpMZ1c3RG4rdzc5YkdZbjhXRU5MOGlVZ3dwa3dyY2ZRTngwa2dUNzZXQjFZQnJSc2V5R1IKZTFRcUgyNEpqdHRpRU1aME8zZ0x4UCsvWXRiWDJlbkZUa3VCVTlJZVQzb0Rvc0FDcVdrOGsyR1p6RW5VZHNENAppcmhLUFlDMHlJRHJwLzY0NnFFQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFFQmgzSEtZOHBqbndrcmx3d1NaQmdJT2x5NzAKZTR3UXk3c3BCL0tKdW1TdG9uY1ZTd2JLRHpiQm5vWmlBcWVWbFpFU0IxWnYwZEdUVmJmZ21MYkwvU1B0NHovNgpNczhUMVFERW9kalJ1dlI0M0RSd0phR2xENHh4cDh2d0o0TysrQ0tITUNKck54OHVKbTFXODBzOEJXbnNxNytQCkQxMEVOZ2JzZHVXZ3NXMjNJNmM0WVB0dCtHeEE0S2wxalVkZGcydFIyNFo5eHNhRHdXRGoxZUg2a2xNcXpqaEYKc295Qk0vODFkWnllbzdzUDh1WGl1MkRUVkpVWWFEV005VzY3TlRSRWZ6TndUbTh2bUFjSjJlVG9lR3Z1MC96RApPejVDSWVsbWJZaVUvclVLVFNNdm0reFlOOFRGVkRmVFVQMHY0cHB2QjBmL2RIQThMTVBRYnhldVJKOD0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= server: https://172.200.1.200:6443 name: kubernetes contexts: - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: kubernetes-admin user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM4akNDQWRxZ0F3SUJBZ0lJQ3NaaEJqaDJyWjB3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TURBeU1EUXhNVE01TVRKYUZ3MHlNVEF5TURNeE1UTTVNVFJhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUc HRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXdwL21nTndmcGJnVlJqUHIKaUF0Y25DeHZBZWh6S2ZjdlhWWEtMOWlKRERFWGFNT0lVVUt5U3JZNlhDOGh2a2xyY0puWGZQRk9WelpoVUk5cgpsbzVCa2UzUm5xbDRrT1pFeDNOejUyeTdpdEhPZHpIa2N1dEpoWjN0c0V5ck9qWlI4aHhxNlZ6eHcvWXpmemJSCmk2VTVEZ0lNQUxKbXoydWErdXVPYlhtcDlHNzhGWGxPdXQ0VFpKM1BkNUxOQWhwYWJnMlZuV0x4dXlTekNEaC8KU3FpMS9ua3d0WTdmYnR3dkNaN2J4eGF0OFpIZXF3cVJUSE9WdnBHaWZDNDV4Sjh5SUs3dzFrc0JqemtXYnhubwpBbU90TzBxM2ZnQ2JnVTF4L05Fc2NvVjJXMi91MnFqdXFIUnZUTEwra3hmbW1OcFBwVFJpMUJqNEFwYXF3eEFZCitVdGRXd0lEQVFBQm95Y3dKVEFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFCOHhmbVdUT1JGVE5yUVJDeVA4V1lUZFRzV1BWQ2R6TFZWdApEMWpOSGZWMkxreXB4bFFGZml2MHpnMFg1UHpkbUNnQXU0V3JVQjlUZGkvQU1zOTRPT1ozZUFmeGR1VDZFdVBHCkdmNm5OVXFOWlpIR3Z3NkpPeldNbUFCQzhxN3VQUHo3cWFOa0FFaDdwS1diMDE4cTFBRFdiYlVtRzhVMW1qOVgKQStnNDRoVVRTYlRKanVMaDFRMVVnbTNtbEZTZmM0VWZ5bDlheWlsQ2dXSXZlTU1TeFRyWDcvbGpSR2hLUUVaNgphcnVuMnVIbEIrODJIZ1NOZE9xdGhLaWlTZFBBZ2c2dDEvWTNxelZ1bmlSN01GdFNjSWkzQWxCeTJQdXE0cUpZCkJ6b3NMUitqclZGSitLUWx1TDlPTVVBUU5hZFd4OWpsUFBUK0VMazFkS0FCTDNRZTBQST0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBd3AvbWdOd2ZwYmdWUmpQcmlBdGNuQ3h2QWVoektmY3ZYVlhLTDlpSkRERVhhTU9JClVVS3lTclk2WEM4aHZrbHJjSm5YZlBGT1Z6WmhVSTlybG81QmtlM1JucWw0a09aRXgzTno1Mnk3aXRIT2R6SGsKY3V0SmhaM3RzRXlyT2paUjhoeHE2Vnp4d y9ZemZ6YlJpNlU1RGdJTUFMSm16MnVhK3V1T2JYbXA5Rzc4RlhsTwp1dDRUWkozUGQ1TE5BaHBhYmcyVm5XTHh1eVN6Q0RoL1NxaTEvbmt3dFk3ZmJ0d3ZDWjdieHhhdDhaSGVxd3FSClRIT1Z2cEdpZkM0NXhKOHlJSzd3MWtzQmp6a1dieG5vQW1PdE8wcTNmZ0NiZ1UxeC9ORXNjb1YyVzIvdTJxanUKcUhSdlRMTCtreGZtbU5wUHBUUmkxQmo0QXBhcXd4QVkrVXRkV3dJREFRQUJBb0lCQVFDVWNpZjdVMnBrR1ROSQoxNk1ub2hyaUY5WVhxM2ZqbzJFaUhLUlp1QnhZQ3oyaXI3bFMyYjlwMHZKU2k3UitFanY3cDZ1LzVjSHVMVkV1CmhDWDRzTXA4aHR0aTNEcFVzdjMwN3krUmJkTGlBRU10a1FXQlRjdEhPZjBvZ21IN3hhRGRQU1dpbHp6a1RlNWIKY3JHRGhPTXV0d3Iyb1J4Znl1QnIwSzFTL1FCUHFkNUNiL3hXU0tScWlDNjUrTGVsK0phQTEvL01ZcUtNUFlNNQplVHVjNVhhdWl6a0Y4K1pVTS9KMXNKVm5QR3VpR0VTR2NhRUlhTVY5bHc5ZC9OMDFwNnVuK255STY3NVJ2TlowCkszSlJoZ0tjNGxPTlpyb0dHS1dwOVloNnU2U2dZdWVYcUU2SUVyVnNvbzJDYWJ1dVJpTDhPM3hQOERJR2hQc1oKRjlmWEY2K1pBb0dCQU8xQXpTa0hNSWJISjduRFcwY250dVdaMUQyN29aajJ2RTZMbmprV0Fia3pkaXhSdGc0YQpmWnVOOTRpZUJSMzFEKy9QclM4WVkxTzdNOVhYaGdBN3BXcC80MnVYY0xFdGpGbUt1MFE5NHZGMnMvcGV2WDVhCncwdFkrNXFSaEliZytHU0tSZGZacHU4dCsreVVIZFVWcTFoYTVIaTVyb0ExWXh6RHJJdzE4SEF0QW9HQkFOSUEKelR6RENDTU5wV1pCc1A5bmhBMGNEWi9UQ01vbmRZcXVnMFllTWVLZ3lzR2tqM3ZoTHlUaEpkOWFTUmF1QzB5aApSSUhCZFpnYkl3V25VdnY2cDQ0alNTb2oyMWptcGpwSVg5c28rZ0dDd1NHRENOWUlFY1VvVG9Yd2ttWmhWQ2c0CjVySXoweXdmamgxQXU4V2xIa3R5ZmVGNHVQMEkwdXJIeUNER2FQQ25Bb0dCQU5jcXFlWEhxMjdRTjJyMWpWYWUKNGZTZzZpZUNmeS9tdFNqVzNvd1BOVWp0THdOS3A3MXFzUGZlYk52dDA5NHpYbHl6RC9GaVFOS3pPSE43bnYrZgpHSW5acWpydGdUcHVnSmJFaHNtQkJzek9Sck9PTUhUamc3SlY1UGx0ZDYrTFlEcHVYS0ZCdDIrN1dIcGFhaVBTCkh5OW1YMFpOdjhCdXFwQnZ0WkVEYWllUkFvR0FTeXJpUzVkN3VDQlFUYlBCeVFtaWFKYmNBWk1tR0VYYmV0SlEKUnE3VUtFeHBocnFDYVZNRzd1cHdCZXhwTU9jSFFGeVJDdWpXVUtXVitaWVV6QURDTE14UWlmYmZzb2lNZzF3WQpnM2U5VlFFYVpBWmxDVWRHSlEzeVhWcm83Q0IyWVJkTTdBaEUxQXhQY0FVVnNQOFRRdW91U0tCUGhySzczREc2ClhwRG1TdzBDZ1lFQTZDYW9HcnZVL21CTjNuSkp2bk41NGVtTGxkbVhGak1MQ2UraDA1RjFxSXVWT3VyQm1lbkEKMlhKMng0bFN6ODJBbVoxeTAxc1JMVXJWVGxJbWxkbW9Ldm92VmJETHMvSmZOUkRTQTFBTjY4ZzFNK0c3QVpNOQppaUNMTmFWS01ncUE0d3JlS2JieUROaGhuSjRjVGQwaWU2eTRLVUJvaFhnTXl4K2FnWUZwQnpNPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=[root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl --kubeconfig=/etc/kubernetes/admin.conf config view apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:6443 name: kubernetes contexts: - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: kubernetes-admin user: client-certificate-data: REDACTED client-key-data: REDACTED [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl --kubeconfig=/etc/kubernetes/admin.conf config view apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:6443 name: kubernetes contexts: - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: kubernetes-admin user: client-certificate-data: REDACTED client-key-data: REDACTED [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl --kubeconfig=/etc/kubernetes/admin.conf config get-clusters NAME kubernetes [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl --kubeconfig=/etc/kubernetes/admin.conf config view apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:6443 name: kubernetes contexts: - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: kubernetes-admin user: client-certificate-data: REDACTED client-key-data: REDACTED [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl --kubeconfig=/etc/kubernetes/admin.conf config get-contexts CURRENT NAME CLUSTER AUTHINFO NAMESPACE * kubernetes-admin@kubernetes kubernetes kubernetes-admin [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl --kubeconfig=/etc/kubernetes/admin.conf config get-contexts CURRENT NAME CLUSTER AUTHINFO NAMESPACE * kubernetes-admin@kubernetes kubernetes kubernetes-admin [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl --kubeconfig=/etc/kubernetes/admin.conf config current-context kubernetes-admin@kubernetes [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
三.自定义常规用户(User Account)实战案例
1>. 创建私钥

[root@master200.yinzhengjie.org.cn ~]# ll /etc/kubernetes/pki/ total 56 -rw-r--r-- 1 root root 1253 Feb 4 19:39 apiserver.crt -rw-r--r-- 1 root root 1090 Feb 4 19:39 apiserver-etcd-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-etcd-client.key -rw------- 1 root root 1679 Feb 4 19:39 apiserver.key -rw-r--r-- 1 root root 1099 Feb 4 19:39 apiserver-kubelet-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-kubelet-client.key -rw-r--r-- 1 root root 1025 Feb 4 19:39 ca.crt -rw------- 1 root root 1675 Feb 4 19:39 ca.key drwxr-xr-x 2 root root 162 Feb 4 19:39 etcd -rw-r--r-- 1 root root 1038 Feb 4 19:39 front-proxy-ca.crt -rw------- 1 root root 1679 Feb 4 19:39 front-proxy-ca.key -rw-r--r-- 1 root root 1058 Feb 4 19:39 front-proxy-client.crt -rw------- 1 root root 1675 Feb 4 19:39 front-proxy-client.key -rw------- 1 root root 1679 Feb 4 19:39 sa.key -rw------- 1 root root 451 Feb 4 19:39 sa.pub [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cd /etc/kubernetes/pki/ [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# openssl genrsa -out jason.key 4096 Generating RSA private key, 4096 bit long modulus .....................................................................................................................................................................++ ..................................................................................................................................................................++ e is 65537 (0x10001) [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# ll total 60 -rw-r--r-- 1 root root 1253 Feb 4 19:39 apiserver.crt -rw-r--r-- 1 root root 1090 Feb 4 19:39 apiserver-etcd-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-etcd-client.key -rw------- 1 root root 1679 Feb 4 19:39 apiserver.key -rw-r--r-- 1 root root 1099 Feb 4 19:39 apiserver-kubelet-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-kubelet-client.key -rw-r--r-- 1 root root 1025 Feb 4 19:39 ca.crt -rw------- 1 root root 1675 Feb 4 19:39 ca.key drwxr-xr-x 2 root root 162 Feb 4 19:39 etcd -rw-r--r-- 1 root root 1038 Feb 4 19:39 front-proxy-ca.crt -rw------- 1 root root 1679 Feb 4 19:39 front-proxy-ca.key -rw-r--r-- 1 root root 1058 Feb 4 19:39 front-proxy-client.crt -rw------- 1 root root 1675 Feb 4 19:39 front-proxy-client.key -rw-r--r-- 1 root root 3243 Feb 13 03:58 jason.key -rw------- 1 root root 1679 Feb 4 19:39 sa.key -rw------- 1 root root 451 Feb 4 19:39 sa.pub [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]#
2>.生成证书签署请求

[root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# ll total 60 -rw-r--r-- 1 root root 1253 Feb 4 19:39 apiserver.crt -rw-r--r-- 1 root root 1090 Feb 4 19:39 apiserver-etcd-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-etcd-client.key -rw------- 1 root root 1679 Feb 4 19:39 apiserver.key -rw-r--r-- 1 root root 1099 Feb 4 19:39 apiserver-kubelet-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-kubelet-client.key -rw-r--r-- 1 root root 1025 Feb 4 19:39 ca.crt -rw------- 1 root root 1675 Feb 4 19:39 ca.key drwxr-xr-x 2 root root 162 Feb 4 19:39 etcd -rw-r--r-- 1 root root 1038 Feb 4 19:39 front-proxy-ca.crt -rw------- 1 root root 1679 Feb 4 19:39 front-proxy-ca.key -rw-r--r-- 1 root root 1058 Feb 4 19:39 front-proxy-client.crt -rw------- 1 root root 1675 Feb 4 19:39 front-proxy-client.key -rw-r--r-- 1 root root 3243 Feb 13 03:58 jason.key -rw------- 1 root root 1679 Feb 4 19:39 sa.key -rw------- 1 root root 451 Feb 4 19:39 sa.pub [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# openssl req -new -key jason.key -out jason.csr -subj "/CN=jason/O=yinzhengjie" [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# ll total 64 -rw-r--r-- 1 root root 1253 Feb 4 19:39 apiserver.crt -rw-r--r-- 1 root root 1090 Feb 4 19:39 apiserver-etcd-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-etcd-client.key -rw------- 1 root root 1679 Feb 4 19:39 apiserver.key -rw-r--r-- 1 root root 1099 Feb 4 19:39 apiserver-kubelet-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-kubelet-client.key -rw-r--r-- 1 root root 1025 Feb 4 19:39 ca.crt -rw------- 1 root root 1675 Feb 4 19:39 ca.key drwxr-xr-x 2 root root 162 Feb 4 19:39 etcd -rw-r--r-- 1 root root 1038 Feb 4 19:39 front-proxy-ca.crt -rw------- 1 root root 1679 Feb 4 19:39 front-proxy-ca.key -rw-r--r-- 1 root root 1058 Feb 4 19:39 front-proxy-client.crt -rw------- 1 root root 1675 Feb 4 19:39 front-proxy-client.key -rw-r--r-- 1 root root 1610 Feb 13 04:01 jason.csr -rw-r--r-- 1 root root 3243 Feb 13 03:58 jason.key -rw------- 1 root root 1679 Feb 4 19:39 sa.key -rw------- 1 root root 451 Feb 4 19:39 sa.pub [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]#
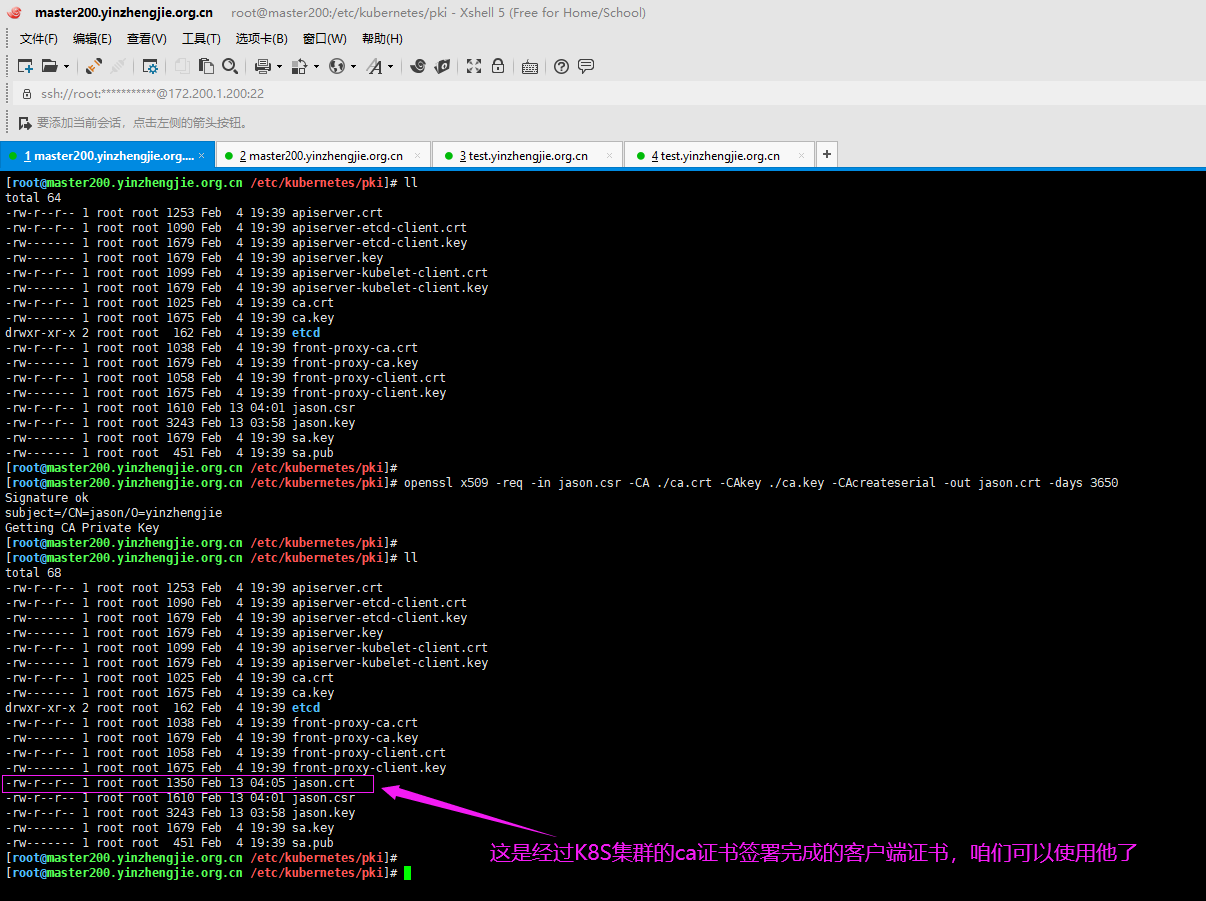
3>.使用Kubernetes集群的ca证书签署客户端证书请求文件

[root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# ll total 64 -rw-r--r-- 1 root root 1253 Feb 4 19:39 apiserver.crt -rw-r--r-- 1 root root 1090 Feb 4 19:39 apiserver-etcd-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-etcd-client.key -rw------- 1 root root 1679 Feb 4 19:39 apiserver.key -rw-r--r-- 1 root root 1099 Feb 4 19:39 apiserver-kubelet-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-kubelet-client.key -rw-r--r-- 1 root root 1025 Feb 4 19:39 ca.crt -rw------- 1 root root 1675 Feb 4 19:39 ca.key drwxr-xr-x 2 root root 162 Feb 4 19:39 etcd -rw-r--r-- 1 root root 1038 Feb 4 19:39 front-proxy-ca.crt -rw------- 1 root root 1679 Feb 4 19:39 front-proxy-ca.key -rw-r--r-- 1 root root 1058 Feb 4 19:39 front-proxy-client.crt -rw------- 1 root root 1675 Feb 4 19:39 front-proxy-client.key -rw-r--r-- 1 root root 1610 Feb 13 04:01 jason.csr -rw-r--r-- 1 root root 3243 Feb 13 03:58 jason.key -rw------- 1 root root 1679 Feb 4 19:39 sa.key -rw------- 1 root root 451 Feb 4 19:39 sa.pub [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# openssl x509 -req -in jason.csr -CA ./ca.crt -CAkey ./ca.key -CAcreateserial -out jason.crt -days 3650 Signature ok subject=/CN=jason/O=yinzhengjie Getting CA Private Key [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# ll total 68 -rw-r--r-- 1 root root 1253 Feb 4 19:39 apiserver.crt -rw-r--r-- 1 root root 1090 Feb 4 19:39 apiserver-etcd-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-etcd-client.key -rw------- 1 root root 1679 Feb 4 19:39 apiserver.key -rw-r--r-- 1 root root 1099 Feb 4 19:39 apiserver-kubelet-client.crt -rw------- 1 root root 1679 Feb 4 19:39 apiserver-kubelet-client.key -rw-r--r-- 1 root root 1025 Feb 4 19:39 ca.crt -rw------- 1 root root 1675 Feb 4 19:39 ca.key drwxr-xr-x 2 root root 162 Feb 4 19:39 etcd -rw-r--r-- 1 root root 1038 Feb 4 19:39 front-proxy-ca.crt -rw------- 1 root root 1679 Feb 4 19:39 front-proxy-ca.key -rw-r--r-- 1 root root 1058 Feb 4 19:39 front-proxy-client.crt -rw------- 1 root root 1675 Feb 4 19:39 front-proxy-client.key -rw-r--r-- 1 root root 1350 Feb 13 04:05 jason.crt -rw-r--r-- 1 root root 1610 Feb 13 04:01 jason.csr -rw-r--r-- 1 root root 3243 Feb 13 03:58 jason.key -rw------- 1 root root 1679 Feb 4 19:39 sa.key -rw------- 1 root root 451 Feb 4 19:39 sa.pub [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]#
4>.配置集群信息

[root@master200.yinzhengjie.org.cn ~]# kubectl config set-cluster -h Sets a cluster entry in kubeconfig. Specifying a name that already exists will merge new fields on top of existing values for those fields. Examples: # Set only the server field on the e2e cluster entry without touching other values. kubectl config set-cluster e2e --server=https://1.2.3.4 # Embed certificate authority data for the e2e cluster entry kubectl config set-cluster e2e --certificate-authority=~/.kube/e2e/kubernetes.ca.crt # Disable cert checking for the dev cluster entry kubectl config set-cluster e2e --insecure-skip-tls-verify=true Options: --embed-certs=false: embed-certs for the cluster entry in kubeconfig Usage: kubectl config set-cluster NAME [--server=server] [--certificate-authority=path/to/certificate/authority] [--insecure-skip-tls-verify=true] [options] Use "kubectl options" for a list of global command-line options (applies to all commands). [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# hostname -i 172.200.1.200 [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config get-clusters NAME kubernetes [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config set-cluster yinzhengjie-k8s --server="https://172.200.1.200:6443" --certificate-authority=/etc/kubernetes/pki/jason.crt --embed-certs=true Cluster "yinzhengjie-k8s" set. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config get-clusters NAME yinzhengjie-k8s kubernetes [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config set-cluster yinzhengjie-k8s --server="https://172.200.1.200:6443" --certificate-authority=/etc/kubernetes/pki/jason.crt --embed-certs=true --kubeconfig=/tmp/jason.config Cluster "yinzhengjie-k8s" set. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# ll /tmp/jason.config -rw------- 1 root root 2007 Feb 13 04:17 /tmp/jason.config [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cat /tmp/jason.config apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR0ekNDQXA4Q0NRRElQbFpIRVVFUUtUQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNREl4TWpJd01EVXpNbG9YRFRNd01ESXdPVEl3TURVek1sb3dKakVPTUF3RwpBMVVFQXd3RmFtRnpiMjR4RkRBU0 JnTlZCQW9NQzNscGJucG9aVzVuYW1sbE1JSUNJakFOQmdrcWhraUc5dzBCCkFRRUZBQU9DQWc4QU1JSUNDZ0tDQWdFQTNCWTlITk9YUWxyNjNwZnF1U3ZJYXgyM3hGUW1kbHV2WUJZT0poVVEKQ3lhcmU3SS9TWXcrUHJETjRValZPN0o0L3VYdE0vNDVaRGcxV2gvN3NWTTl6VTJhUlEzS2ExQXZkZjMzMGVQQQpsYng5azMxZ1ljYk1TVGl2VFRWNm5seHpyazd3UGFuMXZjWDNEdjAzejJteCt1NGhzZW1KRU5KYTMvMlNBWnArCitVY1lHNkx5K0grcEhWMVNDU1VNSU5EdEpkQ0hJMWNoSG4zQXJEejFLRzVXYmVSWTlBbUdzSTdvTUJWYmJJSlcKYWdvbm1DZWpOMXZhMWg2L3JmR1Q0MmI5WkhaQ2taQkRzVGFzTVp6dDlUSVlyb0ticlR4NHBrcHd6N0VqaStKbgpRajFEaGlhRzlaemgwY1hQcW55TEVHRTFXeURxTUlmMXR5TGpyNFZ1ejk3L3dzMlJuRFl3N05ZSVFyUDhZdTdIClVXK1NLbklSQ1QwOCtONmtWSEVEak4rZFlTTDNtMi9kUG9aSGxhWkFqSkZUQVpmbDlSaytBZ1hPL29nUzB1VVAKYktwU2g4WnpGZ1dpcE92ZFFtalYyMHNzc0lUSDVPVGkyRzdOdHV5bWp2ZTRUWW9Zd24rbUVjS3hDWXhyUXh0bwpsSnBja3l3eDZ6eng0eXpWMGd6ZHgrU05NZjNKZ3pCMVBQWVdWM003R3RobThtUVFseUR6dVZNRDZZZDhyeTFlCjkzdzVyMHorL3RiOC9LQmNxV2Y5T25XVDFNejlEUnJuTVRyNjczQWhGSStNVlJYNDM0VzZXY0ttM3drSjFBWGQKSE85SlNMRHU3VGtBSlVYSTBuWWVVd2Rmd1NYbFZpNVBZdGV1WXpFdjF0bk9GZlFkclNqcTk3cEhoaU1EWkVENwprM2NDQXdFQUFUQU5CZ2txaGtpRzl3MEJBUXNGQUFPQ0FRRUFabGFrKzU4Ui81Zy9xWmJqOSsrcEl2Z3JWZkcrCndDZkZrVVJYRlE5UjhZSHVscEVNZDA0WXNQTVFlTEhoWHFWcjMyd2J2b2RsZkVmRVkwWWdEWVVvY1Y2TUdLK24KQzZPSlVqRTdMc0tMMEFUd0VZT2MzY1Q5UTRtbGpEK2dRQWF4UW1DUTF5Nlg3ZnM4NHRtMEROalR4alhqRGlLVAo3RmxoK0JGRm1oc1Zta2NmK0VMSUl3MmtYWjZudFNNbm5DVXJYcElhbGRmRU1zWTY0YVNLaVQvSStPUzJrd0tFCmhKNU5FeHcrYTZXYWt0THowdlZnRVhSZCtCdG0xNzNvdzl6RmVvdlE4N2hiaHJnZWZFMXN5MDR4aEVXM2VYTFIKWFJmYmJFNnlIYzg4NDJkdHE1SUhFVFJYRWtIZk1IWkNLMUhsL1Y5RklJMjM4RXd1Q05rczRYRWh2QT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K server: https://172.200.1.200:443 name: yinzhengjie-k8s contexts: null current-context: "" kind: Config preferences: {} users: null [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
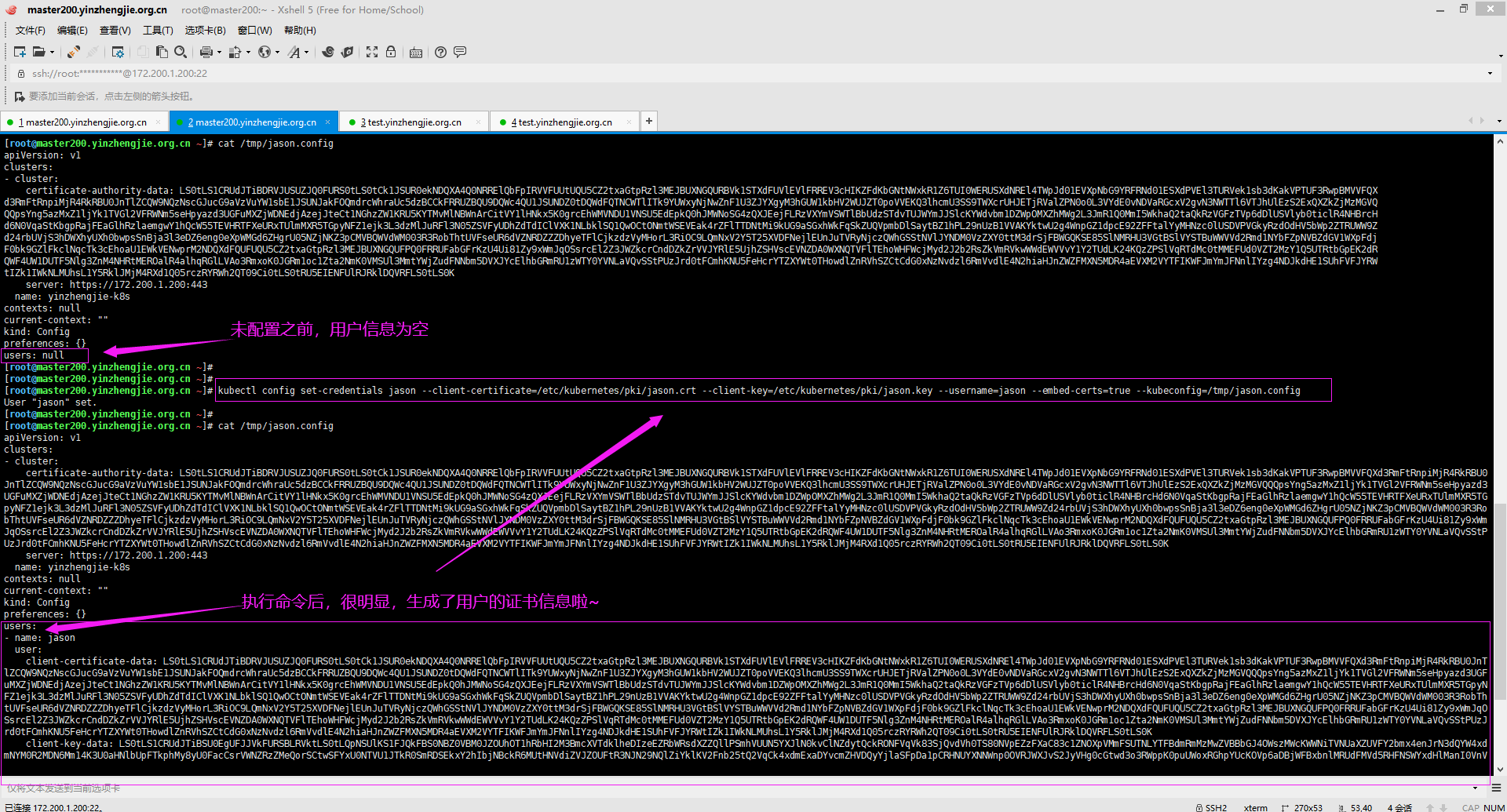
5>.添加用户信息

[root@master200.yinzhengjie.org.cn ~]# kubectl config set-credentials -h Sets a user entry in kubeconfig Specifying a name that already exists will merge new fields on top of existing values. Client-certificate flags: --client-certificate=certfile --client-key=keyfile Bearer token flags: --token=bearer_token Basic auth flags: --username=basic_user --password=basic_password Bearer token and basic auth are mutually exclusive. Examples: # Set only the "client-key" field on the "cluster-admin" # entry, without touching other values: kubectl config set-credentials cluster-admin --client-key=~/.kube/admin.key # Set basic auth for the "cluster-admin" entry kubectl config set-credentials cluster-admin --username=admin --password=uXFGweU9l35qcif # Embed client certificate data in the "cluster-admin" entry kubectl config set-credentials cluster-admin --client-certificate=~/.kube/admin.crt --embed-certs=true # Enable the Google Compute Platform auth provider for the "cluster-admin" entry kubectl config set-credentials cluster-admin --auth-provider=gcp # Enable the OpenID Connect auth provider for the "cluster-admin" entry with additional args kubectl config set-credentials cluster-admin --auth-provider=oidc --auth-provider-arg=client-id=foo --auth-provider-arg=client-secret=bar # Remove the "client-secret" config value for the OpenID Connect auth provider for the "cluster-admin" entry kubectl config set-credentials cluster-admin --auth-provider=oidc --auth-provider-arg=client-secret- # Enable new exec auth plugin for the "cluster-admin" entry kubectl config set-credentials cluster-admin --exec-command=/path/to/the/executable --exec-api-version=client.authentication.k8s.io/v1beta # Define new exec auth plugin args for the "cluster-admin" entry kubectl config set-credentials cluster-admin --exec-arg=arg1 --exec-arg=arg2 # Create or update exec auth plugin environment variables for the "cluster-admin" entry kubectl config set-credentials cluster-admin --exec-env=key1=val1 --exec-env=key2=val2 # Remove exec auth plugin environment variables for the "cluster-admin" entry kubectl config set-credentials cluster-admin --exec-env=var-to-remove- Options: --auth-provider='': Auth provider for the user entry in kubeconfig --auth-provider-arg=[]: 'key=value' arguments for the auth provider --embed-certs=false: Embed client cert/key for the user entry in kubeconfig --exec-api-version='': API version of the exec credential plugin for the user entry in kubeconfig --exec-arg=[]: New arguments for the exec credential plugin command for the user entry in kubeconfig --exec-command='': Command for the exec credential plugin for the user entry in kubeconfig --exec-env=[]: 'key=value' environment values for the exec credential plugin Usage: kubectl config set-credentials NAME [--client-certificate=path/to/certfile] [--client-key=path/to/keyfile] [--token=bearer_token] [--username=basic_user] [--password=basic_password] [--auth-provider=provider_name] [--auth-provider-arg=key=value] [--exec-command=exec_command] [--exec-api-version=exec_api_version] [--exec-arg=arg] [--exec-env=key=value] [options] Use "kubectl options" for a list of global command-line options (applies to all commands). [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# cat /tmp/jason.config apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR0ekNDQXA4Q0NRRElQbFpIRVVFUUtUQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNREl4TWpJd01EVXpNbG9YRFRNd01ESXdPVEl3TURVek1sb3dKakVPTUF3RwpBMVVFQX d3RmFtRnpiMjR4RkRBU0JnTlZCQW9NQzNscGJucG9aVzVuYW1sbE1JSUNJakFOQmdrcWhraUc5dzBCCkFRRUZBQU9DQWc4QU1JSUNDZ0tDQWdFQTNCWTlITk9YUWxyNjNwZnF1U3ZJYXgyM3hGUW1kbHV2WUJZT0poVVEKQ3lhcmU3SS9TWXcrUHJETjRValZPN0o0L3VYdE0vNDVaRGcxV2gvN3NWTTl6VTJhUlEzS2ExQXZkZjMzMGVQQQpsYng5azMxZ1ljYk1TVGl2VFRWNm5seHpyazd3UGFuMXZjWDNEdjAzejJteCt1NGhzZW1KRU5KYTMvMlNBWnArCitVY1lHNkx5K0grcEhWMVNDU1VNSU5EdEpkQ0hJMWNoSG4zQXJEejFLRzVXYmVSWTlBbUdzSTdvTUJWYmJJSlcKYWdvbm1DZWpOMXZhMWg2L3JmR1Q0MmI5WkhaQ2taQkRzVGFzTVp6dDlUSVlyb0ticlR4NHBrcHd6N0VqaStKbgpRajFEaGlhRzlaemgwY1hQcW55TEVHRTFXeURxTUlmMXR5TGpyNFZ1ejk3L3dzMlJuRFl3N05ZSVFyUDhZdTdIClVXK1NLbklSQ1QwOCtONmtWSEVEak4rZFlTTDNtMi9kUG9aSGxhWkFqSkZUQVpmbDlSaytBZ1hPL29nUzB1VVAKYktwU2g4WnpGZ1dpcE92ZFFtalYyMHNzc0lUSDVPVGkyRzdOdHV5bWp2ZTRUWW9Zd24rbUVjS3hDWXhyUXh0bwpsSnBja3l3eDZ6eng0eXpWMGd6ZHgrU05NZjNKZ3pCMVBQWVdWM003R3RobThtUVFseUR6dVZNRDZZZDhyeTFlCjkzdzVyMHorL3RiOC9LQmNxV2Y5T25XVDFNejlEUnJuTVRyNjczQWhGSStNVlJYNDM0VzZXY0ttM3drSjFBWGQKSE85SlNMRHU3VGtBSlVYSTBuWWVVd2Rmd1NYbFZpNVBZdGV1WXpFdjF0bk9GZlFkclNqcTk3cEhoaU1EWkVENwprM2NDQXdFQUFUQU5CZ2txaGtpRzl3MEJBUXNGQUFPQ0FRRUFabGFrKzU4Ui81Zy9xWmJqOSsrcEl2Z3JWZkcrCndDZkZrVVJYRlE5UjhZSHVscEVNZDA0WXNQTVFlTEhoWHFWcjMyd2J2b2RsZkVmRVkwWWdEWVVvY1Y2TUdLK24KQzZPSlVqRTdMc0tMMEFUd0VZT2MzY1Q5UTRtbGpEK2dRQWF4UW1DUTF5Nlg3ZnM4NHRtMEROalR4alhqRGlLVAo3RmxoK0JGRm1oc1Zta2NmK0VMSUl3MmtYWjZudFNNbm5DVXJYcElhbGRmRU1zWTY0YVNLaVQvSStPUzJrd0tFCmhKNU5FeHcrYTZXYWt0THowdlZnRVhSZCtCdG0xNzNvdzl6RmVvdlE4N2hiaHJnZWZFMXN5MDR4aEVXM2VYTFIKWFJmYmJFNnlIYzg4NDJkdHE1SUhFVFJYRWtIZk1IWkNLMUhsL1Y5RklJMjM4RXd1Q05rczRYRWh2QT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K server: https://172.200.1.200:443 name: yinzhengjie-k8s contexts: null current-context: "" kind: Config preferences: {} users: null [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config set-credentials jason --client-certificate=/etc/kubernetes/pki/jason.crt --client-key=/etc/kubernetes/pki/jason.key --username=jason --embed-certs=true --kubeconfig=/tmp/jason.config User "jason" set. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cat /tmp/jason.config apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR0ekNDQXA4Q0NRRElQbFpIRVVFUUtUQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNREl4TWpJd01EVXpNbG9YRFRNd01ESXdPVEl3TURVek1sb3dKakVPTUF3RwpBMVVFQXd3RmFtRnpiMjR4RkRBU0 JnTlZCQW9NQzNscGJucG9aVzVuYW1sbE1JSUNJakFOQmdrcWhraUc5dzBCCkFRRUZBQU9DQWc4QU1JSUNDZ0tDQWdFQTNCWTlITk9YUWxyNjNwZnF1U3ZJYXgyM3hGUW1kbHV2WUJZT0poVVEKQ3lhcmU3SS9TWXcrUHJETjRValZPN0o0L3VYdE0vNDVaRGcxV2gvN3NWTTl6VTJhUlEzS2ExQXZkZjMzMGVQQQpsYng5azMxZ1ljYk1TVGl2VFRWNm5seHpyazd3UGFuMXZjWDNEdjAzejJteCt1NGhzZW1KRU5KYTMvMlNBWnArCitVY1lHNkx5K0grcEhWMVNDU1VNSU5EdEpkQ0hJMWNoSG4zQXJEejFLRzVXYmVSWTlBbUdzSTdvTUJWYmJJSlcKYWdvbm1DZWpOMXZhMWg2L3JmR1Q0MmI5WkhaQ2taQkRzVGFzTVp6dDlUSVlyb0ticlR4NHBrcHd6N0VqaStKbgpRajFEaGlhRzlaemgwY1hQcW55TEVHRTFXeURxTUlmMXR5TGpyNFZ1ejk3L3dzMlJuRFl3N05ZSVFyUDhZdTdIClVXK1NLbklSQ1QwOCtONmtWSEVEak4rZFlTTDNtMi9kUG9aSGxhWkFqSkZUQVpmbDlSaytBZ1hPL29nUzB1VVAKYktwU2g4WnpGZ1dpcE92ZFFtalYyMHNzc0lUSDVPVGkyRzdOdHV5bWp2ZTRUWW9Zd24rbUVjS3hDWXhyUXh0bwpsSnBja3l3eDZ6eng0eXpWMGd6ZHgrU05NZjNKZ3pCMVBQWVdWM003R3RobThtUVFseUR6dVZNRDZZZDhyeTFlCjkzdzVyMHorL3RiOC9LQmNxV2Y5T25XVDFNejlEUnJuTVRyNjczQWhGSStNVlJYNDM0VzZXY0ttM3drSjFBWGQKSE85SlNMRHU3VGtBSlVYSTBuWWVVd2Rmd1NYbFZpNVBZdGV1WXpFdjF0bk9GZlFkclNqcTk3cEhoaU1EWkVENwprM2NDQXdFQUFUQU5CZ2txaGtpRzl3MEJBUXNGQUFPQ0FRRUFabGFrKzU4Ui81Zy9xWmJqOSsrcEl2Z3JWZkcrCndDZkZrVVJYRlE5UjhZSHVscEVNZDA0WXNQTVFlTEhoWHFWcjMyd2J2b2RsZkVmRVkwWWdEWVVvY1Y2TUdLK24KQzZPSlVqRTdMc0tMMEFUd0VZT2MzY1Q5UTRtbGpEK2dRQWF4UW1DUTF5Nlg3ZnM4NHRtMEROalR4alhqRGlLVAo3RmxoK0JGRm1oc1Zta2NmK0VMSUl3MmtYWjZudFNNbm5DVXJYcElhbGRmRU1zWTY0YVNLaVQvSStPUzJrd0tFCmhKNU5FeHcrYTZXYWt0THowdlZnRVhSZCtCdG0xNzNvdzl6RmVvdlE4N2hiaHJnZWZFMXN5MDR4aEVXM2VYTFIKWFJmYmJFNnlIYzg4NDJkdHE1SUhFVFJYRWtIZk1IWkNLMUhsL1Y5RklJMjM4RXd1Q05rczRYRWh2QT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K server: https://172.200.1.200:443 name: yinzhengjie-k8s contexts: null current-context: "" kind: Config preferences: {} users: - name: jason user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR0ekNDQXA4Q0NRRElQbFpIRVVFUUtUQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNREl4TWpJd01EVXpNbG9YRFRNd01ESXdPVEl3TURVek1sb3dKakVPTUF3RwpBMVVFQXd3RmFtRnpiMjR4RkRBU0JnT lZCQW9NQzNscGJucG9aVzVuYW1sbE1JSUNJakFOQmdrcWhraUc5dzBCCkFRRUZBQU9DQWc4QU1JSUNDZ0tDQWdFQTNCWTlITk9YUWxyNjNwZnF1U3ZJYXgyM3hGUW1kbHV2WUJZT0poVVEKQ3lhcmU3SS9TWXcrUHJETjRValZPN0o0L3VYdE0vNDVaRGcxV2gvN3NWTTl6VTJhUlEzS2ExQXZkZjMzMGVQQQpsYng5azMxZ1ljYk1TVGl2VFRWNm5seHpyazd3UGFuMXZjWDNEdjAzejJteCt1NGhzZW1KRU5KYTMvMlNBWnArCitVY1lHNkx5K0grcEhWMVNDU1VNSU5EdEpkQ0hJMWNoSG4zQXJEejFLRzVXYmVSWTlBbUdzSTdvTUJWYmJJSlcKYWdvbm1DZWpOMXZhMWg2L3JmR1Q0MmI5WkhaQ2taQkRzVGFzTVp6dDlUSVlyb0ticlR4NHBrcHd6N0VqaStKbgpRajFEaGlhRzlaemgwY1hQcW55TEVHRTFXeURxTUlmMXR5TGpyNFZ1ejk3L3dzMlJuRFl3N05ZSVFyUDhZdTdIClVXK1NLbklSQ1QwOCtONmtWSEVEak4rZFlTTDNtMi9kUG9aSGxhWkFqSkZUQVpmbDlSaytBZ1hPL29nUzB1VVAKYktwU2g4WnpGZ1dpcE92ZFFtalYyMHNzc0lUSDVPVGkyRzdOdHV5bWp2ZTRUWW9Zd24rbUVjS3hDWXhyUXh0bwpsSnBja3l3eDZ6eng0eXpWMGd6ZHgrU05NZjNKZ3pCMVBQWVdWM003R3RobThtUVFseUR6dVZNRDZZZDhyeTFlCjkzdzVyMHorL3RiOC9LQmNxV2Y5T25XVDFNejlEUnJuTVRyNjczQWhGSStNVlJYNDM0VzZXY0ttM3drSjFBWGQKSE85SlNMRHU3VGtBSlVYSTBuWWVVd2Rmd1NYbFZpNVBZdGV1WXpFdjF0bk9GZlFkclNqcTk3cEhoaU1EWkVENwprM2NDQXdFQUFUQU5CZ2txaGtpRzl3MEJBUXNGQUFPQ0FRRUFabGFrKzU4Ui81Zy9xWmJqOSsrcEl2Z3JWZkcrCndDZkZrVVJYRlE5UjhZSHVscEVNZDA0WXNQTVFlTEhoWHFWcjMyd2J2b2RsZkVmRVkwWWdEWVVvY1Y2TUdLK24KQzZPSlVqRTdMc0tMMEFUd0VZT2MzY1Q5UTRtbGpEK2dRQWF4UW1DUTF5Nlg3ZnM4NHRtMEROalR4alhqRGlLVAo3RmxoK0JGRm1oc1Zta2NmK0VMSUl3MmtYWjZudFNNbm5DVXJYcElhbGRmRU1zWTY0YVNLaVQvSStPUzJrd0tFCmhKNU5FeHcrYTZXYWt0THowdlZnRVhSZCtCdG0xNzNvdzl6RmVvdlE4N2hiaHJnZWZFMXN5MDR4aEVXM2VYTFIKWFJmYmJFNnlIYzg4NDJkdHE1SUhFVFJYRWtIZk1IWkNLMUhsL1Y5RklJMjM4RXd1Q05rczRYRWh2QT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlKS1FJQkFBS0NBZ0VBM0JZOUhOT1hRbHI2M3BmcXVTdklheDIzeEZRbWRsdXZZQllPSmhVUUN5YXJlN0kvClNZdytQckRONFVqVk83SjQvdVh0TS80NVpEZzFXaC83c1ZNOXpVMmFSUTNLYTFBdmRmMzMwZVBBbGJ4OWszMWcKWWNiTVNUaXZUVFY2bmx4enJrN3dQYW4xd mNYM0R2MDN6Mm14K3U0aHNlbUpFTkphMy8yU0FacCsrVWNZRzZMeQorSCtwSFYxU0NTVU1JTkR0SmRDSEkxY2hIbjNBckR6MUtHNVdiZVJZOUFtR3NJN29NQlZiYklKV2Fnb25tQ2VqCk4xdmExaDYvcmZHVDQyYjlaSFpDa1pCRHNUYXNNWnp0OVRJWXJvS2JyVHg0cGtwd3o3RWppK0puUWoxRGhpYUcKOVp6aDBjWFBxbnlMRUdFMVd5RHFNSWYxdHlManI0VnV6OTcvd3MyUm5EWXc3TllJUXJQOFl1N0hVVytTS25JUgpDVDA4K042a1ZIRURqTitkWVNMM20yL2RQb1pIbGFaQWpKRlRBWmZsOVJrK0FnWE8vb2dTMHVVUGJLcFNoOFp6CkZnV2lwT3ZkUW1qVjIwc3NzSVRINU9UaTJHN050dXltanZlNFRZb1l3bittRWNLeENZeHJReHRvbEpwY2t5d3gKNnp6eDR5elYwZ3pkeCtTTk1mM0pnekIxUFBZV1YzTTdHdGhtOG1RUWx5RHp1Vk1ENllkOHJ5MWU5M3c1cjB6KwovdGI4L0tCY3FXZjlPbldUMU16OURScm5NVHI2NzNBaEZJK01WUlg0MzRXNldjS20zd2tKMUFYZEhPOUpTTER1CjdUa0FKVVhJMG5ZZVV3ZGZ3U1hsVmk1UFl0ZXVZekV2MXRuT0ZmUWRyU2pxOTdwSGhpTURaRUQ3azNjQ0F3RUEKQVFLQ0FnQmNEVVVrVUcrY2hsY1ZVTzhRNGZvaXF6eFlkbVhiN1Q4dDdpdWV6QUo0MTRTejZQckZkVTMzaEpXbgoyNEdzUlZxTUtua0szUkwrRXZCbHNLamlJeEhmVTh6cGd2b2Q1bHpqZWdUMEdkRk1ENWxxWGU4NUZpQU5wQkxXCk5UOERDMklyRHNNMjEyWjhLRmZNUWliY3JyV05ZWnBnUW5CY3c4N1Vqc2RKdW1mUE5XZ2s3d08yNGhaR3ZPaDYKQUsvUTdmR3lka1IvaUlyR3FRdzBQZzdBQ1Y1RytsSW1SL0c0MlJ6T043Q1Vjdk5YeU1XRXcxZGw2UnBmb2w3RApqeDR1NTcybURqeUxpNDUwaVl4OTk4Z2pYUCtyeGQ3OUZ5VFRVS0ZjalJkMEE0N3l5cEw2Z2hUQ21BcHZaZEFVCjI2Q0NpbFg1dG91ZEh0Q3I5NERKd2dKMkdTeFpkQlpkdXJtaVAzdDhqbVNBQ1Z5YVdzaVloWThFWjNQMnkxVWwKcHUzNTFjSVNONE5vV09TTmFOcXVoTml1L0lGdEcwUnRGNmNabkVCemZlOXM5VFo4a2RhempYaU5PVHlTRit5MApqbnl5WjRWUVVQTVUveFZ2b1RMMWpYZjdQRzNqZHc5K1MzUVpGdU9xQnNWN1M3SFl1YXFTQW5lUnlTOU5vR25yClhXbGtUbHZwRml6N3VxaW1xM3hBa0xBY1gvOVNCb29UVmI3SVNiQnd6Q3ZrWVllVFNDUENqTGRMZUNheDIxMG4KZm5BRUQvZ0FRMzJGN0w5VzJmdVRhVUpENFlIMjhCQWFLeStIUVZDSWtHWnFFWjNQUGIyTVBqMGtBQks1citKVgo5TXdybHcxc2I1RzFtL3ZldlBBb1poaE9mcmVQUHZ6K3MzUFUxWFc2SDcwZk83emdJUUtDQVFFQS9JL3JvVjViClQ3L0dnd2Z3WmJqamNqUTNKcUhvaEJxM1Zxam5kUTNKc2lRKzJtdVNOaEpWS1NGaUNsaDdCM3FFZjFPZWxxaXQKMGN0VWNITkp4MUp2czBoWGxrQitrT0owdjJiM3gzUHBDcmFReTFDZys4L2xxV2U5OUhJdlMrbkNiR1p4SlNlegp6cklsT0JEZ3FGdDNtNHBIc3M2Q0xTc1BvU3NIdWIvMmp2SkxtUkRLRHRZdFVpaGExN3BGclpNQVUvWEw1ZzFsCjBmdlZJTXVzKzJ1b0N0Nzl5bHNZOWpkVkVXOWI1SGNiL1J1M1dFMHAzNFVROFpSR1FqKy83akpWWFo2SGNwMW4KNklxWS9rOGRIOFU0a1ZGL09FMXM1T3BUVVhXSzR0aGhqd0FRWGlzVURSL2RSWHNsSXUyK2t0Uk9wamw1THE4cgpDOGptSHQyMDlRZ2pod0tDQVFFQTN4VW5sUUdFZDVPQjZ0Z1cxOS9ORkRyb0NoS1E4d2k5R002MWp6QS9Wa1NvCkVxNXN1Vm1WNHFBNXdqbE5ycEJpSjZpenhaS0xHSzEwb1dOaHozT3grZ0hWMGNheWhmdlRjc1UwU2ZrOEloTHMKV0xBcmxIbDFseDNVSVp3eE8zRy91L09mMHFzVUhkanlja3lzZjh4TngzbFNlbktWbk1wSW5kWWJyNHBtTkphcwpxREFxSVkxcWdyaEIxeURqcVRFVHRybjVidS95QkE0c2VPRER3Z0tCMU1DUnp1Z1N2OC9tVVdaQjhqZlNwM2JMCnljbjFpTlR3Smh6emgvT2JPQTFkbTZjZTBtd2x1Vm1mN0pLcHY2Nk9KREFDaEl0VDErSmMzSmdKZ1VRTmxyeGMKS29JWENuZkt2OHV4dXVoVVEzSG1zcXR6YnhkcmsvbWVUK1ZuQ2luc2tRS0NBUUFXRnZCZytNTzd3ZVkyNTZiYQovc1RGNUZNK2ljS3dhelhGMnBnRDRPVFhNOXhiZGpVZmpaTHRPZ0k5TFdmMVMzM3pOUGtWN0VMbnFvVUVJTkUvCkliS3JWNVJ4aThxR0dZaGtoVGordE9DWkUwYXV3YXFTMjZnV25RQThOUkIxNzBnVit3L0NWQ3FoMVdyejhHWDEKMDZvdWJIWEE2ZGJ3NUdkRmpXSHJtU0tUZGhXdW1ZMVNwdURuNHFldlhwZGhpdzNvU2dNL1o4U1VEUmFpKzYxeApnQVQram1wY0hJT2VaVkNIYWRuN3JYOUJMLzlsTmJxSDFqZVpLWUxMb0kvRTRab2R5aFBHcm9XOERRTThtdWJOCk5JNnlCeEs5ZGVna1RXcGtJWWU0TjN5dzZTeUZUL2M4L3FCM3gwR0VRSTcrZ0pzd1pxNTJxdE4xQUdsQUlkd0YKNG1SWkFvSUJBUUNUWG9nOWVUa25QVHpRQlZ4aDA2akl1bmxiWGhSL1dNQ0N5TnRMOGxXRkNlbjJIV0FadWNLNAphWngrWUJpZlB5WjRpSXZwOHZzTW5GbTEyODlibWxSeWtnL01ldlNvYWttdlFmTmZBdFRrdFplSXB5akM5dEhsCnVJRFFpenhDeHN3Z3Y3cFBFMUZBdm5hN1owZDFUV1A4YUh0Q0JMd3RUYnhXK0lCbG9Jb1FKNUY3c2dYREVJYlMKUUNMT21SMk1RYTJDUXEweXlqUVkxYnd2Umx4THFCaFlrYlpBOXpLYm9CM0luRUxvWGxRODZNK0xTRzE1clNIUQpLOFA5aGNKK2J1WHQwNk1hNHZLdzFUSSt1RXlISWlzb1lNYnBCSm1vdmhNV2J5R29VV3FncjJJN2VxRDUrMVRuCkN3c29MQjZ1UjJwZGtjRzZHOENuaW5rNDBwVVZNOGpoQW9JQkFRQ0NCT092OUtCZ1JvRXd2QVA2cmlzY2FZYmUKOVdkZFB3MG12Y3JGM2FUWithMzMxZzdmS0ozSmUvQW8wWE5Cd3Q2UHFHOHNwbzZWRXQ1VnNlVnVUYjZTenJsNApEcEdvMEdPK2pzS2FhK3NWZ3pUdVh4SWQ1LzRJd3Y5QURRRG9zemVER1NrcUV5RmpyS0hCMklLNWFHSTE4bmV1CjdEREo3ZVhrQWZnTjYxYWJ0RXJJT240dWUwZXdJSWZ0TStHSHRBaWZ1dlBVYjdSUkhqZEdBaDY5bU1RTCtpZWcKNGFHb3RuSllrTVdIc3dkMVgyWUdCTUV4dWNlT1NUeFRURVBTNjFVQ0I1SFhnL1E1bTVwb3lYZG56MlpZQktPRApvUDVIUkFYUTBJRXZGTmhSZHJsZURDUGdFbklzY2ZjcXBQeGVtVlBJY3NuKzVUM2EvT1FrYmJYeUtwVk8KLS0tLS1FTkQgUlNBIFBSSVZBVEUgS0VZLS0tLS0K username: jason [root@master200.yinzhengjie.org.cn ~]#
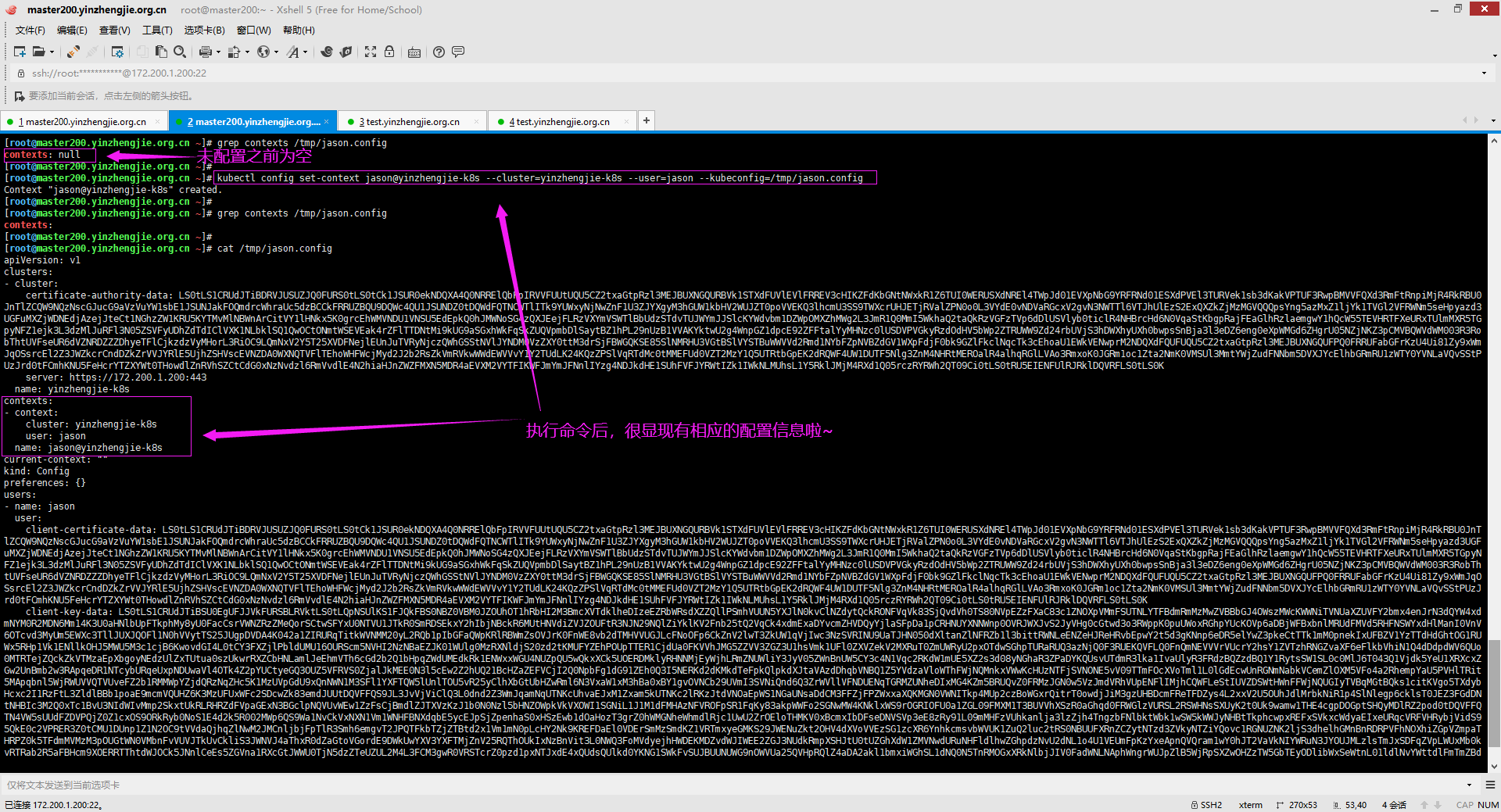
6>.添加上下文的配置信息

[root@master200.yinzhengjie.org.cn ~]# kubectl config set-context -h Sets a context entry in kubeconfig Specifying a name that already exists will merge new fields on top of existing values for those fields. Examples: # Set the user field on the gce context entry without touching other values kubectl config set-context gce --user=cluster-admin Options: --current=false: Modify the current context Usage: kubectl config set-context [NAME | --current] [--cluster=cluster_nickname] [--user=user_nickname] [--namespace=namespace] [options] Use "kubectl options" for a list of global command-line options (applies to all commands). [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# grep contexts /tmp/jason.config contexts: null [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# kubectl config set-context jason@yinzhengjie-k8s --cluster=yinzhengjie-k8s --user=jason --kubeconfig=/tmp/jason.config Context "jason@yinzhengjie-k8s" created. [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# grep contexts /tmp/jason.config contexts: [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# cat /tmp/jason.config apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR0ekNDQXA4Q0NRRElQbFpIRVVFUUtqQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNREl4TkRJek5Ua3pPVm9YRFRNd01ESXhNVEl6TlRrek9Wb3dKakVPTUF3RwpBMVVFQXd3RmFtRnpiMjR4RkRBU0 JnTlZCQW9NQzNscGJucG9aVzVuYW1sbE1JSUNJakFOQmdrcWhraUc5dzBCCkFRRUZBQU9DQWc4QU1JSUNDZ0tDQWdFQXZXcW1iNDBtbHkxaTFIb1N6eWFtTDVqOTBNOGM3K1RnNklxUWNsQVEKUXc0NEpWZHNJTGtBZlJCcGVDVkpRdXJOWVhUNVJzSUU2dkVOWjd1emE0ZnN4SERYZ3RaczU0cW5rdEVacXZsKwpocHYzM2h0Y0pJclZyOEw5Y3JaUVNzNDIxV2ZjMnVndm9CYm1uWjYrSXpmcjVnZlhLbGdYaE1sTS9ya2FLa1FmCmNudEl1ejdKeUp5R1M4ZlhyUFM4RWU2cStVbWY1b0tqZ1EzRDFhL1dlUGFRcVZBaTI4Y3NOTmUxSnBRellxMUcKVkxFRkFaK1Y1cVNNR0RFbGdrUXZzc0VZTVViR1FRMXRpWTk0R2RqaXZvM09FekZmeXZxSjFxUnMvMi9KNDIzOAplZkloTEtvK1JZY2k5VmRkOHhlMHFKbmhKOHlaYmxRQ2xwcEtnOTlwOFlpcnI1RzdaZW16RUJQNjNQV3NhT28yCkxBQnN4ZXhBV0syTXBNYjQ1MjlMM1Q4Tytxem9rNit4WDFVdW9OVjFPWnFIOXBSYWFPNE4wN2pYa0QzTHJ1dEsKcURRZk1Ua04vdTNBYW5oK2ppNW1FdkdWUCszSGIybGFOdzNya1NvMWNBZnZGdXRaOWc1Nit6VjZvT2R6M09aWQpPcytwa2l6azZqdzBCWXVHeFdQVnRneE9yaFJkTzNJK2tqYmZlV0xlVzZZQUdQTzdXdStzRGpuTmVQUDBSRHMxClQ5OXV6WXpmNlYveDllU1ErbC9mMmx6Tkh6VDBsd20vdjBuSGlKUVQ2d1psVFI4WTBNWkMvZGhHSkp3Q3N2RGMKUkduUU41dnJtWlVSRlR4VHRKekpEK1RuekhKSVZEME5nVi9GUmRGby83VTFMMndtMjA5N3pKWEdSR1dDUkoxWgpaaU1DQXdFQUFUQU5CZ2txaGtpRzl3MEJBUXNGQUFPQ0FRRUFDdUxzVTNtN1o4L3hWSlkvVDNLNWpLb1JiVE1DCk5VMVltSWFzYm9UK0JxTVFGdGVMYnRNMGJIREVRTXlGRGVIYkVQZlZMUnlFNUpOQTY0NXVOVzhlK0lobmpzNUMKRkRoaUhFRWw0VkFGNE1rNlE0bUt4OERaWGFLTVRjaGIvazd0akxiWFFXclhUblJpa0E5Vk5FRHVsYU9HekdXdwpnYk1KN2cveTFzU0pTMFRxaHZadW50elhtNWdwcHlsNWFaQVJIcFMvcXJ0bDMzMCswbzZPS1E5MEo5UW4zRk9hCm9GOTJDOWcyajN0TndLSFpkZlJPSjY2VGtxRTNmLzZKYVRHTStLSjc0ck1QRGJPNUxzdFpIaFFvWU12WEpBc1YKaEM0SmllcXVGaXIyQlk4MjkwbkNPQ0k0QllPbXpFY014UzloWHl3RityazNHVlNxZXpTbWpOdmN2UT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K server: https://172.200.1.200:6443 name: yinzhengjie-k8s contexts: - context: cluster: yinzhengjie-k8s user: jason name: jason@yinzhengjie-k8s current-context: "" kind: Config preferences: {} users: - name: jason user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR0ekNDQXA4Q0NRRElQbFpIRVVFUUtqQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNREl4TkRJek5Ua3pPVm9YRFRNd01ESXhNVEl6TlRrek9Wb3dKakVPTUF3RwpBMVVFQXd3RmFtRnpiMjR4RkRBU0JnT lZCQW9NQzNscGJucG9aVzVuYW1sbE1JSUNJakFOQmdrcWhraUc5dzBCCkFRRUZBQU9DQWc4QU1JSUNDZ0tDQWdFQXZXcW1iNDBtbHkxaTFIb1N6eWFtTDVqOTBNOGM3K1RnNklxUWNsQVEKUXc0NEpWZHNJTGtBZlJCcGVDVkpRdXJOWVhUNVJzSUU2dkVOWjd1emE0ZnN4SERYZ3RaczU0cW5rdEVacXZsKwpocHYzM2h0Y0pJclZyOEw5Y3JaUVNzNDIxV2ZjMnVndm9CYm1uWjYrSXpmcjVnZlhLbGdYaE1sTS9ya2FLa1FmCmNudEl1ejdKeUp5R1M4ZlhyUFM4RWU2cStVbWY1b0tqZ1EzRDFhL1dlUGFRcVZBaTI4Y3NOTmUxSnBRellxMUcKVkxFRkFaK1Y1cVNNR0RFbGdrUXZzc0VZTVViR1FRMXRpWTk0R2RqaXZvM09FekZmeXZxSjFxUnMvMi9KNDIzOAplZkloTEtvK1JZY2k5VmRkOHhlMHFKbmhKOHlaYmxRQ2xwcEtnOTlwOFlpcnI1RzdaZW16RUJQNjNQV3NhT28yCkxBQnN4ZXhBV0syTXBNYjQ1MjlMM1Q4Tytxem9rNit4WDFVdW9OVjFPWnFIOXBSYWFPNE4wN2pYa0QzTHJ1dEsKcURRZk1Ua04vdTNBYW5oK2ppNW1FdkdWUCszSGIybGFOdzNya1NvMWNBZnZGdXRaOWc1Nit6VjZvT2R6M09aWQpPcytwa2l6azZqdzBCWXVHeFdQVnRneE9yaFJkTzNJK2tqYmZlV0xlVzZZQUdQTzdXdStzRGpuTmVQUDBSRHMxClQ5OXV6WXpmNlYveDllU1ErbC9mMmx6Tkh6VDBsd20vdjBuSGlKUVQ2d1psVFI4WTBNWkMvZGhHSkp3Q3N2RGMKUkduUU41dnJtWlVSRlR4VHRKekpEK1RuekhKSVZEME5nVi9GUmRGby83VTFMMndtMjA5N3pKWEdSR1dDUkoxWgpaaU1DQXdFQUFUQU5CZ2txaGtpRzl3MEJBUXNGQUFPQ0FRRUFDdUxzVTNtN1o4L3hWSlkvVDNLNWpLb1JiVE1DCk5VMVltSWFzYm9UK0JxTVFGdGVMYnRNMGJIREVRTXlGRGVIYkVQZlZMUnlFNUpOQTY0NXVOVzhlK0lobmpzNUMKRkRoaUhFRWw0VkFGNE1rNlE0bUt4OERaWGFLTVRjaGIvazd0akxiWFFXclhUblJpa0E5Vk5FRHVsYU9HekdXdwpnYk1KN2cveTFzU0pTMFRxaHZadW50elhtNWdwcHlsNWFaQVJIcFMvcXJ0bDMzMCswbzZPS1E5MEo5UW4zRk9hCm9GOTJDOWcyajN0TndLSFpkZlJPSjY2VGtxRTNmLzZKYVRHTStLSjc0ck1QRGJPNUxzdFpIaFFvWU12WEpBc1YKaEM0SmllcXVGaXIyQlk4MjkwbkNPQ0k0QllPbXpFY014UzloWHl3RityazNHVlNxZXpTbWpOdmN2UT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlKS0FJQkFBS0NBZ0VBdldxbWI0MG1seTFpMUhvU3p5YW1MNWo5ME04YzcrVGc2SXFRY2xBUVF3NDRKVmRzCklMa0FmUkJwZUNWSlF1ck5ZWFQ1UnNJRTZ2RU5aN3V6YTRmc3hIRFhndFpzNTRxbmt0RVpxdmwraHB2MzNodGMKSklyVnI4TDljclpRU3M0MjFXZmMydWd2b 0JibW5aNitJemZyNWdmWEtsZ1hoTWxNL3JrYUtrUWZjbnRJdXo3Sgp5SnlHUzhmWHJQUzhFZTZxK1VtZjVvS2pnUTNEMWEvV2VQYVFxVkFpMjhjc05OZTFKcFF6WXExR1ZMRUZBWitWCjVxU01HREVsZ2tRdnNzRVlNVWJHUVExdGlZOTRHZGppdm8zT0V6RmZ5dnFKMXFScy8yL0o0MjM4ZWZJaExLbysKUlljaTlWZGQ4eGUwcUpuaEo4eVpibFFDbHBwS2c5OXA4WWlycjVHN1plbXpFQlA2M1BXc2FPbzJMQUJzeGV4QQpXSzJNcE1iNDUyOUwzVDhPK3F6b2s2K3hYMVV1b05WMU9acUg5cFJhYU80TjA3alhrRDNMcnV0S3FEUWZNVGtOCi91M0Fhbmgramk1bUV2R1ZQKzNIYjJsYU53M3JrU28xY0FmdkZ1dFo5ZzU2K3pWNm9PZHozT1pZT3MrcGtpemsKNmp3MEJZdUd4V1BWdGd4T3JoUmRPM0kra2piZmVXTGVXNllBR1BPN1d1K3NEam5OZVBQMFJEczFUOTl1ell6Zgo2Vi94OWVTUStsL2YybHpOSHpUMGx3bS92MG5IaUpRVDZ3WmxUUjhZME1aQy9kaEdKSndDc3ZEY1JHblFONXZyCm1aVVJGVHhUdEp6SkQrVG56SEpJVkQwTmdWL0ZSZEZvLzdVMUwyd20yMDk3ekpYR1JHV0NSSjFaWmlNQ0F3RUEKQVFLQ0FnQldmdWduMG5ZSDNQTGZnaXNxcTBTQ1FjUE40WFllV2c4V1FZZzZtek1CMi9GcG8rVTlnQjJuL3FHYQorclBjdWVvMWtidnZRdFFLRVMrRTZpTEJmTjF5eXZDdXo0b0ZwYnhsLzlSUHpnU29KWHJuMHVpZHkwUlBNYVNaCkNJWGIweFVaR0lleTh3b2tlYkN2MDNpU0RveExpOU1HaEJtaFNtYzlmbnRqUjU1d29ibVJ2OWRYSTVyejZmc2sKQU5JTkFrYlM5WHJ1UVVPMnYvbG9rQlpKUUpiSXFrNXd2Q0FFdFdnRWlQSjZJaFFXd29zOXRZazNQSGE0NldCdQpmd0tsQnlZc0FseXdBaGkrRTJUTnNNdkNKbkV2TklIQTUrMmZ0WkFNaVJqUklUMkUxanV0OE1QazdoUFpveDdFCnpsTnlGbXJKeU5WYm0wTmZVRytzam80TGZOU2cyaHRjajVCOEEzVWlPRlJ1MjFwTHo3YVFUcDdpN2hFTGVhd3gKRjJjbDVRVEZ6eGxkVXNzZFZXMmJtYVVzOWIxNmNXS0hIL080bFlTcllFSlhsVXAzVWJxbWFBRnk5ZFVWT3lxVQp6TU1KTW1McC95OXVaVm8wNjd2SjVqaFI0dDRpQ1ZOek4rbk5ZckN2RitFZ0UwekE4NW9yU3J0cTBFUVVRaGJzCjRtQWtrQm8zVXUxVlJVNHhDSm8ycTVhbG9Ndk9WSG01UytZd0Y1NEo3bWxXSVVLTm1wSVY3STc0YUlNS1M3SWgKeFF5WnB0N0EzaWREM00xeEJkWllvZC9lNU1xMnY1Y0lvZjJldW1ER3pHRG9qbkdkVFBiNkJMcVg2TGZlT1g3TwpqeXJIeDJZcHpJSHJXTjZlZ3kwM3p3RFlhN1VBQ2w0Q3NIcDZWQkFsY01jSUhoTjVFUUtDQVFFQStlSDlBWWlJClFrQ04wS2JyYkw1TEUzRTJDZlAvbDdoQld4bHVFYUl0Vk9hWW96a0t6NmR2RUdGQTdxMEh1WGVyMFNNUnVSbUgKOG5SajlMWm5uNVlmNEZRL3hhcFlDdjJVNHlRN1REYjNKWE5aNmZ4TmFRdlJrUHMrcEZQSGxQS0I5dkdBSTNicgo5aG1OV3l4NTFDaUxEMmxyMXNEWUpBT1VxTFp4WkxsQ25rNnRsa0Jndmt2UVY5ZmdJNUU5TjdjdnVOS0twM29QCnFhMGhWTFgwL3VsaXpCVnFVS3Z6Qkc1cS9Na25kZVBnQkw4N1hHS0VGUEVZa1BDMGw3Uy9MMWFJeUlpWlJhM20KTVljeFQwV2tmZkQ0VmhxWmN1K1grTHRjcTYxSDc2Z21YR0RPQThnRkVycWZXeUpON3BoR2RBL3RHZ0JtOHQzQgppSGlydjhKU1R5YlRHUUtDQVFFQXdnMjRwQWd1UWYvczhwU2lPMlVNcmh0QlIwQ3M2R1Bsakt3aVZMUmdselBVCmMxN21UNDQxMDVKTXB3blZqaEZLazFhL1E1TWJsQzVSWEJuMWZ0dk1wY3NIRFl0NHhKbEpTT0ZlVHhhWjd1bWkKZEF2QklzaHBGTS9FdGxTT2NXVTV2eGdzM3YwUmVkclNJMXhBUGxPL3FKMUwrY0FDRlhZY0tnMFkxVjNkY0d3MwpnTTA0MkN2UGdoNzNXbWdZeUFGc1J2cVhVSW85TXJqenY1NVowZ29uaG1lMks3SENpbmEyaUtlZlFRTFM0MkY1Cmo3MU1TMDNldTNIdGlRR1hRZVRRRW1OK2Fud2dEMkp0WGJyRHRWTFNXTFJ2L3ZHdlBYaWp0UGlDZVBRelBpelgKQ3VoYzl3aUxSK0lRVnlWcUprZ3JzMW0rcG4rRDI0b2hNcThVSUswR213S0NBUUVBaHRkcE5QdWRNOHNyKzgwbgpPMzRRZTBSYk9kRytPZndHNEliL2UycDlkZFFkeCs2UEkvRWhJTUNxVG1GMnlxR0dTUXZZazM3d2VtaE9UQTVtCktwclRScldQMkRXTTN4bHB6NHlNcHhyK0VPcUhPWm1abURiMWRudnRtTFZRL05KRVNhS1dXQXpqVmVFQ0E1SWoKaDlYOC9Hc1I4MGdMR3B3SUMyYXdGLzlVc0tLYVQzc2IrWFJsMEJGQTlWQjVyV2dmeTJkcHhPZzhMWDZzZnM3VgpqdjBZQURNS05OQWxDbDRmUTV1MHZJd2tKY3VmMThHZHJzTlBVMTlneElDWHJvN09ydy92VGNlQ2NYV1hxVVJXCmVGT2hYcTFwNHJqaDFDb2UzdEZhQVR4R3Z4REord1pqbm5Dd2IzZzZmNmNTVmEwR2NFS0pTME5aSFRDbzFZaWgKNis1eWVRS0NBUUEwOUVHYW9aRGQrZFRUTGJSSHVQK0kwMjh3M25sUXdWSDIzVkpSQXhnSXF1QWl5NWJWeHR6eAphMDczbGp0c2xWTmdlWitmOVJqbGl1NHd6L1NxTlpqVzlWeHJXZEFPOWpXRmFkcXVnbUJuVGVKREFLSW50OERWCktRMXBKQkhxNTlDbVVSYU5rMG1ka3hVZENTT08zcFBDazRvVUVVMkFSY2JSd3Rrd0FIbFpJRzdVK3l1ejhlQ2kKaFlqQ1p2MjhOb2N4cDFoN1pmM2xSWXRla3Z1MzBZV1BxK1dPYnVmRG1UbWVlUCtBWWlEaVk4c2thbWZUZE9CLwpEa3ZmdzB0ZmMrMUQxMXE3L0R0VGQyeVkwMHBzeExrWjg4Tk1NdSs3T3B5UjJlN2d5dUxnNktPV0dtcWtEdlRUCkhPR1FwbWtkSVR5cnFLWGFFWm9ONHRmRVdQcUpJQzVaQW9JQkFCR1pUcjhIM3JzSS9rUTZscngxSzMwQ0ZVSWMKVXNnbVdJdUd5UlJoR1YwSkt5M2ZtNEYyeXA3cE5hb3ljeTJvY3h1b0YwbFNVaDlFVGZJaUdnQ1FCUWVSZm9UNgpDTHdGYjc4ZDRzNEg1Y1hnclVkNFowU2lYZDFRZG9QbENVeVFNRjF3aTRqOUNTaXhwUTJRREt5OGltNkd0RE12CjFwTmRUZVZOdktodXo0QSs3OWVNcUR6VnZTMUhETWF5RS9UNDl5MFNqeVRXaGkxU0pXQVBPR1lwL1BoSC9IYVAKS2J5RzZsYlhoVXpFSXFJOEF6SENNMlVRaE1RVVpHRHdqem12Q0xuU1hKNzJvVm5sYVB0ZUYyMktJNjhXN3IvYgpSdC9qUk5vZDJFNElIZ2Z1bGF1bllDQmN5T1FLS3pSay8yM3k0Q2NibVNZTm1HTmZqNG1ybEF0VDlsZz0KLS0tLS1FTkQgUlNBIFBSSVZBVEUgS0VZLS0tLS0K username: jason [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# [root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]#
7>.如果配置时不使用"--kubeconfig=/tmp/jason.config"选项,默认会保存到"~/.kube/config"

[root@master200.yinzhengjie.org.cn ~]# cat ~/.kube/config apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01ESXdOREV4TXpreE1sb1hEVE13TURJd01URXhNemt4TWxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0 FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTGZMCm1hcDRJVkt4YWFLdFY0c2lDdFp0dWVRczJGWWE0RVlWTGI1c1lSWUtZSUI4YnRRdExpMXVUMWw2QnBxcWIwQ3oKbCtaMVBIN0doRHBiR014NkEzYUYyOVEycFo1NnVVc0tiWTIwZGVIWVZmeFZEek40c0ZwSGF0a25nelNEVGxVTgpoUTgrd004amxnT0k0TTR6NENXY3ZnZUJ0cXZSaTFRYVZaRzRZYm5kZ3AzMVVLRHRsR1ljbzJZK21jY3AxL0VKClJHQ1NmTUt0aFpRMnpMZ1c3RG4rdzc5YkdZbjhXRU5MOGlVZ3dwa3dyY2ZRTngwa2dUNzZXQjFZQnJSc2V5R1IKZTFRcUgyNEpqdHRpRU1aME8zZ0x4UCsvWXRiWDJlbkZUa3VCVTlJZVQzb0Rvc0FDcVdrOGsyR1p6RW5VZHNENAppcmhLUFlDMHlJRHJwLzY0NnFFQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFFQmgzSEtZOHBqbndrcmx3d1NaQmdJT2x5NzAKZTR3UXk3c3BCL0tKdW1TdG9uY1ZTd2JLRHpiQm5vWmlBcWVWbFpFU0IxWnYwZEdUVmJmZ21MYkwvU1B0NHovNgpNczhUMVFERW9kalJ1dlI0M0RSd0phR2xENHh4cDh2d0o0TysrQ0tITUNKck54OHVKbTFXODBzOEJXbnNxNytQCkQxMEVOZ2JzZHVXZ3NXMjNJNmM0WVB0dCtHeEE0S2wxalVkZGcydFIyNFo5eHNhRHdXRGoxZUg2a2xNcXpqaEYKc295Qk0vODFkWnllbzdzUDh1WGl1MkRUVkpVWWFEV005VzY3TlRSRWZ6TndUbTh2bUFjSjJlVG9lR3Z1MC96RApPejVDSWVsbWJZaVUvclVLVFNNdm0reFlOOFRGVkRmVFVQMHY0cHB2QjBmL2RIQThMTVBRYnhldVJKOD0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= server: https://172.200.1.200:6443 name: kubernetes contexts: - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: kubernetes-admin user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM4akNDQWRxZ0F3SUJBZ0lJQ3NaaEJqaDJyWjB3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TURBeU1EUXhNVE01TVRKYUZ3MHlNVEF5TURNeE1UTTVNVFJhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUc HRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXdwL21nTndmcGJnVlJqUHIKaUF0Y25DeHZBZWh6S2ZjdlhWWEtMOWlKRERFWGFNT0lVVUt5U3JZNlhDOGh2a2xyY0puWGZQRk9WelpoVUk5cgpsbzVCa2UzUm5xbDRrT1pFeDNOejUyeTdpdEhPZHpIa2N1dEpoWjN0c0V5ck9qWlI4aHhxNlZ6eHcvWXpmemJSCmk2VTVEZ0lNQUxKbXoydWErdXVPYlhtcDlHNzhGWGxPdXQ0VFpKM1BkNUxOQWhwYWJnMlZuV0x4dXlTekNEaC8KU3FpMS9ua3d0WTdmYnR3dkNaN2J4eGF0OFpIZXF3cVJUSE9WdnBHaWZDNDV4Sjh5SUs3dzFrc0JqemtXYnhubwpBbU90TzBxM2ZnQ2JnVTF4L05Fc2NvVjJXMi91MnFqdXFIUnZUTEwra3hmbW1OcFBwVFJpMUJqNEFwYXF3eEFZCitVdGRXd0lEQVFBQm95Y3dKVEFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFCOHhmbVdUT1JGVE5yUVJDeVA4V1lUZFRzV1BWQ2R6TFZWdApEMWpOSGZWMkxreXB4bFFGZml2MHpnMFg1UHpkbUNnQXU0V3JVQjlUZGkvQU1zOTRPT1ozZUFmeGR1VDZFdVBHCkdmNm5OVXFOWlpIR3Z3NkpPeldNbUFCQzhxN3VQUHo3cWFOa0FFaDdwS1diMDE4cTFBRFdiYlVtRzhVMW1qOVgKQStnNDRoVVRTYlRKanVMaDFRMVVnbTNtbEZTZmM0VWZ5bDlheWlsQ2dXSXZlTU1TeFRyWDcvbGpSR2hLUUVaNgphcnVuMnVIbEIrODJIZ1NOZE9xdGhLaWlTZFBBZ2c2dDEvWTNxelZ1bmlSN01GdFNjSWkzQWxCeTJQdXE0cUpZCkJ6b3NMUitqclZGSitLUWx1TDlPTVVBUU5hZFd4OWpsUFBUK0VMazFkS0FCTDNRZTBQST0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBd3AvbWdOd2ZwYmdWUmpQcmlBdGNuQ3h2QWVoektmY3ZYVlhLTDlpSkRERVhhTU9JClVVS3lTclk2WEM4aHZrbHJjSm5YZlBGT1Z6WmhVSTlybG81QmtlM1JucWw0a09aRXgzTno1Mnk3aXRIT2R6SGsKY3V0SmhaM3RzRXlyT2paUjhoeHE2Vnp4d y9ZemZ6YlJpNlU1RGdJTUFMSm16MnVhK3V1T2JYbXA5Rzc4RlhsTwp1dDRUWkozUGQ1TE5BaHBhYmcyVm5XTHh1eVN6Q0RoL1NxaTEvbmt3dFk3ZmJ0d3ZDWjdieHhhdDhaSGVxd3FSClRIT1Z2cEdpZkM0NXhKOHlJSzd3MWtzQmp6a1dieG5vQW1PdE8wcTNmZ0NiZ1UxeC9ORXNjb1YyVzIvdTJxanUKcUhSdlRMTCtreGZtbU5wUHBUUmkxQmo0QXBhcXd4QVkrVXRkV3dJREFRQUJBb0lCQVFDVWNpZjdVMnBrR1ROSQoxNk1ub2hyaUY5WVhxM2ZqbzJFaUhLUlp1QnhZQ3oyaXI3bFMyYjlwMHZKU2k3UitFanY3cDZ1LzVjSHVMVkV1CmhDWDRzTXA4aHR0aTNEcFVzdjMwN3krUmJkTGlBRU10a1FXQlRjdEhPZjBvZ21IN3hhRGRQU1dpbHp6a1RlNWIKY3JHRGhPTXV0d3Iyb1J4Znl1QnIwSzFTL1FCUHFkNUNiL3hXU0tScWlDNjUrTGVsK0phQTEvL01ZcUtNUFlNNQplVHVjNVhhdWl6a0Y4K1pVTS9KMXNKVm5QR3VpR0VTR2NhRUlhTVY5bHc5ZC9OMDFwNnVuK255STY3NVJ2TlowCkszSlJoZ0tjNGxPTlpyb0dHS1dwOVloNnU2U2dZdWVYcUU2SUVyVnNvbzJDYWJ1dVJpTDhPM3hQOERJR2hQc1oKRjlmWEY2K1pBb0dCQU8xQXpTa0hNSWJISjduRFcwY250dVdaMUQyN29aajJ2RTZMbmprV0Fia3pkaXhSdGc0YQpmWnVOOTRpZUJSMzFEKy9QclM4WVkxTzdNOVhYaGdBN3BXcC80MnVYY0xFdGpGbUt1MFE5NHZGMnMvcGV2WDVhCncwdFkrNXFSaEliZytHU0tSZGZacHU4dCsreVVIZFVWcTFoYTVIaTVyb0ExWXh6RHJJdzE4SEF0QW9HQkFOSUEKelR6RENDTU5wV1pCc1A5bmhBMGNEWi9UQ01vbmRZcXVnMFllTWVLZ3lzR2tqM3ZoTHlUaEpkOWFTUmF1QzB5aApSSUhCZFpnYkl3V25VdnY2cDQ0alNTb2oyMWptcGpwSVg5c28rZ0dDd1NHRENOWUlFY1VvVG9Yd2ttWmhWQ2c0CjVySXoweXdmamgxQXU4V2xIa3R5ZmVGNHVQMEkwdXJIeUNER2FQQ25Bb0dCQU5jcXFlWEhxMjdRTjJyMWpWYWUKNGZTZzZpZUNmeS9tdFNqVzNvd1BOVWp0THdOS3A3MXFzUGZlYk52dDA5NHpYbHl6RC9GaVFOS3pPSE43bnYrZgpHSW5acWpydGdUcHVnSmJFaHNtQkJzek9Sck9PTUhUamc3SlY1UGx0ZDYrTFlEcHVYS0ZCdDIrN1dIcGFhaVBTCkh5OW1YMFpOdjhCdXFwQnZ0WkVEYWllUkFvR0FTeXJpUzVkN3VDQlFUYlBCeVFtaWFKYmNBWk1tR0VYYmV0SlEKUnE3VUtFeHBocnFDYVZNRzd1cHdCZXhwTU9jSFFGeVJDdWpXVUtXVitaWVV6QURDTE14UWlmYmZzb2lNZzF3WQpnM2U5VlFFYVpBWmxDVWRHSlEzeVhWcm83Q0IyWVJkTTdBaEUxQXhQY0FVVnNQOFRRdW91U0tCUGhySzczREc2ClhwRG1TdzBDZ1lFQTZDYW9HcnZVL21CTjNuSkp2bk41NGVtTGxkbVhGak1MQ2UraDA1RjFxSXVWT3VyQm1lbkEKMlhKMng0bFN6ODJBbVoxeTAxc1JMVXJWVGxJbWxkbW9Ldm92VmJETHMvSmZOUkRTQTFBTjY4ZzFNK0c3QVpNOQppaUNMTmFWS01ncUE0d3JlS2JieUROaGhuSjRjVGQwaWU2eTRLVUJvaFhnTXl4K2FnWUZwQnpNPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=[root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
[root@master200.yinzhengjie.org.cn ~]# kubectl config set-cluster yinzhengjie-k8s --server="https://172.200.1.200:6443" --certificate-authority=/etc/kubernetes/pki/jason.crt --embed-certs=true Cluster "yinzhengjie-k8s" set. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config set-credentials jason --client-certificate=/etc/kubernetes/pki/jason.crt --client-key=/etc/kubernetes/pki/jason.key --username=jason --embed-certs=true User "jason" set. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config set-context jason@yinzhengjie-k8s --cluster=yinzhengjie-k8s --user=jason Context "jason@yinzhengjie-k8s" created. [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# cat ~/.kube/config apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01ESXdOREV4TXpreE1sb1hEVE13TURJd01URXhNemt4TWxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0 FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTGZMCm1hcDRJVkt4YWFLdFY0c2lDdFp0dWVRczJGWWE0RVlWTGI1c1lSWUtZSUI4YnRRdExpMXVUMWw2QnBxcWIwQ3oKbCtaMVBIN0doRHBiR014NkEzYUYyOVEycFo1NnVVc0tiWTIwZGVIWVZmeFZEek40c0ZwSGF0a25nelNEVGxVTgpoUTgrd004amxnT0k0TTR6NENXY3ZnZUJ0cXZSaTFRYVZaRzRZYm5kZ3AzMVVLRHRsR1ljbzJZK21jY3AxL0VKClJHQ1NmTUt0aFpRMnpMZ1c3RG4rdzc5YkdZbjhXRU5MOGlVZ3dwa3dyY2ZRTngwa2dUNzZXQjFZQnJSc2V5R1IKZTFRcUgyNEpqdHRpRU1aME8zZ0x4UCsvWXRiWDJlbkZUa3VCVTlJZVQzb0Rvc0FDcVdrOGsyR1p6RW5VZHNENAppcmhLUFlDMHlJRHJwLzY0NnFFQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFFQmgzSEtZOHBqbndrcmx3d1NaQmdJT2x5NzAKZTR3UXk3c3BCL0tKdW1TdG9uY1ZTd2JLRHpiQm5vWmlBcWVWbFpFU0IxWnYwZEdUVmJmZ21MYkwvU1B0NHovNgpNczhUMVFERW9kalJ1dlI0M0RSd0phR2xENHh4cDh2d0o0TysrQ0tITUNKck54OHVKbTFXODBzOEJXbnNxNytQCkQxMEVOZ2JzZHVXZ3NXMjNJNmM0WVB0dCtHeEE0S2wxalVkZGcydFIyNFo5eHNhRHdXRGoxZUg2a2xNcXpqaEYKc295Qk0vODFkWnllbzdzUDh1WGl1MkRUVkpVWWFEV005VzY3TlRSRWZ6TndUbTh2bUFjSjJlVG9lR3Z1MC96RApPejVDSWVsbWJZaVUvclVLVFNNdm0reFlOOFRGVkRmVFVQMHY0cHB2QjBmL2RIQThMTVBRYnhldVJKOD0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= server: https://172.200.1.200:6443 name: kubernetes - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR0ekNDQXA4Q0NRRElQbFpIRVVFUUtUQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNREl4TWpJd01EVXpNbG9YRFRNd01ESXdPVEl3TURVek1sb3dKakVPTUF3RwpBMVVFQXd3RmFtRnpiMjR4RkRBU0 JnTlZCQW9NQzNscGJucG9aVzVuYW1sbE1JSUNJakFOQmdrcWhraUc5dzBCCkFRRUZBQU9DQWc4QU1JSUNDZ0tDQWdFQTNCWTlITk9YUWxyNjNwZnF1U3ZJYXgyM3hGUW1kbHV2WUJZT0poVVEKQ3lhcmU3SS9TWXcrUHJETjRValZPN0o0L3VYdE0vNDVaRGcxV2gvN3NWTTl6VTJhUlEzS2ExQXZkZjMzMGVQQQpsYng5azMxZ1ljYk1TVGl2VFRWNm5seHpyazd3UGFuMXZjWDNEdjAzejJteCt1NGhzZW1KRU5KYTMvMlNBWnArCitVY1lHNkx5K0grcEhWMVNDU1VNSU5EdEpkQ0hJMWNoSG4zQXJEejFLRzVXYmVSWTlBbUdzSTdvTUJWYmJJSlcKYWdvbm1DZWpOMXZhMWg2L3JmR1Q0MmI5WkhaQ2taQkRzVGFzTVp6dDlUSVlyb0ticlR4NHBrcHd6N0VqaStKbgpRajFEaGlhRzlaemgwY1hQcW55TEVHRTFXeURxTUlmMXR5TGpyNFZ1ejk3L3dzMlJuRFl3N05ZSVFyUDhZdTdIClVXK1NLbklSQ1QwOCtONmtWSEVEak4rZFlTTDNtMi9kUG9aSGxhWkFqSkZUQVpmbDlSaytBZ1hPL29nUzB1VVAKYktwU2g4WnpGZ1dpcE92ZFFtalYyMHNzc0lUSDVPVGkyRzdOdHV5bWp2ZTRUWW9Zd24rbUVjS3hDWXhyUXh0bwpsSnBja3l3eDZ6eng0eXpWMGd6ZHgrU05NZjNKZ3pCMVBQWVdWM003R3RobThtUVFseUR6dVZNRDZZZDhyeTFlCjkzdzVyMHorL3RiOC9LQmNxV2Y5T25XVDFNejlEUnJuTVRyNjczQWhGSStNVlJYNDM0VzZXY0ttM3drSjFBWGQKSE85SlNMRHU3VGtBSlVYSTBuWWVVd2Rmd1NYbFZpNVBZdGV1WXpFdjF0bk9GZlFkclNqcTk3cEhoaU1EWkVENwprM2NDQXdFQUFUQU5CZ2txaGtpRzl3MEJBUXNGQUFPQ0FRRUFabGFrKzU4Ui81Zy9xWmJqOSsrcEl2Z3JWZkcrCndDZkZrVVJYRlE5UjhZSHVscEVNZDA0WXNQTVFlTEhoWHFWcjMyd2J2b2RsZkVmRVkwWWdEWVVvY1Y2TUdLK24KQzZPSlVqRTdMc0tMMEFUd0VZT2MzY1Q5UTRtbGpEK2dRQWF4UW1DUTF5Nlg3ZnM4NHRtMEROalR4alhqRGlLVAo3RmxoK0JGRm1oc1Zta2NmK0VMSUl3MmtYWjZudFNNbm5DVXJYcElhbGRmRU1zWTY0YVNLaVQvSStPUzJrd0tFCmhKNU5FeHcrYTZXYWt0THowdlZnRVhSZCtCdG0xNzNvdzl6RmVvdlE4N2hiaHJnZWZFMXN5MDR4aEVXM2VYTFIKWFJmYmJFNnlIYzg4NDJkdHE1SUhFVFJYRWtIZk1IWkNLMUhsL1Y5RklJMjM4RXd1Q05rczRYRWh2QT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K server: https://172.200.1.200:443 name: yinzhengjie-k8s contexts: - context: cluster: yinzhengjie-k8s user: jason name: jason@yinzhengjie-k8s - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: jason user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUR0ekNDQXA4Q0NRRElQbFpIRVVFUUtUQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNREl4TWpJd01EVXpNbG9YRFRNd01ESXdPVEl3TURVek1sb3dKakVPTUF3RwpBMVVFQXd3RmFtRnpiMjR4RkRBU0JnT lZCQW9NQzNscGJucG9aVzVuYW1sbE1JSUNJakFOQmdrcWhraUc5dzBCCkFRRUZBQU9DQWc4QU1JSUNDZ0tDQWdFQTNCWTlITk9YUWxyNjNwZnF1U3ZJYXgyM3hGUW1kbHV2WUJZT0poVVEKQ3lhcmU3SS9TWXcrUHJETjRValZPN0o0L3VYdE0vNDVaRGcxV2gvN3NWTTl6VTJhUlEzS2ExQXZkZjMzMGVQQQpsYng5azMxZ1ljYk1TVGl2VFRWNm5seHpyazd3UGFuMXZjWDNEdjAzejJteCt1NGhzZW1KRU5KYTMvMlNBWnArCitVY1lHNkx5K0grcEhWMVNDU1VNSU5EdEpkQ0hJMWNoSG4zQXJEejFLRzVXYmVSWTlBbUdzSTdvTUJWYmJJSlcKYWdvbm1DZWpOMXZhMWg2L3JmR1Q0MmI5WkhaQ2taQkRzVGFzTVp6dDlUSVlyb0ticlR4NHBrcHd6N0VqaStKbgpRajFEaGlhRzlaemgwY1hQcW55TEVHRTFXeURxTUlmMXR5TGpyNFZ1ejk3L3dzMlJuRFl3N05ZSVFyUDhZdTdIClVXK1NLbklSQ1QwOCtONmtWSEVEak4rZFlTTDNtMi9kUG9aSGxhWkFqSkZUQVpmbDlSaytBZ1hPL29nUzB1VVAKYktwU2g4WnpGZ1dpcE92ZFFtalYyMHNzc0lUSDVPVGkyRzdOdHV5bWp2ZTRUWW9Zd24rbUVjS3hDWXhyUXh0bwpsSnBja3l3eDZ6eng0eXpWMGd6ZHgrU05NZjNKZ3pCMVBQWVdWM003R3RobThtUVFseUR6dVZNRDZZZDhyeTFlCjkzdzVyMHorL3RiOC9LQmNxV2Y5T25XVDFNejlEUnJuTVRyNjczQWhGSStNVlJYNDM0VzZXY0ttM3drSjFBWGQKSE85SlNMRHU3VGtBSlVYSTBuWWVVd2Rmd1NYbFZpNVBZdGV1WXpFdjF0bk9GZlFkclNqcTk3cEhoaU1EWkVENwprM2NDQXdFQUFUQU5CZ2txaGtpRzl3MEJBUXNGQUFPQ0FRRUFabGFrKzU4Ui81Zy9xWmJqOSsrcEl2Z3JWZkcrCndDZkZrVVJYRlE5UjhZSHVscEVNZDA0WXNQTVFlTEhoWHFWcjMyd2J2b2RsZkVmRVkwWWdEWVVvY1Y2TUdLK24KQzZPSlVqRTdMc0tMMEFUd0VZT2MzY1Q5UTRtbGpEK2dRQWF4UW1DUTF5Nlg3ZnM4NHRtMEROalR4alhqRGlLVAo3RmxoK0JGRm1oc1Zta2NmK0VMSUl3MmtYWjZudFNNbm5DVXJYcElhbGRmRU1zWTY0YVNLaVQvSStPUzJrd0tFCmhKNU5FeHcrYTZXYWt0THowdlZnRVhSZCtCdG0xNzNvdzl6RmVvdlE4N2hiaHJnZWZFMXN5MDR4aEVXM2VYTFIKWFJmYmJFNnlIYzg4NDJkdHE1SUhFVFJYRWtIZk1IWkNLMUhsL1Y5RklJMjM4RXd1Q05rczRYRWh2QT09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlKS1FJQkFBS0NBZ0VBM0JZOUhOT1hRbHI2M3BmcXVTdklheDIzeEZRbWRsdXZZQllPSmhVUUN5YXJlN0kvClNZdytQckRONFVqVk83SjQvdVh0TS80NVpEZzFXaC83c1ZNOXpVMmFSUTNLYTFBdmRmMzMwZVBBbGJ4OWszMWcKWWNiTVNUaXZUVFY2bmx4enJrN3dQYW4xd mNYM0R2MDN6Mm14K3U0aHNlbUpFTkphMy8yU0FacCsrVWNZRzZMeQorSCtwSFYxU0NTVU1JTkR0SmRDSEkxY2hIbjNBckR6MUtHNVdiZVJZOUFtR3NJN29NQlZiYklKV2Fnb25tQ2VqCk4xdmExaDYvcmZHVDQyYjlaSFpDa1pCRHNUYXNNWnp0OVRJWXJvS2JyVHg0cGtwd3o3RWppK0puUWoxRGhpYUcKOVp6aDBjWFBxbnlMRUdFMVd5RHFNSWYxdHlManI0VnV6OTcvd3MyUm5EWXc3TllJUXJQOFl1N0hVVytTS25JUgpDVDA4K042a1ZIRURqTitkWVNMM20yL2RQb1pIbGFaQWpKRlRBWmZsOVJrK0FnWE8vb2dTMHVVUGJLcFNoOFp6CkZnV2lwT3ZkUW1qVjIwc3NzSVRINU9UaTJHN050dXltanZlNFRZb1l3bittRWNLeENZeHJReHRvbEpwY2t5d3gKNnp6eDR5elYwZ3pkeCtTTk1mM0pnekIxUFBZV1YzTTdHdGhtOG1RUWx5RHp1Vk1ENllkOHJ5MWU5M3c1cjB6KwovdGI4L0tCY3FXZjlPbldUMU16OURScm5NVHI2NzNBaEZJK01WUlg0MzRXNldjS20zd2tKMUFYZEhPOUpTTER1CjdUa0FKVVhJMG5ZZVV3ZGZ3U1hsVmk1UFl0ZXVZekV2MXRuT0ZmUWRyU2pxOTdwSGhpTURaRUQ3azNjQ0F3RUEKQVFLQ0FnQmNEVVVrVUcrY2hsY1ZVTzhRNGZvaXF6eFlkbVhiN1Q4dDdpdWV6QUo0MTRTejZQckZkVTMzaEpXbgoyNEdzUlZxTUtua0szUkwrRXZCbHNLamlJeEhmVTh6cGd2b2Q1bHpqZWdUMEdkRk1ENWxxWGU4NUZpQU5wQkxXCk5UOERDMklyRHNNMjEyWjhLRmZNUWliY3JyV05ZWnBnUW5CY3c4N1Vqc2RKdW1mUE5XZ2s3d08yNGhaR3ZPaDYKQUsvUTdmR3lka1IvaUlyR3FRdzBQZzdBQ1Y1RytsSW1SL0c0MlJ6T043Q1Vjdk5YeU1XRXcxZGw2UnBmb2w3RApqeDR1NTcybURqeUxpNDUwaVl4OTk4Z2pYUCtyeGQ3OUZ5VFRVS0ZjalJkMEE0N3l5cEw2Z2hUQ21BcHZaZEFVCjI2Q0NpbFg1dG91ZEh0Q3I5NERKd2dKMkdTeFpkQlpkdXJtaVAzdDhqbVNBQ1Z5YVdzaVloWThFWjNQMnkxVWwKcHUzNTFjSVNONE5vV09TTmFOcXVoTml1L0lGdEcwUnRGNmNabkVCemZlOXM5VFo4a2RhempYaU5PVHlTRit5MApqbnl5WjRWUVVQTVUveFZ2b1RMMWpYZjdQRzNqZHc5K1MzUVpGdU9xQnNWN1M3SFl1YXFTQW5lUnlTOU5vR25yClhXbGtUbHZwRml6N3VxaW1xM3hBa0xBY1gvOVNCb29UVmI3SVNiQnd6Q3ZrWVllVFNDUENqTGRMZUNheDIxMG4KZm5BRUQvZ0FRMzJGN0w5VzJmdVRhVUpENFlIMjhCQWFLeStIUVZDSWtHWnFFWjNQUGIyTVBqMGtBQks1citKVgo5TXdybHcxc2I1RzFtL3ZldlBBb1poaE9mcmVQUHZ6K3MzUFUxWFc2SDcwZk83emdJUUtDQVFFQS9JL3JvVjViClQ3L0dnd2Z3WmJqamNqUTNKcUhvaEJxM1Zxam5kUTNKc2lRKzJtdVNOaEpWS1NGaUNsaDdCM3FFZjFPZWxxaXQKMGN0VWNITkp4MUp2czBoWGxrQitrT0owdjJiM3gzUHBDcmFReTFDZys4L2xxV2U5OUhJdlMrbkNiR1p4SlNlegp6cklsT0JEZ3FGdDNtNHBIc3M2Q0xTc1BvU3NIdWIvMmp2SkxtUkRLRHRZdFVpaGExN3BGclpNQVUvWEw1ZzFsCjBmdlZJTXVzKzJ1b0N0Nzl5bHNZOWpkVkVXOWI1SGNiL1J1M1dFMHAzNFVROFpSR1FqKy83akpWWFo2SGNwMW4KNklxWS9rOGRIOFU0a1ZGL09FMXM1T3BUVVhXSzR0aGhqd0FRWGlzVURSL2RSWHNsSXUyK2t0Uk9wamw1THE4cgpDOGptSHQyMDlRZ2pod0tDQVFFQTN4VW5sUUdFZDVPQjZ0Z1cxOS9ORkRyb0NoS1E4d2k5R002MWp6QS9Wa1NvCkVxNXN1Vm1WNHFBNXdqbE5ycEJpSjZpenhaS0xHSzEwb1dOaHozT3grZ0hWMGNheWhmdlRjc1UwU2ZrOEloTHMKV0xBcmxIbDFseDNVSVp3eE8zRy91L09mMHFzVUhkanlja3lzZjh4TngzbFNlbktWbk1wSW5kWWJyNHBtTkphcwpxREFxSVkxcWdyaEIxeURqcVRFVHRybjVidS95QkE0c2VPRER3Z0tCMU1DUnp1Z1N2OC9tVVdaQjhqZlNwM2JMCnljbjFpTlR3Smh6emgvT2JPQTFkbTZjZTBtd2x1Vm1mN0pLcHY2Nk9KREFDaEl0VDErSmMzSmdKZ1VRTmxyeGMKS29JWENuZkt2OHV4dXVoVVEzSG1zcXR6YnhkcmsvbWVUK1ZuQ2luc2tRS0NBUUFXRnZCZytNTzd3ZVkyNTZiYQovc1RGNUZNK2ljS3dhelhGMnBnRDRPVFhNOXhiZGpVZmpaTHRPZ0k5TFdmMVMzM3pOUGtWN0VMbnFvVUVJTkUvCkliS3JWNVJ4aThxR0dZaGtoVGordE9DWkUwYXV3YXFTMjZnV25RQThOUkIxNzBnVit3L0NWQ3FoMVdyejhHWDEKMDZvdWJIWEE2ZGJ3NUdkRmpXSHJtU0tUZGhXdW1ZMVNwdURuNHFldlhwZGhpdzNvU2dNL1o4U1VEUmFpKzYxeApnQVQram1wY0hJT2VaVkNIYWRuN3JYOUJMLzlsTmJxSDFqZVpLWUxMb0kvRTRab2R5aFBHcm9XOERRTThtdWJOCk5JNnlCeEs5ZGVna1RXcGtJWWU0TjN5dzZTeUZUL2M4L3FCM3gwR0VRSTcrZ0pzd1pxNTJxdE4xQUdsQUlkd0YKNG1SWkFvSUJBUUNUWG9nOWVUa25QVHpRQlZ4aDA2akl1bmxiWGhSL1dNQ0N5TnRMOGxXRkNlbjJIV0FadWNLNAphWngrWUJpZlB5WjRpSXZwOHZzTW5GbTEyODlibWxSeWtnL01ldlNvYWttdlFmTmZBdFRrdFplSXB5akM5dEhsCnVJRFFpenhDeHN3Z3Y3cFBFMUZBdm5hN1owZDFUV1A4YUh0Q0JMd3RUYnhXK0lCbG9Jb1FKNUY3c2dYREVJYlMKUUNMT21SMk1RYTJDUXEweXlqUVkxYnd2Umx4THFCaFlrYlpBOXpLYm9CM0luRUxvWGxRODZNK0xTRzE1clNIUQpLOFA5aGNKK2J1WHQwNk1hNHZLdzFUSSt1RXlISWlzb1lNYnBCSm1vdmhNV2J5R29VV3FncjJJN2VxRDUrMVRuCkN3c29MQjZ1UjJwZGtjRzZHOENuaW5rNDBwVVZNOGpoQW9JQkFRQ0NCT092OUtCZ1JvRXd2QVA2cmlzY2FZYmUKOVdkZFB3MG12Y3JGM2FUWithMzMxZzdmS0ozSmUvQW8wWE5Cd3Q2UHFHOHNwbzZWRXQ1VnNlVnVUYjZTenJsNApEcEdvMEdPK2pzS2FhK3NWZ3pUdVh4SWQ1LzRJd3Y5QURRRG9zemVER1NrcUV5RmpyS0hCMklLNWFHSTE4bmV1CjdEREo3ZVhrQWZnTjYxYWJ0RXJJT240dWUwZXdJSWZ0TStHSHRBaWZ1dlBVYjdSUkhqZEdBaDY5bU1RTCtpZWcKNGFHb3RuSllrTVdIc3dkMVgyWUdCTUV4dWNlT1NUeFRURVBTNjFVQ0I1SFhnL1E1bTVwb3lYZG56MlpZQktPRApvUDVIUkFYUTBJRXZGTmhSZHJsZURDUGdFbklzY2ZjcXBQeGVtVlBJY3NuKzVUM2EvT1FrYmJYeUtwVk8KLS0tLS1FTkQgUlNBIFBSSVZBVEUgS0VZLS0tLS0K username: jason - name: kubernetes-admin user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM4akNDQWRxZ0F3SUJBZ0lJQ3NaaEJqaDJyWjB3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TURBeU1EUXhNVE01TVRKYUZ3MHlNVEF5TURNeE1UTTVNVFJhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUc HRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXdwL21nTndmcGJnVlJqUHIKaUF0Y25DeHZBZWh6S2ZjdlhWWEtMOWlKRERFWGFNT0lVVUt5U3JZNlhDOGh2a2xyY0puWGZQRk9WelpoVUk5cgpsbzVCa2UzUm5xbDRrT1pFeDNOejUyeTdpdEhPZHpIa2N1dEpoWjN0c0V5ck9qWlI4aHhxNlZ6eHcvWXpmemJSCmk2VTVEZ0lNQUxKbXoydWErdXVPYlhtcDlHNzhGWGxPdXQ0VFpKM1BkNUxOQWhwYWJnMlZuV0x4dXlTekNEaC8KU3FpMS9ua3d0WTdmYnR3dkNaN2J4eGF0OFpIZXF3cVJUSE9WdnBHaWZDNDV4Sjh5SUs3dzFrc0JqemtXYnhubwpBbU90TzBxM2ZnQ2JnVTF4L05Fc2NvVjJXMi91MnFqdXFIUnZUTEwra3hmbW1OcFBwVFJpMUJqNEFwYXF3eEFZCitVdGRXd0lEQVFBQm95Y3dKVEFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFCOHhmbVdUT1JGVE5yUVJDeVA4V1lUZFRzV1BWQ2R6TFZWdApEMWpOSGZWMkxreXB4bFFGZml2MHpnMFg1UHpkbUNnQXU0V3JVQjlUZGkvQU1zOTRPT1ozZUFmeGR1VDZFdVBHCkdmNm5OVXFOWlpIR3Z3NkpPeldNbUFCQzhxN3VQUHo3cWFOa0FFaDdwS1diMDE4cTFBRFdiYlVtRzhVMW1qOVgKQStnNDRoVVRTYlRKanVMaDFRMVVnbTNtbEZTZmM0VWZ5bDlheWlsQ2dXSXZlTU1TeFRyWDcvbGpSR2hLUUVaNgphcnVuMnVIbEIrODJIZ1NOZE9xdGhLaWlTZFBBZ2c2dDEvWTNxelZ1bmlSN01GdFNjSWkzQWxCeTJQdXE0cUpZCkJ6b3NMUitqclZGSitLUWx1TDlPTVVBUU5hZFd4OWpsUFBUK0VMazFkS0FCTDNRZTBQST0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo= client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBd3AvbWdOd2ZwYmdWUmpQcmlBdGNuQ3h2QWVoektmY3ZYVlhLTDlpSkRERVhhTU9JClVVS3lTclk2WEM4aHZrbHJjSm5YZlBGT1Z6WmhVSTlybG81QmtlM1JucWw0a09aRXgzTno1Mnk3aXRIT2R6SGsKY3V0SmhaM3RzRXlyT2paUjhoeHE2Vnp4d y9ZemZ6YlJpNlU1RGdJTUFMSm16MnVhK3V1T2JYbXA5Rzc4RlhsTwp1dDRUWkozUGQ1TE5BaHBhYmcyVm5XTHh1eVN6Q0RoL1NxaTEvbmt3dFk3ZmJ0d3ZDWjdieHhhdDhaSGVxd3FSClRIT1Z2cEdpZkM0NXhKOHlJSzd3MWtzQmp6a1dieG5vQW1PdE8wcTNmZ0NiZ1UxeC9ORXNjb1YyVzIvdTJxanUKcUhSdlRMTCtreGZtbU5wUHBUUmkxQmo0QXBhcXd4QVkrVXRkV3dJREFRQUJBb0lCQVFDVWNpZjdVMnBrR1ROSQoxNk1ub2hyaUY5WVhxM2ZqbzJFaUhLUlp1QnhZQ3oyaXI3bFMyYjlwMHZKU2k3UitFanY3cDZ1LzVjSHVMVkV1CmhDWDRzTXA4aHR0aTNEcFVzdjMwN3krUmJkTGlBRU10a1FXQlRjdEhPZjBvZ21IN3hhRGRQU1dpbHp6a1RlNWIKY3JHRGhPTXV0d3Iyb1J4Znl1QnIwSzFTL1FCUHFkNUNiL3hXU0tScWlDNjUrTGVsK0phQTEvL01ZcUtNUFlNNQplVHVjNVhhdWl6a0Y4K1pVTS9KMXNKVm5QR3VpR0VTR2NhRUlhTVY5bHc5ZC9OMDFwNnVuK255STY3NVJ2TlowCkszSlJoZ0tjNGxPTlpyb0dHS1dwOVloNnU2U2dZdWVYcUU2SUVyVnNvbzJDYWJ1dVJpTDhPM3hQOERJR2hQc1oKRjlmWEY2K1pBb0dCQU8xQXpTa0hNSWJISjduRFcwY250dVdaMUQyN29aajJ2RTZMbmprV0Fia3pkaXhSdGc0YQpmWnVOOTRpZUJSMzFEKy9QclM4WVkxTzdNOVhYaGdBN3BXcC80MnVYY0xFdGpGbUt1MFE5NHZGMnMvcGV2WDVhCncwdFkrNXFSaEliZytHU0tSZGZacHU4dCsreVVIZFVWcTFoYTVIaTVyb0ExWXh6RHJJdzE4SEF0QW9HQkFOSUEKelR6RENDTU5wV1pCc1A5bmhBMGNEWi9UQ01vbmRZcXVnMFllTWVLZ3lzR2tqM3ZoTHlUaEpkOWFTUmF1QzB5aApSSUhCZFpnYkl3V25VdnY2cDQ0alNTb2oyMWptcGpwSVg5c28rZ0dDd1NHRENOWUlFY1VvVG9Yd2ttWmhWQ2c0CjVySXoweXdmamgxQXU4V2xIa3R5ZmVGNHVQMEkwdXJIeUNER2FQQ25Bb0dCQU5jcXFlWEhxMjdRTjJyMWpWYWUKNGZTZzZpZUNmeS9tdFNqVzNvd1BOVWp0THdOS3A3MXFzUGZlYk52dDA5NHpYbHl6RC9GaVFOS3pPSE43bnYrZgpHSW5acWpydGdUcHVnSmJFaHNtQkJzek9Sck9PTUhUamc3SlY1UGx0ZDYrTFlEcHVYS0ZCdDIrN1dIcGFhaVBTCkh5OW1YMFpOdjhCdXFwQnZ0WkVEYWllUkFvR0FTeXJpUzVkN3VDQlFUYlBCeVFtaWFKYmNBWk1tR0VYYmV0SlEKUnE3VUtFeHBocnFDYVZNRzd1cHdCZXhwTU9jSFFGeVJDdWpXVUtXVitaWVV6QURDTE14UWlmYmZzb2lNZzF3WQpnM2U5VlFFYVpBWmxDVWRHSlEzeVhWcm83Q0IyWVJkTTdBaEUxQXhQY0FVVnNQOFRRdW91U0tCUGhySzczREc2ClhwRG1TdzBDZ1lFQTZDYW9HcnZVL21CTjNuSkp2bk41NGVtTGxkbVhGak1MQ2UraDA1RjFxSXVWT3VyQm1lbkEKMlhKMng0bFN6ODJBbVoxeTAxc1JMVXJWVGxJbWxkbW9Ldm92VmJETHMvSmZOUkRTQTFBTjY4ZzFNK0c3QVpNOQppaUNMTmFWS01ncUE0d3JlS2JieUROaGhuSjRjVGQwaWU2eTRLVUJvaFhnTXl4K2FnWUZwQnpNPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=[root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl config view apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:6443 name: kubernetes - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:443 name: yinzhengjie-k8s contexts: - context: cluster: yinzhengjie-k8s user: jason name: jason@yinzhengjie-k8s - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: kubernetes-admin@kubernetes kind: Config preferences: {} users: - name: jason user: client-certificate-data: REDACTED client-key-data: REDACTED username: jason - name: kubernetes-admin user: client-certificate-data: REDACTED client-key-data: REDACTED [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config get-contexts CURRENT NAME CLUSTER AUTHINFO NAMESPACE jason@yinzhengjie-k8s yinzhengjie-k8s jason * kubernetes-admin@kubernetes kubernetes kubernetes-admin [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get pods NAME READY STATUS RESTARTS AGE etcd-0 0/1 Pending 0 14h [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
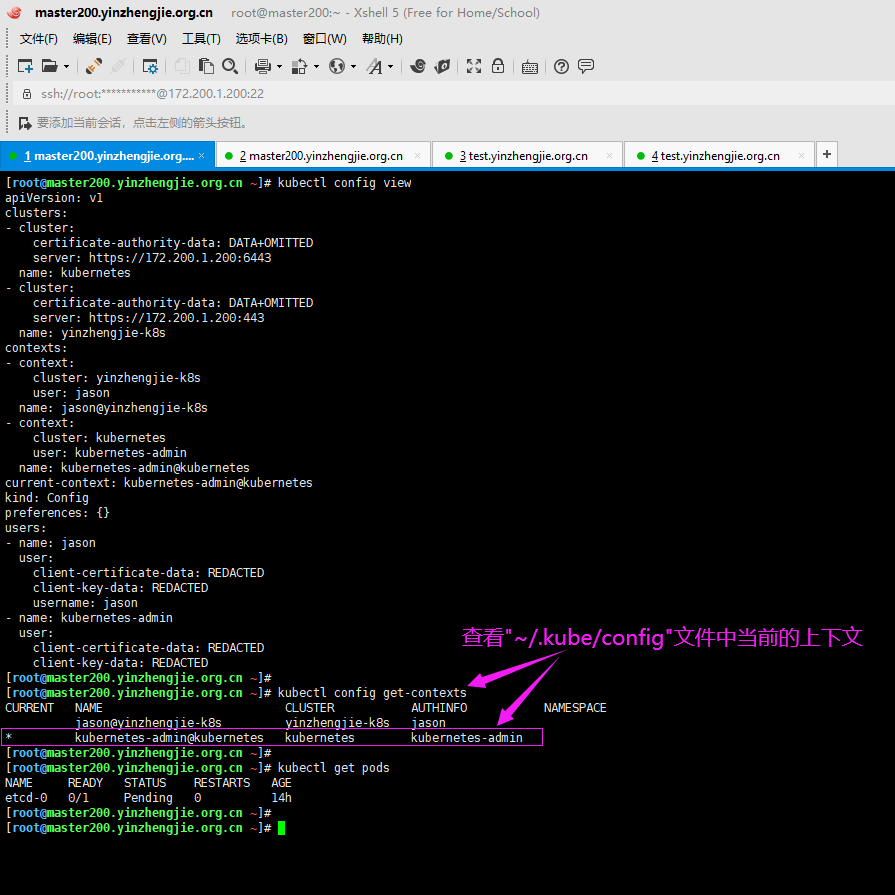
8>.切换用户

[root@master200.yinzhengjie.org.cn ~]# kubectl config get-contexts CURRENT NAME CLUSTER AUTHINFO NAMESPACE jason@yinzhengjie-k8s yinzhengjie-k8s jason * kubernetes-admin@kubernetes kubernetes kubernetes-admin [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get pods NAME READY STATUS RESTARTS AGE etcd-0 0/1 Pending 0 14h [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config use-context jason@yinzhengjie-k8s Switched to context "jason@yinzhengjie-k8s". [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config get-contexts CURRENT NAME CLUSTER AUTHINFO NAMESPACE * jason@yinzhengjie-k8s yinzhengjie-k8s jason kubernetes-admin@kubernetes kubernetes kubernetes-admin [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get pods The connection to the server 172.200.1.200:443 was refused - did you specify the right host or port? [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl get pods The connection to the server 172.200.1.200:443 was refused - did you specify the right host or port? [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config get-contexts CURRENT NAME CLUSTER AUTHINFO NAMESPACE * jason@yinzhengjie-k8s yinzhengjie-k8s jason kubernetes-admin@kubernetes kubernetes kubernetes-admin [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config use-context kubernetes-admin@kubernetes Switched to context "kubernetes-admin@kubernetes". [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config get-contexts CURRENT NAME CLUSTER AUTHINFO NAMESPACE jason@yinzhengjie-k8s yinzhengjie-k8s jason * kubernetes-admin@kubernetes kubernetes kubernetes-admin [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get pods NAME READY STATUS RESTARTS AGE etcd-0 0/1 Pending 0 14h [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
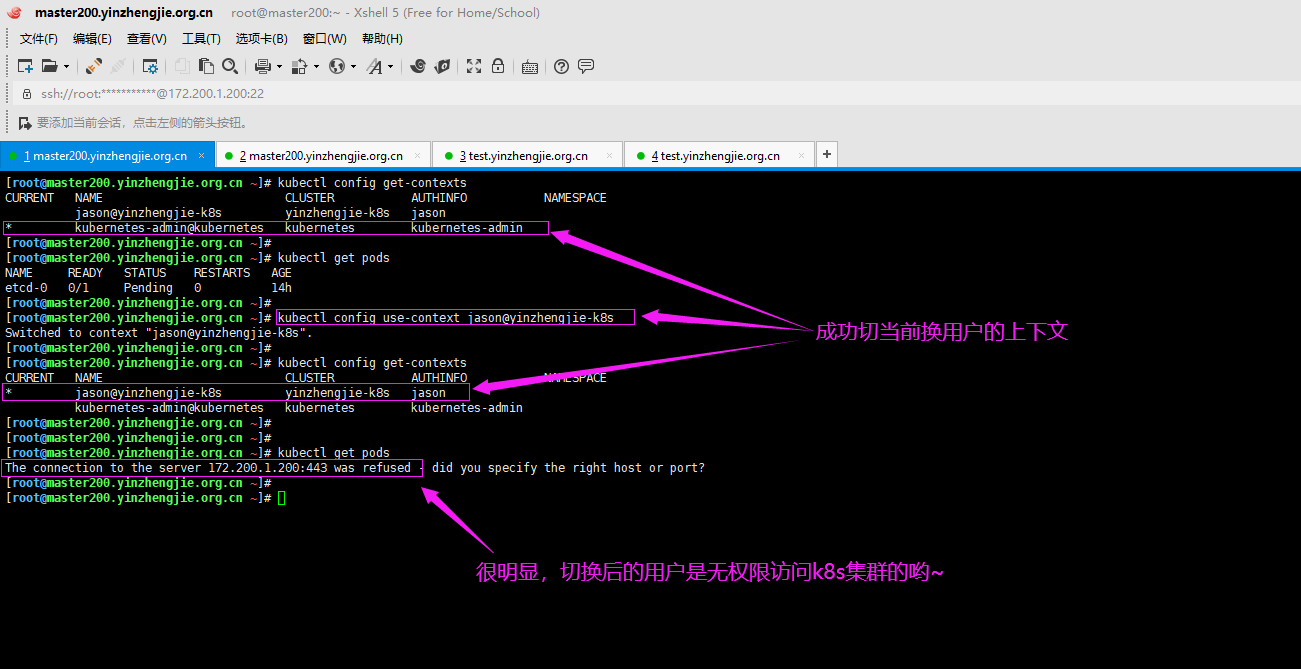
9>.为自定义的配置文件配置上下文

[root@master200.yinzhengjie.org.cn ~]# kubectl config use-context -h Sets the current-context in a kubeconfig file Aliases: use-context, use Examples: # Use the context for the minikube cluster kubectl config use-context minikube Usage: kubectl config use-context CONTEXT_NAME [options] Use "kubectl options" for a list of global command-line options (applies to all commands). [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config view --kubeconfig=/tmp/jason.config apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:443 name: yinzhengjie-k8s contexts: - context: cluster: yinzhengjie-k8s user: jason name: jason@yinzhengjie-k8s current-context: "" kind: Config preferences: {} users: - name: jason user: client-certificate-data: REDACTED client-key-data: REDACTED username: jason [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config get-contexts --kubeconfig=/tmp/jason.config CURRENT NAME CLUSTER AUTHINFO NAMESPACE jason@yinzhengjie-k8s yinzhengjie-k8s jason [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config use-context jason@yinzhengjie-k8s --kubeconfig=/tmp/jason.config Switched to context "jason@yinzhengjie-k8s". [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config view --kubeconfig=/tmp/jason.config apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:443 name: yinzhengjie-k8s contexts: - context: cluster: yinzhengjie-k8s user: jason name: jason@yinzhengjie-k8s current-context: jason@yinzhengjie-k8s kind: Config preferences: {} users: - name: jason user: client-certificate-data: REDACTED client-key-data: REDACTED username: jason [root@master200.yinzhengjie.org.cn ~]#
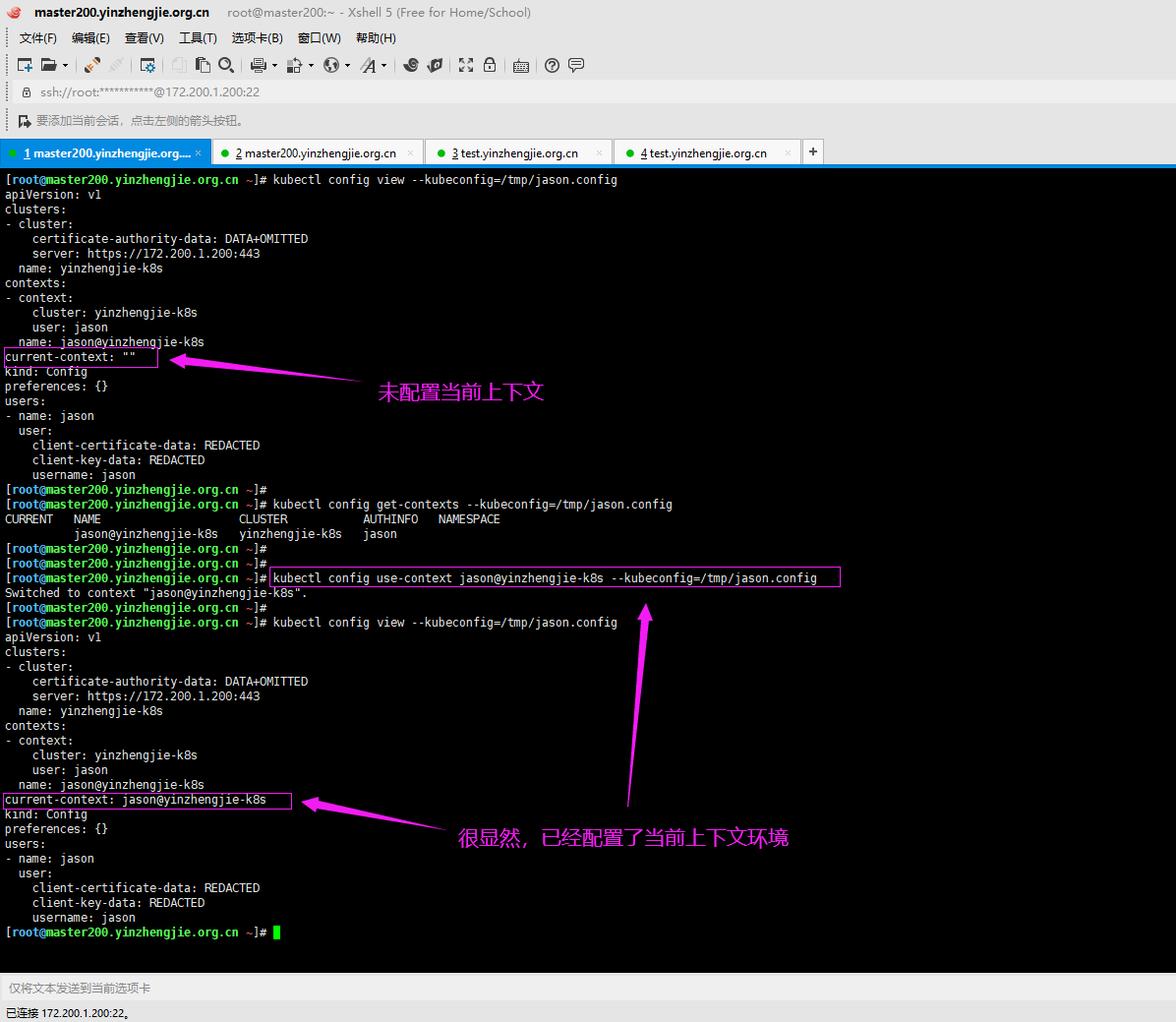
10>.使用自定义的配置文件访问K8s集群(由于没有为用户配置权限,因此无法访问K8S集群)

[root@master200.yinzhengjie.org.cn ~]# kubectl config view --kubeconfig=/tmp/jason.config apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:443 name: yinzhengjie-k8s contexts: - context: cluster: yinzhengjie-k8s user: jason name: jason@yinzhengjie-k8s current-context: jason@yinzhengjie-k8s kind: Config preferences: {} users: - name: jason user: client-certificate-data: REDACTED client-key-data: REDACTED username: jason [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config get-contexts --kubeconfig=/tmp/jason.config CURRENT NAME CLUSTER AUTHINFO NAMESPACE * jason@yinzhengjie-k8s yinzhengjie-k8s jason [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get pods --kubeconfig=/tmp/jason.config The connection to the server 172.200.1.200:443 was refused - did you specify the right host or port? [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
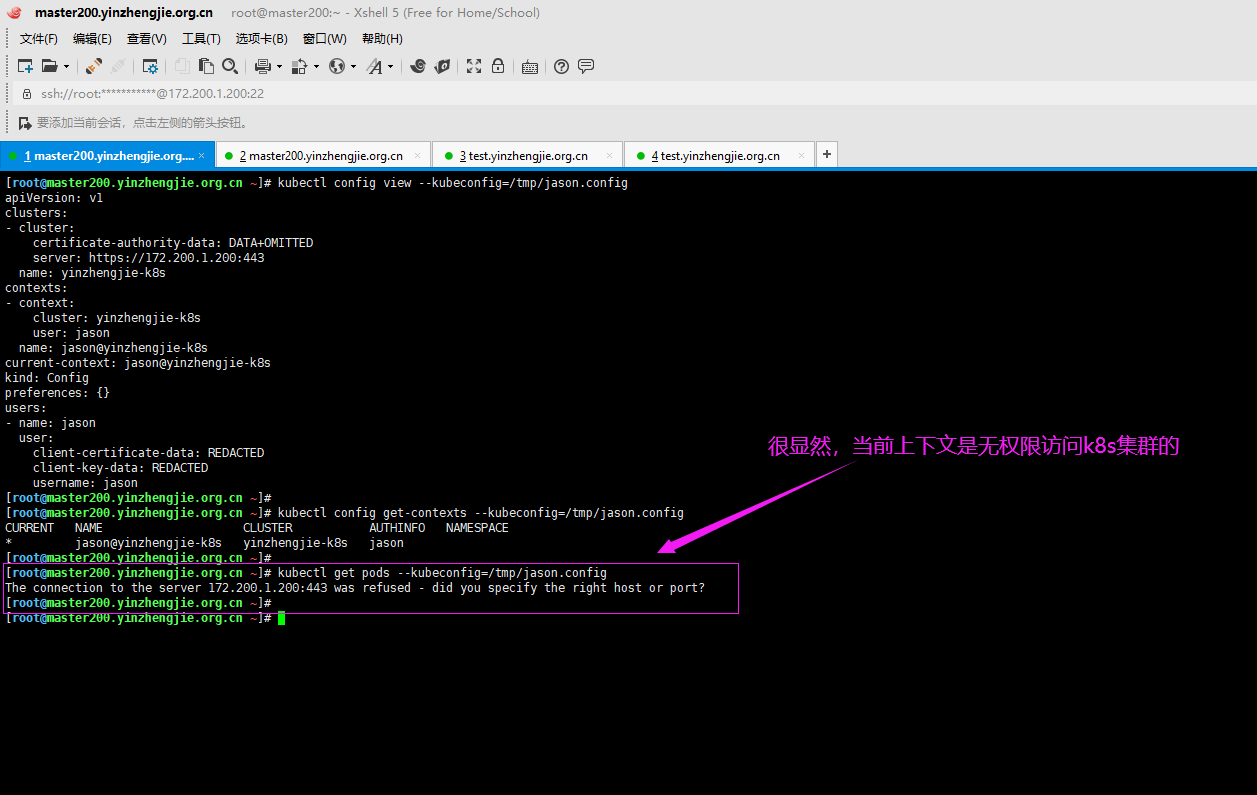
四.自定义服务账号(Service Account)实战案例
1>.定义服务账号的配置清单

[root@master200.yinzhengjie.org.cn ~]# kubectl explain sa KIND: ServiceAccount VERSION: v1 DESCRIPTION: ServiceAccount binds together: * a name, understood by users, and perhaps by peripheral systems, for an identity * a principal that can be authenticated and authorized * a set of secrets FIELDS: apiVersion <string> APIVersion defines the versioned schema of this representation of an object. Servers should convert recognized schemas to the latest internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources automountServiceAccountToken <boolean> AutomountServiceAccountToken indicates whether pods running as this service account should have an API token automatically mounted. Can be overridden at the pod level. imagePullSecrets <[]Object> ImagePullSecrets is a list of references to secrets in the same namespace to use for pulling any images in pods that reference this ServiceAccount. ImagePullSecrets are distinct from Secrets because Secrets can be mounted in the pod, but ImagePullSecrets are only accessed by the kubelet. More info: https://kubernetes.io/docs/concepts/containers/images/#specifying-imagepullsecrets-on-a-pod kind <string> Kind is a string value representing the REST resource this object represents. Servers may infer this from the endpoint the client submits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds metadata <Object> Standard object's metadata. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#metadata secrets <[]Object> Secrets is the list of secrets allowed to be used by pods running using this ServiceAccount. More info: https://kubernetes.io/docs/concepts/configuration/secret [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# cat /yinzhengjie/data/k8s/manifests/basic/serviceaccount-demo.yaml apiVersion: v1 kind: ServiceAccount metadata: name: sa-demo namespace: default [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
2>.创建服务账号

[root@master200.yinzhengjie.org.cn ~]# kubectl get sa NAME SECRETS AGE default 1 10d [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl apply -f /yinzhengjie/data/k8s/manifests/basic/serviceaccount-demo.yaml serviceaccount/sa-demo created [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get sa NAME SECRETS AGE default 1 10d sa-demo 1 2s [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl describe sa Name: default Namespace: default Labels: <none> Annotations: <none> Image pull secrets: <none> Mountable secrets: default-token-4jpjf Tokens: default-token-4jpjf Events: <none> Name: sa-demo Namespace: default Labels: <none> Annotations: kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"v1","kind":"ServiceAccount","metadata":{"annotations":{},"name":"sa-demo","namespace":"default"}} Image pull secrets: <none> Mountable secrets: sa-demo-token-nkz6x Tokens: sa-demo-token-nkz6x Events: <none> [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
3>.查看创建服务账号时K8S自动创建的secrets信息

[root@master200.yinzhengjie.org.cn ~]# kubectl get sa NAME SECRETS AGE default 1 10d sa-demo 1 2m8s [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl describe sa Name: default Namespace: default Labels: <none> Annotations: <none> Image pull secrets: <none> Mountable secrets: default-token-4jpjf Tokens: default-token-4jpjf Events: <none> Name: sa-demo Namespace: default Labels: <none> Annotations: kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"v1","kind":"ServiceAccount","metadata":{"annotations":{},"name":"sa-demo","namespace":"default"}} Image pull secrets: <none> Mountable secrets: sa-demo-token-nkz6x Tokens: sa-demo-token-nkz6x Events: <none> [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get secrets NAME TYPE DATA AGE default-token-4jpjf kubernetes.io/service-account-token 3 10d sa-demo-token-nkz6x kubernetes.io/service-account-token 3 2m18s [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
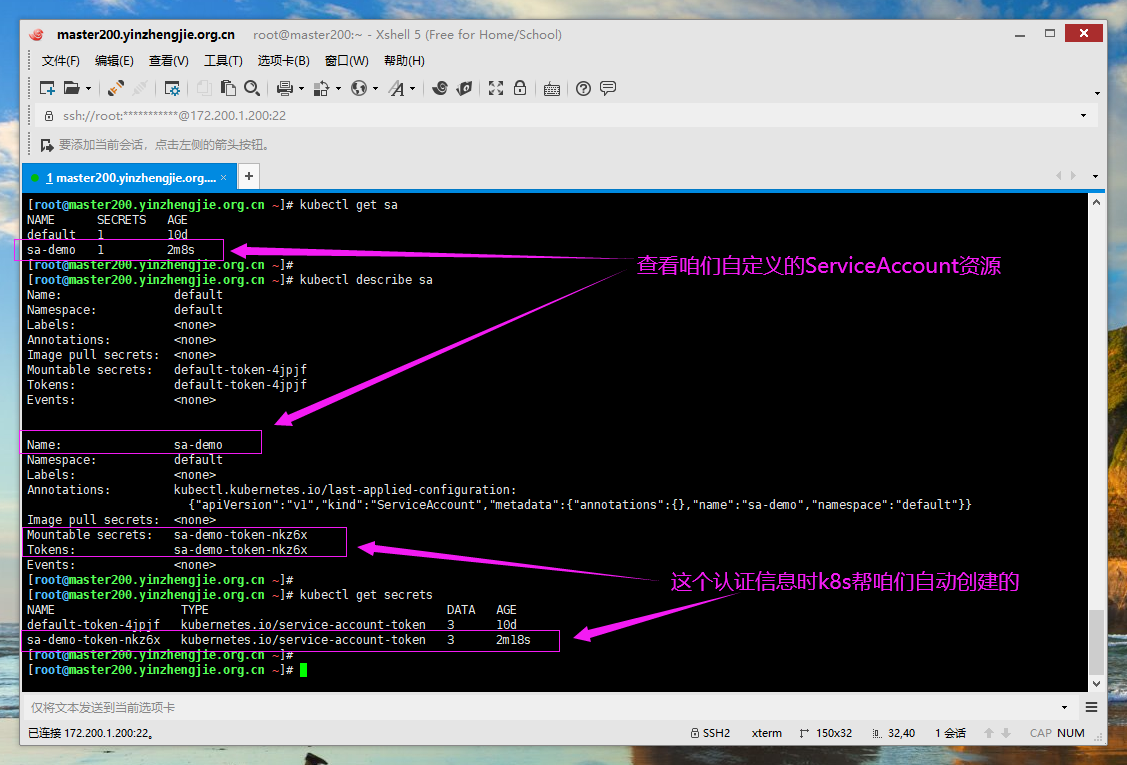
五.Kubernetes授权策略(authorization policy)
博主推荐阅读: https://www.cnblogs.com/yinzhengjie/p/12310192.html
本文来自博客园,作者:尹正杰,转载请注明原文链接:https://www.cnblogs.com/yinzhengjie/p/12302138.html,个人微信: "JasonYin2020"(添加时请备注来源及意图备注,有偿付费)
当你的才华还撑不起你的野心的时候,你就应该静下心来学习。当你的能力还驾驭不了你的目标的时候,你就应该沉下心来历练。问问自己,想要怎样的人生。




